Summary of the invention
In view of the above problems, the present invention has been proposed in order to provide a kind of a kind of interception that overcomes the problems referred to above or address the above problem at least in part that the method and apparatus of Android application program is installed in portable terminal.
According to one aspect of the present invention, the embodiment of the invention provides a kind of interception that the method for Android application program is installed in portable terminal, comprising:
Monitor at the predetermined port that the network-driven layer is bound mutually with Android debugging bridge ADB instrument in to computing machine;
When the process in monitoring computing machine connects by ADB instrument and portable terminal, judge whether process is grey process;
If judging above-mentioned process is grey process, when knowing that the relevant application program of grey process will be installed the Android application program to portable terminal by the ADB instrument, judge whether to allow the relevant application program of this ash process in portable terminal, the Android application program to be installed;
When not allowing the relevant application program of grey process the Android application program to be installed in the portable terminal, tackle the operation that the relevant application program of grey process is installed the Android application program in the portable terminal.
Wherein, said method also comprises: when the process in monitoring computing machine connects by ADB instrument and portable terminal, if judge that the type of process is the white process that is arranged in white list, all operations that then allows the relevant application program of this white process that portable terminal is carried out;
If judge that the type of process is the black process that is arranged in blacklist, then immediately the relevant application program of this black process is tackled, forbid that the relevant application program of black process is carried out any operation to portable terminal and the displaying application program interception successful information relevant to this black process in the user interface pop-up box.
Wherein, before judging whether process is grey process, said method also comprises: judge whether process is the process of supporting the ADB agreement, is then, continues to carry out to judge whether process is the operation of grey process, otherwise, allow the operation of process.
Wherein, above-mentionedly judge that whether process is to support the process of ADB agreement to comprise to judge whether form and the data content of the packet that process sends to predetermined port satisfy the ADB agreement, if satisfy, then process is for supporting the process of ADB agreement, if do not satisfy, then process is not to support the process of ADB agreement.
Wherein, above-mentioned when knowing that the relevant application program of grey process will be installed the Android application program to portable terminal by the ADB instrument, judging whether to allow the relevant application program of this ash process the Android application program to be installed in the portable terminal comprises: when monitoring grey process when sending the installation instruction of Android application program to predetermined port, know that the relevant application program of grey process will install the Android application program to portable terminal by the ADB instrument; Send Android installation kit APK file when monitoring grey process to predetermined port, obtain this APK file and this APK file is scanned, when scanning result indication APK file security, judgement allows the relevant application program of this ash process in portable terminal the Android application program to be installed, otherwise, judge not allow the relevant application program of this ash process in portable terminal, the Android application program to be installed.
Wherein, above-mentioned this APK file is scanned comprises: the Message Digest Algorithm 5 MD5 value of extracting each file under feature, the instruction in the executable file and/or the APK catalogue of feature, the activity of Android assembly of feature, the Android Component service of the installation kit title state the APK file, version number, digital signature, Android assembly receiver; The information that extracts is sent to the server side that is provided with safety identification storehouse, so that the characteristic information that the server side utilization is identified safely in the storehouse scans the information of APK file; The scanning result of the APK file correspondence that the reception server side issues.
Wherein, above-mentioned when knowing that the relevant application program of grey process will be installed the Android application program to portable terminal by the ADB instrument, judging whether to allow the relevant application program of this ash process the Android application program to be installed in the portable terminal comprises: show information in the user interface pop-up box, this information comprises that icon, title, the application of the application program that grey process is relevant are described, indication information and/or the processing mode information of whether advertisement program or rogue program; Receive the selection instruction that the user sends by the user interface pop-up box; When selecting the instruction indication to allow the relevant application program of grey process, judgement allows the relevant application program of this ash process in portable terminal the Android application program to be installed, when selecting the instruction indication to forbid the relevant application program of grey process, judge and forbid that the relevant application program of this ash process installs the Android application program in portable terminal.
Wherein, the operation that the relevant application program of above-mentioned interception ash process is installed the Android application program in the portable terminal comprises: interrupt being connected of grey process and predetermined port, no thoroughfare, and predetermined port will be sent to portable terminal from the APK file of grey process.
According to a further aspect in the invention, the embodiment of the invention provides a kind of interception that the device of Android application program is installed in portable terminal, comprising:
The port monitor is suitable for monitoring at the predetermined port that the network-driven layer is bound mutually with Android debugging bridge ADB instrument in to computing machine;
Determining device when the process in monitoring computing machine of being suitable for connects by ADB instrument and portable terminal, judges whether process is grey process; And, if judging process is grey process, when knowing that the relevant application program of grey process will be installed the Android application program to portable terminal by the ADB instrument, judge whether to allow the relevant application program of this ash process in portable terminal, the Android application program to be installed;
Blocker is suitable for when not allowing the relevant application program of grey process the Android application program to be installed in the portable terminal, tackles the operation that the relevant application program of grey process is installed the Android application program in the portable terminal.
Wherein, determining device when the process in monitoring computing machine of also being suitable for connects by ADB instrument and portable terminal, judges that the type of process is the white process that is arranged in white list, then blocker also is suitable for all operations that allows the relevant application program of this white process that portable terminal is carried out; And
Determining device, when the process in monitoring computing machine of also being suitable for connects by ADB instrument and portable terminal, the type of judgement process is the black process in the blacklist, blocker then, also be suitable for the relevant application program of this black process is tackled, forbid that the relevant application program of black process is carried out any operation to portable terminal and the displaying application program interception successful information relevant to this black process in the user interface pop-up box.
