CN108923925B - Data storage method and device applied to block chain - Google Patents
Data storage method and device applied to block chain Download PDFInfo
- Publication number
- CN108923925B CN108923925B CN201810650431.0A CN201810650431A CN108923925B CN 108923925 B CN108923925 B CN 108923925B CN 201810650431 A CN201810650431 A CN 201810650431A CN 108923925 B CN108923925 B CN 108923925B
- Authority
- CN
- China
- Prior art keywords
- data
- terminal
- public key
- stored
- storage
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Active
Links
Images
Classifications
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/30—Public key, i.e. encryption algorithm being computationally infeasible to invert or user's encryption keys not requiring secrecy
- H04L9/3006—Public key, i.e. encryption algorithm being computationally infeasible to invert or user's encryption keys not requiring secrecy underlying computational problems or public-key parameters
- H04L9/302—Public key, i.e. encryption algorithm being computationally infeasible to invert or user's encryption keys not requiring secrecy underlying computational problems or public-key parameters involving the integer factorization problem, e.g. RSA or quadratic sieve [QS] schemes
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/12—Applying verification of the received information
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/06—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols the encryption apparatus using shift registers or memories for block-wise or stream coding, e.g. DES systems or RC4; Hash functions; Pseudorandom sequence generators
- H04L9/0643—Hash functions, e.g. MD5, SHA, HMAC or f9 MAC
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/08—Key distribution or management, e.g. generation, sharing or updating, of cryptographic keys or passwords
- H04L9/0816—Key establishment, i.e. cryptographic processes or cryptographic protocols whereby a shared secret becomes available to two or more parties, for subsequent use
- H04L9/0819—Key transport or distribution, i.e. key establishment techniques where one party creates or otherwise obtains a secret value, and securely transfers it to the other(s)
- H04L9/0822—Key transport or distribution, i.e. key establishment techniques where one party creates or otherwise obtains a secret value, and securely transfers it to the other(s) using key encryption key
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/32—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials
- H04L9/3236—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials using cryptographic hash functions
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/32—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials
- H04L9/3247—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials involving digital signatures
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Computing Systems (AREA)
- Theoretical Computer Science (AREA)
- Power Engineering (AREA)
- Computer Hardware Design (AREA)
- General Engineering & Computer Science (AREA)
- Storage Device Security (AREA)
Abstract
The embodiment of the application discloses a data storage method and device applied to a block chain. One embodiment of the data storage method applied to the block chain includes: receiving a data storage request sent by a first terminal, wherein the data storage request comprises a public key of the first terminal and data to be stored; determining whether the following set of storage conditions is satisfied: the pre-stored registration public key set comprises the public key of the first terminal; the data to be stored is valid data; in response to determining that the set of storage conditions is satisfied, storing the data to be stored. The embodiment can reduce the risk of abnormal data in the stored data and the risk of data tampering, and improve the safety of the stored data.
Description
Technical Field
The embodiment of the application relates to the technical field of wireless communication, in particular to a data storage method and device.
Background
With the continuous development of internet technology, networks have become an important way for users to obtain information, and meanwhile great convenience is brought to the users.
In the existing information sharing technology, a partially open information sharing platform is usually provided, and a user can store data in the information sharing platform or read required data from the information sharing platform.
Disclosure of Invention
The embodiment of the application provides a data storage method and device.
In a first aspect, an embodiment of the present application provides a data storage method applied to a block chain, including: receiving a data storage request sent by a first terminal, wherein the data storage request comprises a public key of the first terminal and data to be stored; determining whether the following set of storage conditions is satisfied: the pre-stored registration public key set comprises the public key of the first terminal; the data to be stored is valid data; in response to determining that the set of storage conditions is satisfied, storing the data to be stored.
In some embodiments, before receiving the data storage request sent by the first terminal, the method further comprises: receiving a public key registration request sent by the first terminal, wherein the public key registration request comprises a public key of the first terminal; encrypting the public key of the first terminal; and adding the encrypted public key to the registration public key set, and sending the encrypted public key to the second terminal.
In some embodiments, before receiving the data storage request sent by the first terminal, the method further comprises: receiving a public key registration request sent by a first terminal; generating a public key and a private key pair based on the public key registration request; sending the generated public key and private key pair to the first terminal, and encrypting the generated public key; and adding the encrypted public key to the registration public key set, and sending the encrypted public key to the second terminal.
In some embodiments, the data storage request further comprises a digital signature; and whether the determination satisfies the following set of storage conditions, including: decrypting and verifying the digital signature by using the public key of the first terminal to determine whether the digital signature is valid; in response to determining that the digital signature is valid, determining that the data to be stored is valid data.
In some embodiments, the data storage request further includes a storage data identification; and in response to determining that the set of storage conditions is satisfied, storing data to be stored, including: encrypting the storage data identification by using the public key of the first terminal; taking the encrypted storage data identification as a primary key word of the data to be stored, and storing the encrypted storage data identification; and in response to the determination that the storage is successful, returning information of successful storage to the first terminal, and sending the storage data identifier to the second terminal.
In some embodiments, the method further comprises: receiving a data access request sent by the second terminal, wherein the data access request comprises a public key of the second terminal, a held access public key and a storage data identifier of data requested to be accessed; determining whether the following set of access conditions are satisfied: the pre-stored registration public key set comprises a public key of the second terminal; the held access public key is the public key of the first terminal; in response to determining that the set of access conditions is satisfied, encrypting the stored data identifier of the requested access data with the public key of the first terminal, and determining whether the stored data identifier of the encrypted requested access data is the same as the encrypted stored data identifier stored by the first terminal; and in response to determining that the storage data identification of the encrypted access-requested data is the same as the encrypted storage data identification stored by the first terminal, sending the data stored by the first terminal to the second terminal.
In a second aspect, an embodiment of the present application provides a data storage device applied to a block chain, including: the data storage device comprises a receiving unit, a storing unit and a storing unit, wherein the receiving unit is configured to receive a data storage request sent by a first terminal, and the data storage request comprises a public key of the first terminal and data to be stored; a determination unit configured to determine whether the following storage condition group is satisfied: the pre-stored registration public key set comprises the public key of the first terminal; the data to be stored is valid data; a storage unit configured to store data to be stored in response to determining that the set of storage conditions is satisfied.
