Implementation of Shokri et al(2016) Membership Inference Attacks Against Machine Learning Models
Modifications were made on shadow models' training methodology in order to prevent overfitting
- Added weight decay factor
- Implemented early stopping
- Loads & saves best model based on evaluation metrics
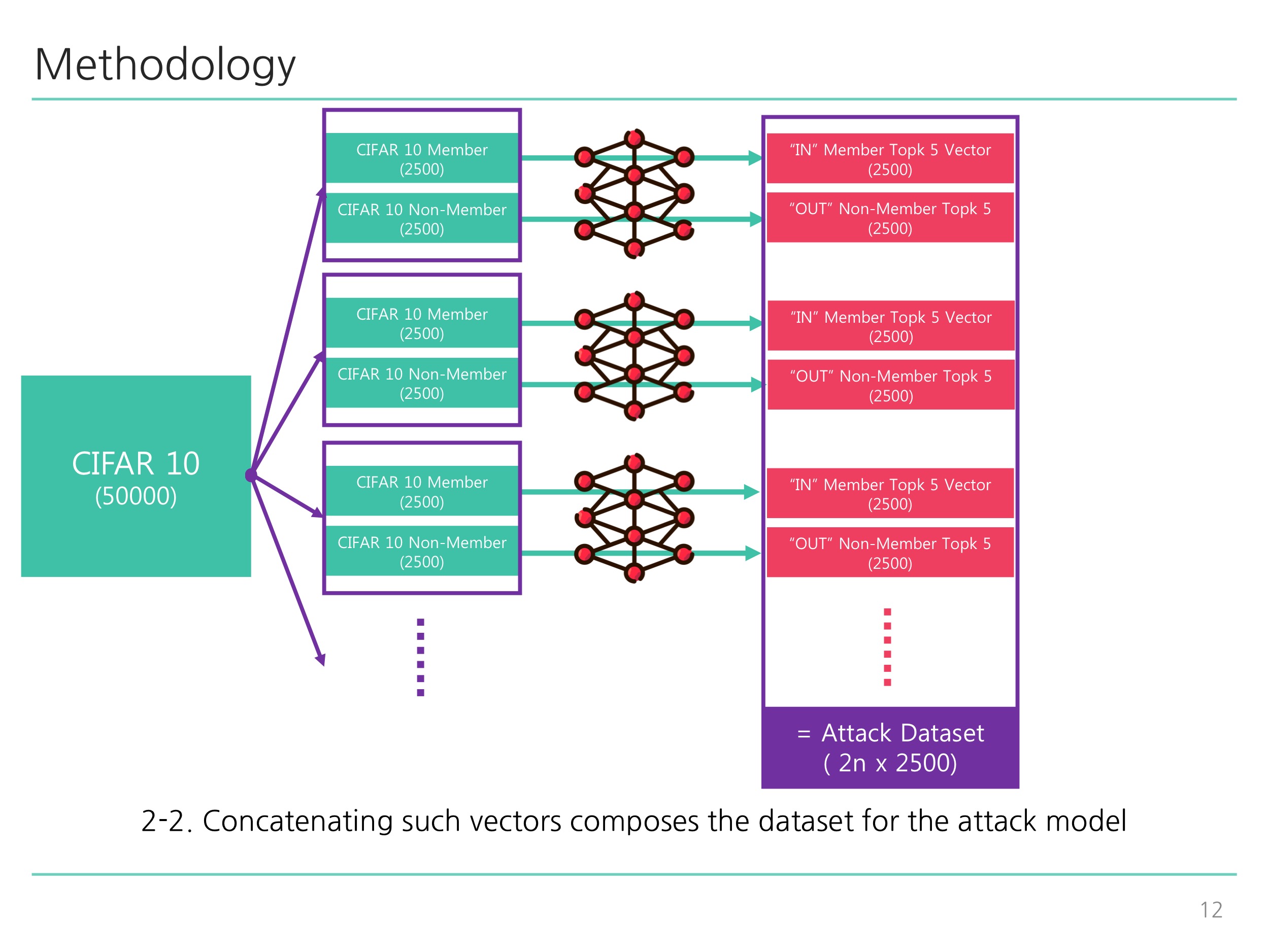
- Creates member vs non-member attack dataset based on shadow testset
-
(Optional) Customize train / inference configurations in config.yaml
