KR20170067120A - Gateway and method for authentication - Google Patents
Gateway and method for authentication Download PDFInfo
- Publication number
- KR20170067120A KR20170067120A KR1020160018230A KR20160018230A KR20170067120A KR 20170067120 A KR20170067120 A KR 20170067120A KR 1020160018230 A KR1020160018230 A KR 1020160018230A KR 20160018230 A KR20160018230 A KR 20160018230A KR 20170067120 A KR20170067120 A KR 20170067120A
- Authority
- KR
- South Korea
- Prior art keywords
- user
- server
- authentication
- subscriber
- information
- Prior art date
Links
Images
Classifications
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/10—Network architectures or network communication protocols for network security for controlling access to devices or network resources
- H04L63/105—Multiple levels of security
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L12/00—Data switching networks
- H04L12/66—Arrangements for connecting between networks having differing types of switching systems, e.g. gateways
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/08—Network architectures or network communication protocols for network security for authentication of entities
- H04L63/0807—Network architectures or network communication protocols for network security for authentication of entities using tickets, e.g. Kerberos
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/08—Network architectures or network communication protocols for network security for authentication of entities
- H04L63/0815—Network architectures or network communication protocols for network security for authentication of entities providing single-sign-on or federations
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/08—Network architectures or network communication protocols for network security for authentication of entities
- H04L63/0892—Network architectures or network communication protocols for network security for authentication of entities by using authentication-authorization-accounting [AAA] servers or protocols
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/32—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials
- H04L9/321—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials involving a third party or a trusted authority
- H04L9/3213—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials involving a third party or a trusted authority using tickets or tokens, e.g. Kerberos
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Computer Hardware Design (AREA)
- Computing Systems (AREA)
- General Engineering & Computer Science (AREA)
- Business, Economics & Management (AREA)
- Accounting & Taxation (AREA)
- Data Exchanges In Wide-Area Networks (AREA)
Abstract
The present invention includes a communication module, a memory for storing a program for managing user authentication and access, and a processor for executing a program stored in the memory. At this time, when the user requests access to the non-subscriber company server, the processor performs authentication of the user with respect to the non-subscriber company server based on the information of the user and transmits the user's access to the non- Allow. The user information includes authentication information of the subscriber institution server of the user, and the subscriber server of the user is different from the non-subscriber server of the user.
Description
The present invention relates to an authentication method of an authentication gateway and an authentication gateway.
In cloud services, account management solutions include signal sign-on (SSO), extranet access management (EAM), and identity access management (IAM).
Integrated authentication is a security solution that enables you to use various systems or Internet services with one login. Integrated authentication can access various systems and services with only one account without having to go through multiple authentication procedures. Therefore, integrated authentication has the advantage of reducing user convenience and management cost.
Integrated authentication management is defined by the Gartner group. Integrated authentication management manages the integrated authentication and user authentication. Integrated authentication management uses a single mechanism based on security policy to manage user access to applications and data.
As such, integrated authentication and integrated authentication management are applications' access-oriented solutions. In contrast, integrated account management is a more comprehensive concept. Integrated account management is often referred to as account management solutions, integrated account management, and integrated authentication management. Integrated account management can manage user access to system resources through identifiers and privileges in various systems.
In this regard, Korean Patent Laid-Open Publication No. 10-2013-0046155 (entitled "Access Control System in Cloud Computing Service") discloses an access control and authorization policy for providing a personal cloud service. Specifically, the present invention includes a user authentication server, a plurality of cloud service servers, and a collaboration service server, and compares the access token information with the user access control list through the cloud service server to approve the service access of the user.
The present invention provides an authentication gateway and an authentication gateway authentication method for performing authentication of a non-subscription server through a base server in an inter-cloud environment.
It should be understood, however, that the technical scope of the present invention is not limited to the above-described technical problems, and other technical problems may exist.