Wherein, determining device also was suitable for before judging whether process is grey process, judged whether process is the process of supporting the ADB agreement, is then, continues to carry out to judge whether process is the operation of grey process, otherwise, allow the operation of process.
Wherein, determining device is suitable for judging whether process satisfies the ADB agreement to form and the data content of the packet of predetermined port transmission, if satisfy, then process is for supporting the process of ADB agreement, and as if not satisfying, then process is not to support the process of ADB agreement.
Wherein, determining device is suitable for when monitoring grey process when sending the installation instruction of Android application program to predetermined port, knows that the relevant application program of grey process will install the Android application program to portable terminal by the ADB instrument; Send Android installation kit APK file when monitoring grey process to predetermined port, obtain this APK file and this APK file is scanned, when scanning result indication APK file security, judgement allows the relevant application program of this ash process in portable terminal the Android application program to be installed, otherwise, judge not allow the relevant application program of this ash process in portable terminal, the Android application program to be installed.
Wherein, determining device is suitable for obtaining in the following way scanning result: the MD5 value of each file under feature, the instruction in the executable file and/or the APK catalogue of the feature of the installation kit title of extraction APK file, version number, digital signature, Android assembly receiver, the feature of Android Component service, the activity of Android assembly; The information that extracts is sent to the server side that is provided with safety identification storehouse, so that the characteristic information that the server side utilization is identified safely in the storehouse scans the information of APK file; The scanning result of the APK file correspondence that the reception server side issues.
Wherein, determining device is suitable for showing information that in the user interface pop-up box this information comprises indication information and/or the processing mode information of icon, title, application description, whether advertisement program or the rogue program of the application program that grey process is relevant; Receive the selection instruction that the user sends by the user interface pop-up box; When selecting the instruction indication to allow the relevant application program of grey process, judgement allows the relevant application program of this ash process in portable terminal the Android application program to be installed, when selecting the instruction indication to forbid the relevant application program of grey process, judge and forbid that the relevant application program of this ash process installs the Android application program in portable terminal.
Wherein, blocker is suitable for interrupting being connected of grey process and predetermined port, and no thoroughfare, and predetermined port will be sent to portable terminal from the APK file of grey process.
From the above mentioned, the embodiment of the invention is by the monitoring to the predetermined port bound mutually with the ADB instrument, learn all processes that connect with the ADB instrument, filter out grey process wherein and the relevant application program of grey process installed the technological means that the authority of Android application program is judged in the portable terminal, solved the problem that third party's program causes with set up applications in the purpose portable terminal in the prior art, can carry out effective monitoring to utilizing the mutual third party's program of ADB instrument and Android, and the authority by process type and decision logic control third party program, thereby ensured the security of information in the portable terminal, convenient for users.
Above-mentioned explanation only is the general introduction of technical solution of the present invention, for can clearer understanding technological means of the present invention, and can be implemented according to the content of instructions, and for above and other objects of the present invention, feature and advantage can be become apparent, below especially exemplified by the specific embodiment of the present invention.
Embodiment
Exemplary embodiment of the present disclosure is described below with reference to accompanying drawings in more detail.Though shown exemplary embodiment of the present disclosure in the accompanying drawing, yet should be appreciated that and to realize the disclosure and the embodiment that should do not set forth limits here with various forms.On the contrary, it is in order to understand the disclosure more thoroughly that these embodiment are provided, and can with the scope of the present disclosure complete convey to those skilled in the art.
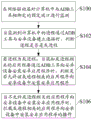
The method that one embodiment of the invention provides a kind of interception that the Android application program is installed in portable terminal, referring to Fig. 1, this method comprises:
S100: monitor at the predetermined port that the network-driven layer is bound mutually with ADB (Android Debug Bridge, Android debugging bridge) instrument in to computing machine.
Present embodiment is carried out in the network-driven layer the interception of the operation of Android application program is installed in portable terminal, this network-driven layer is in the upper strata and drives, and is to call as winsock (WindowsSockets) to be forwarded to the auxiliary middle layer that core protocol drives.The driving that is in this layer can indiscriminately monitor all local and long-range winsock and call and monitor the network bottom layer protocol-driven.
Predetermined port in the above-mentioned computing machine can be 127.0.0.1:5037 port (5037 port), and wherein, the ADB instrument is bound mutually with this 5037 port.
S102: when the process in monitoring computing machine connects by ADB instrument and portable terminal, judge whether process is grey process.
In the present embodiment be that Android equipment (supporting the terminal of Android system as Android mobile phone or other) describes for example with the portable terminal.
The ash process is the unknown process in white list and blacklist not, when the type of the process that monitors belongs to grey process, need further monitor this process, confirm whether to allow the relevant application program of this ash process in Android equipment, the Android application program to be installed.
Wherein, in the data in server storehouse, can safeguard a white list and blacklist in the present embodiment, white list is the list of record security process, blacklist when process is arranged in white list, allows the follow-up all operations of this white process for the list of the dangerous process of record, no longer this white process is monitored, when process is arranged in blacklist, in case monitor out black process, carry out interception immediately.