-
(Optional)
python train_target.py: Train the victim model which is the target of the extraction. -
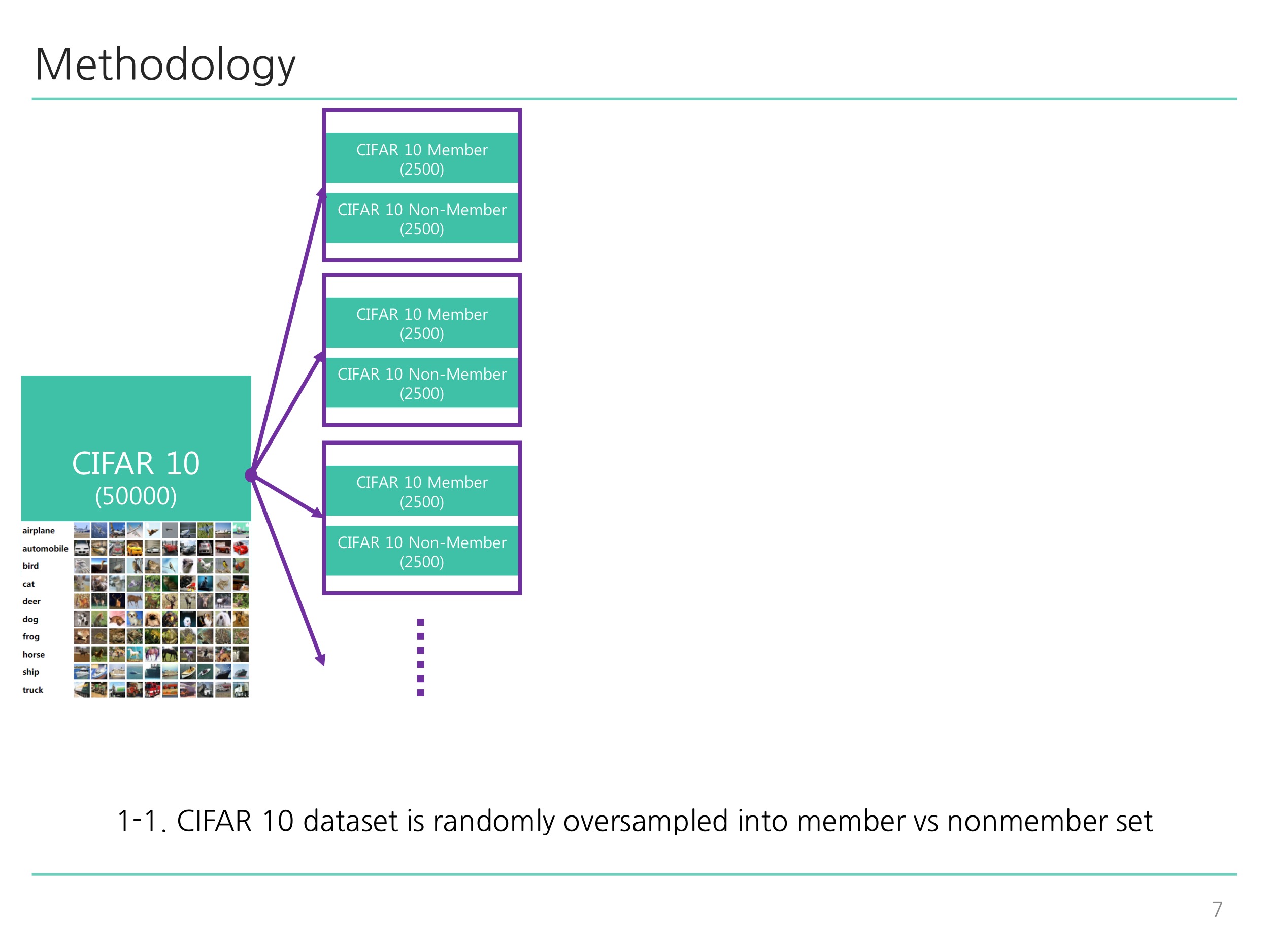
