CN116383867A - Data query method, device, electronic equipment and computer readable medium - Google Patents
Data query method, device, electronic equipment and computer readable medium Download PDFInfo
- Publication number
- CN116383867A CN116383867A CN202310118592.6A CN202310118592A CN116383867A CN 116383867 A CN116383867 A CN 116383867A CN 202310118592 A CN202310118592 A CN 202310118592A CN 116383867 A CN116383867 A CN 116383867A
- Authority
- CN
- China
- Prior art keywords
- encrypted data
- file
- ciphertext file
- character string
- ciphertext
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Pending
Links
- 238000000034 method Methods 0.000 title claims abstract description 45
- 238000012795 verification Methods 0.000 claims abstract description 26
- 230000004044 response Effects 0.000 claims abstract description 22
- 230000009466 transformation Effects 0.000 claims description 41
- 238000004364 calculation method Methods 0.000 claims description 23
- 238000004590 computer program Methods 0.000 claims description 9
- 238000004422 calculation algorithm Methods 0.000 claims description 7
- 238000004458 analytical method Methods 0.000 claims description 6
- 238000013507 mapping Methods 0.000 claims description 5
- 230000000873 masking effect Effects 0.000 claims 1
- 238000012545 processing Methods 0.000 description 15
- 238000010586 diagram Methods 0.000 description 14
- 230000006870 function Effects 0.000 description 14
- 238000004891 communication Methods 0.000 description 7
- 235000010627 Phaseolus vulgaris Nutrition 0.000 description 5
- 244000046052 Phaseolus vulgaris Species 0.000 description 5
- 238000006243 chemical reaction Methods 0.000 description 4
- 230000003287 optical effect Effects 0.000 description 4
- 238000012935 Averaging Methods 0.000 description 3
- 230000036541 health Effects 0.000 description 3
- 238000003780 insertion Methods 0.000 description 3
- 230000037431 insertion Effects 0.000 description 3
- 238000012986 modification Methods 0.000 description 3
- 230000004048 modification Effects 0.000 description 3
- 230000008569 process Effects 0.000 description 3
- 241001076732 Rhodomonas lens Species 0.000 description 2
- 230000008901 benefit Effects 0.000 description 2
- 238000005516 engineering process Methods 0.000 description 2
- 239000000835 fiber Substances 0.000 description 2
- 230000000644 propagated effect Effects 0.000 description 2
- 239000004065 semiconductor Substances 0.000 description 2
- 238000013475 authorization Methods 0.000 description 1
- 238000010276 construction Methods 0.000 description 1
- 125000004122 cyclic group Chemical group 0.000 description 1
- 238000013461 design Methods 0.000 description 1
- 230000000694 effects Effects 0.000 description 1
- 239000004973 liquid crystal related substance Substances 0.000 description 1
- 239000013307 optical fiber Substances 0.000 description 1
- 230000001737 promoting effect Effects 0.000 description 1
- 238000004171 remote diagnosis Methods 0.000 description 1
- 238000006467 substitution reaction Methods 0.000 description 1
Images
Classifications
-
- G—PHYSICS
- G06—COMPUTING; CALCULATING OR COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/60—Protecting data
- G06F21/62—Protecting access to data via a platform, e.g. using keys or access control rules
- G06F21/6218—Protecting access to data via a platform, e.g. using keys or access control rules to a system of files or objects, e.g. local or distributed file system or database
- G06F21/6245—Protecting personal data, e.g. for financial or medical purposes
-
- G—PHYSICS
- G16—INFORMATION AND COMMUNICATION TECHNOLOGY [ICT] SPECIALLY ADAPTED FOR SPECIFIC APPLICATION FIELDS
- G16H—HEALTHCARE INFORMATICS, i.e. INFORMATION AND COMMUNICATION TECHNOLOGY [ICT] SPECIALLY ADAPTED FOR THE HANDLING OR PROCESSING OF MEDICAL OR HEALTHCARE DATA
- G16H10/00—ICT specially adapted for the handling or processing of patient-related medical or healthcare data
- G16H10/60—ICT specially adapted for the handling or processing of patient-related medical or healthcare data for patient-specific data, e.g. for electronic patient records
-
- G—PHYSICS
- G16—INFORMATION AND COMMUNICATION TECHNOLOGY [ICT] SPECIALLY ADAPTED FOR SPECIFIC APPLICATION FIELDS
- G16H—HEALTHCARE INFORMATICS, i.e. INFORMATION AND COMMUNICATION TECHNOLOGY [ICT] SPECIALLY ADAPTED FOR THE HANDLING OR PROCESSING OF MEDICAL OR HEALTHCARE DATA
- G16H50/00—ICT specially adapted for medical diagnosis, medical simulation or medical data mining; ICT specially adapted for detecting, monitoring or modelling epidemics or pandemics
- G16H50/70—ICT specially adapted for medical diagnosis, medical simulation or medical data mining; ICT specially adapted for detecting, monitoring or modelling epidemics or pandemics for mining of medical data, e.g. analysing previous cases of other patients
-
- G—PHYSICS
- G06—COMPUTING; CALCULATING OR COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F2221/00—Indexing scheme relating to security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F2221/21—Indexing scheme relating to G06F21/00 and subgroups addressing additional information or applications relating to security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F2221/2107—File encryption
-
- Y—GENERAL TAGGING OF NEW TECHNOLOGICAL DEVELOPMENTS; GENERAL TAGGING OF CROSS-SECTIONAL TECHNOLOGIES SPANNING OVER SEVERAL SECTIONS OF THE IPC; TECHNICAL SUBJECTS COVERED BY FORMER USPC CROSS-REFERENCE ART COLLECTIONS [XRACs] AND DIGESTS
- Y02—TECHNOLOGIES OR APPLICATIONS FOR MITIGATION OR ADAPTATION AGAINST CLIMATE CHANGE
- Y02D—CLIMATE CHANGE MITIGATION TECHNOLOGIES IN INFORMATION AND COMMUNICATION TECHNOLOGIES [ICT], I.E. INFORMATION AND COMMUNICATION TECHNOLOGIES AIMING AT THE REDUCTION OF THEIR OWN ENERGY USE
- Y02D10/00—Energy efficient computing, e.g. low power processors, power management or thermal management
Landscapes
- Engineering & Computer Science (AREA)
- Health & Medical Sciences (AREA)
- General Health & Medical Sciences (AREA)
- Medical Informatics (AREA)
- Public Health (AREA)
- Databases & Information Systems (AREA)
- Bioethics (AREA)
- Data Mining & Analysis (AREA)
- Primary Health Care (AREA)
- Epidemiology (AREA)
- Theoretical Computer Science (AREA)
- General Physics & Mathematics (AREA)
- General Engineering & Computer Science (AREA)
- Physics & Mathematics (AREA)
- Software Systems (AREA)
- Computer Hardware Design (AREA)
- Computer Security & Cryptography (AREA)
- Biomedical Technology (AREA)
- Pathology (AREA)
- Storage Device Security (AREA)
- Information Retrieval, Db Structures And Fs Structures Therefor (AREA)
Abstract
The application discloses a data query method, a data query device, electronic equipment and a computer readable medium, and relates to the technical field of Internet medical treatment, wherein a specific implementation mode comprises the steps of receiving a data query request and acquiring a corresponding terminal identifier and a corresponding retrieval condition; determining a corresponding ciphertext file according to the retrieval condition, and further performing access permission verification according to the ciphertext file and the terminal identification; in response to successful access right verification, calling a local encryption key to encrypt the search condition, and generating an encrypted search condition; matching the encryption retrieval condition with the ciphertext file, and obtaining a successfully matched file in response to the fact that the file exists in the ciphertext file and the encryption retrieval condition are successfully matched; and calling the local decryption key to decrypt the successfully matched file to obtain query result data. So as to improve the safety of the user information and effectively prevent the user information from being leaked.