Need to prove that present embodiment is on the level of process, the scheme of interception being installed the Android application program in portable terminal (Android equipment) is described.Application program is static, and process is dynamic, and process is a program of carrying out, the i.e. program example that is moving in the computing machine; It can be distributed to processor and be carried out by processor as an entity.Can the be applied result of program of process.Application program once operates to a process on a data set, process and application program are not one to one, and an application program operates in and forms a plurality of different processes on a plurality of different data sets.Process produces when creating, and in response to moving with the scheduling of program, the back process can be undone finishing the work.Process can reflect whole dynamic processes that an application program is moved at certain data set.The application program that above-mentioned process is relevant refers to the application program moved on the process.
S104: when knowing that the relevant application program of grey process will be installed the Android application program to portable terminal by the ADB instrument, judge whether to allow the relevant application program of this ash process in portable terminal, the Android application program to be installed.
The application program that process is relevant utilizes the ADB instrument can carry out polytype operation, for example, enumerate Android equipment that current system connects, connect, read and write file and catalogue in the Android equipment, the APK file be installed for Android equipment, carry out shell instruction on the Android equipment etc. with Android equipment.At this, this programme is mainly paid close attention to the function that the APK file is installed based on the ADB agreement, and then in this step, the logic of startup interception operation is judged when knowing that the relevant application program of grey process will be installed the Android application program to Android equipment by the ADB instrument.
S106: when not allowing the relevant application program of grey process the Android application program to be installed in the portable terminal, tackle the operation that the relevant application program of grey process is installed the Android application program in the portable terminal.
From the above mentioned, the embodiment of the invention PC end equipment for example computer is connected with Android equipment when transmitting, protect Android equipment not to be forced to install ad ware or Malware.This programme not only can be intercepted malice harassing and wrecking program, also can intercept any rogue program that obtains the authority of set up applications on mobile phone by the ADB instrument.
Can't use the third party who utilizes the ADB instrument at mobile phone the Android application program to be installed in the existing Android system and check, and the ADB instrument can obtain all authorities of Android application program, comprise and carry out shell instruction etc., thereby after causing mobile phone and computing machine being connected, virus is easy to be transmitted to mobile phone, for addressing this problem, present embodiment is by the monitoring to the predetermined port bound mutually with the ADB instrument, learn all processes that connect with the ADB instrument, filter out grey process wherein and the relevant application program of grey process installed the technological means that the authority of Android application program is judged in the Android equipment, solved the problem that third party's program causes with set up applications in the purpose Android equipment in the prior art, can carry out effective monitoring to utilizing the mutual third party's program of ADB instrument and Android, and the authority by process type and decision logic control third party program, thereby ensured the security of information in the portable terminal, convenient for users.
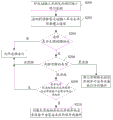
On basis embodiment illustrated in fig. 1, the method for Android application program is installed in a kind of interception that another embodiment of the present invention provides in portable terminal, referring to Fig. 2, comprise the steps:
S200: to monitoring with 5037 ports of ADB instrument binding.
In this step, the packet that in background program, passes through in monitoring 5037 ports, these packets can also can be the packet of sending entity data for sending the packet of instruction.
Above-mentioned monitoring can be realized by ADB instrument or the device that is arranged in the ADB instrument.
The function of ADB instrument mainly comprises: the order of operation Android equipment, the port mapping of management Android simulator or Android equipment, upload or download file between control computing machine or the Android equipment, and the APK file of this locality is mounted to Android simulator or Android equipment.The ADB instrument has played the effect of a transfer between computing machine and Android equipment.
The ADB instrument is based on client-service end model realization, comprises three parts: ADB client, ADB service end and finger daemon.
The ADB client operates on the computer of exploitation usefulness, can move ADB in order line and order to call this client, and the Android instrument as ADB plug-in unit and DDMS also can call the ADB client.
The ADB service end is to operate in exploitation with the background process on the computer, and management equipment also is responsible for exchanges data between computing machine and the equipment;
ADB client and ADB service end may reside among the same executable file, for example in the Windows system in the executable file of adb.exe by name.The ADB client is responsible for and user interactions, just withdraws from after executing order; And the ADB service end runs in the computing machine after startup always.
Finger daemon operates in the process in the Android system, receives data and execution command that the ADB service end is sent.
When starting the ADB client, whether client at first detects ADB service end process and moves, if not operation then starts the ADB service end.When the ADB service end started, it can be tied to local TCP5037 port, and monitored the order of sending from the ADB client.All ADB clients all use 5037 ports to communicate by letter with the ADB service end.
S202: the process in monitoring computing machine connects by ADB instrument and Android equipment.
The ADB instrument can operate the Android mobile phone by predetermined port, in the Android mobile phone set up applications, carry out mobile phone synchronously and function such as upload file, third party's program can communicate by bundling an ADB instrument and sending order to Android equipment.
The ADB instrument comprises ADB client and ADB service end.The ADB service end is responsible for and the Android device talk always at running background, can the APK file transfers be arrived the ADB service end by network, gets on thereby be installed to portable terminal by transfer; The ADB client is responsible for being connected of third party's program and predetermined port, and is provided with the ADB communications protocol in the local network layer, to support the communication of ADB instrument.For example, the mobile phone assistant just is equivalent to an ADB service end, when other application program with after the mobile phone assistant is connected, other application program also can utilize mobile phone assistant's service to Android equipment set up applications etc.
