CN112583588B - Communication method and device and readable storage medium - Google Patents
Communication method and device and readable storage medium Download PDFInfo
- Publication number
- CN112583588B CN112583588B CN202011461594.8A CN202011461594A CN112583588B CN 112583588 B CN112583588 B CN 112583588B CN 202011461594 A CN202011461594 A CN 202011461594A CN 112583588 B CN112583588 B CN 112583588B
- Authority
- CN
- China
- Prior art keywords
- certificate
- communication
- password
- password generation
- encrypted
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Active
Links
Images
Classifications
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/08—Key distribution or management, e.g. generation, sharing or updating, of cryptographic keys or passwords
- H04L9/0816—Key establishment, i.e. cryptographic processes or cryptographic protocols whereby a shared secret becomes available to two or more parties, for subsequent use
- H04L9/0819—Key transport or distribution, i.e. key establishment techniques where one party creates or otherwise obtains a secret value, and securely transfers it to the other(s)
- H04L9/0822—Key transport or distribution, i.e. key establishment techniques where one party creates or otherwise obtains a secret value, and securely transfers it to the other(s) using key encryption key
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/04—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks
- H04L63/0428—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks wherein the data content is protected, e.g. by encrypting or encapsulating the payload
- H04L63/0442—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks wherein the data content is protected, e.g. by encrypting or encapsulating the payload wherein the sending and receiving network entities apply asymmetric encryption, i.e. different keys for encryption and decryption
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/06—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols the encryption apparatus using shift registers or memories for block-wise or stream coding, e.g. DES systems or RC4; Hash functions; Pseudorandom sequence generators
- H04L9/0643—Hash functions, e.g. MD5, SHA, HMAC or f9 MAC
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/08—Key distribution or management, e.g. generation, sharing or updating, of cryptographic keys or passwords
- H04L9/0816—Key establishment, i.e. cryptographic processes or cryptographic protocols whereby a shared secret becomes available to two or more parties, for subsequent use
- H04L9/0819—Key transport or distribution, i.e. key establishment techniques where one party creates or otherwise obtains a secret value, and securely transfers it to the other(s)
- H04L9/0825—Key transport or distribution, i.e. key establishment techniques where one party creates or otherwise obtains a secret value, and securely transfers it to the other(s) using asymmetric-key encryption or public key infrastructure [PKI], e.g. key signature or public key certificates
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/08—Key distribution or management, e.g. generation, sharing or updating, of cryptographic keys or passwords
- H04L9/0861—Generation of secret information including derivation or calculation of cryptographic keys or passwords
- H04L9/0866—Generation of secret information including derivation or calculation of cryptographic keys or passwords involving user or device identifiers, e.g. serial number, physical or biometrical information, DNA, hand-signature or measurable physical characteristics
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/32—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials
- H04L9/3263—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials involving certificates, e.g. public key certificate [PKC] or attribute certificate [AC]; Public key infrastructure [PKI] arrangements
- H04L9/3268—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials involving certificates, e.g. public key certificate [PKC] or attribute certificate [AC]; Public key infrastructure [PKI] arrangements using certificate validation, registration, distribution or revocation, e.g. certificate revocation list [CRL]
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Computer Hardware Design (AREA)
- Computing Systems (AREA)
- General Engineering & Computer Science (AREA)
- Power Engineering (AREA)
- Mobile Radio Communication Systems (AREA)
Abstract
The application provides a communication method and device and a readable storage medium. The communication method comprises the following steps: acquiring strategy information sent by a communication object; the policy information includes a target password generation policy encrypted by a first public key; generating a decryption key according to the preset identity information; decrypting the encrypted first private key by the decryption key; the first private key corresponds to the first public key, and an encryption key of the first private key is generated according to the identity information; decrypting the encrypted target password generation strategy through the first private key to obtain the target password generation strategy; generating a communication password according to the target password generation strategy, and encrypting the communication password through a second public key to obtain an encrypted communication password; and sending the encrypted communication password to the communication object. The communication method is used for improving the safety of the secret key and further realizing safe and reliable communication.
Description
Technical Field
The present application relates to the field of communications technologies, and in particular, to a communication method and apparatus, and a readable storage medium.
Background
In the prior art, when data communication is performed between a server and a device, the data to be communicated is usually encrypted by a symmetric communication password. The communication password can be generated through mutual authentication before the server side and the equipment side positively interact data.
However, the encryption key applied to either the server side or the device side is plaintext data, which makes the encryption key easily intercepted and counterfeited by other devices, i.e. the security of the key is low, and thus, the communication is not secure and reliable enough.
Disclosure of Invention
An object of the embodiments of the present application is to provide a communication method and apparatus, and a readable storage medium, so as to improve security of a secret key, thereby implementing secure and reliable communication.
In a first aspect, an embodiment of the present application provides a communication method, including: acquiring strategy information sent by a communication object; the policy information includes a target password generation policy encrypted by a first public key; generating a decryption key according to the preset identity information; decrypting the encrypted first private key by the decryption key; the first private key corresponds to the first public key, and an encryption key of the first private key is generated according to the identity information; decrypting the encrypted target password generation strategy through the first private key to obtain the target password generation strategy; generating a communication password according to the target password generation strategy, and encrypting the communication password through a second public key to obtain an encrypted communication password; and sending the encrypted communication password to the communication object.