As a technical means for achieving the above technical object, an authentication gateway according to the first aspect of the present invention includes a communication module, a memory for storing a program for managing authentication and access of a user, and a processor for executing a program stored in the memory . At this time, when the user requests access to the non-subscriber company server, the processor performs authentication of the user with respect to the non-subscriber company server based on the information of the user and transmits the user's access to the non- Allow. The user information includes authentication information of the subscriber institution server of the user, and the subscriber server of the user is different from the non-subscriber server of the user.
According to a second aspect of the present invention, there is provided an authentication method of an authentication gateway, including: performing authentication of a user to a non-subscriber server based on information of a user when the user requests access to the non-subscriber server; And allowing the user to access the non-subscriber server performing the authentication. At this time, the information of the user includes the authentication information of the subscriber institution server of the user, and the subscriber server of the user is different from the non-subscriber server of the user.
The present invention can access the information of the non-subscriber based on the information of the minimum base institution and the information of the user received from the base institution in the inter-cloud environment. Therefore, the present invention can provide an integrated account management service so that the information of other organizations can be utilized safely and efficiently. In addition, the present invention can seamlessly provide a plurality of services to a user.
1 is a block diagram of an authentication system in accordance with an embodiment of the present invention.
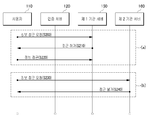
2 is a flowchart of a basic authentication process according to an embodiment of the present invention.
3 is a flow chart of the authentication process of the authentication server according to the embodiment of the present invention.
4 is a block diagram of an authentication gateway according to an embodiment of the present invention.
5 is a flowchart of an authentication method of an authentication gateway according to an embodiment of the present invention.
Hereinafter, embodiments of the present invention will be described in detail with reference to the accompanying drawings, which will be readily apparent to those skilled in the art. The present invention may, however, be embodied in many different forms and should not be construed as limited to the embodiments set forth herein. In order to clearly illustrate the present invention, parts not related to the description are omitted, and similar parts are denoted by like reference characters throughout the specification.
Throughout the specification, when a part is referred to as being "connected" to another part, it includes not only "directly connected" but also "electrically connected" with another part in between . Also, when a part is referred to as "including " an element, it does not exclude other elements unless specifically stated otherwise.
The
1 is a block diagram of an
The
The
In addition, the
The
The
The
The
The
The
The authentication process in the
2 is a flowchart of a basic authentication process according to an embodiment of the present invention.
As shown in FIG. 2 (a), the
The
Then, the
In FIG. 2B, the second
The
If the
3 is a flow chart of the authentication process of the
Specifically, when the
At this time, the
The
At this time, the information of the
Also, the first
Specifically, the
The
For example, the first
The
At this time, the login information of the
For example, if the predetermined format is JSON, the
The
The
At this time, the
The
Thus, the
The first
4, an
4 is a block diagram of an
The
The
The
The
At this time, the non-subscriber station server and the subscriber station server according to an embodiment of the present invention may be a cloud service server.
The affiliate institution server is an institution server to which the
The non-subscriber server is also an agency server to which the
At this time, the affiliate server may be an agency server selected by the
The
When the subscription authority server authenticates the user information and transmits the login information of the
At this time, the login information includes an identifier of the
The
The non-subscriber company server receiving the encrypted token may perform authentication of the
The
The
Next, an authentication method of the
5 is a flowchart of an authentication method of an
When the
Specifically, the
The
At this time, the
The
If authentication of the
The authentication method of the
Therefore, the authentication method of the
One embodiment of the present invention may also be embodied in the form of a recording medium including instructions executable by a computer, such as program modules, being executed by a computer. Computer readable media can be any available media that can be accessed by a computer and includes both volatile and nonvolatile media, removable and non-removable media. In addition, the computer-readable medium may include both computer storage media and communication media. Computer storage media includes both volatile and nonvolatile, removable and non-removable media implemented in any method or technology for storage of information such as computer readable instructions, data structures, program modules or other data. Communication media typically includes any information delivery media, including computer readable instructions, data structures, program modules, or other data in a modulated data signal such as a carrier wave, or other transport mechanism.