Third party's program can be set up Socket (socket) by ADB client and 5037 ports and be connected, and is connected to Android equipment by this Socket connection and ADB service end then.As when being installed to application program on the mobile phone, the ADB client passes to the ADB service end with the installation kit of application program, and the ADB service end is just installed this application program to mobile phone.
S204: judging that whether process is to support the process of ADB agreement, is execution in step S206 then.
Packet by 5037 port transmission except with the packet of Android device talk, the packet that also can comprise other types, for fear of intercepting other normal programs, guarantee the normal operation of other programs, in the present embodiment, judge the whether use ADB agreement of the process monitor, when using the ADB agreement, illustrate that this process is the process of meeting with the Android devices communicating, continuation is monitored this process, when not using the ADB agreement, illustrate this process for not with other processes of Android devices communicating, no longer this process is monitored, allowed the operation of this process.
The operation of ADB agreement support comprises the Android equipment that uses ADB to enumerate current system to connect, connects, reads and writes file and catalogue in the Android equipment, the APK file is installed for Android equipment, carries out shell instruction on the Android equipment etc. with Android equipment.
Judging whether process is when supporting the process of ADB agreement, can judge whether this process satisfies the ADB agreement to form and the data content of the packet of predetermined port (5037 port) transmission, if satisfy, then this process is for supporting the process of ADB agreement, if do not satisfy, then this process is not to support the process of ADB agreement.For example, when the form of judgment data bag satisfies the call format of ADB agreement, and indicated the notebook data bag for based on the packet of ADB agreement the time in the data content, the affirmation process is for supporting the process of ADB agreement.
S206: the type of judging process.
Present embodiment can be collected and add up the information of process in advance, white list and the blacklist of maintenance and the process of preservation.
White list is the list of record security process, and blacklist is the list of the dangerous process of record.The type that is arranged in the white list process is white process, and the type that is arranged in the blacklist process is black process, and the unknown process of all outside white list and blacklist belongs to grey process.In addition, present embodiment can also and be associated with performance of program by the behavior of client collection procedure, thereby logging program feature and corresponding program behavior thereof in database, incidence relation according to the program behavior of collecting and performance of program, can in database, carry out analytic induction to sample, thereby help software or program are belonged to the judgement of blacklist or white list.Owing in database, recorded the behavior record of performance of program and this feature correspondence, therefore can analyze unknown program in conjunction with known white list.For example, if the unknown program feature is identical with known procedure feature in the existing white list, then all list this unknown program feature and program behavior thereof in white list.If the unknown program behavior is identical or approximate with the known procedure behavior in the existing white list, then all list this unknown program behavior and performance of program thereof in white list.
When process is white process (process of calling as 360 mobile phone assistants, 91 mobile phone assistants or pea pods etc.), confirm that the relevant application program of this process is believable application program, allow the operation of this process.
When process during for black process (promoting the process etc. of the application call of APK as malice), confirm that the relevant application program of this process is incredible application program, after judging the type of this process, tackle the operation (as being connected to tackle this process by what disconnect this process and 5037 ports) of this process immediately, forbid that the relevant application program of this process carries out any operation (as enumerating the Android equipment that connects in the system) to Android equipment, and will tackle successful information and be sent to the user, as in the user interface pop-up box, showing the application program interception successful information relevant to this black process.
When process is grey process, enter step S208, continue this ash process is monitored.
S208: judge whether to allow the relevant application program of this ash process in Android equipment, the Android application program to be installed.
This programme is mainly paid close attention to the scene that third party's program is utilized ADB agreement set up applications on Android equipment, and when grey process was carried out other operations, the operation as enumeration operation, read-write Android facility inventory can allow the execution of these operations.
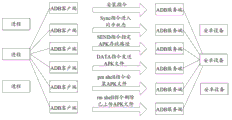
In order to be illustrated more clearly in this programme, at first utilize the ADB instrument that the describing of scene of Android application program is installed in the Android equipment in conjunction with the relevant application program of the process of Fig. 3 below, the interaction flow synoptic diagram when Fig. 3 shows process and utilizes the ADB instrument Android application program to be installed in the Android equipment.Wherein, process is set up Socket by the ADB client with 5037 ports and is connected, and connects by this Socket various instruction and datas are sent to 5037 ports, and then by the ADB service end instruction and data is sent to Android equipment, when carrying out the installation of APK file, mainly comprise following operation:
1), process sends install (installation) instruction by ADB client and ADB service end to Android equipment.
Above-mentioned install instruction indication process namely will be carried out the operation that the Android application program is installed to Android equipment.
2), process sends Sync by ADB client and ADB service end to Android equipment (indication enters synchronous regime for synchronous, instruction synchronously).
3), process passes through the ADB client and the ADB service end sends SEND (transmission) instruction to Android equipment, specifies the path of depositing of APK file.
4), process sends DATA (data) instruction by ADB client and ADB service end to Android equipment, thereby the APK file that will need to install sends to Android equipment.
5), process sends pm shell instruction by ADB client and ADB service end to Android equipment, the installation of startup APK file on Android equipment.
After the APK file is installed, can also comprise the steps 6).
6), process sends rm shell instruction, the data such as APK file that deletion is uploaded by ADB client and ADB service end to Android equipment in installation process.
