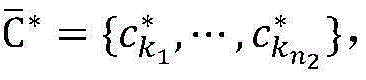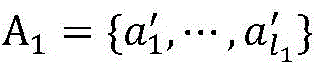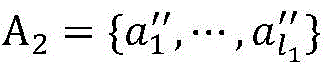CN113515778B - Multi-party privacy data fusion method and device and electronic equipment - Google Patents
Multi-party privacy data fusion method and device and electronic equipment Download PDFInfo
- Publication number
- CN113515778B CN113515778B CN202110769349.1A CN202110769349A CN113515778B CN 113515778 B CN113515778 B CN 113515778B CN 202110769349 A CN202110769349 A CN 202110769349A CN 113515778 B CN113515778 B CN 113515778B
- Authority
- CN
- China
- Prior art keywords
- party
- class
- data
- class set
- private
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Active
Links
Images
Classifications
-
- G—PHYSICS
- G06—COMPUTING; CALCULATING OR COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/60—Protecting data
- G06F21/62—Protecting access to data via a platform, e.g. using keys or access control rules
- G06F21/6218—Protecting access to data via a platform, e.g. using keys or access control rules to a system of files or objects, e.g. local or distributed file system or database
- G06F21/6245—Protecting personal data, e.g. for financial or medical purposes
-
- G—PHYSICS
- G06—COMPUTING; CALCULATING OR COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F18/00—Pattern recognition
- G06F18/20—Analysing
- G06F18/25—Fusion techniques
- G06F18/251—Fusion techniques of input or preprocessed data
-
- G—PHYSICS
- G06—COMPUTING; CALCULATING OR COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/60—Protecting data
- G06F21/602—Providing cryptographic facilities or services
Landscapes
- Engineering & Computer Science (AREA)
- Theoretical Computer Science (AREA)
- General Health & Medical Sciences (AREA)
- Physics & Mathematics (AREA)
- Bioethics (AREA)
- Health & Medical Sciences (AREA)
- General Physics & Mathematics (AREA)
- General Engineering & Computer Science (AREA)
- Data Mining & Analysis (AREA)
- Computer Hardware Design (AREA)
- Software Systems (AREA)
- Computer Security & Cryptography (AREA)
- Life Sciences & Earth Sciences (AREA)
- Bioinformatics & Computational Biology (AREA)
- Bioinformatics & Cheminformatics (AREA)
- Artificial Intelligence (AREA)
- Evolutionary Computation (AREA)
- Computer Vision & Pattern Recognition (AREA)
- Evolutionary Biology (AREA)
- Medical Informatics (AREA)
- Databases & Information Systems (AREA)
- Telephonic Communication Services (AREA)
Abstract
The specification discloses a method, a device and electronic equipment for fusing multi-party private data, and relates to the technical field of data security, wherein each party randomly splits a private data set into two types of sets, firstly adopts a private key of each party to process the two types of sets, then transmits the processed first type of sets to the next party in a positive sequence, and transmits the second type of sets to the next party in a negative sequence; each party also carries out N-2 rounds of data interaction, and in each round of interaction, each party processes the received two types of sets through a private key of each party, and then transmits the positive sequence of the first type of set to the next party and transmits the negative sequence of the second type of set to the next party; each party processes the received two types of sets through a private key of each party, further performs set operation on the two types of sets after processing, and sends an operation result to other parties; and each party executes the set operation again according to the received set operation result to obtain a multi-party fusion result. In the scheme, each party cannot acquire intersection or union information of any two parties.
Description
Technical Field
The present application relates to the field of data security technologies, and in particular, to a method and an apparatus for fusing multiparty private data, and an electronic device.
Background
Data size and capacity are one of the major competitiveness of commercial establishments. Each organization expands the data volume of the organization to improve the data coverage and the comprehensive application requirement. When an organization shares user information (ID, mobile phone number, device number, etc.) with other organizations, authorization of a corresponding user needs to be obtained as a necessary condition. In practical scenarios, the user authorization process may have negative effects such as timeliness and user experience, and may pose a potential compliance risk (e.g., the authorization terms are not strict or misleading, and are easily complained or negatively evaluated by the user). Therefore, a data sharing and fusion scheme for really protecting privacy of each party (privacy of a demand party + privacy of a provider) needs to be explored in a technical level, so that the privacy and benefits of each party are protected to the greatest extent, and meanwhile, hidden dangers of business compliance are avoided.
However, in the prior art, when multi-party data privacy fusion is solved, leakage of extra information such as intersection scale and union scale is caused, for example, a, B, and C are privacy data sets of a third party, a second party, and a third party, respectively, the first party can obtain element number information of | B £ C | and | B $ C |, element number information of privacy data sets (intersection, union) of two parties of ethylene-propylene is disclosed to other mechanisms, privacy leakage is formed for the second party and the third party, and although security of original data is not involved, certain risk still exists.
Disclosure of Invention
The embodiment of the application aims to provide a multi-party private data fusion method, a multi-party private data fusion device and electronic equipment, so as to solve the problem that intersection or union information of multiple parties is easy to leak.
In order to solve the foregoing technical problem, an embodiment of the present specification provides a multiparty private data fusion method, including: each party in the N parties splits the private data set of the each party into a first class set and a second class set; each party in the N parties processes the first class set of the party by the private key of the party and transmits the first class set to the next party according to a first transmission sequence, and processes the second class set of the party by the private key of the party and transmits the second class set to the next party according to a second transmission sequence, wherein the second transmission sequence is opposite to the first transmission sequence; each of the N parties performs N-2 rounds of data interaction: in each round of processing, each party processes the received first class set and the second class set through a private key of each party, transmits the processed first class set to the next party according to a first transmission sequence, and transmits the processed second class set to the next party according to a second transmission sequence; each party processes the currently received first class set and second class set through a private key of the party, performs first set operation on the processed first class set and second class set, and sends set operation results to all parties except the party in the N party; and each party executes a second set operation according to the received set operation result to obtain a multi-party fusion result.