While the methods and systems of the present invention have been described in connection with specific embodiments, some or all of those elements or operations may be implemented using a computer system having a general purpose hardware architecture.
It will be understood by those skilled in the art that the foregoing description of the present invention is for illustrative purposes only and that those of ordinary skill in the art can readily understand that various changes and modifications may be made without departing from the spirit or essential characteristics of the present invention. will be. It is therefore to be understood that the above-described embodiments are illustrative in all aspects and not restrictive. For example, each component described as a single entity may be distributed and implemented, and components described as being distributed may also be implemented in a combined form.
The scope of the present invention is defined by the appended claims rather than the detailed description and all changes or modifications derived from the meaning and scope of the claims and their equivalents are to be construed as being included within the scope of the present invention do.
100: Authentication system
110: User
120: Authentication server
130: Authentication gateway
140: Policy decision server
150: First institution server
160: Second institution server
Claims (11)
Communication module,
A memory storing a program for managing user authentication and access, and
And a processor for executing a program stored in the memory,
The processor, when the user requests access to a non-subscriber server,
Performing authentication of the user with respect to the non-subscriber server based on the information of the user, allowing the user to access the non-subscriber server performing the authentication,
Wherein the information of the user includes authentication information of a subscriber institution server of the user,
Wherein the user's subscription authority server is different from the user's non-subscription authority server.
The processor forwards the information of the user to the subscriber's server of the user to perform authentication of the user to the non-subscriber server.
Wherein the processor receives login information corresponding to the user authentication from the subscription authority server and performs authentication of the user with respect to the non-subscription authority server based on the received login information,
Wherein the login information is composed of an identifier of the user, an authority level of the user at the subscription authority server, an authentication time of the user at the subscription authority server, information of the subscription authority, and a URL of the non- , Authentication gateway.
Wherein the processor generates an encrypted token based on the login information received from the subscriber's server through the policy determination server,
And transmits the generated encrypted token to the non-subscriber server.
And the non-subscriber station server sets the authority level of the user corresponding to the access request of the user based on the authority level of the user included in the login information.
Wherein the processor performs authentication of the user with respect to the non-subscriber server based on authentication information included in the subscriber server selected by the user among subscriber's servers included in the user information.
Wherein the non-subscriber company server and the subscription authority server are cloud service servers.
Performing authentication of the user to the non-subscriber server based on the information of the user when the user requests access to the non-subscriber company server; And
And allowing the user to access the non-subscriber server performing the authentication,
Wherein the information of the user includes authentication information of a subscriber institution server of the user,
Wherein the user's subscription authority server is different from the user's non-subscription authority server.
Wherein performing the authentication of the user to the non-
Transferring the information of the user to a subscriber institution server of the user; And
And performing authentication of the user to the non-subscriber server through the subscriber's server of the user.
Wherein performing the authentication of the user to the non-
Receiving login information corresponding to the user authentication from the subscriber's server; And
And performing authentication of the user to the non-subscriber server based on the received login information,
Wherein the login information is composed of an identifier of the user, an authority level of the user at the subscription authority server, an authentication time of the user at the subscription authority server, information of the subscription authority, and a URL of the non- , Authentication method of the authentication gateway.