In the embodiment of the application, compared with the prior art, the first private key used for decrypting the target password generation strategy encrypted by the first public key is encrypted by the encryption key, and the decryption key corresponding to the encryption key is not plaintext data, so that the identification information is used for field generation when the first private key is required to be used, and further, the security of the first private key is improved under the condition of ensuring the security of the decryption key; on the basis of improving the security of the first private key, the security of a target password generation strategy is also ensured, and the security of the finally generated communication password is also higher; the communication between the two communication parties is also safer and more reliable through the communication password with higher safety.
As a possible implementation manner, before the obtaining of the policy information sent by the communication object, the method further includes: sending at least one selectable password generation policy and a first certificate to the communication object, so that the communication object generates the policy information according to the at least one selectable password generation policy and the first public key in the first certificate; the first certificate is a certificate of the first certificate.
In the embodiment of the application, the communication object feeds back a more reasonable and reliable target password generation strategy based on the selectable password generation strategy by providing the selectable password generation strategy to the communication object.
As a possible implementation, before the sending the at least one selectable password generation policy to the communication object, the method further includes: sending self SSL version information to the communication object; receiving a second certificate returned by the communication object and an SSL protocol version of the communication object; the second certificate is a certificate of the communication object; verifying whether the second certificate is a legal certificate; correspondingly, the sending at least one selectable password generation policy and the first certificate to the communication object includes: and when the second certificate is determined to be a legal certificate, sending at least one selectable password generation strategy and the first certificate to the communication object.
In the embodiment of the application, the certificate of the communication object is verified, so that the certificate of the communication object is guaranteed to be legal, and the communication with the communication object is more safe and reliable.
As a possible implementation manner, the verifying whether the second certificate is a legal certificate includes: acquiring a trust certificate library; judging whether the second certificate belongs to the certificate in the trust certificate library or not; if the second certificate belongs to the certificate in the trust certificate library, determining that the second certificate is a legal certificate; and if the second certificate does not belong to the certificate in the trust certificate library, determining that the second certificate is an illegal certificate.
In the embodiment of the application, the validity of the second certificate is verified through the trust certificate library, so that the verification efficiency and reliability are improved.
As one possible implementation, before the sending the at least one selectable password generation policy and the first certificate to the communication object, the method further includes: and determining the at least one selectable password generation strategy from the password generation strategies stored locally according to preset communication password constraint conditions.
In the embodiment of the application, the initial screening of the password generation strategy stored locally is realized through the communication password constraint condition, and the selection efficiency of the password generation strategy is further improved.
As a possible implementation manner, the policy information further includes signature information generated by the communication object by signing the encrypted target password generation policy through a second private key, and before the policy information is decrypted through the first private key to obtain the communication password generation policy, the method further includes: verifying the signature information through the second public key; correspondingly, the decrypting the encrypted target password generation policy by the first private key to obtain the target password generation policy includes: and after the signature information passes the verification, decrypting the strategy information through the first private key to obtain the target password generation strategy.
In the embodiment of the application, the policy information further includes signature information, and the signature information is verified through the second public key, so that validity verification of the policy information is realized, and the security of the policy information is improved.
As a possible implementation manner, the sending the encrypted communication password to the communication object includes: signing the encrypted communication password through the first private key to generate signature information; and sending the signature information and the encrypted communication password to the communication object.
In the embodiment of the application, when the encrypted communication password is transmitted, the encrypted communication password is signed to generate the signature information, so that the communication object can verify the validity of the encrypted communication password, and the security of the encrypted communication password is improved.
As a possible implementation manner, the decryption key is generated according to preset identity information and a KDF key derivation algorithm.
In the embodiment of the present application, a decryption Key is generated by using a KDF (Key Derivation Function) Key Derivation algorithm, so as to realize fast generation of the decryption Key.
In a second aspect, an embodiment of the present application provides a communication apparatus, including: functional modules for implementing the communication method described in the first aspect and any one of its possible implementation manners.
In a third aspect, an embodiment of the present application provides a readable storage medium, where a computer program is stored, and the computer program, when executed by a computer, performs the method as described in the first aspect and any one of the possible implementation manners of the first aspect.
Drawings
In order to more clearly illustrate the technical solutions of the embodiments of the present application, the drawings that are required to be used in the embodiments of the present application will be briefly described below, it should be understood that the following drawings only illustrate some embodiments of the present application and therefore should not be considered as limiting the scope, and that those skilled in the art can also obtain other related drawings based on the drawings without inventive efforts.
Fig. 1 is a schematic diagram of a communication system provided in an embodiment of the present application;
fig. 2 is a schematic diagram of an electronic device provided in an embodiment of the present application;
fig. 3 is a flowchart of a communication method provided in an embodiment of the present application;
fig. 4 is a functional block diagram of a communication device according to an embodiment of the present disclosure.
An icon: 100-a communication system; 101-a communication device; 102-a server; 200-an electronic device; 201-a memory; 202-a communication module; 203-bus; 204-a processor; 400-a communication device; 401-an acquisition module; 402-a first generation module; 403-a decryption module; 404-a second generation module; 405-a sending module.