In the method for fusing multi-party private data provided by the embodiment of the specification, each party randomly splits a private data set of the party into two types of sets, firstly, each party processes the two types of sets by using a private key of the party, then, transmits the processed first type of set to the next party according to a positive sequence, and transmits the second type of set to the next party in a reverse sequence; each party also carries out N-2 rounds of data interaction, and in each round of interaction, each party processes the received two types of sets through a private key of each party, transmits the first type of set to the next party according to a positive sequence and transmits the second type of set to the next party according to a negative sequence; each party processes the received two types of sets through the private key of the party, further performs set operation on the two types of sets after processing, and sends the operation result to other parties; and each party executes the set operation again according to the received set operation result to obtain a multi-party fusion result. In the process of the scheme, each party cannot acquire intersection or union information of any two parties, so that the safety of private data fusion is improved.
Drawings
In order to more clearly illustrate the embodiments of the present application or the technical solutions in the prior art, the drawings needed to be used in the description of the embodiments or the prior art will be briefly introduced below, it is obvious that the drawings in the following description are only some embodiments described in the present application, and for those skilled in the art, other drawings can be obtained according to the drawings without creative efforts.
FIG. 1 illustrates a flow diagram of a method of multi-party privacy data fusion in accordance with an embodiment of the present description;
FIG. 2A shows a schematic diagram of a logically closed loop formed by three parties;
FIG. 2B shows a schematic diagram of a logically closed loop formed by four squares;
FIG. 3 illustrates a flow diagram of another multi-party private data fusion method in accordance with an embodiment of the present description;
FIG. 4 illustrates a flow diagram of a multi-party privacy data fusion method according to an embodiment of the present description;
FIG. 5A illustrates a functional block diagram of a multi-party private data fusion apparatus according to an embodiment of the present description;
FIG. 5B illustrates a functional block diagram of another multi-party privacy data fusion apparatus in accordance with an embodiment of the present description;
FIG. 6 illustrates a functional block diagram of an electronic device in accordance with an embodiment of the present description.
Detailed Description
In order to make those skilled in the art better understand the technical solutions in the present application, the technical solutions in the embodiments of the present application will be clearly and completely described below with reference to the drawings in the embodiments of the present application, and it is obvious that the described embodiments are only a part of the embodiments of the present application, and not all of the embodiments. All other embodiments obtained by a person of ordinary skill in the art based on the embodiments in the present application without making creative efforts shall fall within the protection scope of the present application.
The embodiment of the specification provides a multi-party privacy data fusion method. The following takes the first, second and third parties as examples, and a detailed description is made on a multiparty private data fusion method.
First, the data of the third party, A, B and C, is preprocessed before the fusion is started. Specifically, the following steps (1) to (5) may be used.
(1) The third party determines the elliptic curve by negotiationAnd a random point generating function H p (. O) and determining an elliptic curve generatorIn the present specification, the operation of multiplying an elliptic curve is expressed in the form of an exponentiation, but may be expressed in other forms.
(2) Respective generation of ethylene propylene monomerPrivate key of itselfWherein sk 1 Is the private key of Party A, sk 2 Is the private key of party B, sk 3 Is the private key of the third party, and each party calculates its own public keyAnd disclose;
(3) The A, B and C parties extract original data of private data to be fused from a database of the A, B and C parties, and randomly disturb the sequence to obtain a set A = { a = 1 ,…,a l }、B={b 1 ,…,b m And C = { C = } 1 ,…,c n }。
(4) The third party calculates the shared secret key K of the privacy data fusion task according to the key agreement mechanism of the third party,
(5) The Party A carries out randomized splitting on the set A to obtain two split setsAnd satisfy the requirements ofAnd l 1 +l 2 = l, then calculate own private data setAnd
party B goes to set BThe lines are split randomly to obtain two split setsAndsatisfy the requirement ofAnd m is 1 +m 2 = m, then calculates the private data set of itselfAnd
the third party carries out randomized resolution on the set C to obtain two resolution setsAndsatisfy the requirement ofAnd n is 1 +n 2 = n, then the private data set of itself is calculated And
after the data preprocessing is finished, each party converts the original data to be fused in the database of the party into the private data, and then the data fusion process can be started.
For three-way data fusion, the data fusion process comprises four rounds of data interaction and one set operation. The details are as follows.
In the first round of interaction, all parties do not change the element sequence in the sets, and the third parties A, B and C respectively send the two privacy data sets to the other two parties in a forward and reverse double-loop mode. The method comprises the following specific steps.
(1) For i =1, \8230;, l 1 Calculate the first placeObtaining a private data set of Party AThen, the private data is collected A 1 Sending to the second party; for i =1, \ 8230;, l 2 Calculate the first placeObtaining a private data set of Party AThe private data is then aggregatedSending to the third party.
(2) For j =1, \ 8230;, m 1 Calculation of second partyObtaining private data set of party BThen, the private data is collected into a set B 1 Sending to the third party; for j =1, \ 8230;, m 1 Calculation of second partyObtaining private data set of party BThe private data is then aggregatedAnd sending to the first party.
(3) For k =1, \ 8230;, n 1 Calculation of third PartyDeriving private data sets for Party threeThen, the private data is collected C 1 Sending to the first party; for k =1, \8230;, n 2 Calculation of third PartyDeriving private data sets for Party threeThe private data is then assembledAnd sending the data to the second party.
In the second round of interaction, all parties do not change the element sequence in the sets, and the third parties A, B and C respectively send the two private data sets to the other two parties in a forward and reverse dual-cycle mode. The method comprises the following specific steps.
(1) Private data collection received by Party A for the previous roundAnd(from Party B, C 1 From third party), calculate for all elements in both setsAndrespectively obtaining two new privacy data setsAndthe private data is then assembledSending to the third party, and C 2 And sending the data to the second party.
(2) Private data set received by party B for previous roundAnd(from prescription A of third party 1 From the first party), calculate all elements in both setsAndrespectively obtaining two new privacy data setsAndthen, the private data is collected A 2 Sending to the third party and collecting the private dataAnd sending to the first party.