Description
Technical Field
The present disclosure relates to the field of internet medical technology, and in particular, to a data query method, a data query device, an electronic device, and a computer readable medium.
Background
Currently, internet medical is an emerging industry for developing various health medical information services such as on-line health education, medical information consultation, remote diagnosis or consultation, electronic prescriptions, electronic health files, etc. by using the internet as a carrier and a technical means, and has been rapidly developed in recent years. On one hand, internet medical treatment provides a new solving way in the aspects of solving unbalance of medical resource supply and demand, accelerating industry competition, promoting innovation of a medical service system, deepening medical reform and the like; on the other hand, in the internet medical scene, patient information needs to be processed, and information security and privacy management of the patient information are important points of attention.
Disclosure of Invention
In view of this, embodiments of the present application provide a data query method, apparatus, electronic device, and computer readable medium, which can enhance protection of patient information, and patient information is safer.
To achieve the above object, according to one aspect of the embodiments of the present application, there is provided a data query method, including:
receiving a data query request, and acquiring a corresponding terminal identifier and a search condition;
determining a corresponding ciphertext file according to the retrieval condition, and further performing access permission verification according to the ciphertext file and the terminal identification;
In response to successful access right verification, calling a local encryption key to encrypt the search condition, and generating an encrypted search condition;
matching the encryption retrieval condition with the ciphertext file, and obtaining a successfully matched file in response to the fact that the file exists in the ciphertext file and the encryption retrieval condition are successfully matched;
and calling the local decryption key to decrypt the successfully matched file to obtain query result data.
Optionally, before determining the corresponding ciphertext file according to the retrieval condition, the method further comprises:
acquiring historical user information and historical retrieval conditions;
determining a corresponding user identifier according to the historical user information, and mapping the user identifier and the historical user information to a target object;
encrypting the attribute of the character string type in the target object to obtain first encrypted data;
performing encryption calculation on the first encrypted data based on the information summary algorithm to obtain second encrypted data;
and generating the ciphertext file based on the historical search condition and the second encrypted data.
Optionally, generating the ciphertext file based on the historical search condition and the second encrypted data includes:
determining a target access address according to the history retrieval condition;
Calling a character string hash function to calculate a corresponding hash value based on the target access address;
based on the hash value, determining the number of character string bits, and further based on the number of character string bits, generating a target character string and determining a character string interval;
and generating a ciphertext file based on the second encrypted data, the string interval, and the target string.
Optionally, generating the ciphertext file based on the second encrypted data, the string interval, and the target string, includes:
performing remainder calculation on the second encrypted data to obtain a remainder calculation result, and generating first transformed encrypted data based on the remainder calculation result and the character string interval;
adding characters in the target character string to the first transformation encrypted data based on the character string interval to obtain second transformation encrypted data;
a random number is generated, and a ciphertext file is generated based on the random number, the string interval, and the second transformed encrypted data.
Optionally, generating the ciphertext file based on the random number, the string interval, and the second transformed encrypted data comprises:
performing a data flip operation on the second transformed encrypted data based on the random number to generate third transformed encrypted data;
generating a random string according to the random number, further adding the random string to the tail part of the third transformation encrypted data, and adding the random number and the character string interval to the head part of the third transformation encrypted data;
Acquiring a sequence number of the analysis rule, and further adding the sequence number to the tail of the third transformation encrypted data to generate fourth transformation encrypted data;
and obtaining the ciphertext file based on the fourth transformed encrypted data.
Optionally, acquiring historical user information includes:
the method comprises the steps of obtaining original user information, carrying out mask processing on the original user information to obtain historical user information and obtaining the historical user information.
Optionally, obtaining the file successfully matched includes:
searching whether a character string matched with the encryption search condition exists in the ciphertext file, if so, traversing a byte array of the ciphertext file to obtain a matching substring list, and making a difference between each element in the matching substring list and the ciphertext corresponding to the user identifier to obtain a successfully matched file, and if not, returning matching failure information.
In addition, the application also provides a data query device, which comprises:
the receiving unit is configured to receive the data query request and acquire the corresponding terminal identification and the search condition;
the verification unit is configured to determine a corresponding ciphertext file according to the retrieval condition, and further perform access permission verification according to the ciphertext file and the terminal identifier;
an encryption unit configured to invoke a local encryption key to encrypt the search condition in response to success of the access right verification, generating an encrypted search condition;
The matching unit is configured to match the encryption retrieval condition with the ciphertext file, and the successfully matched file is obtained in response to the fact that the file exists in the ciphertext file and the encryption retrieval condition are successfully matched;
and the decryption unit is configured to call the local decryption key to decrypt the successfully matched file to obtain query result data.
Optionally, the data query device further includes a ciphertext file generating unit configured to:
acquiring historical user information and historical retrieval conditions;
determining a corresponding user identifier according to the historical user information, and mapping the user identifier and the historical user information to a target object;
encrypting the attribute of the character string type in the target object to obtain first encrypted data;
performing encryption calculation on the first encrypted data based on the information summary algorithm to obtain second encrypted data;
and generating the ciphertext file based on the historical search condition and the second encrypted data.