Detailed Description
The technical solutions in the embodiments of the present application will be described below with reference to the drawings in the embodiments of the present application. The particular methods of operation in the method embodiments may also be applied to apparatus embodiments or system embodiments. In the description of the present application, "at least one" includes one or more unless otherwise specified. "plurality" means two or more. For example, at least one of A, B and C, comprising: a alone, B alone, a and B in combination, a and C in combination, B and C in combination, and A, B and C in combination. In this application, "/" means "or, for example, A/B may mean A or B; "and/or" herein is merely an association relationship describing an associated object, and means that there may be three relationships, for example, a and/or B, and may mean: a exists alone, A and B exist simultaneously, and B exists alone.
Fig. 1 is a schematic diagram of a communication system 100 according to an embodiment of the present disclosure.
In this embodiment, the communication system 100 may include one or more communication devices 101 and a server 102, each communication device 101 is connected to the server 102, and data communication, such as data transmission, data access and the like, between the communication device 101 and the server 102 may be implemented.
The communication device 101 and the server 102 may communicate with each other by using HTTP (Hyper Text Transfer Protocol over secure Layer).
In order to ensure the security of communication, whether communication between a plurality of communication devices 101 or communication between the communication devices 101 and the server 102, for example: ensuring that the transmitted data is not stolen; to ensure that the transmitted data is not tampered, it is possible to adopt: identity authentication of communication parties, encryption of communication data and other security measures.
Based on this, embodiments of the present application provide a communication method, which improves security and reliability of communication on the basis of ensuring security of a key used to encrypt data. The communication method may be applied to the communication apparatus 101 and also to the server 102. In the prior art, the communication security assurance measures adopted by the server 102 are relatively comprehensive, and therefore, if the communication method is applied to the communication device 101, the effect of improving the security and reliability of communication is better.
Before the communication method is described, an environment in which the communication method operates is described.
Referring to fig. 2, the electronic device 200 includes: memory 201, communication module 202, bus 203, and processor 204. The processor 204, the communication module 202 and the memory 201 are connected by a bus 203.
In the embodiment of the present application, the electronic device 200 may be the server 102, or may also be a terminal (i.e., the communication device 101. when the electronic device 200 is the server 102, for example, a network server, a database server, a cloud server, or a server assembly composed of a plurality of sub-servers, etc., or when the electronic device 200 is the communication device 101, for example, a personal computer, a tablet computer, a smart phone, a personal digital assistant, etc.
In the embodiment of the present application, the memory 201 stores programs required to implement the communication method provided in the embodiment of the present application.
The Memory 201 may include, but is not limited to, a RAM (Random Access Memory), a ROM (Read Only Memory), a PROM (Programmable Read-Only Memory), an EPROM (Erasable Read-Only Memory), an EEPROM (electrically Erasable Read-Only Memory), and the like.
The bus 203 may be an ISA (Industry Standard Architecture) bus, a PCI (Peripheral Component Interconnect) bus, an EISA (Enhanced Industry Standard Architecture) bus, or the like. The bus may be divided into an address bus, a data bus, a control bus, etc. For ease of illustration, only one double-headed arrow is shown in FIG. 2, but this does not indicate only one bus or one type of bus.
The processor 204 is used to execute executable modules, such as computer programs, stored in the memory 201. The method performed by the apparatus according to the processes or definitions disclosed in the embodiments of the present application may be implemented in the processor 204 or implemented by the processor 204. After the processor 204 receives the execution instruction and calls the program stored in the memory 201 through the bus 203, the processor 204 controls the communication module 202 through the bus 203 to implement the flow of the communication method.
The processor 204 may be an integrated circuit chip having signal processing capabilities. The Processor 204 may be a general-purpose Processor including a Central Processing Unit (CPU), a Network Processor (NP), and the like; but may also be a digital signal processor, an application specific integrated circuit, an off-the-shelf programmable gate array or other programmable logic device, discrete gate or transistor logic, discrete hardware components. Which may implement or perform the methods, steps, and logic blocks disclosed in the embodiments of the present application. A general purpose processor may be a microprocessor or the processor may be any conventional processor or the like.
The components and configuration of electronic device 200 shown in FIG. 2 are exemplary only, and not limiting, as electronic device 200 may have other components and configurations as desired.
With reference to fig. 3, a flowchart of a communication method according to an embodiment of the present application is provided based on the introduction of the hardware operating environment and the application scenario, where the communication method includes: step 301, step 302, step 303, step 304, step 305 and step 306.
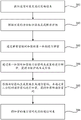
Step 301: and acquiring the strategy information sent by the communication object. The policy information includes a target password generation policy encrypted by the first public key.
Step 302: and generating a decryption key according to the preset identity information.
Step 303: the encrypted first private key is decrypted by the decryption key. The first private key corresponds to the first public key, and an encryption key of the first private key is generated according to the identity information.
Step 304: and decrypting the encrypted target password generation strategy through the first private key to obtain the target password generation strategy.
Step 305: and generating a communication password according to the target password generation strategy, and encrypting the communication password through the second public key to obtain an encrypted communication password.
Step 306: and sending the encrypted communication password to the communication object.
Compared with the prior art, the first private key used for decrypting the target password generation strategy encrypted by the first public key is encrypted by the encryption key, the decryption key corresponding to the encryption key is not plaintext data, and when the first private key is required to be used, the first private key is generated on site by using the identity identification information, so that the safety of the first private key is improved under the condition of ensuring the safety of the decryption key; on the basis of improving the security of the first private key, the security of a target password generation strategy is also ensured, and the security of the finally generated communication password is also higher; the communication between the two communication parties is also safer and more reliable through the communication password with higher safety.