In some embodiments, the apparatus further comprises: a public key registration request unit configured to receive a public key registration request sent by the first terminal, the public key registration request including a public key of the first terminal; an encryption unit configured to encrypt a public key of the first terminal; an adding unit configured to add the encrypted public key to the set of registration public keys and to transmit the encrypted public key to the second terminal.
In some embodiments, the apparatus further comprises: a public key registration request unit configured to receive a public key registration request transmitted by a first terminal; a generation unit configured to generate a public key and a private key pair based on the public key registration request; an encryption unit configured to transmit the generated pair of the public key and the private key to the first terminal and encrypt the generated public key; an adding unit configured to add the encrypted public key to the registration public key set, and to transmit the encrypted public key to the second terminal.
In some embodiments, the data storage request further comprises a digital signature; and the determining unit is further configured to: the public key of the first terminal is used for decrypting and verifying the digital signature to determine whether the digital signature is valid; in response to determining that the digital signature is valid, determining that the data to be stored is valid data.
In some embodiments, the data storage request further includes a storage data identification; and the adding unit is further configured to: encrypting the storage data identification by using the public key of the first terminal; taking the encrypted storage data identification as a primary key word of the data to be stored, and storing the encrypted storage data identification; and in response to the determination that the storage is successful, returning information of successful storage to the first terminal, and sending the storage data identifier to the second terminal.
In some embodiments, the apparatus is further configured to: receiving a data access request sent by the second terminal, wherein the data access request comprises a public key of the second terminal, a held access public key and a storage data identifier of data requested to be accessed; determining whether the following set of access conditions are satisfied: the pre-stored registration public key set comprises a public key of the second terminal; the held access public key is the public key of the first terminal; in response to determining that the set of access conditions is satisfied, encrypting the stored data identifier of the requested access data with the public key of the first terminal, and determining whether the stored data identifier of the encrypted requested access data is the same as the encrypted stored data identifier stored by the first terminal; and in response to determining that the stored data identification of the encrypted access-requested data is the same as the encrypted stored data identification stored by the first terminal, sending the data stored by the first terminal to the second terminal.
In a third aspect, an embodiment of the present application provides a first terminal device, where the first terminal device includes: one or more processors; a storage device having one or more programs stored thereon; when the one or more programs are executed by the one or more processors, the one or more processors are caused to implement the method as described in any implementation of the first aspect.
In a fourth aspect, the present application provides a computer-readable medium, on which a computer program is stored, which, when executed by a processor, implements the method as described in any implementation manner of the first aspect.
According to the data storage method and device provided by the embodiment of the application, the data storage request sent by the first terminal is received, whether the data storage request of the first terminal meets the storage condition group or not is determined, and finally the data to be stored is stored under the condition that the data storage request of the first terminal meets the storage condition group. The data storage method can reduce the risk of abnormal data (such as virus data) in the stored data and the risk of data tampering, and improve the safety of the stored data.
Drawings
Other features, objects and advantages of the present application will become more apparent upon reading of the following detailed description of non-limiting embodiments thereof, made with reference to the accompanying drawings in which:
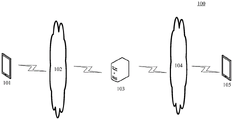
FIG. 1 is an exemplary system architecture diagram to which one embodiment of the present application may be applied;
FIG. 2 is a flow diagram for one embodiment of a data storage method applied to a blockchain in accordance with the present application;
FIG. 3 is a schematic diagram of an application scenario of the data storage method provided in FIG. 2 as applied to a blockchain;
FIG. 4 is a flow diagram of yet another embodiment of a data storage method applied to a blockchain in accordance with the present application;
FIG. 5 is a flow diagram for one embodiment of a data storage device applied to a blockchain in accordance with the present application;
FIG. 6 is a schematic block diagram of a computer system suitable for use in implementing embodiments of the present application.
Detailed Description
The present application will be described in further detail with reference to the drawings and examples. It is to be understood that the specific embodiments described herein are merely illustrative of the invention and are not to be construed as limiting the invention. It should be noted that, for convenience of description, only the portions related to the related invention are shown in the drawings.
It should be noted that, in the present application, the embodiments and features of the embodiments may be combined with each other without conflict. The present application will be described in detail below with reference to the accompanying drawings in conjunction with embodiments.
Fig. 1 illustrates an exemplary system architecture 100 to which embodiments of the data storage method applied to blockchains of the present application may be applied.
As shown in fig. 1, the system architecture 100 may include a first terminal device 101, networks 102, 104, a blockchain 103, and a second terminal device 105. Network 102 may be used to provide a medium for a communication link between first terminal device 101 and blockchain 103, and network 104 may be used to provide a medium for a communication link between blockchain 103 and second terminal device 105. The networks 102, 104 may include various connection types, such as wired, wireless communication links, or fiber optic cables, among others. A user may use a first terminal device 101 and a second terminal device 105 to interact with the blockchain 103 over networks 102, 104, respectively, to receive or send messages, etc. Various communication client applications, such as a wireless access point connection application, a search application, a data storage application, a data reading application, and the like, may be installed on the first terminal device 101 and the second terminal device 105.
The first terminal apparatus 101 and the second terminal apparatus 105 may be hardware or software. When the first terminal device 101 and the second terminal device 105 are hardware, they may be various electronic devices supporting connection with a wireless access point, including but not limited to a smart phone, a tablet computer, a laptop portable computer, a desktop computer, and the like. When the first terminal apparatus 101 and the second terminal apparatus 105 are software, they may be installed in the electronic apparatuses listed above. It may be implemented as multiple pieces of software or software modules, or as a single piece of software or software module. And is not particularly limited herein.
The first terminal device 101 and the second terminal device 104 may access the block chain as block link points in a wired connection or a wireless connection manner. Meanwhile, when the first terminal device 101 is a node device that stores data to a blockchain and the second terminal device 105 is a node device that acquires data stored in the first terminal device 101 from the blockchain, the second terminal device 105 may acquire data from the first terminal device 101 through the blockchain.