Optionally, the ciphertext file generating unit is further configured to:
determining a target access address according to the history retrieval condition;
calling a character string hash function to calculate a corresponding hash value based on the target access address;
based on the hash value, determining the number of character string bits, and further based on the number of character string bits, generating a target character string and determining a character string interval;
And generating a ciphertext file based on the second encrypted data, the string interval, and the target string.
Optionally, the ciphertext file generating unit is further configured to:
performing remainder calculation on the second encrypted data to obtain a remainder calculation result, and generating first transformed encrypted data based on the remainder calculation result and the character string interval;
adding characters in the target character string to the first transformation encrypted data based on the character string interval to obtain second transformation encrypted data;
a random number is generated, and a ciphertext file is generated based on the random number, the string interval, and the second transformed encrypted data.
Optionally, the ciphertext file generating unit is further configured to:
performing a data flip operation on the second transformed encrypted data based on the random number to generate third transformed encrypted data;
generating a random string according to the random number, further adding the random string to the tail part of the third transformation encrypted data, and adding the random number and the character string interval to the head part of the third transformation encrypted data;
acquiring a sequence number of the analysis rule, and further adding the sequence number to the tail of the third transformation encrypted data to generate fourth transformation encrypted data;
and obtaining the ciphertext file based on the fourth transformed encrypted data.
Optionally, the ciphertext file generating unit is further configured to:
the method comprises the steps of obtaining original user information, carrying out mask processing on the original user information to obtain historical user information and obtaining the historical user information.
Optionally, the matching unit is further configured to:
searching whether a character string matched with the encryption search condition exists in the ciphertext file, if so, traversing a byte array of the ciphertext file to obtain a matching substring list, and making a difference between each element in the matching substring list and the ciphertext corresponding to the user identifier to obtain a successfully matched file, and if not, returning matching failure information.
In addition, the application also provides a data query electronic device, which comprises: one or more processors; and a storage device for storing one or more programs which, when executed by the one or more processors, cause the one or more processors to implement the data query method as described above.
In addition, the application also provides a computer readable medium, on which a computer program is stored, which when executed by a processor, implements the data query method as described above.
One embodiment of the above invention has the following advantages or benefits: the method comprises the steps of obtaining corresponding terminal identifiers and search conditions by receiving a data query request; determining a corresponding ciphertext file according to the retrieval condition, and further performing access permission verification according to the ciphertext file and the terminal identification; in response to successful access right verification, calling a local encryption key to encrypt the search condition, and generating an encrypted search condition; matching the encryption retrieval condition with the ciphertext file, and obtaining a successfully matched file in response to the fact that the file exists in the ciphertext file and the encryption retrieval condition are successfully matched; and calling the local decryption key to decrypt the successfully matched file to obtain query result data. So as to improve the safety of the user information and effectively prevent the user information from being leaked.
Further effects of the above-described non-conventional alternatives are described below in connection with the embodiments.
Drawings
The drawings are included to provide a better understanding of the present application and are not to be construed as unduly limiting the present application. Wherein:
FIG. 1 is a schematic diagram of the main flow of a data query method according to one embodiment of the present application;
FIG. 2 is a schematic diagram of the main flow of a data query method according to one embodiment of the present application;
fig. 3 is an application scenario schematic diagram of a data query method according to an embodiment of the present application;
FIG. 4 is a schematic diagram of the main units of a data querying device according to an embodiment of the present application;
FIG. 5 is an exemplary system architecture diagram in which embodiments of the present application may be applied;
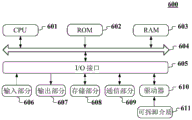
fig. 6 is a schematic diagram of a computer system suitable for use in implementing the terminal device or server of the embodiments of the present application.
Detailed Description
Exemplary embodiments of the present application are described below in conjunction with the accompanying drawings, which include various details of the embodiments of the present application to facilitate understanding, and should be considered as merely exemplary. Accordingly, one of ordinary skill in the art will recognize that various changes and modifications of the embodiments described herein can be made without departing from the scope and spirit of the present application. Also, descriptions of well-known functions and constructions are omitted in the following description for clarity and conciseness. It should be noted that, in the technical solution of the present disclosure, the related aspects of collecting, updating, analyzing, processing, using, transmitting, storing, etc. of the personal information of the user all conform to the rules of the related laws and regulations, and are used for legal purposes without violating the public order colloquial. Necessary measures are taken for the personal information of the user, illegal access to the personal information data of the user is prevented, and the personal information security, network security and national security of the user are maintained.
Fig. 1 is a schematic diagram of main flow of a data query method according to an embodiment of the present application, where, as shown in fig. 1, the data query method includes:
step S101, receiving a data query request, and acquiring a corresponding terminal identifier and a search condition.
In this embodiment, the execution body (for example, may be a server) of the data query method may receive the data query request through a wired connection or a wireless connection. The data query request may be, for example, a request for querying data that needs to be kept secret, for example, a request for querying patient data. The content of the data query request in the embodiment of the present application is not particularly limited. After the execution body obtains the data query request, the execution body can obtain the terminal identifier and the search condition carried in the request.
The terminal identifier may be a client number, a client name, etc. used when the user initiates the data query request, which is not specifically limited in the embodiment of the present application. The search condition may be, for example, a search sentence including a user name and a user search keyword, and the content of the search condition is not particularly limited in the embodiment of the present application.
Step S102, determining a corresponding ciphertext file according to the search condition, and further performing access permission verification according to the ciphertext file and the terminal identification.
The access control system may call each ciphertext file to match the search condition carried in the data query request with each called ciphertext file, specifically may match the search condition carried in the data query request with the history search condition associated with each called ciphertext file, and determine the ciphertext file corresponding to the matched history search condition as the ciphertext file corresponding to the search condition carried in the data query request.
After determining the ciphertext file corresponding to the search condition carried in the data query request, the execution subject can call the permission verification program to match the terminal identifier corresponding to the data query request with the determined ciphertext file, so as to perform access permission verification based on the matching result.
Step S103, in response to successful access right verification, the local encryption key is called to encrypt the search condition, and an encrypted search condition is generated.
When the executing main body determines that the terminal corresponding to the terminal identifier has access right to the ciphertext file, the local key can be used for encrypting the search condition to match the ciphertext file.
Step S104, matching the encryption retrieval condition with the ciphertext file, and obtaining a successfully matched file in response to successful matching of the file existing in the ciphertext file and the encryption retrieval condition.
And after the encryption retrieval condition is matched with the file to be retrieved in the ciphertext file, downloading the successfully matched ciphertext file to be retrieved to the local.