The communication method will be described in detail with reference to steps 301 to 306.
Assuming that the communication method is applied to the server 102, the communication object is any communication device 101; assuming that the communication method is applied to the communication apparatus 101, the communication object is the server 102. In order to facilitate understanding of the technical solutions provided in the embodiments of the present application, in the following embodiments, any communication device 101 is used as an execution subject of the communication method, and the server 102 is used as the communication object.
The policy information transmitted by the server 102 includes a target password generation policy encrypted by the first public key. The target password generation policy is a generation policy corresponding to a communication password used for symmetric encrypted communication between the server 102 and the communication device 101, and therefore, the generation policy may include: encryption schemes such as symmetric encryption algorithms.
The first public key may be understood as a public key corresponding to the first private key of the communication device 101, such as: the first private key is the private key of the certificate of the communication device 101, and the first public key is the public key of the certificate of the communication device 101. The first private key may be understood as a private key in asymmetric encryption, and correspondingly, the first public key may be understood as a public key corresponding to the private key in asymmetric encryption, the private key is used by a certificate holder (i.e., the communication device 101), and the public key is used by an object (i.e., the server 102) interacting with the certificate holder.
As an alternative embodiment, the server 102 selects a target password generation policy from the selectable password generation policies and then sends the selected target password generation policy to the communication device 101. The selectable password generation policy may be determined by the server 102 or the communication device 101. If determined by server 102, server 102 may determine an alternative password generation policy from the locally stored password generation policies. If it is determined by the communication device 101, before step 301, the method further comprises: sending the at least one selectable password generation policy and the first certificate to the communication object, so that the communication object generates the policy information according to the at least one selectable password generation policy and the first public key in the first certificate; the first certificate is its own certificate.
The first certificate may be understood as a certificate of the communication device 101, which corresponds to the first public key and the first private key.
As an optional implementation, the determining of the at least one selectable password generation policy includes: and determining at least one selectable password generation strategy from the password generation strategies stored locally according to the preset communication password constraint conditions.
The locally stored password generation policy may be a symmetric encryption algorithm supported by the communication device 101.
Correspondingly, the communication password constraint condition may be the encryption degree, the complexity, or the like of the communication password. Generally, a symmetric encryption algorithm may set rating information for characterizing the degree of encryption or the encryption complexity, and based on the rating information, the degree of encryption or the encryption complexity of each encryption algorithm may be determined. Such as: in the constraint condition, the encryption degree needs to be greater than a preset degree, or the encryption complexity needs to be greater than a preset complexity, or both the encryption degree and the encryption complexity need to reach a preset level or value.
In the embodiment of the application, the initial screening of the password generation strategy stored locally is realized through the communication password constraint condition, and the selection efficiency of the password generation strategy is further improved.
After the communication device 101 determines at least one selectable password generation policy, the at least one selectable password generation policy and a first certificate are sent to the server 102, wherein the first certificate functions as: the server 102 is made aware of the first public key corresponding to the first private key.
For the server 102, after receiving the at least one selectable password generation policy, a target password generation policy is determined from the at least one selectable password generation policy. When the server 102 selects the target password generation policy, the selection may also be performed based on preset selection conditions, for example: a password generation policy supported by server 102; the communication cipher complexity and encryption level required by the server 102.
After the server 102 determines the target password generation policy, the target password generation policy is encrypted by the first public key and then transmitted to the communication apparatus 101.
In this embodiment of the present application, if the server 102 cannot determine the target password generation policy based on the selectable password generation policies, for example: the encryption complexity of the alternative password generation policy is too low, at which point the server 102 may again interact with the communication device 101 requesting a new alternative password generation policy that satisfies the conditions. Or, the server 102 directly determines a selectable password generation policy, and then sends the password generation policy to the communication device 101, and after the feedback of the communication device 101, the server 102 determines a target password generation policy from the password generation policy.
In the present embodiment, the identity of the server 102 is also verifiable to the communication device 101, since it is not excluded that the server 102 is in an impersonation or insecure situation. Therefore, before step 301, the method further comprises: the communication device 101 sends SSL (Secure socket layer) version information of itself to the server 102; receiving a second certificate returned by the server 102 and the SSL protocol version of the server 102; the second certificate is a certificate of the server 102; verifying whether the second certificate is a legal certificate. Correspondingly, at least one selectable password generation strategy and the first certificate are sent to the communication object, and the method comprises the following steps: upon determining that the second certificate is a legitimate certificate, at least one alternative password generation policy and the first certificate are sent to server 102.
The SSL is a protocol used in the HTTP-based communication method, and other protocols may be used in other communication methods, which are not limited in the embodiments of the present application.
The communication device 101 synchronizes its SSL version to the server 102, and the server 102 also synchronizes its SSL version to the communication device 101 to ensure consistency of the SSL versions.
After the server 102 determines the consistency of the versions, the second certificate is sent to the communication device 101, and the communication device 101 verifies the validity of the certificate. As an optional implementation, the verification process includes: acquiring a trust certificate library; judging whether the second certificate belongs to a certificate in a trust certificate library or not; if the second certificate belongs to the certificate in the trust certificate library, determining the second certificate as a legal certificate; and if the second certificate does not belong to the certificate in the trust certificate library, determining that the second certificate is an illegal certificate.