(3) Private data collection received by the third party for the previous roundAnd(from Paris polyphylla, B 1 From the second party), compute on all elements in both setsAndrespectively obtaining two new privacy data setsAndthe private data is then aggregatedSending to the second party and collecting the privacy data B 2 And sending to the first party.
In the third round of interaction, none of the parties changes the order of the elements within the set, and the following steps are performed.
(1) Private data collection received by Party A for the previous roundAnd(B 2 the medicine comes from the third party of the recipe,from the second party), compute on all elements in both setsAndrespectively obtaining two new privacy data setsAndcalculating the union of the two and disordering the element sequence to obtainAnd X is A Respectively sending to the second party and the third party;
(2) Private data set received by party B for previous roundAnd(from Paris polyphylla, C 2 From the first party) for all elements in both setsAndrespectively obtaining two new privacy data setsAndcalculating the union of the two and disordering the element sequence to obtainAnd mixing X B Respectively sending to the first and third parties;
(3) Private data set received by third party for last roundAnd(A 2 the source of the second party is that of the second party,from the first party), calculate all elements in both setsAndrespectively obtaining two new privacy data setsAndcalculating the union of the two and disordering the element sequence to obtainAnd mixing X C Respectively sent to the first party and the second party.
After the three rounds of data interaction, a set operation is executed. The method specifically comprises the following two steps:
(1) For the third parties A, B and C, X is shared in the last round of communication A ,X B ,X C Each party calculates union X ABC =X A ∪X B ∪X C . Union set X ABC The element order in (2) needs to follow a predetermined ordering rule to ensure that the acquisition sets of each party are the same and the element order is the same.
(2) Record union X ABC Aggregate size of, | X ABC |=α ABC .
A fourth round of data interaction is then performed to ensure that the parties know where the elements of themselves are in the union. The fourth data interaction may include the following steps.
(1) Party A according to private data setAndfor each set, sequentially for each element, in union X ABC In finding its location information, i.e. calculatingAndrespectively correspond toAndat X ABC And then will beSent to the second party toSending to the third party.
(2) B according to private data setAndfor each set, sequentially for each element, in union X ABC In finding its location information, i.e. calculatingAndrespectively correspond toAndat X ABC And then will beSent to the first party, willSending to the third party.
(3) Third party according to private data collectionAndfor each set, sequentially for each element, in union X ABC In finding its location information, i.e. calculatingAndrespectively correspond toAndat X ABC And then will beSending to the first party toAnd sending the data to the second party.
(4) Each party collects the position information received in the round according to the splitting and random out-of-order operation in the self data preprocessing, reversely deduces the position of the self element in the multi-party and centralized manner, marks the position and completes the multi-party data fusion.
The following table one illustrates the process of the three-party private data fusion, where the private data set of the first party is a, and the private data set of the second party is B. The private data sets of the parties are split into 2 sets. A. The 1 Indicating that one party has processed the data in set A with its own private key, C 2 * Two parties process the data in the set C by using own private keys, and so on, understand the contents represented by other symbols with the same format in the table.
Watch 1
The following table two shows another three-party private data fusion process, where the private data set of a is a, the private data set of B is B, and the private data set of C is C. The private data sets of the parties are split into 3 sets. A1 (1) Indicating that one party has processed the data in the set A1 with its own private key, C3 (3) It indicates that three parties process the data in the set C3 by using their own private keys, and so on, to understand what is represented by other symbols in the same format in the table.
Watch 2
The following table three shows a process of fusing the four-party privacy data, where the privacy data set of a is a, the privacy data set of B is B, the privacy data set of C is C, and the privacy data set of D is D. The private data sets of the parties are split into 2 sets. A1 (1) Indicating that one party has processed the data in the set A1 with its own private key, C3 (3) It is shown that three parties process the data in the set C3 by using their own private keys, and so on, to understand what other symbols in the same format in the table represent.
Watch III
The three-party privacy data fusion method embodies the process of the multi-party privacy data fusion method provided by the embodiment of the specification. The following describes a multi-party private data fusion method provided in an embodiment of the present specification. The number of the participants of the privacy data fusion in the method is N, and N is an integer greater than or equal to 3. As shown in fig. 1, the method includes the following steps.
S110: each of the N parties divides the private data set of the each party into a first class set and a second class set.
This step corresponds to the data preprocessing step in the embodiment shown in table one, and specifically corresponds to the randomization splitting step therein.
The first set of classes is at least one and the second set of classes is at least one. The first class set and the second class set are only used for subsequently distinguishing different directions of data transmission, and have no other limiting meanings. That is, each party splits its own private data set into M sets, where M is an integer greater than or equal to 2, and classifies at least one of the M sets as a first-class set, and then classifies the rest of the M sets as a second-class set, where the second-class set includes at least one set.
The number of the first-type sets split by each party is equal, but the number of each set element in the first-type sets can be different. The number of second-class collections split by the parties is equal, but the number of each collection element in the second-class collections may be different.
In the first-class set and the second-class set, the intersection of any two sets may be null or not null, but the union of all sets in the first-class set and the second-class set should be a private data set.
In the case where the intersection of any two or more sets is empty, reference may be made to the specific embodiment illustrated in table one.
In a case where the intersection of the two sets is not empty, for example, there are five elements A1, A2, A3, a4, and a5 in the private data set of the first party, the data A1 and A2 may be extracted as the set A1, the data A2 and A3 may be extracted as the set A2, and the data A3, a4, and a5 may be extracted as the set A3, that is, 3 sets are extracted from the private data set of the first party.
In some embodiments, there may be two or more sets of elements that are the same in the first-class set and the second-class set.
In some embodiments, the number of the first class set and the second class set may be preset. For example, in the embodiment illustrated in Table one, the number of each type of collection is 1. The number of sets of classes may be independent of the number of parties involved in the fusion of private data, or may be independent of the size of the amount of data provided by the parties for fusion.
In some embodiments, the parties may agree on the number of sets of each of the first class set and the second class set before performing step S110. For example, the number of each type of set may be determined according to the number of participants in data fusion, or the number of each type of set may be determined according to the amount of data provided by the party providing the largest amount of data for fusion, or the number of each type of set may also be determined according to other situations, which is not listed in this specification.