Specifically, obtaining a file successfully matched includes: searching whether a character string matched with the encryption search condition exists in the ciphertext file, if so, traversing a byte array of the ciphertext file to obtain a matching substring list, and making a difference between each element in the matching substring list and the ciphertext corresponding to the user identifier, wherein the user identifier can be a user serial number, for example, an execution subject can make a user information signature on the user serial number, so that a successfully matched file is obtained, and if not, returning matching failure information.
Step S105, the local decryption key is called to decrypt the successfully matched file, and query result data is obtained.
After downloading the successfully matched ciphertext file to be searched to the local, decrypting the successfully matched ciphertext file to be searched by using the local key to obtain the finally searched query result data.
The embodiment obtains the corresponding terminal identification and the search condition by receiving the data query request; determining a corresponding ciphertext file according to the retrieval condition, and further performing access permission verification according to the ciphertext file and the terminal identification; in response to successful access right verification, calling a local encryption key to encrypt the search condition, and generating an encrypted search condition; matching the encryption retrieval condition with the ciphertext file, and obtaining a successfully matched file in response to the fact that the file exists in the ciphertext file and the encryption retrieval condition are successfully matched; and calling the local decryption key to decrypt the successfully matched file to obtain query result data. So as to improve the safety of the user information and effectively prevent the user information from being leaked.
Fig. 2 is a main flow chart of a data query method according to an embodiment of the present application, as shown in fig. 2, before determining a corresponding ciphertext file according to a retrieval condition, the data query method further includes:
step S201, acquiring history user information and history retrieval conditions.
Specifically, acquiring historical user information includes:
the method comprises the steps of obtaining original user information, carrying out mask processing on the original user information to obtain historical user information and obtaining the historical user information.
For example, the original user information is written with a user nickname example (corresponding to a patient nickname in an internet hospital) in a code, a method mask name 8Star is written in the code, the head and the tail of the user nickname are reserved by using a character string splicing application method in the method, the middle part is replaced by 'x', and the user nickname information after mask processing can be obtained and used as historical user information after the operation is completed.
The history search condition may include, for example, a search keyword, a user name, etc. input by each history user corresponding to the history user information, and the embodiment of the present application does not specifically limit the history search condition.
Step S202, corresponding user identification is determined according to the historical user information, and the user identification and the historical user information are mapped to a target object.
Each user has a unique identification serial number, and the serial number is used for signing patient information, namely the user identification corresponding to the historical user information. The target object may be, for example, a bean object, and the corresponding historical user information and user identification are mapped in the bean object and stored.
In step S203, the attribute of the character string type in the target object is encrypted to obtain the first encrypted data.
And encrypting all the attributes which are of the character string type in the user information bean to obtain first encrypted data.
In step S204, the first encrypted data is encrypted based on the information summarization algorithm to obtain second encrypted data.
And processing the encrypted first encrypted data based on the information digest algorithm, namely performing MD5 processing, wherein the MD5 processing is to call Apache commons codec to realize MD5 encryption on the first encrypted data, calculate the MD5 digest and return a hexadecimal character string with 32 characters, namely second encrypted data.
Step S205, a ciphertext file is generated based on the history retrieval condition and the second encrypted data.
The history retrieval condition and the second encrypted data are mapped in a target object (such as a bean object), and all the attributes of all the character string types in the target object are encrypted.
Specifically, based on the history retrieval condition and the second encrypted data, generating the ciphertext file includes: determining a target access address according to the history retrieval condition; calling a character string hash function to calculate a corresponding hash value based on the target access address; based on the hash value, determining the number of character string bits, and further based on the number of character string bits, generating a target character string and determining a character string interval; and generating a ciphertext file based on the second encrypted data, the string interval, and the target string.
Taking the original user information as an example (corresponding to the patient pin in the internet hospital) of the user personal identification code (Personal identification number, pin), the MD5 is used to encrypt the original user information into a 32-bit ciphertext p, where p is the received traditional ciphertext, and the following is set as follows:
p=2510c39011c5be704182423e3a695e91;
processing a server IP address to be accessed by a user (i.e. a target access address) by using a Fu Chuanha hash function to obtain a hash value x, averaging all numbers in x to obtain a value y, judging which value of 8, 16 and 32 is closest to the value y according to the numerical value of y x 4 to determine to randomly generate a string of 8 or 16 or 32 bits, wherein the value range of the characters in the string is [0, f ] (16 scale), for example, the average value y=5 is 5*4 =20 closest to 16, the string of 16 bits is generated as r, the length of the string is r.lens, for example, r=2db 95e8e1a9267b7 is r.lens=16; taking the interval i=32/r.length, where i=2. And generating a ciphertext file based on the second encrypted data, the string interval, and the target string.
Specifically, generating the ciphertext file based on the second encrypted data, the string interval, and the target string, includes: performing remainder calculation on the second encrypted data to obtain a remainder calculation result, and generating first transformed encrypted data based on the remainder calculation result and the character string interval; adding characters in the target character string to the first transformation encrypted data based on the character string interval to obtain second transformation encrypted data; a random number is generated, and a ciphertext file is generated based on the random number, the string interval, and the second transformed encrypted data.
p is transformed according to the operation of taking the remainder of the original character and adding the i value, and the remainder of y=x is converted into y after the original character x is set, so that a transformation table is generated as follows:
original x 01 2 3 4 5 6 7 8 9a b c d e f takes the remainder f e d c b a 9 8 7 6 5 4 3 2 10 final value y 1 0f e d c b a 9 8 7 6 5 4 3 2
p is converted according to the conversion table, and the p-converted encrypted data p1=fc 015e81005c63a1d09fdfe3e7b8c380 is converted into first converted encrypted data
On the basis of the above conversion, the character in r is added uniformly every i bits in the p character string, where i=2 corresponds to the insertion of one character every 2 bits, and 16 bits are inserted in total, and the obtained second converted encrypted data p2 is as follows;
p2=fc(2)01(d)5e(b)81(9)00(5)5ce63(8)a1(e)d0(1)9f(a)df(9)e3(2)e7(6)
b8(7)c3(b)80(7);
Wherein the characters in brackets are the characters in the character string r;
based on the transformation, a random number j is generated, and the value range is [2, 15], for example, j=7.
Encrypting data based on random number j, string interval i and second transformation
p2=fc (2) 01 (d) 5e (b) 81 (9) 00 (5) 5ce63 (8) a1 (e) d0 (1) 9f (a) df (9) e3 (2) e7 (6) b8 (7) c3 (b) 80 (7), generating a ciphertext file.