In this embodiment, the communication device 101 stores a trust certificate repository, where the certificates in the trust certificate repository are all legal certificates, and if the second certificate is a certificate in the certificate repository, the certificate is a legal certificate; if the second certificate is not a certificate in the certificate store, it is not a legitimate certificate.
In the embodiment of the application, the validity of the second certificate is verified through the trust certificate library, so that the verification efficiency and reliability are improved.
In addition to this alternative embodiment, the communication device 101 may also authenticate in other ways, such as: a third party Certificate Authority, which may be a third party CA (Certificate Authority), is requested to verify the legitimacy of the Certificate.
In addition to the validity verification, the communication device 101 may also verify the validity of the second certificate, and the validity verification may adopt a verification method that is mature in the field and is not described in detail here.
In the embodiment of the present application, after the communication device 101 sends the first certificate to the server 102, the server 102 may also verify the validity, and the like of the first certificate in the same way as the communication device 101, and the description is not repeated here.
In this embodiment of the application, after encrypting the target password generation policy, the server 102 sends the encrypted target password generation policy to the communication device 101, and in order to ensure the security and the validity of the encrypted target password generation policy, the server 102 may further sign the encrypted target password generation policy by using a second private key corresponding to a second certificate, generate signature information, and based on the signature information, before step 301, the method further includes: and verifying the signature information through the second public key.
The second public key is a public key corresponding to the second certificate, and the second public key and the second private key also adopt an asymmetric encryption algorithm. When the server 102 signs, the encrypted target password generation policy may be subjected to hash calculation to obtain a hash value, and then the hash value is signed by the second private key. Therefore, when the communication device 101 verifies, the hash value may be decrypted by the second public key to obtain a corresponding hash value; then, carrying out hash calculation by using an encrypted target password generation strategy to obtain a hash value; comparing the two hash values, and if the comparison result is consistent, determining that the signature information is verified and the encrypted target password generation strategy is valid data; and if the comparison result is inconsistent, determining that the signature information is not verified, and determining that the encrypted target password generation strategy is invalid data.
Correspondingly, if the signature information is not verified, the subsequent steps are not executed; if the signature information is verified, the following steps, step 303, are continued, including: and after the signature information passes the verification, decrypting the strategy information through the first private key to obtain a target password generation strategy.
In step 302, the preset identification information may be the identification of the communication device 101, or may be a more secure identification generated by performing various complex transformations on the identification of the communication device 101, which is not limited in this embodiment of the present application.
As an alternative implementation, step 302 includes: and generating a decryption key according to the preset identity information and a KDF key derivation algorithm.
In the embodiment of the present application, other implementable key derivation algorithms, a key derivation algorithm customized by the communication device 101, and the like may be used instead of the KDF key derivation algorithm, which is not limited in the embodiment of the present application.
In step 303, the encrypted first private key is decrypted by the decryption key to obtain the first private key. And the encryption key of the first private key is generated according to the identity identification information.
The encryption key and the decryption key of the first private key may be understood as symmetrically encrypted keys. When the same key derivation algorithm is based on the same information, the derived keys are the same, and therefore, the consistency of the encryption key and the decryption key can be ensured.
In step 304, the encrypted target password generation policy is decrypted by the first private key. It is understood that the first private key and the first public key are asymmetric keys, and therefore, the server 102 uses the first public key to encrypt information, and the communication device 101 can use the first private key to decrypt the information, so as to obtain the target password generation policy.
In step 305, the communication device 101 may generate a corresponding communication password according to the encryption algorithm specified in the target password generation policy. This process is the same as the key derivation process, and will not be described again.
Further, in step 306, the communication device 101 may synchronize the encrypted communication password to the server 102.
It can be understood that, since the communication device 101 needs to synchronize the communication password to the server 102, in order to ensure the security of the communication password during the synchronization process, the communication device 101 may encrypt the communication password by using the second public key, and then the server 102, after receiving the communication password, decrypts the communication password by using the second private key corresponding to the second public key to obtain the communication password. Namely, the key of the communication cipher adopts an asymmetric encryption mode.
In the embodiment of the present application, for the communication device 101, the security assurance measure of the communication password may be to perform signature on the basis of encryption in addition to encryption. Thus, as an alternative embodiment, step 306 includes: signing the encrypted communication password through a first private key to generate signature information; the signature information and the encrypted communication password are sent to the server 102.
The communication device 101 calculates a hash value based on the encrypted communication password, and then signs the hash value with the first private key, thereby completing generation of the signature information.
After the communication device 101 synchronizes the signature information and the encrypted communication password to the server 102, the server 102 verifies the signature information with the first public key: decrypting the hash value in the signature information by using the first public key, calculating the hash value by using the encrypted communication password, comparing the two hash values, and if the comparison result is consistent, verifying the signature information; if the comparison result is not consistent, the signature information is not verified.
After the signature information passes the verification, the server 102 decrypts the encrypted communication password by using the second private key to obtain the communication password. If the signature information is not verified, the server 102 may request the communication device 101 to retransmit the encrypted communication password and feed back hint information that the encrypted communication password may be tampered with.