The triggering when knowing that the relevant application program of grey process will be installed the Android application program to Android equipment by the ADB instrument of this step begins to carry out.When the install function that monitors grey process transfer ADB instrument sends the install instruction of Android application program to predetermined port, know that the relevant application program of grey process will be by the ADB instrument to Android equipment installation Android application program; After sending the install instruction, the ash process also can send Sync (synchronous to predetermined port by the ADB instrument, instruction synchronously), SEND (transmission) instruction etc., grey process sends DATA (data) instruction that carries the APK file to predetermined port then, then ought monitor grey process and send Android installation kit APK file to predetermined port, obtain this APK file and this APK file is scanned, scan and whether contain malice in this APK file that will install and deduct fees, the malice harassing and wrecking, steal the hostile content such as code of privacy, scanning result is not the APK file security when having hostile content, otherwise scanning result is the danger of APK file.
When scanning result was indicated the APK file security, judgement allowed the relevant application program of this ash process in Android equipment the Android application program to be installed, otherwise the application program that judgement does not allow this ash process to be correlated with is installed the Android application program in Android equipment.
When the scanning of carrying out the APK file, specifically carry out following operation:
Extract the various information of APK file, the MD5 value of these information each file under the feature of the feature of the feature of installation kit title, version number, digital signature, Android assembly receiver (receiver), Android Component service (service), Android assembly activity (activity), instruction (or character string) in the executable file and/or the APK catalogue; Then, the information that extracts is sent to the server side that is provided with safety identification storehouse, so that the characteristic information that the server side utilization is identified safely in the storehouse scans the information of APK file; The scanning result of the APK file correspondence that the reception server side issues, thus know information such as scanning result, package name, certificate.
Preferably, the above-mentioned storehouse of identifying safely can be cloud killing engine.
Wherein, above-mentioned executable file comprises Dex file and/or ELF file, and this Dex file comprises classes.dex file, the file of expansion .jar by name and the file of Dex form etc.
Need to prove that present embodiment needed collect the information of APK file in advance before the employing aforesaid way scans, and for example, chose sample Android installation kit, this sample Android installation kit comprises the Android installation kit under the various level of securitys.To the bag name of various sample Android installation kits, version number, digital signature, the feature of Android assembly receiver, the feature of Android assembly service, the feature of Android assembly activity, instruction or the character string in the executable file, the MD5 value of each file is collected under the Android installation kit catalogue, the information of collecting is preset in the safety identification storehouse of server side.
Both collect the characteristic information of the APK file of various Malwares such as identification virus, wooden horse in the safety identification storehouse that server side presets, also collected the characteristic information of the APK file of identification normal use.Have an information to hit the characteristic information of Malware in the information of APK file, it is not safe that the scanning result of this APK file correspondence that then obtains is indicated this APK file.
Further, also allow the user that the installation of Android application program is selected in the present embodiment, namely by above-mentioned decision logic to whether permission process relevant application program in Android equipment, install after the Android application program judges, make final court verdict in conjunction with user's selection.When confirming to allow the relevant application program of grey process the Android application program to be installed in the Android equipment according to above-mentioned decision logic (perhaps other allow the scene of set up applications in Android equipment, as white process), this method also comprises:
In the user interface pop-up box, show information, this information comprises indication information and/or the processing mode information of icon, title, application description, whether advertisement program or the rogue program of the application program that grey process is relevant, and this processing mode information can comprise the processing suggestion of the application programs of recommending etc.Then, receive the selection instruction that the user sends by the user interface pop-up box; When selecting the instruction indication to allow the relevant application program of grey process, the final application program of judging that this ash process of permission is correlated with is installed the Android application program in Android equipment, and carry out the fitting operation of this Android application program, when selecting the instruction indication to forbid the relevant application program of grey process, judge and to forbid that the relevant application program of this ash process installs the Android application program in Android equipment, no longer carry out the installation process of this Android application program.
S210: tackle the operation that the relevant application program of grey process is installed the Android application program in the Android equipment.
In the interception mechanism of this programme, interrupt being connected of grey process and 5037 ports, as control the ADB client terminal and disconnect with grey process and being connected, and, no thoroughfare, and 5037 ports will be sent to Android equipment from the APK file of grey process, for example, control ADB service end forbids the APK file of this ash process is sent to Android equipment.
The device 400 that another embodiment of the present invention provides a kind of interception that the Android application program is installed in portable terminal referring to Fig. 4, comprises port monitor 410, determining device 412 and blocker 414.
Port monitor 410 is suitable for monitoring at the predetermined port that the network-driven layer is bound mutually with Android debugging bridge ADB instrument in to computing machine.This predetermined port is 127.0.0.1:5037 port (5037 port).Referring to Fig. 4, the ADB instrument comprises ADB client and ADB service end.The process of third party application is set up Socket by the ADB client with 5037 ports and is connected, and 5037 ports are bound mutually with the ADB service end, and the ADB service end is connected with Android equipment by USB.Device 400 can be controlled the ADB instrument in the computing machine and 5037 ports.
In the present embodiment be that Android equipment (supporting the terminal of Android system as Android mobile phone or other) describes for example with the portable terminal.