The "private data" described in this specification may be raw data stored in the databases of the parties that is not disclosed to other institutions. For example, a database of an organization may store a plurality of pieces of field information about users later, each user record has contents of the fields, and the original data may be values of a plurality of records in one of the fields, such as device numbers of a plurality of users, identity numbers of a plurality of users, mobile phone numbers of a plurality of users, business registration numbers of a plurality of users, and the like.
The "private data" described in this specification may also be data obtained by using an encryption algorithm based on these original data, and the encrypted data may be disclosed to other organizations. The encryption algorithm referred to herein may be a random point generation function to map the original data to points on an elliptic curve as in the specific embodiment illustrated in table one, or may be an encryption algorithm such as RSA, DES, MD5, etc., which is not listed in this specification.
In some embodiments, before data in each original data set is converted into private data, the order of the data in each original data set is also randomly disturbed, so that even if the private data is acquired, the corresponding original data cannot be directly known, thereby further improving the security of the original data.
S120: each party in the N parties processes the first class set of the party by the private key of the party and transmits the first class set to the next party according to a first transmission sequence, and processes the second class set of the party by the private key of the party and transmits the second class set to the next party according to a second transmission sequence, wherein the second transmission sequence is opposite to the first transmission sequence.
This step corresponds to the first round of interaction in the illustrated embodiment of table one.
S130: each of the N parties carries out N-2 rounds of processing: in each round of processing, each party processes the received first class set and the second class set through a private key of the party, transmits the processed first class set to the next party according to a first transmission sequence, and transmits the processed second class set to the next party according to a second transmission sequence.
This step corresponds to the second round of interaction in the illustrated embodiment of Table one.
In step S130, "each party processes the received first class set and second class set through its own private key," the received first class set and second class set "shall be the first class set and second class set received after the transfer operation in step S120, or the first class set and second class set received after the last transfer operation.
The first transfer order and the second transfer order refer to transfer orders of the sets on a logic closed ring formed by the N parties, the transfer orders can be clockwise or anticlockwise, the first transfer order is one of the transfer orders, and the second transfer order is the other transfer order.
For example, when there are three data fusion participants, the step S130 performs 1 round of transmission, and a logical closed loop formed by the three parties is shown in fig. 2A; when the number of the participating parties of data fusion is four, the step S130 performs 2 rounds of transfer, and the logical closed loop formed by the four parties may be as shown in fig. 2B.
The first transmission direction in step S102 may be a clockwise direction, and the second transmission direction may be a counterclockwise direction. Of course, the first transmission direction may be a counterclockwise direction, and the second transmission direction may be a clockwise direction.
In some embodiments, the order of the data in the collection is not disturbed by either party when the collection is passed to the next party in steps S120 and S130.
In steps S120, S130 and S140 described below, the set is processed "by its own private key", that is, the data in the set is processed. In some embodiments, the processing mode may be an exponentiation, in which the number corresponding to the private key is an exponent and the number corresponding to the data in the set is a base number. In some occasions with higher requirements on data safety, the processing mode can also be a point doubling operation of an elliptic curve. The method has the following characteristics no matter power operation or point doubling operation of an elliptic curve: the private keys of all parties have no influence on the processing sequence of the data on the results obtained after the multiple rounds of transmission.
S140: each party processes the currently received first class set and second class set through a private key of the party, performs first set operation on the processed first class set and second class set, and sends set operation results to all parties except the party in the N parties.
This step corresponds to the third round of interaction in the illustrated embodiment of Table one.
After going through steps S120, S130 and S140, each party receives the first class set and the second class set. After processing the sets in step S130, each of the first class set and the second class set is processed by the multi-party private key.
S150: and each party executes a second set operation according to the received set operation result to obtain a multi-party fusion result.
This step corresponds to the first set operation after three rounds of interaction in the embodiment shown in Table one.
The first set operation in step S140 and the second set operation in step S150 may be an intersection operation or a union operation, which is determined according to actual requirements.
After each party in step S140 sends the set operation result to all the parties except the party itself, each party receives the operation results of M sets (the sum of the number of the first set and the second set is M) from the N-1 party, and step S150 combines the first set and the second set when the party performs the first set operation, and each party can know the operation results of N × M sets, that is, the fusion result of the multi-party data is obtained.
The fused set of multi-party data can be provided to a special organization, and the special organization provides data services for users needing the data information. The special mechanism can have the authority to obtain the private keys of all parties, and then the data of all parties can be analyzed from the fused set.
In the method for fusing multi-party private data provided in the embodiment of the present specification, each party randomly splits its own private data set into two types of sets, and each party processes its own two types of sets by using its own private key, then transmits the processed first type of set to the next party in a positive order, and transmits the second type of set to the next party in a reverse order; each party also carries out N-2 rounds of data interaction, and in each round of interaction, each party processes the received two types of sets through a private key of each party, transmits the first type of set to the next party according to a positive sequence and transmits the second type of set to the next party according to a negative sequence; each party processes the received two types of sets through the private key of the party, further performs set operation on the two types of sets after processing, and sends the operation result to other parties; and each party executes the set operation again according to the received set operation result to obtain a multi-party fusion result. In the process of the scheme, all parties cannot acquire intersection or union information of any two parties, so that the safety of private data fusion is improved.
In some embodiments, the multi-party data fusion process needs to provide the corresponding locations of the private data of the parties in the fused data set in addition to the fused data set. To this end, as shown in fig. 3, the following steps may be performed:
s160: each party identifies the corresponding positions of the elements in the first class set and the second class set in the multi-party fusion result when the parties perform the first set operation, transmits the position identification results of the elements in the first class set to the next party according to a first transmission sequence, and transmits the position identification results of the elements in the second class set to the next party according to a second transmission sequence.
The method corresponds to the fourth round of interaction in the embodiment illustrated in table one.
For example, in the embodiment illustrated in Table one, nail is paired with B in the third round 3 And C 3 * The set operation is executed, and the "elements in the first class set and the second class set when executing the first set operation by itself" in this step S160 means the set B 3 And C 3 * Of (1).