After the server 102 successfully obtains the communication password, corresponding feedback information may be sent to the communication device 101, and then, in the next communication process, the data transmitted between the server 102 and the communication device 101 may be encrypted symmetrically by using the communication password.
As can be seen from the description of the above embodiments, in the communication process between the server 102 and the communication device 101, the communication method provided in the embodiment of the present application does not include any plaintext data, whether it is an encryption key, a decryption key, or a communication password, or a first public key, a second public key, a first private key, and a second private key, that is, the security and reliability of these data are ensured, and further the security and reliability of the communication between the server 102 and the communication device 101 are also ensured.
Referring to fig. 4, an embodiment of the present application further provides a communication apparatus 400, which includes an obtaining module 401, a first generating module 402, a decrypting module 403, a second generating module 404, and a sending module 405.
The obtaining module 401 is configured to: acquiring strategy information sent by a communication object; the policy information includes a target password generation policy encrypted by a first public key. The first generation module 402 is configured to: and generating a decryption key according to the preset identity information. The decryption module 403 is configured to: decrypting the encrypted first private key by the decryption key; the first private key corresponds to the first public key, and an encryption key of the first private key is generated according to the identity information; decrypting the encrypted target password generation strategy through the first private key to obtain the target password generation strategy; the second generation module 404 is configured to: generating a communication password according to the target password generation strategy, and encrypting the communication password through a second public key to obtain an encrypted communication password; the sending module 405 is configured to send the encrypted communication password to the communication object.
In this embodiment of the present application, the sending module 405 is further configured to: sending at least one selectable password generation policy and a first certificate to the communication object, so that the communication object generates the policy information according to the at least one selectable password generation policy and the first public key in the first certificate; the first certificate is a certificate of the first certificate.
In this embodiment of the present application, the sending module 405 is further configured to send SSL version information of itself to the communication object. The communication device 400 further comprises a receiving module, configured to receive a second certificate returned by the communication object and the SSL protocol version of the communication object; the second certificate is a certificate of the communication object; the communication apparatus 400 further comprises a verification module for verifying whether the second certificate is a legal certificate. The sending module 405 is specifically configured to send at least one selectable password generation policy and the first certificate to the communication object when it is determined that the second certificate is a legal certificate.
In this embodiment of the application, the obtaining module 401 is further configured to obtain a trust certificate library; the verification module is specifically used for judging whether the second certificate belongs to the certificate in the trust certificate library; if the second certificate belongs to the certificate in the trust certificate library, determining that the second certificate is a legal certificate; and if the second certificate does not belong to the certificate in the trust certificate library, determining that the second certificate is an illegal certificate.
In this embodiment, the communication device 400 further includes a determining module, configured to determine the at least one selectable password generation policy from the locally stored password generation policies according to a preset communication password constraint condition.
In this embodiment of the present application, the verification module is further configured to verify the signature information through the second public key. The decryption module 403 is further specifically configured to decrypt the policy information through the first private key after the signature information passes verification, so as to obtain the target password generation policy.
In this embodiment, the sending module 405 is specifically configured to: signing the encrypted communication password through the first private key to generate signature information; and sending the signature information and the encrypted communication password to the communication object.
In this embodiment of the present application, the first generating module 402 is specifically configured to: and generating the decryption key according to preset identity information and a KDF key derivation algorithm.
Embodiments of the present application further provide a storage medium, on which one or more programs are stored, and the one or more programs are executable by one or more processors to implement the communication method in the present embodiment.
In the embodiments provided in the present application, it should be understood that the disclosed apparatus and method may be implemented in other ways. The above-described embodiments of the apparatus are merely illustrative, and for example, the division of the units is only one logical division, and there may be other divisions when actually implemented, and for example, a plurality of units or components may be combined or integrated into another system, or some features may be omitted, or not executed. In addition, the shown or discussed mutual coupling or direct coupling or communication connection may be an indirect coupling or communication connection of devices or units through some communication interfaces, and may be in an electrical, mechanical or other form.
In addition, units described as separate parts may or may not be physically separate, and parts displayed as units may or may not be physical units, may be located in one place, or may be distributed on a plurality of network units. Some or all of the units can be selected according to actual needs to achieve the purpose of the solution of the embodiment.
In addition, functional modules in the embodiments of the present application may be integrated together to form an independent part, or each module may exist alone, or two or more modules may be integrated to form an independent part.
In this document, relational terms such as first and second, and the like may be used solely to distinguish one entity or action from another entity or action without necessarily requiring or implying any actual such relationship or order between such entities or actions.
The above description is only an example of the present application and is not intended to limit the scope of the present application, and various modifications and changes may be made by those skilled in the art. Any modification, equivalent replacement, improvement and the like made within the spirit and principle of the present application shall be included in the protection scope of the present application.