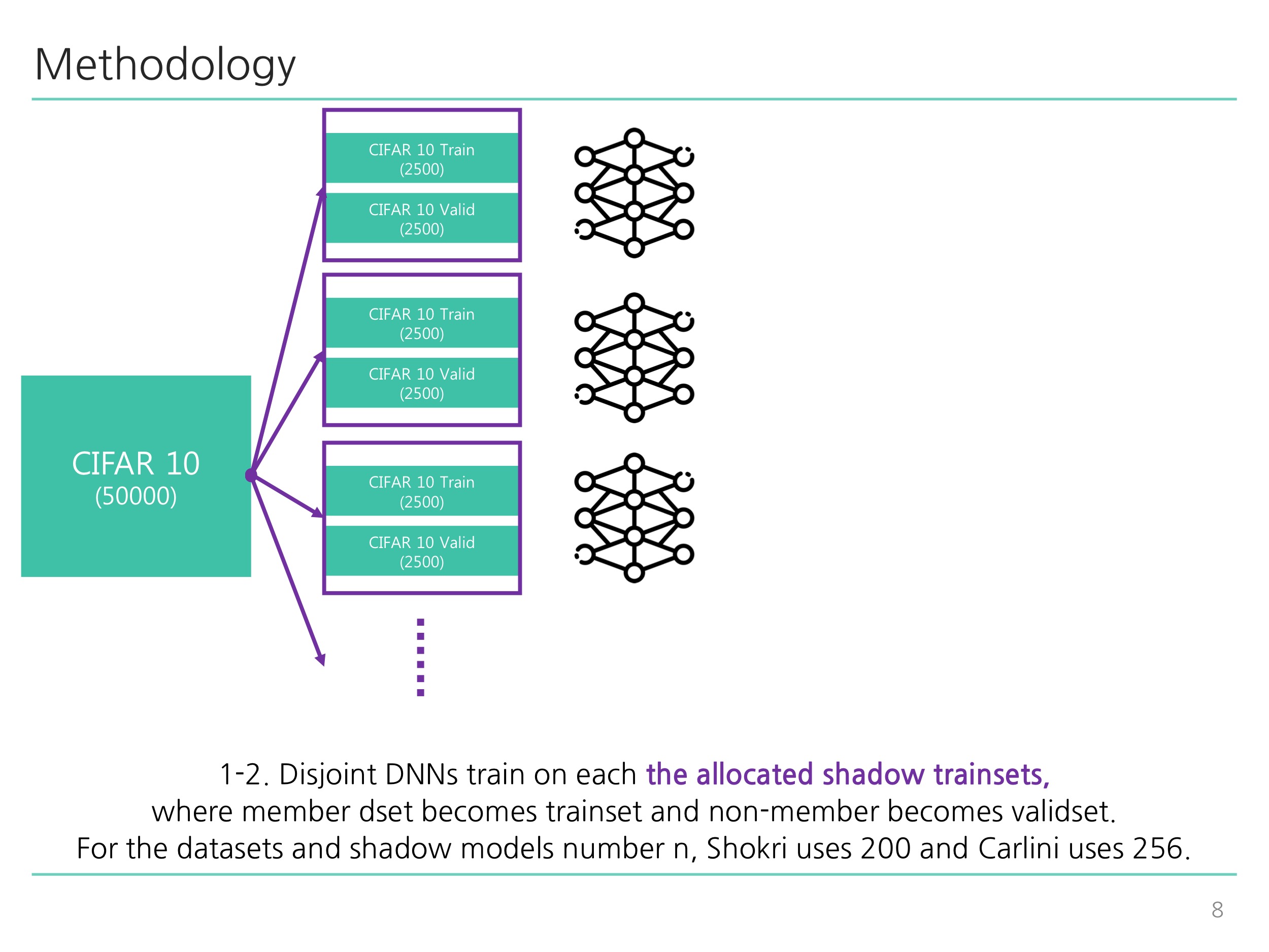
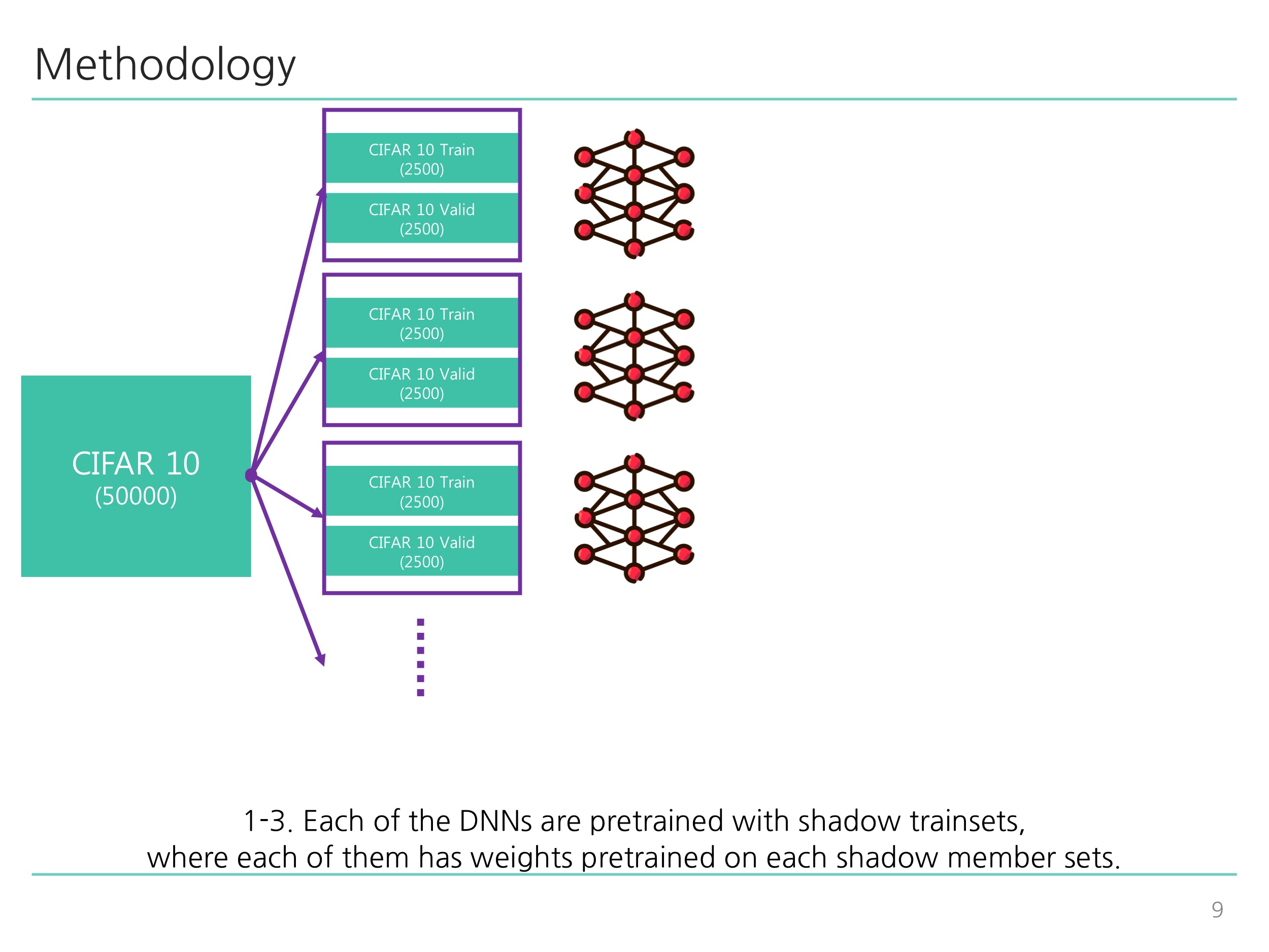
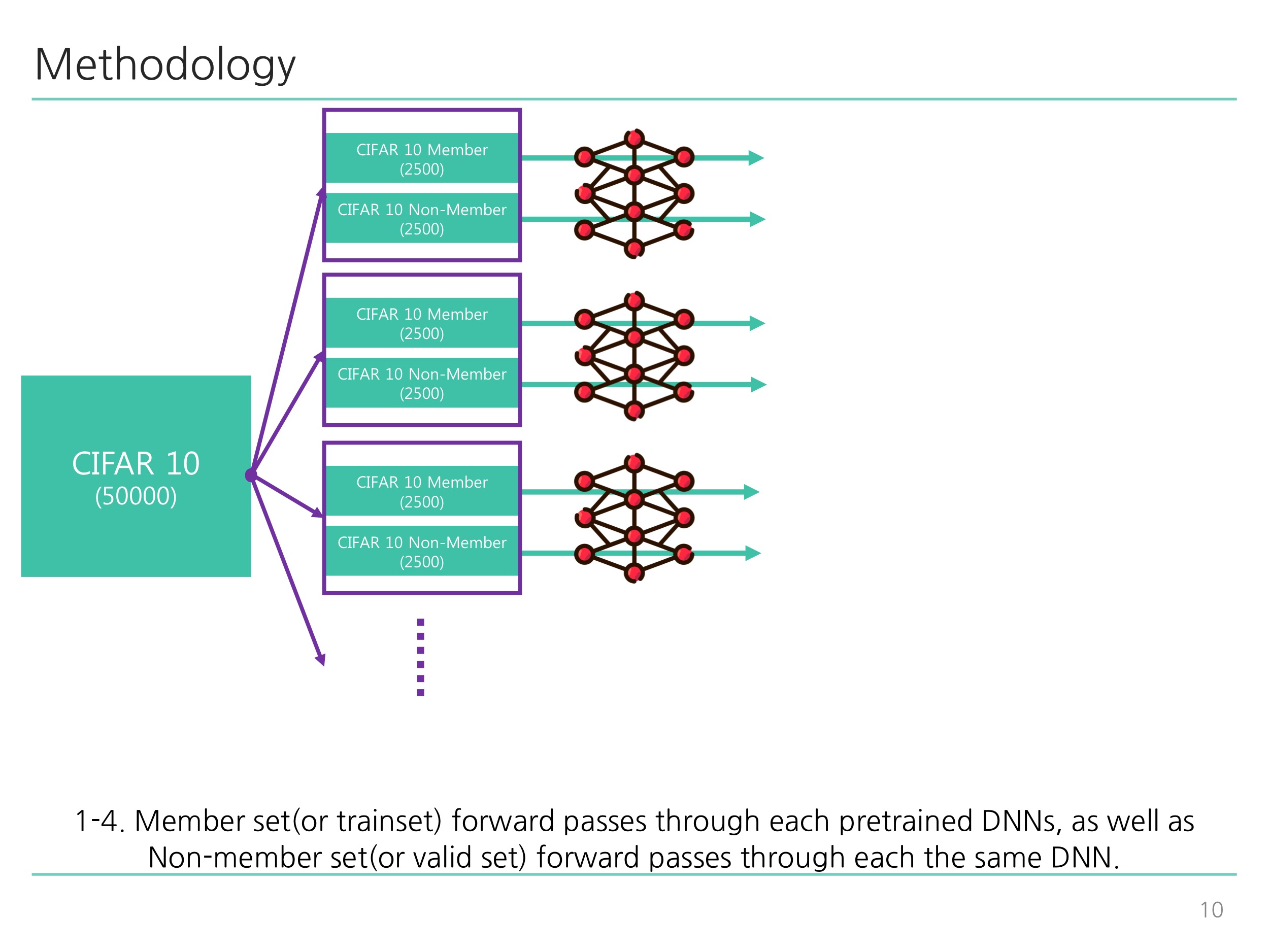
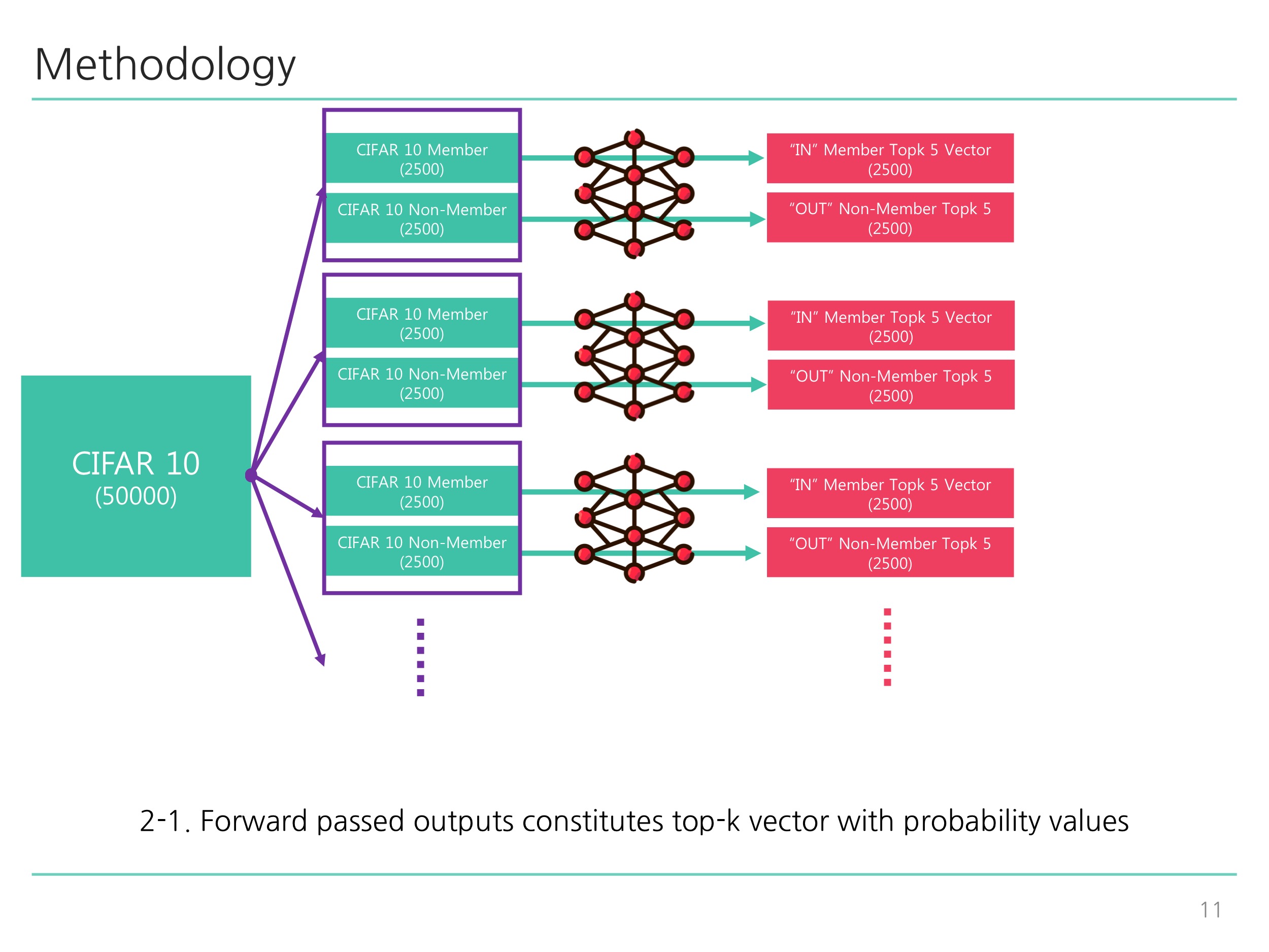