Specifically, generating the ciphertext file based on the random number, the string interval, and the second transformed encrypted data, includes: performing a data flip operation on the second transformed encrypted data based on the random number to generate third transformed encrypted data; generating a random string according to the random number, further adding the random string to the tail part of the third transformation encrypted data, and adding the random number and the character string interval to the head part of the third transformation encrypted data; acquiring a sequence number of the analysis rule, and further adding the sequence number to the tail of the third transformation encrypted data to generate fourth transformation encrypted data; and obtaining the ciphertext file based on the fourth transformed encrypted data.
For example, the second transformed encrypted data p2 string is transformed according to j=7, flipped once every 7 bits, and finally flipped less than 7 bits, and the processed third transformed encrypted data p string is as follows:
p3=5d102cf-00918be-836ec55-910de1a-3e9fdaf-78b67e2-708b3c;
Based on the transformation, a random string s is generated according to j, the length is j, the content value range is [0, f ], for example, s=f327a9910 c;
adding the character string s to the tail part of the character string p to obtain:
p3’=5d102cf-00918be-836ec55-910de1a-3e9fdaf-78b67e2-708b3c-f46a91c;
adding parameters j and i to the string p header, yields:
p3”=725d102cf-00918be-836ec55-910de1a-3e9fdaf-78b67e2-708b3c-f46a91c;
adding the sequence number k=2 of the parsing rule to the tail of the fourth transformed encrypted data string p, to obtain:
p4=725 d102cf-00918be-836ec55-910de1a-3e9fdaf-78b67e2-708b3c-f46a91c2, thereby completing further encryption of the string p to obtain a result ciphertext string, i.e. a ciphertext file.
By way of example, the following is an overall embodiment of generating a ciphertext file:
acquiring historical user information and historical retrieval conditions;
determining a corresponding user identification according to the historical user information, and mapping the historical user information to a target object, such as a bean object;
encrypting the attribute of the character string type in the target object to obtain first encrypted data;
performing encryption calculation on the first encrypted data based on the information summary algorithm to obtain second encrypted data;
determining a target access address according to the history retrieval condition;
calling a character string hash function to calculate a corresponding hash value based on the target access address;
Averaging the numbers in the hash value to obtain an average value;
determining the number of character string bits (e.g., 8 bits, 16 bits, 32 bits) according to the average value and the preset value (e.g., 8, 16, 32);
generating a target character string (r) according to the number of character string bits and a preset character value range, such as [0, f ] (16 scale);
determining a character string interval (i) according to the number of character string bits;
performing remainder calculation on the second encrypted data to obtain a remainder calculation result, and generating first transformed encrypted data p1 based on the remainder calculation result and the character string interval;
adding characters in the target character string to the first transformed encrypted data based on the character string interval to obtain second transformed encrypted data p2;
generating a random number, and further performing a data flip operation on the second transformed encrypted data based on the random number to generate third transformed encrypted data p3;
generating a random string according to the random number, adding the random string to the tail of the third transformation encrypted data, adding the random number and a character string interval to the head of the third transformation encrypted data, and adding the sequence number of the analysis rule to the tail of the third transformation encrypted data to generate fourth transformation encrypted data p4;
And obtaining the ciphertext file based on the fourth transformed encrypted data.
For example, taking the original user information as an example, taking the user pin (corresponding to the patient pin in the internet hospital), the MD5 is used to encrypt the original user information into a 32-bit ciphertext p, where p is the received traditional ciphertext, and the following is set as follows:
p=2510c39011c5be704182423e3a695e91;
processing the IP address of the service end to be accessed by a user by using a Fu Chuanha hash function to obtain a hash value x, averaging all numbers in x to obtain a value y, judging which value of 8, 16 and 32 is closest to the value y according to the numerical value of y.4 to determine to randomly generate a string of 8 or 16 or 32 bits, wherein the value range of the characters in the string is [0, f ] (16 scale), for example, the average value y=5 is 5*4 =20 closest to 16, the string of 16 bits is generated as r, the length of the string is r.length, for example, r=2db 95e8e1a9267b7, and r.length=16;
taking the string interval i=32/r.length, where i=2;
p is transformed according to the operation of taking the remainder of the original character and adding the i value, and the remainder of y=x is converted into y after the original character x is set, so that a transformation table is generated as follows:
original x 0 1 2 3 4 5 67 8 9a b c d e f takes the remainder f e d c b a9 8 7 6 5 4 32 10 final value y 1 0f e d c b a9 8 7 6 5 4 32
When p is converted according to the conversion table, p=fc 015e81005c63a1d09fdfe3e7b8c380 is obtained
On the basis of the above conversion, the character in r is added uniformly every i bits in the p character string, where i=2 corresponds to the insertion of one character every 2 bits, and the total insertion of 16 bits gives the result p as follows;
p2=fc(2)01(d)5e(b)81(9)00(5)5ce63(8)a1(e)d0(1)9f(a)df(9)e3(2)e7(6)
b8(7)c3(b)80(7);
wherein the characters in brackets are the characters in r;
based on the transformation, a random number j is generated, and the value range is [2, 15], for example, j=7.
The p string is converted according to j=7, and is flipped once every 7 bits, and finally, all the p strings with less than 7 bits are flipped, and the processed p string is as follows:
p3=5d102cf-00918be-836ec55-910de1a-3e9fdaf-78b67e2-708b3c;
based on the transformation, a random string s is generated according to j, the length is j, the content value range is [0, f ], for example, s=f327a9910 c;
adding the character string s to the tail part of the character string p to obtain:
p3’=5d102cf-00918be-836ec55-910de1a-3e9fdaf-78b67e2-708b3c-f46a91c;
adding parameters j and i to the string p header, yields:
p3”=725d102cf-00918be-836ec55-910de1a-3e9fdaf-78b67e2-708b3c-f46a91c;
adding the sequence number k=2 of the parsing rule to the tail of the character string p, to obtain:
p4=725 d102cf-00918be-836ec55-910de1a-3e9fdaf-78b67e2-708b3c-f46a91c2, thereby completing further encryption of the string p to obtain a result ciphertext string, i.e. a ciphertext file.
Fig. 3 is an application scenario diagram of a data query method according to an embodiment of the present application. The data query method of the embodiment of the application can be applied to a scene of querying encrypted data. As shown in fig. 3, the medical data and the search condition are encrypted by using the local key of the client, and are stored in the storage module in a ciphertext mode, so that the server can be ensured that the server cannot know the information contained in the ciphertext medical file; when the Client retrieves, the user uses the retrieval condition to enter the access control system through the Client (Client), and the access control system determines whether the Client has access rights to the ciphertext file. If the authority is not available, directly returning; if the client has the access right, the client directly encrypts the search condition to the ciphertext file by using the local key to match, downloads the file to be searched to the local after finding the file to be searched, and then decrypts the ciphertext file by using the local key to obtain a final searched result.