Applications Claiming Priority (2)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| KR1020150173095 | 2015-12-07 | ||
| KR20150173095 | 2015-12-07 |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| KR20170067120A true KR20170067120A (en) | 2017-06-15 |
| KR101824562B1 KR101824562B1 (en) | 2018-02-01 |
Family
ID=59217739
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| KR1020160018230A KR101824562B1 (en) | 2015-12-07 | 2016-02-17 | Gateway and method for authentication |
Country Status (1)
| Country | Link |
|---|---|
| KR (1) | KR101824562B1 (en) |
Cited By (5)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| KR102004821B1 (en) * | 2018-07-06 | 2019-07-29 | 황치범 | Apparatus and method for providing mediation service supporting integrated processing of private authentication |
| KR20190134135A (en) * | 2018-05-25 | 2019-12-04 | 삼성에스디에스 주식회사 | Service providing method based on cloud platform and system thereof |
| KR20200132375A (en) * | 2019-05-17 | 2020-11-25 | 주식회사 모티링크 | Method for authorizing virtual space user and system for providing virtual space |
| CN114070585A (en) * | 2021-10-18 | 2022-02-18 | 北京天融信网络安全技术有限公司 | SSL VPN authentication method, device and gateway |
| KR102670856B1 (en) * | 2023-12-04 | 2024-05-30 | 주식회사 범익 | Apparatus for relaying customer verification authentication and method therefo |
Family Cites Families (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JP4758575B2 (en) * | 2001-08-09 | 2011-08-31 | ヤフー株式会社 | User authentication method and user authentication system |
-
2016
- 2016-02-17 KR KR1020160018230A patent/KR101824562B1/en active IP Right Grant
Cited By (5)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| KR20190134135A (en) * | 2018-05-25 | 2019-12-04 | 삼성에스디에스 주식회사 | Service providing method based on cloud platform and system thereof |
| KR102004821B1 (en) * | 2018-07-06 | 2019-07-29 | 황치범 | Apparatus and method for providing mediation service supporting integrated processing of private authentication |
| KR20200132375A (en) * | 2019-05-17 | 2020-11-25 | 주식회사 모티링크 | Method for authorizing virtual space user and system for providing virtual space |
| CN114070585A (en) * | 2021-10-18 | 2022-02-18 | 北京天融信网络安全技术有限公司 | SSL VPN authentication method, device and gateway |
| KR102670856B1 (en) * | 2023-12-04 | 2024-05-30 | 주식회사 범익 | Apparatus for relaying customer verification authentication and method therefo |
Also Published As
| Publication number | Publication date |
|---|---|
| KR101824562B1 (en) | 2018-02-01 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US10581827B2 (en) | Using application level authentication for network login | |
| US10673861B2 (en) | Identity proxy to provide access control and single sign on | |
| US10057251B2 (en) | Provisioning account credentials via a trusted channel | |
| US10104084B2 (en) | Token scope reduction | |
| US10277409B2 (en) | Authenticating mobile applications using policy files | |
| US10136315B2 (en) | Password-less authentication system, method and device | |
| US9038138B2 (en) | Device token protocol for authorization and persistent authentication shared across applications | |
| US9584615B2 (en) | Redirecting access requests to an authorized server system for a cloud service | |
| US9178868B1 (en) | Persistent login support in a hybrid application with multilogin and push notifications | |
| US20170099148A1 (en) | Securely authorizing client applications on devices to hosted services | |
| CN105991614B (en) | It is a kind of it is open authorization, resource access method and device, server | |
| US10148651B2 (en) | Authentication system | |
| US9590972B2 (en) | Application authentication using network authentication information | |
| KR101824562B1 (en) | Gateway and method for authentication | |
| US11418498B2 (en) | Single sign on proxy for regulating access to a cloud service | |
| US9787678B2 (en) | Multifactor authentication for mail server access | |
| CN103069742A (en) | Method and apparatus to bind a key to a namespace | |
| US20220311626A1 (en) | Cloud-based identity provider interworking for network access authentication | |
| CN115190483B (en) | Method and device for accessing network | |
| CN114764507A (en) | Method and device for realizing resource access, electronic equipment and storage medium | |
| JP2018037025A (en) | Program, authentication system, and authentication cooperative system | |
| JP5920891B2 (en) | Communication service authentication / connection system and method thereof | |
| KR20170067119A (en) | Server and method for oauth risk management of resource |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| A201 | Request for examination | ||
| E902 | Notification of reason for refusal | ||
| E90F | Notification of reason for final refusal | ||
| E701 | Decision to grant or registration of patent right | ||
| GRNT | Written decision to grant |