python train_shadow.py: Corresponds to Diagram 1-1 ~ Diagram 2-2 illustrated below. -
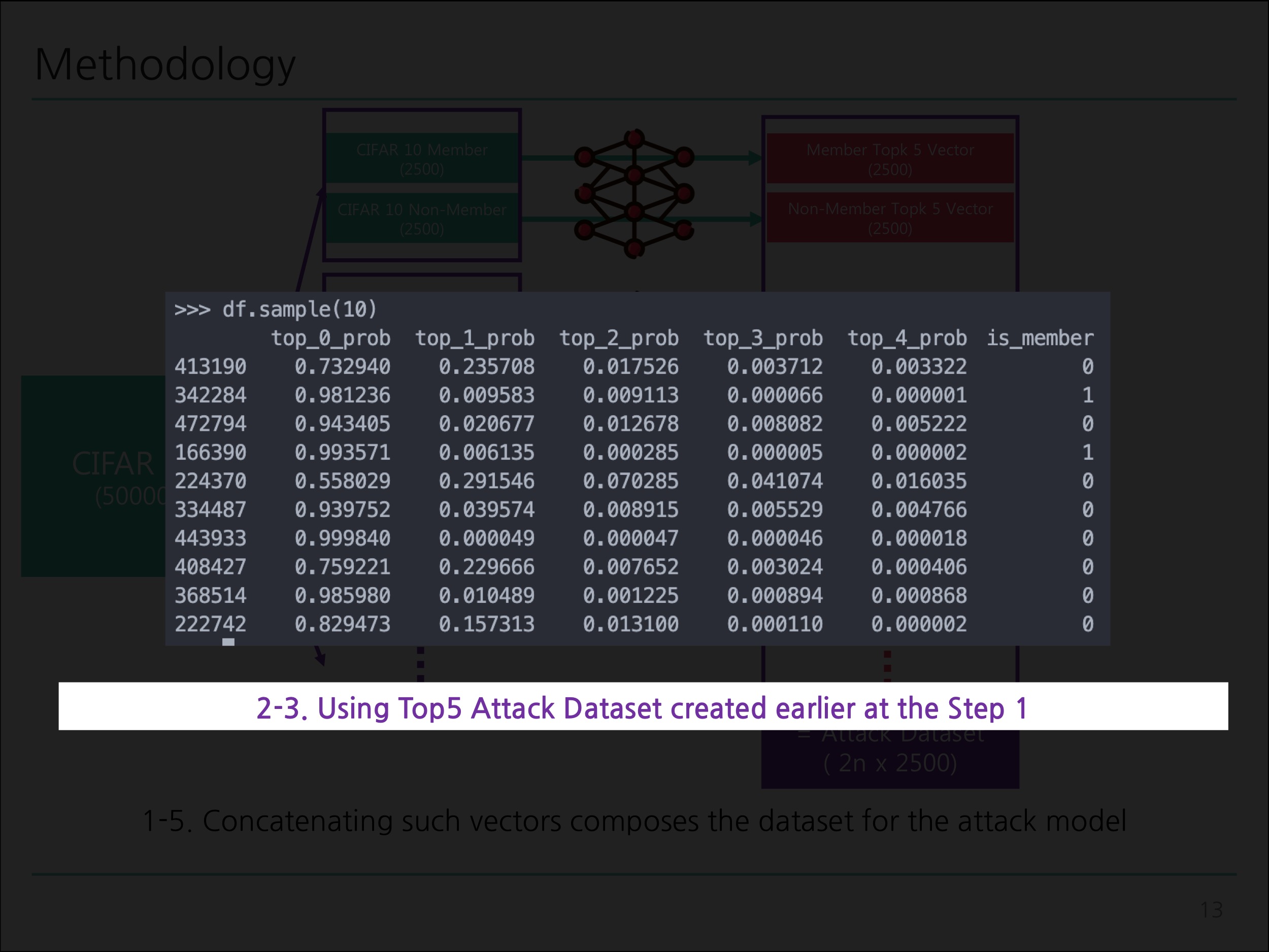
python train_attack.py: Corresponds