The blockchain 103 may provide various services, for example, may verify a data storage request received by the first terminal device 101, and store the requested data after determining that the first terminal device 101 and the requested data satisfy the storage condition. For another example, after verifying the received data access request of the second terminal device 104, the blockchain 103 may send the data requested to be accessed by the second terminal device 104 to the second terminal device 104 when the access condition set is satisfied.
It should be noted that the blockchain 103 may be hardware or software. When the blockchain 103 is hardware, a clustered service may be implemented, or a single service may be implemented. When the server is software, it may be implemented as multiple pieces of software or software modules (e.g., to provide distributed services), or as a single piece of software or software module. And is not particularly limited herein.
It should be noted that the data storage method provided in the embodiment of the present application may be executed by the block chain 103. Accordingly, data storage devices are typically provided in the block chain 103.
At this time, the process of the present invention,
it should be understood that the number of first terminal devices, second terminal devices, networks and block chains in fig. 1 is merely illustrative. There may be any number of first terminal devices, second terminal devices, networks, and blockchains, as desired for the implementation.
With continued reference to FIG. 2, a flow 200 of one embodiment of a data storage method applied to a blockchain in accordance with the present application is illustrated. The method comprises the following steps:
In this embodiment, the execution subject of the data storage method (for example, the blockchain 103 shown in fig. 1) may receive the data storage request sent by the first terminal through a wired connection or a wireless connection. The execution subject may be a data storage server, and the data storage server may store data of at least one first terminal. Here, the first terminal may be a terminal that transmits a data storage request to the execution main body. Therefore, the execution main body may receive the data storage request transmitted by one first terminal, or may receive the data storage requests transmitted by two or three first terminals at the same time, which is not limited herein and is set according to the needs of the application scenario.
In this embodiment, the execution principal may receive a data storage request including a public key of the first terminal and data to be stored. The public key of the first terminal may be generated locally for the first terminal, or may be obtained from the execution subject for the first terminal. The data to be stored may be the data content itself, or may be a data digest generated by performing hash calculation on the data content.
As an example, the first terminal may first locally generate a public key and private key pair using an encryption algorithm (e.g., JAVA RSA encryption algorithm). Then, based on a preset protocol (e.g., a connection protocol of the first terminal with the execution principal, a transmission protocol, etc.), the first terminal may send the locally generated public key to the execution principal so as to execute principal storage. When the execution main body determines that the preset protocol is correct and the public key meets a preset format (for example, a preset public key character length and a preset algorithm for generating the public key), the public key of the first terminal may be stored in the registration public key set. When the execution main body is successfully stored, the public key of the first terminal is indicated to be registered in the execution main body. In the data storage, the first terminal may transmit the public key registered in the execution principal and the data to be stored to the execution principal.
As an example, when the data requested to be stored by the first terminal is a block in a block chain, the execution subject may be the block chain. Here, the blockchain is a novel data storage device of computer technologies such as distributed data storage, point-to-point transmission, consensus mechanism, encryption algorithm, and the like. The blockchain may include, but is not limited to, at least one of: private chain, federation chain, license chain. The federation chain is taken as an example for illustration.
The alliance chain is a block chain which is only opened for specific group members, and a plurality of pre-selected first terminals are appointed in the alliance chain to be used as nodes of the alliance chain to store data in the alliance chain. Here, the first terminal may join the federation chain in an authorization permission manner according to an authorization permission mechanism preset by an Application Programming Interface (API) in the federation chain, so as to be able to add data stored in the federation chain. Therefore, the first terminal is a node capable of storing data into the federation chain. Here, the manner of authorizing the license may include, for example, authorizing the license to the first terminal according to a preset condition (e.g., meeting a certain industry consensus standard, obtaining an industry certificate, etc.). After the first terminal is authorized to be licensed, the federation chain may generate a public key and a private key using an encryption algorithm, store the generated public key in a registration public key set, and send the generated public key and private key pair to the first terminal authorized to be licensed. When the first terminal stores data to a block in the federation chain, the public key of the federation chain authorization permission and the data to be stored need to be sent to the federation chain.
In this embodiment, when the execution main body receives the public key of the first terminal, the public key of the first terminal may be compared with public keys in a pre-stored registration public key set, so as to determine whether the public key of the first terminal is included in the registration public key set.
In this embodiment, the execution main body further needs to verify the received data to be stored sent by the first terminal, so as to determine whether the data to be stored is valid data. Here, the valid data may include, for example, data of the data to be stored during a valid period. Specifically, the execution body may store data in a preset time period sent by the first terminal. The data to be stored typically includes encrypted time stamp information. The execution main body may decrypt the encrypted timestamp information using a public key of the first terminal or a key agreed with the first terminal, and determine whether the data to be stored is valid data according to the decrypted timestamp information. Here, the encrypted key may be, for example, a private key corresponding to the public key of the first terminal, or may be a key of another scheme agreed with the execution principal.
In this embodiment, when it is determined that the pre-stored registration public key set includes the public key of the first terminal and the data to be stored is valid data, it may be determined that the first terminal and the data stored by the first terminal satisfy the preset storage condition.
In some optional implementations of this embodiment, the data storage request of the first terminal further includes a digital signature. The executing body can decrypt and verify the digital signature by using the public key of the first terminal, thereby determining whether the digital signature is valid. And when the digital signature is valid, determining the data to be stored as valid data.
Specifically, the digital signature is generally obtained by the first terminal performing hash calculation on data to be stored by using a hash function (for example, SHA-256 algorithm) to generate a digest of the data to be stored, and then encrypting the generated digest by using a private key of the first terminal. Therefore, the executing body may perform hash calculation on the data to be stored sent by the first terminal by using the same calculation method as that of the first terminal, and generate a digest of the data to be stored sent by the first terminal. Then, the executing body decrypts the data signature sent by the first terminal by using the public key of the first terminal to obtain the abstract of the data to be stored. Finally, the executing entity may compare the digest obtained by decrypting the digital signature of the first terminal with the calculated digest, and determine whether the two are the same. When the two are the same, it may be determined that the digital signature transmitted by the first terminal is valid. Thus, the execution subject may determine that the data to be stored is valid data.