The process that determining device 412 is suitable in monitoring computing machine when connecting, judges whether process is grey process by ADB instrument and portable terminal (Android equipment); And, if judging process is grey process, when knowing that the relevant application program of grey process will be installed the Android application program to Android equipment by the ADB instrument, judge whether to allow the relevant application program of this ash process in Android equipment, the Android application program to be installed.Concrete, determining device 412 knows that when monitoring grey process when sending the installation instruction of Android application program to predetermined port the relevant application program of grey process will be by the ADB instrument to Android equipment installation Android application program; Send Android installation kit APK file when monitoring grey process to predetermined port, obtain this APK file and this APK file is scanned, when scanning result indication APK file security, judgement allows the relevant application program of this ash process in Android equipment the Android application program to be installed, otherwise, judge not allow the relevant application program of this ash process in Android equipment, the Android application program to be installed.
Determining device 412 is when the scanning of carrying out the APK file, concrete carry out following operation: extract the various information of APK file, the MD5 value (also can be the SHA1 value) of these information each file under the feature of the feature of the feature of installation kit title, version number, digital signature, Android assembly receiver (receiver), Android Component service (service), Android assembly activity (activity), instruction (or character string) in the executable file and/or the APK catalogue; Then, the information that extracts is sent to the server side that is provided with safety identification storehouse, so that the characteristic information that the server side utilization is identified safely in the storehouse scans the information of APK file; The scanning result of the APK file correspondence that the reception server side issues, thus know scanning result.Wherein, at server side, the characteristic information of the Malware in the information of the APK file that determining device is reported and the safety identification storehouse is compared, as long as there is an information to hit, then this APK file is not safe file just.Preferably, the above-mentioned storehouse of identifying safely can be cloud killing engine.
The ash process is default white list and all processes outside the blacklist, present embodiment also utilizes default white list and blacklist dialogue process and black process to identify, concrete, when determining device 412 also is suitable for process in monitoring computing machine and connects by ADB instrument and Android equipment, the type of judgement process is the white process that is arranged in white list, and then blocker 414 also is suitable for allowing the relevant application program of this white process to all operations of Android equipment execution.
And, when determining device 412 also is suitable for process in monitoring computing machine and connects by ADB instrument and Android equipment, the type of judgement process is the black process that is arranged in blacklist, then blocker 414 also is suitable for immediately the relevant application program of this black process being tackled, and forbids deceiving the relevant application program of process Android equipment is carried out any operation.
Further, since the packet by 5037 port transmission except with the packet of Android device talk, also can comprise the packet of other types, for fear of intercepting other normal programs, guarantee the normal operation of other programs, in the present embodiment, determining device 412 also was suitable for before judging whether process is grey process, judged whether process is the process of supporting the ADB agreement, be then, continue to carry out to judge whether process is the operation of grey process, otherwise, allow the operation of process.Concrete, determining device 412 judges whether process satisfies the ADB agreement to form and the data content of the packet of predetermined port transmission, if satisfy, then process is for supporting the process of ADB agreement, and as if not satisfying, then process is not to support the process of ADB agreement.
Further, present embodiment is also made final court verdict in conjunction with user's selection installing after the Android application program judges whether allowing process according to above-mentioned decision logic by determining device 412 in Android equipment.For example, determining device 412 is showed information in the user interface pop-up box, and this information comprises indication information and/or the processing mode information of icon, title, application description, whether advertisement program or the rogue program of the application program that grey process is relevant; Receive the selection instruction that the user sends by the user interface pop-up box; When selecting the instruction indication to allow the relevant application program of grey process, judgement allows the relevant application program of this ash process in Android equipment the Android application program to be installed, when selecting the instruction indication to forbid the relevant application program of grey process, judge and forbid that the relevant application program of this ash process installs the Android application program in Android equipment.
For the interception of grey process, blocker 414 is tackled the operation that the relevant application program of grey process is installed the Android application program in the Android equipment when not allowing the relevant application program of grey process the Android application program to be installed in the Android equipment.For example, the grey process of blocker 414 interruptions is connected with predetermined port, and no thoroughfare, and predetermined port will be sent to Android equipment from the APK file of grey process.For the interception of white process and black process, referring to the description of above related content.
The concrete working method of each device can not repeat them here referring to method embodiment of the present invention among apparatus of the present invention embodiment.
From the above mentioned, the embodiment of the invention is by the monitoring to the predetermined port bound mutually with the ADB instrument, learn all processes that connect with the ADB instrument, filter out grey process wherein and the relevant application program of grey process installed the technological means that the authority of Android application program is judged in the portable terminal, solved the problem that third party's program causes with set up applications in the purpose portable terminal in the prior art, can carry out effective monitoring to utilizing the mutual third party's program of ADB instrument and Android, and the authority by process type and decision logic control third party program, thereby ensured the security of information in the portable terminal, convenient for users.
Intrinsic not relevant with any certain computer, virtual system or miscellaneous equipment with demonstration at this algorithm that provides.Various general-purpose systems also can be with using based on the teaching at this.According to top description, it is apparent constructing the desired structure of this type systematic.In addition, the present invention is not also at any certain programmed language.Should be understood that and to utilize various programming languages to realize content of the present invention described here, and the top description that language-specific is done is in order to disclose preferred forms of the present invention.
In the instructions that provides herein, a large amount of details have been described.Yet, can understand, embodiments of the invention can be put into practice under the situation of these details not having.In some instances, be not shown specifically known method, structure and technology, so that not fuzzy understanding of this description.