to Diagram 2-3 ~ Diagram 3 illustrated below. -
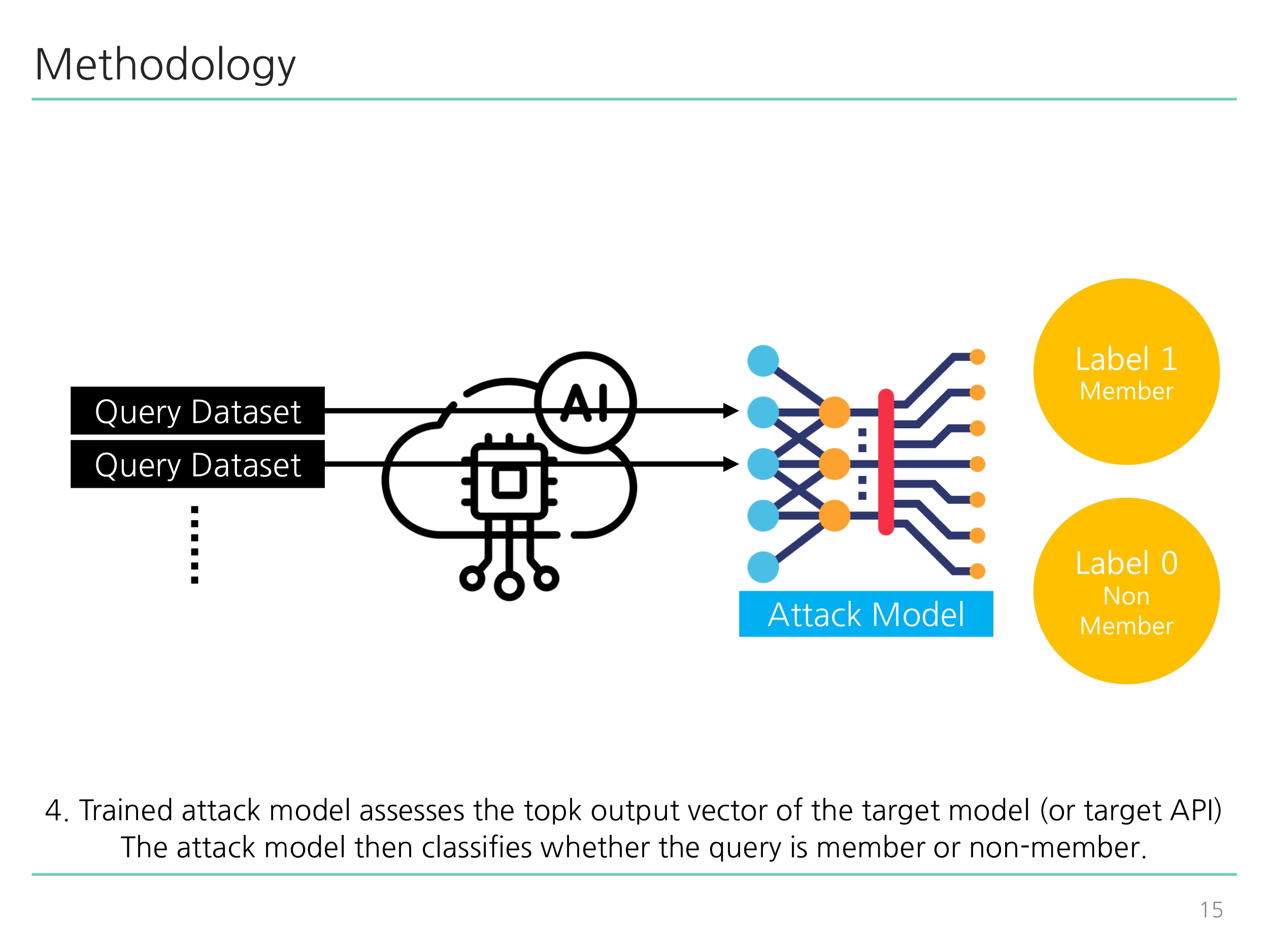
python inference_attack.py: Corresponds to Diagram 4 illustrated below.