In this stepThe "identify" operation is simply to see if they are the same. For example, set B 3 In the middle has elementsThe corresponding positions of these elements in the fused result are identified separately.
S170: and each party marks the corresponding position of the private data set of the party in the multi-party fusion result according to the received position identification results of the elements in the first-class set and the second-class set.
This step corresponds to the first set operation after three rounds of interaction in the embodiment shown in Table one.
In some embodiments, before performing step S110, each party converts data in its own raw data set into private data, thereby obtaining a private data set. The specific method can be as follows: acquiring a target data set, namely an original data set; carrying out disorder processing on data in the target data set; and converting the target data set subjected to out-of-order processing into a private data set. The elliptic curve and random point generating function can be agreed with other parties in the N parties, and then the original data set is converted into the private data set by adopting the elliptic curve and random point generating function.
The specific method can be understood by referring to the specific embodiment corresponding to table one, and is not described in detail.
In some embodiments, in order to prevent private data obtained by converting the same data of the same party during each data fusion task from being the same content, so that the data is easy to leak, each party may obtain a shared key before converting data in its original data set into the private data, where the shared key is determined by N participating parties performing private data fusion together; and converting the target data set into the private data set by the shared key.
For example, in some embodiments, the shared key may be a product of private keys of the parties, or a sum of private keys of the parties, or may also be 1024 times the number of data fusion participants. The agreement of the shared key may be various, and this specification does not limit this.
The following describes a multi-party private data fusion method provided in this specification, taking one of the N parties as an example. The description of the steps and the beneficial effects of the method can be understood by referring to the embodiment illustrated in fig. 1, which is not described in detail below.
As shown in fig. 4, the method includes the following steps.
S410: the method includes the steps that the private data set of the user is divided into a first class set and a second class set.
S420: the first class set of the self is processed through the private key of the self and is transmitted to the next party according to a first transmission sequence, the second class set of the self is processed through the private key of the self and is transmitted to the next party according to a second transmission sequence, and the second transmission sequence is opposite to the first transmission sequence.
S430: performing N-2 rounds of data interaction: in each round of processing, each party processes the received first class set and the second class set through a private key of the party, transmits the processed first class set to the next party according to a first transmission sequence, and transmits the processed second class set to the next party according to a second transmission sequence.
S440: and processing the currently received first class set and second class set through a private key of the self, executing first set operation on the processed first class set and second class set, and sending set operation results to all the parties except the self in the N parties.
S450: and executing a second set operation according to the received set operation result to obtain a multi-party fusion result.
In some embodiments, the following steps are also included as shown in fig. 4.
S460: and identifying the corresponding positions of the elements in the first class set and the second class set in the multi-party fusion result when the first class set operation is executed by the self, transmitting the position identification results of the elements in the first class set to the next party according to a first transmission sequence, and transmitting the position identification results of the elements in the second class set to the next party according to a second transmission sequence.
S470: and marking the corresponding position of the private data set of the user in the multi-party fusion result according to the received position identification results of the elements in the first-class set and the second-class set.
In some embodiments, before step S410, a target data set may also be obtained; carrying out disorder processing on data in the target data set; and converting the target data set subjected to out-of-order processing into a private data set.
In some embodiments, the "converting the out-of-order processed target data set into a private data set" may be: negotiating elliptic curve and random point generating functions with other parties in the N parties; and converting the original data set into a private data set by adopting an elliptic curve and a random point generating function.
In some embodiments, the "converting the out-of-order processed target data set into the private data set" may be: acquiring a shared key, wherein the shared key is determined by N participants performing private data fusion together; and converting the target data set into the private data set by the shared key.
The embodiment of the present specification further provides a multi-party privacy data fusion device, which may be used to implement the multi-party privacy data fusion method shown in fig. 4. The detailed description and advantages of the apparatus can be understood with reference to the embodiment illustrated in fig. 1, which is not repeated herein. As shown in fig. 5A, the apparatus includes a splitting unit 501, a first interacting unit 502, a second interacting unit 503, a third interacting unit 504, and a fusing unit 505.
The splitting unit 501 is configured to split the private data set of itself into a first class set and a second class set.
The first interaction unit 502 is configured to process a first class set of itself through a private key of itself and transmit the first class set to a next party according to a first transmission order, and process a second class set of itself through a private key of itself and transmit the second class set to the next party according to a second transmission order, where the second transmission order is opposite to the first transmission order.
The second interaction unit 503 is configured to perform N-2 rounds of data interaction: in each round of processing, each party processes the received first class set and the second class set through a private key of the party, transmits the processed first class set to the next party according to a first transmission sequence, and transmits the processed second class set to the next party according to a second transmission sequence.
The third interaction unit 504 is configured to process the currently received first class set and second class set through a private key of the third interaction unit, perform first set operation on the processed first class set and second class set, and send set operation results to all parties except the third interaction unit in the N parties.
The fusion unit 505 is configured to perform a second set operation according to the received set operation result to obtain a multi-party fusion result.
In some embodiments, as shown in fig. 5B, the multi-party privacy data fusion apparatus further comprises a recognition unit 506 and a marking unit 507.
The identifying unit 506 is configured to identify positions of elements in the first class set and the second class set corresponding to the multi-party fusion result when the first class set performs the first set operation, transmit the position identification results of the elements in the first class set to the next party according to the first transmission order, and transmit the position identification results of the elements in the second class set to the next party according to the second transmission order.
The marking unit 507 is configured to mark, according to the received position identification results of the elements in the first-class set and the second-class set, a corresponding position of the private data set of the marking unit in the multi-party fusion result.
In some embodiments, as shown in fig. 5B, the multi-party privacy data fusion apparatus further includes a first obtaining unit 508, an out-of-order unit 509, and a converting unit 510.
The first obtaining unit 508 is configured to obtain a target data set. The out-of-order unit 509 is configured to perform out-of-order processing on the data in the target data set. The converting unit 510 is configured to convert the target data set after the out-of-order processing into a private data set.