Claims (8)
1. A method of communication, comprising:
acquiring strategy information sent by a communication object; the policy information includes a target password generation policy encrypted by a first public key;
generating a decryption key according to the preset identity information;
decrypting the encrypted first private key by the decryption key; the first private key corresponds to the first public key, and an encryption key of the first private key is generated according to the preset identity information;
decrypting the encrypted target password generation strategy through the first private key to obtain the target password generation strategy;
generating a communication password according to the target password generation strategy, and encrypting the communication password through a second public key to obtain an encrypted communication password;
sending the encrypted communication password to the communication object;
before the obtaining of the policy information sent by the communication object, the method further includes:
sending at least one selectable password generation policy and a first certificate to the communication object, so that the communication object generates the policy information according to the at least one selectable password generation policy and the first public key in the first certificate; the first certificate is a certificate of the first certificate;
prior to said sending at least one selectable password generation policy to said communication partner, said method further comprises:
sending self SSL version information to the communication object;
receiving a second certificate returned by the communication object and an SSL protocol version of the communication object; the second certificate is a certificate of the communication object;
verifying whether the second certificate is a legal certificate;
correspondingly, the sending the at least one selectable password generation policy and the first certificate to the communication object includes:
and when the second certificate is determined to be a legal certificate, sending at least one selectable password generation strategy and the first certificate to the communication object.
2. The communication method according to claim 1, wherein the verifying whether the second certificate is a legal certificate comprises:
acquiring a trust certificate library;
judging whether the second certificate belongs to the certificate in the trust certificate library or not;
if the second certificate belongs to the certificate in the trust certificate library, determining that the second certificate is a legal certificate;
and if the second certificate does not belong to the certificate in the trust certificate library, determining that the second certificate is an illegal certificate.
3. The communication method of claim 1, wherein prior to said sending the at least one selectable password generation policy and the first certificate to the communication object, the method further comprises:
and determining the at least one selectable password generation strategy from the password generation strategies stored locally according to preset communication password constraint conditions.
4. The communication method according to claim 1, wherein the policy information further includes signature information generated by the communication object by signing the encrypted target password generation policy with a second private key, and before the policy information is decrypted with the first private key to obtain the target password generation policy, the method further includes:
verifying the signature information through the second public key;
correspondingly, the decrypting the encrypted target password generation policy by the first private key to obtain the target password generation policy includes:
and after the signature information passes the verification, decrypting the strategy information through the first private key to obtain the target password generation strategy.
5. The communication method according to claim 1, wherein the sending the encrypted communication password to the communication object includes:
signing the encrypted communication password through the first private key to generate signature information;
and sending the signature information and the encrypted communication password to the communication object.
6. The communication method according to claim 1, wherein the generating a decryption key according to the preset identification information comprises:
and generating the decryption key according to preset identity information and a KDF key derivation algorithm.
7. A communications apparatus, comprising:
the acquisition module is used for acquiring the strategy information sent by the communication object; the policy information includes a target password generation policy encrypted by a first public key;
the first generation module is used for generating a decryption key according to the preset identity information;
the decryption module is used for decrypting the encrypted first private key through the decryption key; the first private key corresponds to the first public key, and an encryption key of the first private key is generated according to the identity information; decrypting the encrypted target password generation strategy through the first private key to obtain the target password generation strategy;
the second generation module is used for generating a communication password according to the target password generation strategy and encrypting the communication password through a second public key to obtain an encrypted communication password;
a sending module, configured to send the encrypted communication password to the communication object;
the sending module is further configured to: sending self SSL version information to the communication object; receiving a second certificate returned by the communication object and an SSL protocol version of the communication object; the second certificate is a certificate of the communication object; verifying whether the second certificate is a legal certificate; when the second certificate is determined to be a legal certificate, sending at least one selectable password generation strategy and a first certificate to the communication object, so that the communication object generates the strategy information according to the at least one selectable password generation strategy and the first public key in the first certificate; the first certificate is a certificate of the first certificate.
8. A readable storage medium, having stored thereon a computer program which, when executed by a computer, performs the method of any one of claims 1-6.
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202011461594.8A CN112583588B (en) | 2020-12-08 | 2020-12-08 | Communication method and device and readable storage medium |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202011461594.8A CN112583588B (en) | 2020-12-08 | 2020-12-08 | Communication method and device and readable storage medium |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN112583588A CN112583588A (en) | 2021-03-30 |