- Replicated the paper's configuration on config.yaml
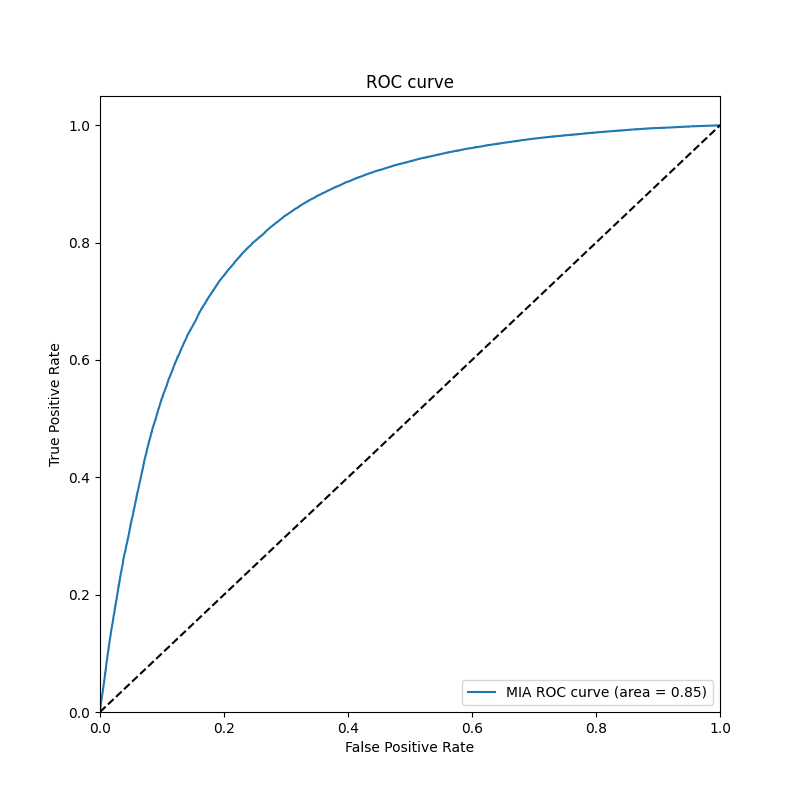
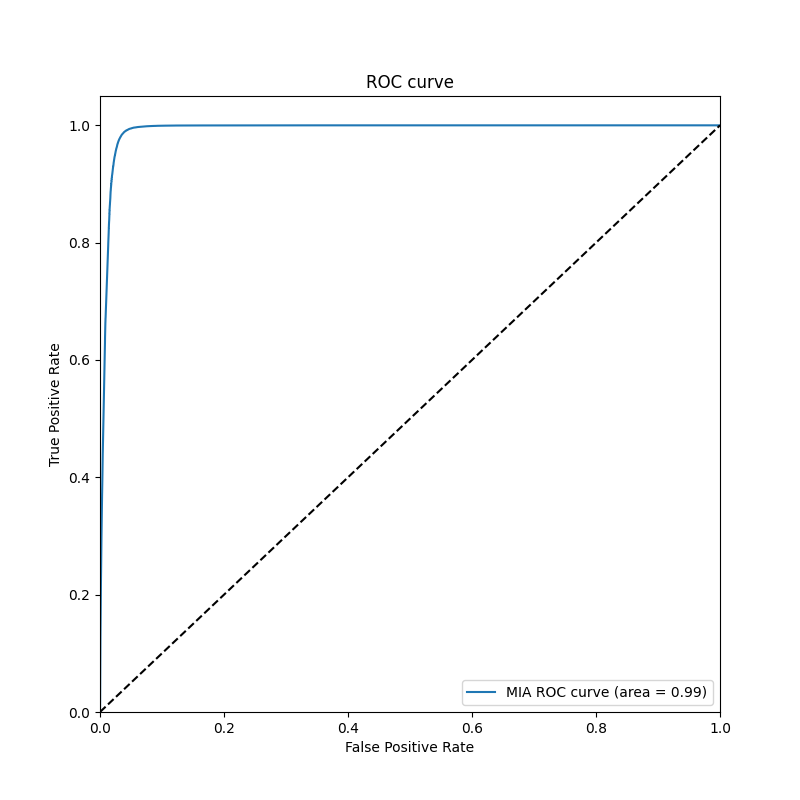
- ROC Curve is plotting
TPR / FPRaccording to MIA classification thresholds
| MIA Attack Metrics | Accuracy | Precision | Recall | F1 Score |
|---|---|---|---|---|
| CIFAR10 | 0.7761 | 0.7593 | 0.8071 | 0.7825 |
| CIFAR100 | 0.9746 | 0.9627 | 0.9875 | 0.9749 |
| MIA ROC Curve CIFAR10 | MIA ROC Curve CIFAR100 |
|---|---|
 |
 |