Similarly, be to be understood that, in order to simplify the disclosure and to help to understand one or more in each inventive aspect, in the description to exemplary embodiment of the present invention, each feature of the present invention is grouped together in single embodiment, figure or the description to it sometimes in the above.Yet the method for the disclosure should be construed to the following intention of reflection: namely the present invention for required protection requires the more feature of feature clearly put down in writing than institute in each claim.Or rather, as following claims reflected, inventive aspect was to be less than all features of the disclosed single embodiment in front.Therefore, follow claims of embodiment and incorporate this embodiment thus clearly into, wherein each claim itself is as independent embodiment of the present invention.
Those skilled in the art are appreciated that and can adaptively change and they are arranged in one or more equipment different with this embodiment the module in the equipment among the embodiment.Can become a module or unit or assembly to the module among the embodiment or unit or combination of components, and can be divided into a plurality of submodules or subelement or sub-component to them in addition.In such feature and/or process or unit at least some are mutually repelling, and can adopt any combination to disclosed all features in this instructions (comprising claim, summary and the accompanying drawing followed) and so all processes or the unit of disclosed any method or equipment make up.Unless clearly statement in addition, disclosed each feature can be by providing identical, being equal to or the alternative features of similar purpose replaces in this instructions (comprising claim, summary and the accompanying drawing followed).
In addition, those skilled in the art can understand, although embodiment more described herein comprise some feature rather than further feature included among other embodiment, the combination of features of different embodiment means and is within the scope of the present invention and forms different embodiment.For example, in the following claims, the one of any of embodiment required for protection can be used with array mode arbitrarily.
Each parts embodiment of the present invention can realize with hardware, perhaps realizes with the software module of moving at one or more processor, and perhaps the combination with them realizes.It will be understood by those of skill in the art that and to use microprocessor or digital signal processor (DSP) to realize according to the interception of the embodiment of the invention some or all some or repertoire of parts in the device of Android application program being installed in portable terminal in practice.The present invention can also be embodied as for part or all equipment or the device program (for example, computer program and computer program) of carrying out method as described herein.Such realization program of the present invention can be stored on the computer-readable medium, perhaps can have the form of one or more signal.Such signal can be downloaded from internet website and obtain, and perhaps provides at carrier signal, perhaps provides with any other form.
It should be noted above-described embodiment the present invention will be described rather than limit the invention, and those skilled in the art can design alternative embodiment under the situation of the scope that does not break away from claims.In the claims, any reference symbol between bracket should be configured to limitations on claims.Word " comprises " not to be got rid of existence and is not listed in element or step in the claim.Being positioned at word " " before the element or " one " does not get rid of and has a plurality of such elements.The present invention can realize by means of the hardware that includes some different elements and by means of the computing machine of suitably programming.In having enumerated the unit claim of some devices, several in these devices can be to come imbody by same hardware branch.Any order is not represented in the use of word first, second and C grade.Can be title with these word explanations.
Embodiments of the invention have disclosed the Android application program is installed in A1, a kind of interception in portable terminal method, comprising: monitor at the predetermined port that the network-driven layer is bound mutually with Android debugging bridge ADB instrument in to computing machine; When the process in monitoring computing machine connects by ADB instrument and portable terminal, judge whether described process is grey process; If to judge described process be grey process, when knowing that the relevant application program of described grey process will be installed the Android application program to portable terminal by the ADB instrument, judge whether to allow the relevant application program of this ash process in portable terminal, the Android application program to be installed; When not allowing the relevant application program of described grey process the Android application program to be installed in the portable terminal, tackle the operation that the relevant application program of described grey process is installed the Android application program in the portable terminal.A2, according to the described method of claim A1, wherein, described method also comprises: when the process in monitoring computing machine connects by ADB instrument and portable terminal, if judge that the type of described process is the white process that is arranged in white list, all operations that then allows the relevant application program of this white process that portable terminal is carried out; If judge that the type of described process is the black process that is arranged in blacklist, then immediately the relevant application program of this black process is tackled, forbid that the relevant application program of described black process is carried out any operation to portable terminal and the displaying application program interception successful information relevant to this black process in the user interface pop-up box.A3, according to claim A1 or the described method of A2, wherein, before judging whether described process is grey process, described method also comprises: judge whether described process is the process of supporting the ADB agreement, be then, continue to carry out to judge whether described process is the operation of grey process, otherwise, allow the operation of described process.A4, according to the described method of claim A3, wherein, describedly judge that whether described process is to support the process of ADB agreement to comprise: whether form and the data content of judging the packet that described process sends to described predetermined port satisfy the ADB agreement, if satisfy, then described process is for supporting the process of ADB agreement, if do not satisfy, then described process is not to support the process of ADB agreement.A5, according to the described method of claim A3, wherein, described when knowing that the relevant application program of described grey process will be installed the Android application program to portable terminal by the ADB instrument, judging whether to allow the relevant application program of this ash process the Android application program to be installed in the portable terminal comprises: when monitoring described grey process when sending the installation instruction of Android application program to described predetermined port, know that the relevant application program of described grey process will install the Android application program to portable terminal by the ADB instrument; Send Android installation kit APK file when monitoring described grey process to described predetermined port, obtain this APK file and this APK file is scanned, when scanning result indication APK file security, judgement allows the relevant application program of this ash process in portable terminal the Android application program to be installed, otherwise, judge not allow the relevant application program of this ash process in portable terminal, the Android application program to be installed.A6, according to the described method of claim A5, wherein, described this APK file is scanned comprises: the Message Digest Algorithm 5 MD5 value of extracting each file under feature, the instruction in the executable file and/or the APK catalogue of