The data security module is protected by two layers of security technologies, and great progress is made in protecting the privacy of medical data. The protection function of the access control system can effectively prevent illegal access of a part of users, and the integrity of medical data is protected: a searchable symmetric encryption scheme is adopted, and local keys are used for encryption to improve the information access security coefficient. The patient information security is increased by multiple encryption and signing, and encrypting the information in the database. The database stores all the encrypted data, and the real user information can not be detected through ordinary inquiry. To obtain the user's real information, the encrypted data must be taken out of the database and decrypted before the correct user information can be found. The encryption process for data may include the following: 1. input: indefinite length information (information to be encrypted). 2. And (3) outputting: fixed length 128-bits. Consists of four 32-bit packets, which are concatenated to generate a 128-bit hash value. 3. The basic mode is as follows: and (5) performing cyclic operation on the remainder, the adjustment length and the link variable to obtain a result.
Fig. 4 is a schematic diagram of main units of a data query device according to an embodiment of the present application. As shown in fig. 4, the data query apparatus 400 includes a receiving unit 401, a verifying unit 402, an encrypting unit 403, a matching unit 404, and a decrypting unit 405.
A receiving unit 401 configured to receive a data query request, and obtain a corresponding terminal identifier and a search condition;
the verification unit 402 is configured to determine a corresponding ciphertext file according to the retrieval condition, and further perform access permission verification according to the ciphertext file and the terminal identifier;
an encryption unit 403 configured to invoke a local encryption key to encrypt the search condition in response to success of the access right verification, generating an encrypted search condition;
a matching unit 404 configured to match the encrypted search condition with the ciphertext file, and obtain a successfully matched file in response to successful matching of the file existing in the ciphertext file with the encrypted search condition;
the decryption unit 405 is configured to call the local decryption key to decrypt the successfully matched file, so as to obtain query result data.
In some embodiments, the data querying device further comprises a ciphertext file generating unit, not shown in fig. 4, configured to: acquiring historical user information and historical retrieval conditions; determining a corresponding user identifier according to the historical user information, and mapping the user identifier and the historical user information to a target object; encrypting the attribute of the character string type in the target object to obtain first encrypted data; performing encryption calculation on the first encrypted data based on the information summary algorithm to obtain second encrypted data; and generating the ciphertext file based on the historical search condition and the second encrypted data.
In some embodiments, the ciphertext file generating unit is further configured to: determining a target access address according to the history retrieval condition; calling a character string hash function to calculate a corresponding hash value based on the target access address; based on the hash value, determining the number of character string bits, and further based on the number of character string bits, generating a target character string and determining a character string interval; and generating a ciphertext file based on the second encrypted data, the string interval, and the target string.
In some embodiments, the ciphertext file generating unit is further configured to: performing remainder calculation on the second encrypted data to obtain a remainder calculation result, and generating first transformed encrypted data based on the remainder calculation result and the character string interval; adding characters in the target character string to the first transformation encrypted data based on the character string interval to obtain second transformation encrypted data; a random number is generated, and a ciphertext file is generated based on the random number, the string interval, and the second transformed encrypted data.
In some embodiments, the ciphertext file generating unit is further configured to: performing a data flip operation on the second transformed encrypted data based on the random number to generate third transformed encrypted data; generating a random string according to the random number, further adding the random string to the tail part of the third transformation encrypted data, and adding the random number and the character string interval to the head part of the third transformation encrypted data; acquiring a sequence number of the analysis rule, and further adding the sequence number to the tail of the third transformation encrypted data to generate fourth transformation encrypted data; and obtaining the ciphertext file based on the fourth transformed encrypted data.
In some embodiments, the ciphertext file generating unit is further configured to: the method comprises the steps of obtaining original user information, carrying out mask processing on the original user information to obtain historical user information and obtaining the historical user information.
In some embodiments, the matching unit 404 is further configured to: searching whether a character string matched with the encryption search condition exists in the ciphertext file, if so, traversing a byte array of the ciphertext file to obtain a matching substring list, and making a difference between each element in the matching substring list and the ciphertext corresponding to the user identifier to obtain a successfully matched file, and if not, returning matching failure information.
It should be noted that, the data query method and the data query device in the present application have a corresponding relationship in implementation content, so repeated content will not be described.
Fig. 5 illustrates an exemplary system architecture 500 in which the data query method or data query apparatus of embodiments of the present application may be applied.
As shown in fig. 5, the system architecture 500 may include terminal devices 501, 502, 503, a network 504, and a server 505. The network 504 is used as a medium to provide communication links between the terminal devices 501, 502, 503 and the server 505. The network 504 may include various connection types, such as wired, wireless communication links, or fiber optic cables, among others.
A user may interact with the server 505 via the network 504 using the terminal devices 501, 502, 503 to receive or send messages or the like. Various communication client applications may be installed on the terminal devices 501, 502, 503, such as shopping class applications, web browser applications, search class applications, instant messaging tools, mailbox clients, social platform software, etc. (by way of example only).
The terminal devices 501, 502, 503 may be a variety of electronic devices having a data query processing screen and supporting web browsing, including but not limited to smartphones, tablets, laptop and desktop computers, and the like.
The server 505 may be a server providing various services, such as a background management server (by way of example only) providing support for data query requests submitted by users using the terminal devices 501, 502, 503. The background management server can receive the data query request and acquire the corresponding terminal identification and the search condition; determining a corresponding ciphertext file according to the retrieval condition, and further performing access permission verification according to the ciphertext file and the terminal identification; in response to successful access right verification, calling a local encryption key to encrypt the search condition, and generating an encrypted search condition; matching the encryption retrieval condition with the ciphertext file, and obtaining a successfully matched file in response to the fact that the file exists in the ciphertext file and the encryption retrieval condition are successfully matched; and calling the local decryption key to decrypt the successfully matched file to obtain query result data. So as to improve the safety of the user information and effectively prevent the user information from being leaked.
It should be noted that, the data query method provided in the embodiments of the present application is generally executed by the server 505, and accordingly, the data query device is generally disposed in the server 505.
It should be understood that the number of terminal devices, networks and servers in fig. 5 is merely illustrative. There may be any number of terminal devices, networks, and servers, as desired for implementation.