In some embodiments, as shown in fig. 5B, the converting unit 510 includes an agreeing unit 511 and a first converting subunit 512.
The agreeing unit 511 is configured to agree on an elliptic curve and a random point generating function with the rest of the N parties. The first converting subunit 512 is configured to convert the original data set into the private data set by using the elliptic curve and the random point generating function.
In some embodiments, as shown in fig. 5B, the conversion unit 510 includes a second obtaining sub-unit 513 and a second converting sub-unit 514.
The second obtaining subunit 513 is configured to obtain a shared key, where the shared key is determined jointly by the N participants performing the private data fusion. The second converting subunit 514 is further configured to convert the target data set into a private data set through the shared key.
An embodiment of the present invention further provides an electronic device, as shown in fig. 6, the electronic device may include a processor 61 and a memory 62, and further include a communication module 63. Wherein the processor 61 and the memory 62 may be connected by a bus or other means, as exemplified by the bus connection in fig. 6.
The memory 62, which is a non-transitory computer readable storage medium, may be used to store non-transitory software programs, non-transitory computer executable programs, and modules, such as program instructions/modules corresponding to the multi-party private data fusion method in the embodiment of the present invention (for example, the splitting unit 501, the first interacting unit 502, the second interacting unit 503, the third interacting unit 504, and the fusion unit 505 shown in fig. 5A). The processor 61 executes various functional applications and data processing of the processor by running non-transitory software programs, instructions and modules stored in the memory 62, so as to implement the multi-party private data fusion method in the above method embodiment.
The memory 62 may include a storage program area and a storage data area, wherein the storage program area may store an operating system, an application program required for at least one function; the storage data area may store data created by the processor 61, and the like. Further, the memory 62 may include high speed random access memory, and may also include non-transitory memory, such as at least one magnetic disk storage device, flash memory device, or other non-transitory solid state storage device. In some embodiments, the memory 62 may optionally include memory located remotely from the processor 61, and these remote memories may be connected to the processor 61 via a network. Examples of such networks include, but are not limited to, the internet, intranets, local area networks, mobile communication networks, and combinations thereof.
The one or more modules are stored in the memory 62 and when executed by the processor 61 perform a multi-party private data fusion method as in the embodiment shown in fig. 4.
The details of the electronic device may be understood with reference to the corresponding related description and effects in the embodiment of fig. 4, and are not described herein again.
It will be understood by those skilled in the art that all or part of the processes of the methods of the embodiments described above can be implemented by a computer program, which can be stored in a computer-readable storage medium, and when executed, can include the processes of the embodiments of the methods described above. The storage medium may be a magnetic Disk, an optical Disk, a Read-Only Memory (ROM), a Random Access Memory (RAM), a Flash Memory (Flash Memory), a Hard Disk (Hard Disk Drive, abbreviated as HDD), a Solid State Drive (SSD), or the like; the storage medium may also comprise a combination of memories of the kind described above.
In the 90 s of the 20 th century, improvements in a technology could clearly distinguish between improvements in hardware (e.g., improvements in circuit structures such as diodes, transistors, switches, etc.) and improvements in software (improvements in process flow). However, as technology advances, many of today's process flow improvements have been seen as direct improvements in hardware circuit architecture. Designers almost always obtain a corresponding hardware circuit structure by programming an improved method flow into the hardware circuit. Thus, it cannot be said that an improvement in the process flow cannot be realized by hardware physical modules. For example, a Programmable Logic Device (PLD), such as a Field Programmable Gate Array (FPGA), is an integrated circuit whose Logic functions are determined by programming the Device by a user. A digital system is "integrated" on a PLD by the designer's own programming without requiring the chip manufacturer to design and fabricate a dedicated integrated circuit chip 2. Furthermore, nowadays, instead of manually manufacturing an Integrated Circuit chip, such Programming is often implemented by "logic compiler" software, which is similar to a software compiler used in program development, but the original code before compiling is also written in a specific Programming Language, which is called Hardware Description Language (HDL), and the HDL is not only one kind but many kinds, such as abll (Advanced boot Expression Language), AHDL (alternate hard Description Language), traffic, CUPL (computer universal Programming Language), HDCal (Java hard Description Language), lava, lola, HDL, PALASM, software, rhydl (Hardware Description Language), and vhul-Language (vhyg-Language), which is currently used commonly. It will also be apparent to those skilled in the art that hardware circuitry for implementing the logical method flows can be readily obtained by a mere need to program the method flows with some of the hardware description languages described above and into an integrated circuit.
The embodiments in the present specification are described in a progressive manner, and the same and similar parts among the embodiments can be referred to each other, and each embodiment focuses on the differences from the other embodiments.
The systems, devices, modules or units described in the above embodiments may be implemented by a computer chip or an entity, or by a product with certain functions.
For convenience of description, the above devices are described as being divided into various units by function, respectively. Of course, the functionality of the various elements may be implemented in the same one or more pieces of software and/or hardware in the practice of the present application.
From the above description of the embodiments, it is clear to those skilled in the art that the present application can be implemented by software plus a necessary general hardware platform. Based on such understanding, the technical solutions of the present application may be essentially or partially implemented in the form of software products, which may be stored in a storage medium, such as ROM/RAM, magnetic disk, optical disk, etc., and include instructions for causing a computer device (which may be a personal computer, a server, or a network device, etc.) to execute the methods of some parts of the embodiments of the present application.
The application is operational with numerous general purpose or special purpose computing system environments or configurations. For example: personal computers, server computers, hand-held or portable devices, tablet-type devices, multiprocessor systems, microprocessor-based systems, set top boxes, programmable consumer electronics, network PCs, minicomputers, mainframe computers, distributed computing environments that include any of the above systems or devices, and the like.
The application may be described in the general context of computer-executable instructions, such as program modules, being executed by a computer. Generally, program modules include routines, programs, objects, components, data structures, etc. that perform particular tasks or implement particular abstract data types. The application may also be practiced in distributed computing environments where tasks are performed by remote processing devices that are linked through a communications network. In a distributed computing environment, program modules may be located in both local and remote computer storage media including memory storage devices.
Although the present application has been described in terms of embodiments, those of ordinary skill in the art will recognize that there are numerous variations and modifications of the present application without departing from the spirit of the application, and it is intended that the appended claims encompass such variations and modifications without departing from the spirit of the application.
Claims (17)
1. A multi-party privacy data fusion method is characterized in that the number of participants of privacy data fusion is N, wherein N is an integer greater than or equal to 3, and the method comprises the following steps:
each party in the N parties randomly scrambles original data in the private data set of the party and splits the original data into a first class set and a second class set;
each party in the N parties processes a first class set of the each party through a private key of the each party and transmits the first class set to the next party according to a first transmission sequence, processes a second class set of the each party through the private key of the each party and transmits the second class set to the next party according to a second transmission sequence, wherein the second transmission sequence is opposite to the first transmission sequence;
each of the N parties performs N-2 rounds of data interaction: in each round of processing, each party processes the received first class set and the second class set through a private key of each party, transmits the processed first class set to the next party according to a first transmission sequence, and transmits the processed second class set to the next party according to a second transmission sequence;
each party processes the currently received first class set and second class set through a private key of the party, performs first set operation on the processed first class set and second class set, and sends set operation results to all parties except the party in the N party; the first set operation is a union set operation;
each party executes a second set operation according to the received set operation result to obtain a multi-party fusion result; the second set operation is a union set operation.
2. The method of claim 1, after each party performs a second set operation according to the received set operation result to obtain a multi-party fusion result, further comprising:
each party identifies the corresponding positions of the elements in the first class set and the second class set in the multi-party fusion result when the party executes the first set operation, transmits the position identification results of the elements in the first class set to the next party according to the first transmission sequence, and transmits the position identification results of the elements in the second class set to the next party according to the second transmission sequence;
and each party marks the corresponding position of the private data set of the party in the multi-party fusion result according to the received position identification results of the elements in the first-class set and the second-class set.
3. The method of claim 1, wherein before each of the N parties splits its own set of private data into the first class set and the second class set, respectively, further comprising:
each party acquires a target data set of the party;
all parties carry out disorder processing on the data in the target data set;
and each party converts the target data set subjected to the out-of-order processing into a private data set.
4. The method of claim 3, wherein the parties convert the out-of-order processed target data set into a private data set, comprising:
the N parties agree on an elliptic curve and a random point generating function;
and each party converts the original data set of the party into a private data set by adopting the elliptic curve and the random point generating function.
5. The method of claim 3, wherein the parties convert the out-of-order processed target data set into a private data set, comprising:
the N parties jointly determine a shared secret key;
and each party converts the target data set into a private data set through the shared secret key.
6. A multi-party private data fusion method is characterized by comprising the following steps:
randomly disordering original data in the private data set of the user, and splitting the original data into a first class set and a second class set;
processing a first type set of the self through a private key of the self, transmitting the first type set to a next party according to a first transmission sequence, processing a second type set of the self through the private key of the self, and transmitting the second type set to the next party according to a second transmission sequence, wherein the second transmission sequence is opposite to the first transmission sequence;
and performing N-2 rounds of data interaction: in each round of processing, each party processes the received first class set and the second class set through a private key of each party, transmits the processed first class set to the next party according to a first transmission sequence, and transmits the processed second class set to the next party according to a second transmission sequence; the number of the participants for privacy data fusion is N, and N is an integer greater than or equal to 3;
processing a currently received first class set and a currently received second class set through a private key of the N party, executing first set operation on the processed first class set and the processed second class set, and sending set operation results to all the N parties except the N party; the first set operation is a union set operation;
executing a second set operation according to the received set operation result to obtain a multi-party fusion result; the second set operation is a union set operation.
7. The method of claim 6, after performing a second set operation according to the received set operation result to obtain a multi-party fusion result, further comprising:
identifying the corresponding positions of the elements in the first class set and the second class set in the multi-party fusion result when the first class set operation is executed by the self, transmitting the position identification result of the elements in the first class set to the next party according to the first transmission sequence, and transmitting the position identification result of the elements in the second class set to the next party according to the second transmission sequence;
and marking the corresponding position of the private data set of the user in the multi-party fusion result according to the received position identification results of the elements in the first-class set and the second-class set.
8. The method of claim 6, wherein before splitting the private data set of the user into the first class set and the second class set, the method further comprises:
acquiring a target data set;
carrying out disorder processing on the data in the target data set;
and converting the target data set subjected to out-of-order processing into a private data set.
9. The method of claim 8, wherein converting the out-of-order processed target data set into a private data set comprises:
negotiating elliptic curve and random point generating functions with the rest of the N parties;
and converting the original data set into a private data set by adopting the elliptic curve and the random point generating function.
10. The method of claim 8, wherein converting the out-of-order processed target data set into a private data set comprises:
acquiring a shared key, wherein the shared key is determined by N participants performing private data fusion together;
and converting the target data set into a private data set through the shared secret key.
11. A multi-party private data fusion apparatus, comprising:
the splitting unit is used for randomly disordering original data in the private data set of the splitting unit and splitting the original data into a first class set and a second class set;
the first interaction unit is used for processing the first type set of the first interaction unit through the private key of the first interaction unit and transmitting the first type set to the next party according to a first transmission sequence, and processing the second type set of the first interaction unit through the private key of the first interaction unit and transmitting the second type set to the next party according to a second transmission sequence, wherein the second transmission sequence is opposite to the first transmission sequence;
the second interaction unit is used for performing N-2 rounds of data interaction: in each round of processing, each party processes the received first class set and the second class set through a private key of each party, transmits the processed first class set to the next party according to a first transmission sequence, and transmits the processed second class set to the next party according to a second transmission sequence; the number of the participants for private data fusion is N, and N is an integer greater than or equal to 3;
the third interaction unit is used for processing the currently received first class set and second class set through a private key of the third interaction unit, executing first set operation on the processed first class set and second class set, and sending set operation results to all parties except the third interaction unit in the N parties; the first set operation is a union set operation;
the fusion unit is used for executing second set operation according to the received set operation result to obtain a multi-party fusion result; the second set operation is a union set operation.
12. The apparatus of claim 11, further comprising:
the identification unit is used for identifying the corresponding positions of the elements in the first class set and the second class set in the multi-party fusion result when the identification unit executes the first set operation, transmitting the position identification results of the elements in the first class set to the next party according to the first transmission sequence, and transmitting the position identification results of the elements in the second class set to the next party according to the second transmission sequence;
and the marking unit is used for marking the corresponding position of the private data set of the marking unit in the multi-party fusion result according to the received position identification results of the elements in the first-class set and the second-class set.
13. The apparatus of claim 11, further comprising:
a first acquisition unit configured to acquire a target data set;
the disorder unit is used for carrying out disorder processing on the data in the target data set;
and the conversion unit is used for converting the target data set subjected to the out-of-order processing into the privacy data set.
14. The apparatus of claim 13, wherein the conversion unit comprises:
an agreement unit for agreeing an elliptic curve and a random point generation function with the rest of the N parties;
and the first conversion subunit is used for converting the original data set into the privacy data set by adopting the elliptic curve and the random point generation function.
15. The apparatus of claim 13, wherein the conversion unit comprises:
a second obtaining subunit, configured to obtain a shared key, where the shared key is determined jointly by N participants performing private data fusion;
the second conversion subunit is further configured to convert the target data set into a private data set through the shared key.
16. An electronic device, comprising:
a communication module, a memory and a processor, wherein the communication module, the processor and the memory are communicatively connected to each other, the memory stores computer instructions, and the processor executes the computer instructions to realize the steps of the method according to any one of claims 6 to 10.
17. A computer storage medium storing computer program instructions which, when executed, implement the steps of the method of any one of claims 6 to 10.
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202110769349.1A CN113515778B (en) | 2021-07-07 | 2021-07-07 | Multi-party privacy data fusion method and device and electronic equipment |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202110769349.1A CN113515778B (en) | 2021-07-07 | 2021-07-07 | Multi-party privacy data fusion method and device and electronic equipment |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN113515778A CN113515778A (en) | 2021-10-19 |
| CN113515778B true CN113515778B (en) | 2022-12-16 |
Family
ID=78066956
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202110769349.1A Active CN113515778B (en) | 2021-07-07 | 2021-07-07 | Multi-party privacy data fusion method and device and electronic equipment |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN113515778B (en) |
Families Citing this family (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN115982747B (en) * | 2023-03-20 | 2023-07-14 | 建信金融科技有限责任公司 | Secure multiparty multiplication method based on communication between participant and trusted third party |
| CN116244753B (en) * | 2023-05-12 | 2023-08-15 | 建信金融科技有限责任公司 | Method, device, equipment and storage medium for intersection of private data |
Family Cites Families (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US10547592B2 (en) * | 2017-01-19 | 2020-01-28 | Hewlett Packard Enterprise Development Lp | Computing a global sum that preserves privacy of parties in a multi-party environment |
| CN110941673B (en) * | 2019-11-26 | 2023-03-24 | 中国人民解放军战略支援部队信息工程大学 | Block chain data structure and task processing method and device |
| CN111931207B (en) * | 2020-08-07 | 2024-04-09 | 北京百度网讯科技有限公司 | Method, device, equipment and storage medium for obtaining privacy set intersection |
| CN113079137B (en) * | 2021-03-22 | 2022-05-27 | 华控清交信息科技(北京)有限公司 | Multi-party privacy intersection method and privacy data processing system |
-
2021
- 2021-07-07 CN CN202110769349.1A patent/CN113515778B/en active Active
Also Published As
| Publication number | Publication date |
|---|---|
| CN113515778A (en) | 2021-10-19 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN111428887B (en) | Model training control method, device and system based on multiple computing nodes | |
| CN113127916A (en) | Data set processing method, data processing device and storage medium | |
| CN113515778B (en) | Multi-party privacy data fusion method and device and electronic equipment | |
| CN111191255B (en) | Information encryption processing method, server, terminal, device and storage medium | |
| CN108038128B (en) | Retrieval method, system, terminal equipment and storage medium of encrypted file | |
| US20180337904A1 (en) | System, methods and software application for sending secured messages on decentralized networks | |
| CN116049626A (en) | Data statistics method, device, equipment and storage medium | |
| CN107196840B (en) | Data processing method, device and equipment | |
| CN113722755B (en) | Data processing system, method, device and equipment for realizing privacy protection | |
| CN114547078A (en) | Federal cross-feature query method, device, medium and equipment based on privacy computation | |
| CN112788001B (en) | Data encryption-based data processing service processing method, device and equipment | |
| CN112231309A (en) | Method, device, terminal equipment and medium for removing duplicate of longitudinal federal data statistics | |
| CN111193741A (en) | Information sending method, information obtaining method, device and equipment | |
| CN116094686B (en) | Homomorphic encryption method, homomorphic encryption system, homomorphic encryption equipment and homomorphic encryption terminal for quantum convolution calculation | |
| CN116095671B (en) | Resource sharing method based on meta universe and related equipment thereof | |
| WO2023215290A1 (en) | Privacy secure batch retrieval using private information retrieval and secure multi-party computation | |
| CN116011028A (en) | Electronic signature method, electronic signature device and electronic signature system | |
| CN113965310A (en) | Method for realizing mixed privacy calculation processing based on controllable de-identification label | |
| US11657297B2 (en) | Computer architecture for communications in a cloud-based correlithm object processing system | |
| CN113094735A (en) | Method for training privacy model | |
| US10853392B2 (en) | Computer architecture for offline node remapping in a cloud-based correlithm object processing system | |
| CN117827884B (en) | Batch data query method and device | |
| US11314537B2 (en) | Computer architecture for establishing data encryption in a correlithm object processing system | |
| US10768957B2 (en) | Computer architecture for establishing dynamic correlithm object communications in a correlithm object processing system | |
| US11409985B2 (en) | Computer architecture for emulating a correlithm object converter in a correlithm object processing system |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| GR01 | Patent grant | ||
| GR01 | Patent grant |