feature, the activity of Android assembly of feature, the Android Component service of installation kit title, version number, digital signature, the Android assembly receiver of described APK file; The information that extracts is sent to the server side that is provided with safety identification storehouse, so that the characteristic information that the server side utilization is identified safely in the storehouse scans the information of described APK file; The scanning result of the described APK file correspondence that the reception server side issues.A7, according to the described method of claim A1, wherein, described when knowing that the relevant application program of described grey process will be installed the Android application program to portable terminal by the ADB instrument, judging whether to allow the relevant application program of this ash process the Android application program to be installed in the portable terminal comprises: show information in the user interface pop-up box, described information comprises that icon, title, the application of the application program that described grey process is relevant are described, indication information and/or the processing mode information of whether advertisement program or rogue program; Receive the selection instruction that the user sends by described user interface pop-up box; When the indication of described selection instruction allows the relevant application program of described grey process, judgement allows the relevant application program of this ash process in portable terminal the Android application program to be installed, when the relevant application program of described grey process is forbidden in the indication of described selection instruction, judge and forbid that the relevant application program of this ash process installs the Android application program in portable terminal.A8, according to the described method of claim A1, wherein, the operation that the relevant application program of the described grey process of described interception is installed the Android application program in the portable terminal comprises: interrupt being connected of described grey process and described predetermined port, no thoroughfare, and described predetermined port will be sent to portable terminal from the APK file of described grey process.The device of Android application program is installed in A9, a kind of interception in portable terminal, comprising: the port monitor is suitable for monitoring at the predetermined port that the network-driven layer is bound mutually with Android debugging bridge ADB instrument in to computing machine; Determining device when the process in monitoring computing machine of being suitable for connects by ADB instrument and portable terminal, judges whether described process is grey process; And, if to judge described process be grey process, when knowing that the relevant application program of described grey process will be installed the Android application program to portable terminal by the ADB instrument, judge whether to allow the relevant application program of this ash process in portable terminal, the Android application program to be installed; Blocker is suitable for when not allowing the relevant application program of described grey process the Android application program to be installed in the portable terminal, tackles the operation that the relevant application program of described grey process is installed the Android application program in the portable terminal.A10, according to the described device of claim A9, wherein, described determining device, when the process in monitoring computing machine of also being suitable for connects by ADB instrument and portable terminal, the type of judging described process is the white process in the white list, then described blocker also is suitable for all operations that allows the relevant application program of this white process that portable terminal is carried out; And described determining device, when the process in monitoring computing machine of also being suitable for connects by ADB instrument and portable terminal, the type of judging described process is the black process in the blacklist, described blocker then, also be suitable for the relevant application program of this black process is tackled, forbid that the relevant application program of described black process is carried out any operation to portable terminal and the displaying application program interception successful information relevant to this black process in the user interface pop-up box.A11, according to claim A9 or the described device of A10, wherein, described determining device, also be suitable for before judging whether described process is grey process, judge whether described process is the process of supporting the ADB agreement, is then, continues to carry out and judges whether described process is the operation of grey process, otherwise, allow the operation of described process.A12, according to the described device of claim A11, wherein, described determining device, be suitable for judging whether described process satisfies the ADB agreement to form and the data content of the packet of described predetermined port transmission, if satisfy, then described process is for supporting the process of ADB agreement, if do not satisfy, then described process is not to support the process of ADB agreement.A13, according to the described device of claim A11, wherein, described determining device, be suitable for when monitoring described grey process when sending the installation instruction of Android application program to described predetermined port, know that the relevant application program of described grey process will install the Android application program to portable terminal by the ADB instrument; Send Android installation kit APK file when monitoring described grey process to described predetermined port, obtain this APK file and this APK file is scanned, when scanning result indication APK file security, judgement allows the relevant application program of this ash process in portable terminal the Android application program to be installed, otherwise, judge not allow the relevant application program of this ash process in portable terminal, the Android application program to be installed.A14, according to the described device of claim A9, wherein, described determining device is suitable for obtaining described scanning result in the following way: the MD5 value of extracting each file under feature, the instruction in the executable file and/or the APK catalogue of feature, the activity of Android assembly of feature, the Android Component service of installation kit title, version number, digital signature, the Android assembly receiver of described APK file; The information that extracts is sent to the server side that is provided with safety identification storehouse, so that the characteristic information that the server side utilization is identified safely in the storehouse scans the information of described APK file; The scanning result of the described APK file correspondence that the reception server side issues.A15, according to the described device of claim A9, wherein, described determining device is suitable for showing information that in the user interface pop-up box described information comprises indication information and/or the processing mode information of icon, title, application description, whether advertisement program or the rogue program of the application program that described grey process is relevant; Receive the selection instruction that the user sends by described user interface pop-up box; When the indication of described selection instruction allows the relevant application program of described grey process, judgement allows the relevant application program of this ash process in portable terminal the Android application program to be installed, when the relevant application program of described grey process is forbidden in the indication of described selection instruction, judge and forbid that the relevant application program of this ash process installs the Android application program in portable terminal.A16, according to the described device of claim A9, wherein, described blocker is suitable for interrupting being connected of described grey process and described predetermined port, no thoroughfare, and described predetermined port will be sent to portable terminal from the APK file of described grey process.