Referring now to FIG. 6, a schematic diagram of a computer system 600 suitable for use in implementing the terminal device of an embodiment of the present application is shown. The terminal device shown in fig. 6 is only an example, and should not impose any limitation on the functions and the scope of use of the embodiments of the present application.
As shown in fig. 6, the computer system 600 includes a Central Processing Unit (CPU) 601, which can perform various appropriate actions and processes according to a program stored in a Read Only Memory (ROM) 602 or a program loaded from a storage section 608 into a Random Access Memory (RAM) 603. In the RAM603, various programs and data required for the operation of the computer system 600 are also stored. The CPU601, ROM602, and RAM603 are connected to each other through a bus 604. An input/output (I/O) interface 605 is also connected to bus 604.
The following components are connected to the I/O interface 605: an input portion 606 including a keyboard, mouse, etc.; an output portion 607 including a Cathode Ray Tube (CRT), a liquid crystal credit authorization query processor (LCD), and the like, and a speaker, and the like; a storage section 608 including a hard disk and the like; and a communication section 609 including a network interface card such as a LAN card, a modem, or the like. The communication section 609 performs communication processing via a network such as the internet. The drive 610 is also connected to the I/O interface 605 as needed. Removable media 611 such as a magnetic disk, an optical disk, a magneto-optical disk, a semiconductor memory, or the like is installed as needed on drive 610 so that a computer program read therefrom is installed as needed into storage section 608.
In particular, according to embodiments of the present disclosure, the processes described above with reference to flowcharts may be implemented as computer software programs. For example, embodiments disclosed herein include a computer program product comprising a computer program embodied on a computer readable medium, the computer program comprising program code for performing the method shown in the flowcharts. In such an embodiment, the computer program may be downloaded and installed from a network through the communication portion 609, and/or installed from the removable medium 611. The above-described functions defined in the system of the present application are performed when the computer program is executed by a Central Processing Unit (CPU) 601.
It should be noted that the computer readable medium shown in the present application may be a computer readable signal medium or a computer readable storage medium, or any combination of the two. The computer readable storage medium may include, for example, but is not limited to, an electronic, magnetic, optical, electromagnetic, infrared, or semiconductor system, apparatus, or device, or a combination of any of the foregoing. More specific examples of the computer-readable storage medium may include, but are not limited to: an electrical connection having one or more wires, a portable computer diskette, a hard disk, a Random Access Memory (RAM), a read-only memory (ROM), an erasable programmable read-only memory (EPROM or flash memory), an optical fiber, a portable compact disc read-only memory (CD-ROM), an optical storage device, a magnetic storage device, or any suitable combination of the foregoing. In the context of this document, a computer readable storage medium may be any tangible medium that can contain, or store a program for use by or in connection with an instruction execution system, apparatus, or device. In the present application, however, a computer-readable signal medium may include a data signal propagated in baseband or as part of a carrier wave, with computer-readable program code embodied therein. Such a propagated data signal may take any of a variety of forms, including, but not limited to, electro-magnetic, optical, or any suitable combination of the foregoing. A computer readable signal medium may also be any computer readable medium that is not a computer readable storage medium and that can communicate, propagate, or transport a program for use by or in connection with an instruction execution system, apparatus, or device. Program code embodied on a computer readable medium may be transmitted using any appropriate medium, including but not limited to: wireless, wire, fiber optic cable, RF, etc., or any suitable combination of the foregoing.
The flowcharts and block diagrams in the figures illustrate the architecture, functionality, and operation of possible implementations of systems, methods and computer program products according to various embodiments of the present application. In this regard, each block in the flowchart or block diagrams may represent a module, segment, or portion of code, which comprises one or more executable instructions for implementing the specified logical function(s). It should also be noted that, in some alternative implementations, the functions noted in the block may occur out of the order noted in the figures. For example, two blocks shown in succession may, in fact, be executed substantially concurrently, or the blocks may sometimes be executed in the reverse order, depending upon the functionality involved. It will also be noted that each block of the block diagrams or flowchart illustration, and combinations of blocks in the block diagrams or flowchart illustration, can be implemented by special purpose hardware-based systems which perform the specified functions or acts, or combinations of special purpose hardware and computer instructions.
The units involved in the embodiments of the present application may be implemented by software, or may be implemented by hardware. The described units may also be provided in a processor, for example, described as: a processor includes a receiving unit, a checking unit, an encrypting unit, a matching unit, and a decrypting unit. Wherein the names of the units do not constitute a limitation of the units themselves in some cases.
As another aspect, the present application also provides a computer-readable medium that may be contained in the apparatus described in the above embodiments; or may be present alone without being fitted into the device. The computer readable medium carries one or more programs, which when executed by one of the devices, cause the device to receive a data query request, and obtain a corresponding terminal identification and search conditions; determining a corresponding ciphertext file according to the retrieval condition, and further performing access permission verification according to the ciphertext file and the terminal identification; in response to successful access right verification, calling a local encryption key to encrypt the search condition, and generating an encrypted search condition; matching the encryption retrieval condition with the ciphertext file, and obtaining a successfully matched file in response to the fact that the file exists in the ciphertext file and the encryption retrieval condition are successfully matched; and calling the local decryption key to decrypt the successfully matched file to obtain query result data.
According to the technical scheme of the embodiment of the application, the safety of the user information can be improved, and the user information is effectively prevented from being leaked.
The above embodiments do not limit the scope of the application. It will be apparent to those skilled in the art that various modifications, combinations, sub-combinations and alternatives can occur depending upon design requirements and other factors. Any modifications, equivalent substitutions and improvements made within the spirit and principles of the present application are intended to be included within the scope of the present application.
Claims (10)
1. A method of querying data, comprising:
receiving a data query request, and acquiring a corresponding terminal identifier and a search condition;
determining a corresponding ciphertext file according to the search condition, and further performing access permission verification according to the ciphertext file and the terminal identifier;
in response to successful access right verification, calling a local encryption key to encrypt the search condition, and generating an encryption search condition;
matching the encryption retrieval condition with the ciphertext file, and obtaining a successfully matched file in response to successful matching of the file existing in the ciphertext file and the encryption retrieval condition;
and calling a local decryption key to decrypt the successfully matched file to obtain query result data.
2. The method of claim 1, wherein prior to said determining the corresponding ciphertext file based on the retrieval condition, the method further comprises:
acquiring historical user information and historical retrieval conditions;
determining a corresponding user identifier according to the historical user information, and mapping the user identifier and the historical user information to a target object;
encrypting the attribute of the character string type in the target object to obtain first encrypted data;
performing encryption calculation on the first encrypted data based on an information summary algorithm to obtain second encrypted data;
and generating a ciphertext file based on the historical search condition and the second encrypted data.