| CN112583588B true CN112583588B (en) | 2022-06-21 |
Family
ID=75132222
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202011461594.8A Active CN112583588B (en) | 2020-12-08 | 2020-12-08 | Communication method and device and readable storage medium |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN112583588B (en) |
Families Citing this family (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN113645198B (en) * | 2021-07-23 | 2023-12-26 | 天津航远信息技术有限公司 | Computer network information safety monitoring method |
| CN114499859A (en) * | 2022-03-22 | 2022-05-13 | 深圳壹账通智能科技有限公司 | Password verification method, device, equipment and storage medium |
Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN106533659A (en) * | 2015-09-14 | 2017-03-22 | 北京中质信维科技有限公司 | Secret key updating method and system |
| CN110247762A (en) * | 2019-06-20 | 2019-09-17 | 江西金格科技股份有限公司 | A kind of reliable website building method based on SM9 algorithm |
| CN110278080A (en) * | 2019-07-11 | 2019-09-24 | 珠海格力电器股份有限公司 | Method, system and computer readable storage medium for data transmission |
| CN111953705A (en) * | 2020-08-20 | 2020-11-17 | 全球能源互联网研究院有限公司 | Internet of things identity authentication method and device and electric power Internet of things identity authentication system |
Family Cites Families (14)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20070039042A1 (en) * | 2005-08-12 | 2007-02-15 | First Data Corporation | Information-security systems and methods |
| US8861716B2 (en) * | 2010-03-30 | 2014-10-14 | International Business Machines Corporation | Efficient homomorphic encryption scheme for bilinear forms |
| CN103366278B (en) * | 2013-06-04 | 2016-11-23 | 天地融科技股份有限公司 | Process the method and system of operation requests |
| CN106452770B (en) * | 2015-08-12 | 2020-10-13 | 深圳市腾讯计算机系统有限公司 | Data encryption method, data decryption method, device and system |
| CN105337741A (en) * | 2015-10-14 | 2016-02-17 | 四川省宁潮科技有限公司 | Trust device autonomous registering method based on asymmetric algorithm |
| US10270801B2 (en) * | 2016-01-25 | 2019-04-23 | Oath Inc. | Compromised password detection based on abuse and attempted abuse |
| CN107659632B (en) * | 2017-09-19 | 2021-02-05 | 咪咕数字传媒有限公司 | File encryption and decryption method and device and computer readable storage medium |
| CN109412791B (en) * | 2018-11-29 | 2019-11-22 | 北京三快在线科技有限公司 | Key information processing method, device, electronic equipment and computer-readable medium |
| CN110474898B (en) * | 2019-08-07 | 2021-06-22 | 北京明朝万达科技股份有限公司 | Data encryption and decryption and key distribution method, device, equipment and readable storage medium |
| CN110740128B (en) * | 2019-09-27 | 2022-08-23 | 武汉虹识技术有限公司 | Offline data encryption method and device |
| CN111510426A (en) * | 2020-03-06 | 2020-08-07 | 珠海格力电器股份有限公司 | Internet of things distribution network encryption method, device and system, electronic equipment and storage medium |
| CN111723410A (en) * | 2020-06-19 | 2020-09-29 | 深圳前海微众银行股份有限公司 | Hard disk encryption method, hard disk lock system, hard disk encryption device and storage medium |
| CN112016104B (en) * | 2020-07-14 | 2024-04-23 | 北京淇瑀信息科技有限公司 | Encryption method, device and system for financial sensitive data |
| CN111740828B (en) * | 2020-07-29 | 2021-02-12 | 北京信安世纪科技股份有限公司 | Key generation method, device and equipment and encryption and decryption method |
-
2020
- 2020-12-08 CN CN202011461594.8A patent/CN112583588B/en active Active
Patent Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN106533659A (en) * | 2015-09-14 | 2017-03-22 | 北京中质信维科技有限公司 | Secret key updating method and system |
| CN110247762A (en) * | 2019-06-20 | 2019-09-17 | 江西金格科技股份有限公司 | A kind of reliable website building method based on SM9 algorithm |
| CN110278080A (en) * | 2019-07-11 | 2019-09-24 | 珠海格力电器股份有限公司 | Method, system and computer readable storage medium for data transmission |
| CN111953705A (en) * | 2020-08-20 | 2020-11-17 | 全球能源互联网研究院有限公司 | Internet of things identity authentication method and device and electric power Internet of things identity authentication system |
Non-Patent Citations (3)
| Title |
|---|
| Liqun Chen ect..Cross-Domain Password-Based Authenticated Key Exchange Revisited.《2013 Proceedings IEEE INFOCOM》.2013,全文. * |
| 陈铁明等.LogIDStamp:一个基于IBE的日志身份戳系统.《浙江工业大学学报》.2011,(第03期),全文. * |
| 雷蕾等.支持策略隐藏的加密云存储访问控制机制.《软件学报》.2016,(第06期),全文. * |
Also Published As
| Publication number | Publication date |
|---|---|
| CN112583588A (en) | 2021-03-30 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN108768664B (en) | Key management method, device, system, storage medium and computer equipment | |
| US20240007308A1 (en) | Confidential authentication and provisioning | |
| TWI454111B (en) | Techniques for ensuring authentication and integrity of communications | |
| CN111556025A (en) | Data transmission method, system and computer equipment based on encryption and decryption operations | |
| US11196722B2 (en) | Method for mutual symmetric authentication between a first application and a second application | |
| CA2357792C (en) | Method and device for performing secure transactions | |
| US20160080157A1 (en) | Network authentication method for secure electronic transactions | |
| CN110958209B (en) | Bidirectional authentication method, system and terminal based on shared secret key | |
| CN109861813B (en) | Anti-quantum computing HTTPS communication method and system based on asymmetric key pool | |
| WO2015161689A1 (en) | Data processing method based on negotiation key | |
| CN107733636B (en) | Authentication method and authentication system | |
| CN112583588B (en) | Communication method and device and readable storage medium | |
| CN110929231A (en) | Digital asset authorization method and device and server | |
| CN110838919A (en) | Communication method, storage method, operation method and device | |
| WO2015158173A1 (en) | Agreement key-based data processing method | |
| CN112995213B (en) | Security authentication method and application device thereof | |
| WO2023284691A1 (en) | Account opening method, system, and apparatus | |
| CN110401535B (en) | Digital certificate generation, secure communication and identity authentication method and device | |
| CN114329426A (en) | Client authentication method, device, equipment and storage medium | |
| CN114065170A (en) | Method and device for acquiring platform identity certificate and server | |
| US20240223370A1 (en) | Method for authentication of a service provider device to a user device | |
| KR101737925B1 (en) | Method and system for authenticating user based on challenge-response | |
| CN111641507A (en) | Software communication system structure component registration management method and device |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| GR01 | Patent grant | ||
| GR01 | Patent grant |