In some optional implementations of this embodiment, the set of registration public keys further includes an identifier of the first terminal stored in correspondence with the public key of the first terminal. In order to facilitate to confirm whether the first terminal has the authority to store the data, the main body may further compare the identifier of the first terminal with identifiers in a preset identifier set to determine whether the first terminal has the authority to store the data.
And step 203, responding to the determination that the storage condition group is met, and storing the data to be stored.
In this embodiment, when the executing entity determines that the pre-stored registration public key set includes the public key of the first terminal and the data to be stored is valid data, the data to be stored may be stored. Here, the execution body may store the data content itself, or may store a data digest obtained by performing hash calculation on the data content.
With continued reference to fig. 3, fig. 3 is a schematic diagram of an application scenario 300 of the data storage method applied to the blockchain provided in fig. 2. In the application scenario of fig. 3, a user sends a data storage request for "financial reports" to a server 302 via a handset 301. The "financial report" storage request includes a public key 303 generated by the user through key calculation by the mobile phone 301 and the "financial report" data 304. Next, the server 302 compares the public key 303 sent by the mobile phone 301 with public keys in a pre-stored registration public key set, and determines that the registration public key set includes the public key 303. The server 302 also needs to validate the "financial reports" data 304 to determine that the "financial reports" data 304 is valid data. Finally, the server 302 stores the "financial report" data when determining that the pre-stored registration public key set includes the public key 303 sent by the mobile phone 301 and the "financial report" data 304 as valid data.
The data storage method provided by the embodiment of the application comprises the steps of firstly receiving a data storage request sent by a first terminal, then determining whether the data storage request of the first terminal meets a storage condition group, and finally storing data to be stored under the condition that the data storage request of the first terminal meets the storage condition group. The data storage method can reduce the risk of abnormal data (such as virus data) in the stored data and the risk of data tampering, and improve the safety of the stored data, thereby providing safety guarantee for the data sharing platform.
With further reference to fig. 4, a flow 400 of yet another embodiment of a data storage method applied to a blockchain in accordance with the present application is illustrated. The method comprises the following steps:
In this embodiment, the execution subject of the data storage method (for example, the blockchain 103 shown in fig. 1) may receive the public key registration request sent by the first terminal through a wired connection or a wireless connection. Here, the execution subject may be a data storage server, and the data storage server may store data of at least one first terminal. The public key requested to be registered in the public key registration request may be generated locally by the first terminal (for example, the first terminal device 101 shown in fig. 1), or may be generated by the execution subject.
As an implementation manner, the first terminal may first locally generate a public key and a private key pair by using an encryption algorithm (for example, JAVA RSA encryption algorithm). Then, based on a preset protocol (e.g., a connection protocol of the first terminal and the execution principal, a transmission protocol, etc.), the execution principal may receive a public key locally generated by the first terminal to register on the execution principal.
As another implementation manner, when the execution subject of the data storage method is a block chain, the first terminal may add the block chain in an authorized manner through an authorized permission mechanism preset in the block chain, so that data may be stored in the block chain. The authorization may include, for example, authorizing the first terminal according to a preset condition (e.g., meeting a certain industry consensus standard, obtaining an industry certificate, etc.). When the first terminal is authorized to be licensed, the blockchain may generate a public key and a private key pair using an encryption algorithm. And then, storing the generated public key to a registration public key set, and sending the generated public key and the private key together to the first terminal authorized to be licensed. Thus, the first terminal requesting to join the blockchain may act as sending a public key registration request to the blockchain.
In this embodiment, after receiving the public key registration request sent by the first terminal, the executing entity may encrypt the public key sent by the first terminal or the locally generated public key by using a preset encryption algorithm of the prior art.
In this embodiment, the execution principal may add the encrypted public key to the registration public key set, and then send the public key of the first terminal to the second terminal. Therefore, the second terminal can carry the public key of the first terminal when accessing the data stored in the first terminal to the execution main body.
In this embodiment, the execution subject of the data storage method (e.g., the blockchain 103 shown in fig. 1) may receive the data storage request sent by the first terminal through a wired connection or a wireless connection. Here, the first terminal may be a terminal that transmits a data storage request to the execution main body. Therefore, the execution main body may receive the data storage request sent by one first terminal, or may simultaneously receive the data storage requests sent by two or three first terminals, which is not limited herein and is set according to the needs of the application scenario.
In this embodiment, the executing entity may receive a data storage request including a public key of the first terminal, data to be stored, and a storage data identifier of the data to be stored. The public key of the first terminal may be generated locally by the first terminal, or may be obtained by the first terminal from the execution subject. The data to be stored may be the data content itself, or may be a data digest generated by performing hash calculation on the data content.
In this embodiment, when the execution main body receives the public key of the first terminal, the public key of the first terminal may be compared with public keys in a pre-stored registration public key set, so as to determine whether the public key of the first terminal is included in the registration public key set.
In this embodiment, the execution main body further needs to verify the received data to be stored sent by the first terminal, so as to determine whether the data to be stored is valid data. Here, the valid data may include, for example, data of the data to be stored in the valid period. Specifically, the execution body may store data in a preset time period sent by the first terminal. The data to be stored typically includes encrypted time stamp information. The execution main body may decrypt the encrypted timestamp information using a public key of the first terminal or a key agreed with the first terminal, and determine whether the data to be stored is valid data according to the decrypted timestamp information. Here, the encrypted key may be, for example, a private key corresponding to the public key of the first terminal, or may be a key of another scheme agreed with the execution agent.
In this embodiment, when it is determined that the pre-stored registration public key set includes the public key of the first terminal and the data to be stored are valid data, it may be determined that the first terminal and the data stored by the first terminal satisfy the preset condition.
In this embodiment, the storage data identifier is used to identify data to be stored, and may include, but is not limited to: the combination of the version number of the first terminal and the data storage number, the message header of the stored data, and the like. Specific formats of the data store identification may include, but are not limited to, at least one of: letters, symbols, combinations of letters and symbols, and the like.
In this embodiment, it is determined in step 405 whether the first terminal and the data requested to be stored by the first terminal satisfy the storage condition, and when it is determined that the first terminal and the data requested to be stored by the first terminal satisfy the storage condition, the execution main body may encrypt the identifier of the stored data by using a public key encryption algorithm (for example, a hash encryption algorithm, an RSA asymmetric encryption algorithm) using the public key of the first terminal.
In this embodiment, the primary key is one or more fields for uniquely identifying a record or data content. Here, the primary key may be used to uniquely identify data to be stored by the first terminal. Since the storage data identifier can be used to uniquely identify the data to be stored, the encrypted storage data identifier can be used as a primary key of the data to be stored. Therefore, the stored data can be searched after the encrypted stored data identification is searched and decrypted.
In this embodiment, the execution subject may store the data to be stored directly. Or storing the data abstract of the data to be stored after the hash calculation. The data to be stored may not be directly stored, and when there is another terminal that needs to access the data stored in the first terminal, the execution main body may establish a connection between the first terminal and the another terminal, so that the another terminal directly obtains the data from the first terminal.
And step 408, in response to determining that the storage is successful, returning information of successful storage to the first terminal, and sending the storage data identifier to the second terminal.
In this embodiment, after storing the encrypted storage data according to step 407, the execution main body may return information of successful storage to the first terminal in response to the condition that it is determined that storage is successful. Meanwhile, the execution main body can also send the encrypted storage data identifier to the second terminal.
In this embodiment, when the execution subject is a blockchain, the data requested to be stored by the first terminal is also the data shared in the blockchain. Therefore, the block chain only needs to store the encrypted storage data identifier. And simultaneously sending the encrypted storage data identifier to the second terminal. When the second terminal needs to access the data stored by the first terminal, the carried stored data identification can be provided to the block chain. The block chain can search the first terminal according to the stored data identifier, so that data can be directly obtained from the first terminal.
And step 409, receiving a data access request sent by the second terminal.
In this embodiment, the execution body may further receive a data access request sent by the second terminal according to the data requested to be stored by the first terminal and the encrypted stored data identifier sent to the second terminal, which are stored in step 408. Here, the data access request may include the public key of the second terminal, the held access public key, and the stored data identification of the data requested to be accessed.
In this embodiment, the public key of the second terminal may be locally generated by the second terminal, or may be generated by the execution subject and sent to the second terminal. The held access public key and the stored data identification of the requested access data are both sent by the executing entity to the second terminal in steps 403 and 408.
In this embodiment, when the execution main body receives the public key of the second terminal, the public key of the second terminal may be compared with public keys in a pre-stored registration public key set, so as to determine whether the public key of the second terminal is included in the registration public key set. Here, as for the method for generating the public key of the second terminal, reference may be made to the method for generating the public key and the private key by the first terminal shown in step 401, which is not described herein again.
In this embodiment, the executing entity further needs to verify the access public key held by the second terminal, and determine whether the access public key held by the second terminal is the public key of the first terminal storing the data accessed by the second terminal. Here, the execution subject may decrypt an access public key held by the second terminal. And then comparing the decrypted public key with the public key corresponding to the stored data identifier to determine whether the decrypted public key is the same as the public key corresponding to the stored data identifier. And in response to determining that the decrypted public key is the same as the public key corresponding to the stored data identifier, determining that the access public key held by the second terminal is the public key of the first terminal storing the data accessed by the second terminal.
In this embodiment, when the execution subject determines that the public key of the second terminal is included in the registration public key set and determines that the access public key held by the second terminal is the public key of the first terminal storing the data accessed by the second terminal, it is determined that the second terminal satisfies the access condition set.
And 411, in response to determining that the access condition group is met, encrypting the storage data identifier of the requested access data by using the public key of the first terminal, and determining whether the storage data identifier of the encrypted requested access data is the same as the encrypted storage data identifier stored by the first terminal.
In this embodiment, according to whether the second terminal meets the access condition set determined in step 410, when the execution subject determines that the access condition set is met, the public key of the first terminal may be used to perform encryption calculation on the stored data identifier of the requested access data through an existing public key encryption algorithm. The encrypted calculated stored data identification is then compared with the encrypted stored data identification stored in step 407 to determine if the two are the same.
And step 412, in response to determining that the storage data identifier of the encrypted data requested to be accessed is the same as the encrypted storage data identifier stored by the first terminal, sending the data stored by the first terminal to the second terminal.
In this embodiment, after the execution subject determines that the storage identifier of the requested access data is the same as the storage identifier of the data stored in the first terminal, the data stored in the first terminal may be directly sent to the second terminal.
As can be seen from fig. 4, unlike the embodiment shown in fig. 2, the embodiment adds a step of public key registration of the first terminal and a step of accessing data stored in the first terminal by the second terminal, thereby improving flexibility of interaction between terminals and between a terminal and an execution subject, and further improving security of data storage and data access.
With further reference to fig. 5, as an implementation of the method shown in the above figures, the present application provides an embodiment of a data storage apparatus applied to a block chain, where the embodiment of the apparatus corresponds to the embodiment of the method shown in fig. 2, and the apparatus may be applied to various electronic devices in particular.
As shown in fig. 5, the data storage device 500 applied to the block chain of the present embodiment includes: a receiving unit 501, a determining unit 502 and a storing unit 503. The receiving unit 501 is configured to receive a data storage request sent by a first terminal, where the data storage request includes a public key of the first terminal and data to be stored. A determining unit 502 configured to determine whether the following set of storage conditions is satisfied: the pre-stored registration public key set comprises the public key of the first terminal; the data to be stored is valid data. A storage unit 503 configured to store the data to be stored in response to determining that the set of storage conditions is satisfied.
In the present embodiment, the data storage device 500 applied to the block chain: the specific implementation of the receiving unit 501, the determining unit 502, and the storing unit 503 and the technical effects thereof can refer to the related descriptions of step 201, step 202, and step 203 in the corresponding embodiment of fig. 2, which are not repeated herein.
In some optional implementations of this embodiment, the data storage device 500 applied to the block chain further includes: a public key registration request unit (not shown) configured to receive a public key registration request transmitted by the first terminal, the public key registration request including a public key of the first terminal; an encryption unit (not shown) configured to encrypt a public key of the first terminal; an adding unit (not shown) configured to add the encrypted public key to the set of registration public keys and to send the encrypted public key to the second terminal.
In some optional implementations of this embodiment, the data storage device 500 applied to the block chain further includes: a public key registration request unit (not shown) configured to receive a public key registration request transmitted by the first terminal; a generation unit (not shown) configured to generate a public key and a private key pair based on the public key registration request; an encryption unit (not shown) configured to transmit the generated public and private key pair to the first terminal, and encrypt the generated public key; an adding unit (not shown) configured to add the encrypted public key to the set of registration public keys and to transmit the encrypted public key to the second terminal.
In some optional implementations of this embodiment, the data storage request further includes a digital signature; and the determining unit 502 is configured to: decrypting and verifying the digital signature by using the public key of the first terminal to determine whether the digital signature is valid; in response to determining that the digital signature is valid, determining that the data to be stored is valid data.
In some optional implementations of this embodiment, the data storage request further includes a storage data identifier; and the adding unit 503 is further configured to: encrypting the storage data identification by using the public key of the first terminal; taking the encrypted storage data identification as a primary key word of the data to be stored, and storing the encrypted storage data identification; and in response to the determination that the storage is successful, returning information of successful storage to the first terminal, and sending a storage data identifier to the second terminal.
In some optional implementations of the present embodiment, the data storage device 500 applied to the blockchain is further configured to: receiving a data access request sent by the second terminal, wherein the data access request comprises a public key of the second terminal, a held access public key and a storage data identifier of data requested to be accessed; determining whether the following set of access conditions is satisfied: the pre-stored registration public key set comprises a public key of the second terminal; the held access public key is the public key of the first terminal; in response to determining that the set of access conditions is satisfied, encrypting the stored data identifier of the requested access data with the public key of the first terminal, and determining whether the stored data identifier of the encrypted requested access data is the same as the encrypted stored data identifier stored by the first terminal; and in response to determining that the storage data identification of the encrypted access-requested data is the same as the encrypted storage data identification stored by the first terminal, sending the data stored by the first terminal to the second terminal.
Referring now to FIG. 6, shown is a block diagram of a computer system 600 suitable for use in implementing the first terminal device of the embodiments of the present application. The first terminal device shown in fig. 6 is only an example, and should not bring any limitation to the functions and the scope of use of the embodiments of the present application.
As shown in fig. 6, the computer system 600 includes a Central Processing Unit (CPU) 601 that can perform various appropriate actions and processes according to a program stored in a Read Only Memory (ROM) 602 or a program loaded from a storage section 608 into a Random Access Memory (RAM) 603. In the RAM 603, various programs and data necessary for the operation of the system 600 are also stored. The CPU 601, ROM 602, and RAM 603 are connected to each other via a bus 604. An input/output (I/O) interface 605 is also connected to bus 604.
The following components are connected to the I/O interface 605: an input portion 606 including a keyboard, a mouse, and the like; an output portion 607 including a display such as a Cathode Ray Tube (CRT), a Liquid Crystal Display (LCD), and the like, and a speaker; a storage section 608 including a hard disk and the like; and a communication section 609 including a network interface card such as a LAN card, a modem, or the like. The communication section 609 performs communication processing via a network such as the internet. The driver 610 is also connected to the I/O interface 605 as needed. A removable medium 611 such as a magnetic disk, an optical disk, a magneto-optical disk, a semiconductor memory, or the like is mounted on the drive 610 as necessary, so that a computer program read out therefrom is mounted in the storage section 608 as necessary.
In particular, according to an embodiment of the present disclosure, the processes described above with reference to the flowcharts may be implemented as computer software programs. For example, embodiments of the present disclosure include a computer program product comprising a computer program embodied on a computer readable medium, the computer program comprising program code for performing the method illustrated in the flow chart. In such an embodiment, the computer program may be downloaded and installed from a network through the communication section 609, and/or installed from the removable medium 611. The computer program performs the above-described functions defined in the method of the present application when executed by a Central Processing Unit (CPU) 601. It should be noted that the computer readable medium described herein can be a computer readable signal medium or a computer readable medium or any combination of the two. A computer readable medium may be, for example, but not limited to, an electronic, magnetic, optical, electromagnetic, infrared, or semiconductor system, apparatus, or device, or any combination of the foregoing. More specific examples of the computer readable medium may include, but are not limited to: an electrical connection having one or more wires, a portable computer diskette, a hard disk, a Random Access Memory (RAM), a read-only memory (ROM), an erasable programmable read-only memory (EPROM or flash memory), an optical fiber, a portable compact disc read-only memory (CD-ROM), an optical storage device, a magnetic storage device, or any suitable combination of the foregoing. In the context of this application, a computer readable medium may be any tangible medium that can contain, or store a program for use by or in connection with an instruction execution system, apparatus, or device. In this application, however, a computer readable signal medium may include a propagated data signal with computer readable program code embodied therein, for example, in baseband or as part of a carrier wave. Such a propagated data signal may take many forms, including, but not limited to, electro-magnetic, optical, or any suitable combination thereof. A computer readable signal medium may also be any computer readable medium that is not a computer readable medium and that can communicate, propagate, or transport a program for use by or in connection with an instruction execution system, apparatus, or device. Program code embodied on a computer readable medium may be transmitted using any appropriate medium, including but not limited to: wireless, wire, fiber optic cable, RF, etc., or any suitable combination of the foregoing.
Computer program code for carrying out operations for aspects of the present application may be written in any combination of one or more programming languages, including an object oriented programming language such as Java, smalltalk, C + + or the like and conventional procedural programming languages, such as the "C" programming language or similar programming languages. The program code may execute entirely on the user's computer, partly on the user's computer, as a stand-alone software package, partly on the user's computer and partly on a remote computer or entirely on the remote computer or server. In the latter scenario, the remote computer may be connected to the user's computer through any type of network, including a Local Area Network (LAN) or a Wide Area Network (WAN), or the connection may be made to an external computer (for example, through the Internet using an Internet service provider).
The flowchart and block diagrams in the figures illustrate the architecture, functionality, and operation of possible implementations of systems, methods and computer program products according to various embodiments of the present application. In this regard, each block in the flowchart or block diagrams may represent a module, segment, or portion of code, which comprises one or more executable instructions for implementing the specified logical function(s). It should also be noted that, in some alternative implementations, the functions noted in the block may occur out of the order noted in the figures. For example, two blocks shown in succession may, in fact, be executed substantially concurrently, or the blocks may sometimes be executed in the reverse order, depending upon the functionality involved. It will also be noted that each block of the block diagrams and/or flowchart illustration, and combinations of blocks in the block diagrams and/or flowchart illustration, can be implemented by special purpose hardware-based systems which perform the specified functions or acts, or combinations of special purpose hardware and computer instructions.
The units described in the embodiments of the present application may be implemented by software or hardware. The described units may also be provided in a processor, and may be described as: a processor includes a receiving unit, a determining unit, and a storing unit. The names of these units do not in some cases constitute a limitation to the unit itself, and for example, the receiving unit may also be described as a "unit that receives a data storage request transmitted by the first terminal".
As another aspect, the present application also provides a computer-readable medium, which may be contained in the first terminal device described in the above embodiments; or may be separate and not incorporated into the first terminal device. The computer readable medium carries one or more programs which, when executed by the first terminal device, cause the first terminal device to: receiving a data storage request sent by a first terminal, wherein the data storage request comprises a public key of the first terminal and data to be stored; determining whether the following set of storage conditions is satisfied: the pre-stored registration public key set comprises the public key of the first terminal; the data to be stored is valid data; in response to determining that the set of storage conditions is satisfied, storing the data to be stored.
The foregoing description is only exemplary of the preferred embodiments of the application and is illustrative of the principles of the technology employed. It will be appreciated by those skilled in the art that the scope of the invention herein disclosed is not limited to the particular combination of features described above, but also encompasses other arrangements formed by any combination of the above features or their equivalents without departing from the spirit of the invention. For example, the above features may be replaced with (but not limited to) features having similar functions disclosed in the present application.
Claims (12)
1. A data storage method applied to a blockchain, comprising:
receiving a data storage request sent by a first terminal, wherein the data storage request comprises a public key of the first terminal and data to be stored;
determining whether the following set of storage conditions is satisfied: the pre-stored registration public key set comprises a public key of the first terminal; the data to be stored is valid data;
in response to determining that the set of storage conditions is satisfied, storing data to be stored;
determining whether the following set of storage conditions is satisfied, including: decrypting the timestamp information in the data to be stored by adopting a pre-agreed key, and determining whether the data to be stored is valid data according to the decrypted timestamp information;
receiving a data access request sent by a second terminal, wherein the data access request comprises a public key of the second terminal, a held access public key and a storage data identifier of data requested to be accessed;
determining whether the following set of access conditions are satisfied: the pre-stored registration public key set comprises a public key of the second terminal; the held access public key is the public key of the first terminal;
in response to determining that the set of access conditions is satisfied, encrypting a stored data identifier of the requested access data with a public key of the first terminal, determining whether the stored data identifier of the encrypted requested access data is the same as the encrypted stored data identifier stored by the first terminal;
and in response to determining that the storage data identification of the encrypted access-requested data is the same as the encrypted storage data identification stored by the first terminal, sending the data stored by the first terminal to the second terminal.
2. The method of claim 1, wherein prior to receiving the data storage request sent by the first terminal, the method further comprises:
receiving a public key registration request sent by the first terminal, wherein the public key registration request comprises a public key of the first terminal;
encrypting the public key of the first terminal;
and adding the encrypted public key to the registration public key set, and sending the encrypted public key to the second terminal.
3. The method of claim 1, wherein prior to receiving the data storage request sent by the first terminal, the method further comprises:
receiving a public key registration request sent by the first terminal;
generating a public key and a private key pair based on the public key registration request;
sending the generated public key and private key pair to the first terminal, and encrypting the generated public key;
and adding the encrypted public key to the registration public key set, and sending the encrypted public key to the second terminal.
4. The method of one of claims 1-3, wherein the data storage request further comprises a digital signature; and
the determining whether the following set of storage conditions is satisfied includes:
decrypting and verifying the digital signature by using the public key of the first terminal to determine whether the digital signature is valid;
in response to determining that the digital signature is valid, determining that the data to be stored is valid data.
5. The method of claim 2 or 3, wherein the data storage request further comprises a storage data identification; and
in response to determining that the set of storage conditions is satisfied, storing data to be stored, including:
encrypting the storage data identification by using the public key of the first terminal;
taking the encrypted storage data identification as a primary key word of the data to be stored, and storing the encrypted storage data identification;
and in response to the determination that the storage is successful, returning information of successful storage to the first terminal, and sending the storage data identifier to the second terminal.
6. A data storage device applied to a blockchain, comprising:
the data storage device comprises a receiving unit, a storing unit and a storing unit, wherein the receiving unit is configured to receive a data storage request sent by a first terminal, and the data storage request comprises a public key of the first terminal and data to be stored;
a determination unit configured to determine whether the following storage condition sets are satisfied: the pre-stored registration public key set comprises the public key of the first terminal; the data to be stored is valid data;
a storage unit configured to store data to be stored in response to determining that the set of storage conditions is satisfied;
the determination unit is further configured to: decrypting the timestamp information in the data to be stored by adopting a pre-agreed key, and determining whether the data to be stored is valid data according to the decrypted timestamp information;
the apparatus is further configured to:
receiving a data access request sent by a second terminal, wherein the data access request comprises a public key of the second terminal, a held access public key and a storage data identifier of data requested to be accessed;
determining whether the following set of access conditions is satisfied: the pre-stored registration public key set comprises a public key of the second terminal; the held access public key is the public key of the first terminal;
in response to determining that the set of access conditions is satisfied, encrypting a stored data identifier of the requested access data with a public key of the first terminal, determining whether the stored data identifier of the encrypted requested access data matches the encrypted stored data identifier stored by the first terminal;
and in response to determining that the storage data identification of the encrypted access-requested data matches the encrypted storage data identification stored by the first terminal, sending the data stored by the first terminal to the second terminal.
7. The apparatus of claim 6, wherein the apparatus further comprises:
a public key registration request unit configured to receive a public key registration request sent by the first terminal, the public key registration request including a public key of the first terminal;
an encryption unit configured to encrypt a public key of the first terminal;
an adding unit configured to add the encrypted public key to the registration public key set and to transmit the encrypted public key to the second terminal.
8. The apparatus of claim 6, wherein the apparatus further comprises:
a public key registration request unit configured to receive a public key registration request sent by the first terminal;
a generation unit configured to generate a public key and a private key pair based on the public key registration request;
an encryption unit configured to transmit the generated public key and private key pair to the first terminal and encrypt the generated public key;
an adding unit configured to add the encrypted public key to the set of registration public keys and to send the encrypted public key to the second terminal.
9. The apparatus of one of claims 6-8, wherein the data storage request further comprises a digital signature; and
the determination unit is configured to:
decrypting and verifying the digital signature by using the public key of the first terminal to determine whether the digital signature is valid;
in response to determining that the digital signature is valid, determining that the data to be stored is valid data.
10. The apparatus of claim 7 or 8, wherein the data storage request further comprises a storage data identification; and
the adding unit is configured to:
encrypting the storage data identification by using the public key of the first terminal;
taking the encrypted storage data identification as a primary key word of the data to be stored, and storing the encrypted storage data identification;
and in response to the determination that the storage is successful, returning information of successful storage to the first terminal, and sending a storage data identifier to the second terminal.
11. A first terminal device comprising:
one or more processors;
a storage device having one or more programs stored thereon;
when executed by the one or more processors, cause the one or more processors to implement the method of any one of claims 1-5.
12. A computer-readable storage medium, on which a computer program is stored which, when being executed by a processor, carries out the method according to any one of claims 1-5.
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201810650431.0A CN108923925B (en) | 2018-06-22 | 2018-06-22 | Data storage method and device applied to block chain |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201810650431.0A CN108923925B (en) | 2018-06-22 | 2018-06-22 | Data storage method and device applied to block chain |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN108923925A CN108923925A (en) | 2018-11-30 |
| CN108923925B true CN108923925B (en) | 2022-11-08 |
Family
ID=64420822
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN201810650431.0A Active CN108923925B (en) | 2018-06-22 | 2018-06-22 | Data storage method and device applied to block chain |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN108923925B (en) |
Families Citing this family (5)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN110602089B (en) * | 2019-09-11 | 2021-08-10 | 腾讯科技(深圳)有限公司 | Block chain-based medical data storage method, device, equipment and storage medium |
| CN111182525B (en) * | 2019-12-25 | 2022-09-02 | 中国联合网络通信集团有限公司 | Method and device for storing data |
| CN111291420B (en) * | 2020-01-21 | 2022-11-11 | 国家市场监督管理总局信息中心 | Distributed off-link data storage method based on block chain |
| CN112532646B (en) * | 2020-12-09 | 2022-08-16 | 杭州趣链科技有限公司 | Data sharing method, system, device, equipment and storage medium |
| CN113222728A (en) * | 2021-05-31 | 2021-08-06 | 广州大学 | Financial data processing method, system, device and storage medium |
Citations (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN105915520A (en) * | 2016-04-18 | 2016-08-31 | 深圳大学 | File storage and searching method based on public key searchable encryption, and storage system |
| CN107292181A (en) * | 2017-06-20 | 2017-10-24 | 无锡井通网络科技有限公司 | Database Systems based on block chain and the application method using the system |
| CN107770182A (en) * | 2017-10-30 | 2018-03-06 | 中国联合网络通信集团有限公司 | The date storage method and home gateway of home gateway |
Family Cites Families (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN106452770B (en) * | 2015-08-12 | 2020-10-13 | 深圳市腾讯计算机系统有限公司 | Data encryption method, data decryption method, device and system |
-
2018
- 2018-06-22 CN CN201810650431.0A patent/CN108923925B/en active Active
Patent Citations (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN105915520A (en) * | 2016-04-18 | 2016-08-31 | 深圳大学 | File storage and searching method based on public key searchable encryption, and storage system |
| CN107292181A (en) * | 2017-06-20 | 2017-10-24 | 无锡井通网络科技有限公司 | Database Systems based on block chain and the application method using the system |
| CN107770182A (en) * | 2017-10-30 | 2018-03-06 | 中国联合网络通信集团有限公司 | The date storage method and home gateway of home gateway |
Also Published As
| Publication number | Publication date |
|---|---|
| CN108923925A (en) | 2018-11-30 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN108923925B (en) | Data storage method and device applied to block chain | |
| CN112131316B (en) | Data processing method and device applied to block chain system | |
| CN107248984B (en) | Data exchange system, method and device | |
| CN108668277B (en) | Method and equipment for sharing and acquiring information | |
| CN110636043A (en) | File authorization access method, device and system based on block chain | |
| CN110611657A (en) | File stream processing method, device and system based on block chain | |
| CN114024710A (en) | Data transmission method, device, system and equipment | |
| JP7235930B2 (en) | Methods and apparatus, electronic devices, storage media and computer programs for processing data requests | |
| CN115296807B (en) | Key generation method, device and equipment for preventing industrial control network viruses | |
| CN111199037A (en) | Login method, system and device | |
| CN111291420B (en) | Distributed off-link data storage method based on block chain | |
| CN114584299A (en) | Data processing method and device, electronic equipment and storage medium | |
| CN116383867A (en) | Data query method, device, electronic equipment and computer readable medium | |
| CN113282951B (en) | Application program security verification method, device and equipment | |
| CN111010283B (en) | Method and apparatus for generating information | |
| CN114499893B (en) | Bidding file encryption and evidence storage method and system based on block chain | |
| CN110602075A (en) | File stream processing method, device and system for encryption access control | |
| CN111050326A (en) | Short message verification method, device, equipment and medium based on block chain | |
| JP2019057827A (en) | Distributed authentication system and program | |
| CN110166226B (en) | Method and device for generating secret key | |
| CN113301058A (en) | Information encryption transmission method and device, electronic equipment and computer readable medium | |
| CN115378743B (en) | Information encryption transmission method, device, equipment and medium | |
| CN110619236A (en) | File authorization access method, device and system based on file credential information | |
| CN114826616B (en) | Data processing method, device, electronic equipment and medium | |
| CN115828309B (en) | Service calling method and system |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| GR01 | Patent grant | ||
| GR01 | Patent grant |