3. The method of claim 2, wherein the generating a ciphertext file based on the historical search condition and the second encrypted data comprises:
determining a target access address according to the history retrieval condition;
calling a character string hash function to calculate a corresponding hash value based on the target access address;
based on the hash value, determining the number of character string bits, and further generating a target character string and determining a character string interval based on the number of character string bits;
And generating a ciphertext file based on the second encrypted data, the character string interval and the target character string.
4. The method of claim 3, wherein the generating a ciphertext file based on the second encrypted data, the string interval, and the target string comprises:
performing remainder calculation on the second encrypted data to obtain a remainder calculation result, and further generating first transformed encrypted data based on the remainder calculation result and the character string interval;
adding characters in the target character string to the first transformation encrypted data based on the character string interval to obtain second transformation encrypted data;
a random number is generated, and a ciphertext file is generated based on the random number, the string interval, and the second transformed encrypted data.
5. The method of claim 4, wherein the generating a ciphertext file based on the random number, the string interval, and the second transformed encrypted data comprises:
performing a data flip operation on the second transformed encrypted data based on the random number to generate third transformed encrypted data;
generating a random string according to the random number, further adding the random string to the tail of the third transformation encrypted data, and adding the random number and the character string interval to the head of the third transformation encrypted data;
Acquiring a sequence number of an analysis rule, and further adding the sequence number to the tail of the third transformation encrypted data to generate fourth transformation encrypted data;
and obtaining the ciphertext file based on the fourth transformed encrypted data.
6. The method of claim 2, wherein the obtaining historical user information comprises:
and acquiring original user information, masking the original user information to obtain historical user information and acquiring the historical user information.
7. The method of claim 2, wherein the obtaining the successfully matched file comprises:
and searching whether a character string matched with the encryption retrieval condition exists in the ciphertext file, if so, traversing a byte array of the ciphertext file to obtain a matching substring list, and differencing each element in the matching substring list with the ciphertext corresponding to the user identifier to obtain a successfully matched file, and if not, returning matching failure information.
8. A data query device, comprising:
the receiving unit is configured to receive the data query request and acquire the corresponding terminal identification and the search condition;
The verification unit is configured to determine a corresponding ciphertext file according to the retrieval condition, and further perform access right verification according to the ciphertext file and the terminal identifier;
an encryption unit configured to invoke a local encryption key to encrypt the search condition in response to success of the access right verification, generating an encrypted search condition;
the matching unit is configured to match the encryption retrieval condition with the ciphertext file, and obtain a successfully matched file in response to successful matching of the file existing in the ciphertext file and the encryption retrieval condition;
and the decryption unit is configured to call a local decryption key to decrypt the successfully matched file to obtain query result data.
9. A data querying electronic device, comprising:
one or more processors;
storage means for storing one or more programs,
when executed by the one or more processors, causes the one or more processors to implement the method of any of claims 1-7.
10. A computer readable medium, on which a computer program is stored, characterized in that the program, when being executed by a processor, implements the method according to any of claims 1-7.
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202310118592.6A CN116383867A (en) | 2023-01-30 | 2023-01-30 | Data query method, device, electronic equipment and computer readable medium |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202310118592.6A CN116383867A (en) | 2023-01-30 | 2023-01-30 | Data query method, device, electronic equipment and computer readable medium |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| CN116383867A true CN116383867A (en) | 2023-07-04 |
Family
ID=86972022
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202310118592.6A Pending CN116383867A (en) | 2023-01-30 | 2023-01-30 | Data query method, device, electronic equipment and computer readable medium |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN116383867A (en) |
Cited By (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN116846685A (en) * | 2023-08-30 | 2023-10-03 | 中通服建设有限公司 | Remote access method and system for medical information security |
| CN117650944A (en) * | 2024-01-25 | 2024-03-05 | 中国信息通信研究院 | Industrial Internet identification analysis method, system, electronic equipment and storage medium |
-
2023
- 2023-01-30 CN CN202310118592.6A patent/CN116383867A/en active Pending
Cited By (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN116846685A (en) * | 2023-08-30 | 2023-10-03 | 中通服建设有限公司 | Remote access method and system for medical information security |
| CN116846685B (en) * | 2023-08-30 | 2023-11-10 | 中通服建设有限公司 | Remote access method and system for medical information security |
| CN117650944A (en) * | 2024-01-25 | 2024-03-05 | 中国信息通信研究院 | Industrial Internet identification analysis method, system, electronic equipment and storage medium |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US8694467B2 (en) | Random number based data integrity verification method and system for distributed cloud storage | |
| CN113347206B (en) | Network access method and device | |
| US20140172830A1 (en) | Secure search processing system and secure search processing method | |
| CN113179323B (en) | HTTPS request processing method, device and system for load balancing equipment | |
| CN108923925B (en) | Data storage method and device applied to block chain | |
| CN111131278A (en) | Data processing method and device, computer storage medium and electronic equipment | |
| CN112689014B (en) | Double-full-work communication method, device, computer equipment and storage medium | |
| CN107040520B (en) | Cloud computing data sharing system and method | |
| US8924725B2 (en) | Authenticated file handles for network file systems | |
| CN116383867A (en) | Data query method, device, electronic equipment and computer readable medium | |
| CN113610526A (en) | Data trust method and device, electronic equipment and storage medium | |
| CN112966287B (en) | Method, system, device and computer readable medium for acquiring user data | |
| CN109474616B (en) | Multi-platform data sharing method and device and computer readable storage medium | |
| CN110022207B (en) | Method, apparatus, device and computer readable medium for key management and data processing | |
| CN117539927A (en) | Encrypted data fuzzy query method and device and electronic equipment | |
| CN112565156B (en) | Information registration method, device and system | |
| CN113746916A (en) | Block chain-based third-party service providing method, system and related node | |
| CN113761566A (en) | Data processing method and device | |
| KR102517001B1 (en) | System and method for processing digital signature on a blockchain network | |
| CN114840739B (en) | Information retrieval method, device, electronic equipment and storage medium | |
| CN114826729B (en) | Data processing method, page updating method and related hardware | |
| CN115589316A (en) | Data encryption transmission method and device, electronic equipment and storage medium | |
| CN115567263A (en) | Data transmission management method, data processing method and device | |
| JP2005222488A (en) | User authentication system, information distribution server and user authentication method | |
| CN118690412B (en) | Data access method, device, electronic equipment and computer readable medium |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination |