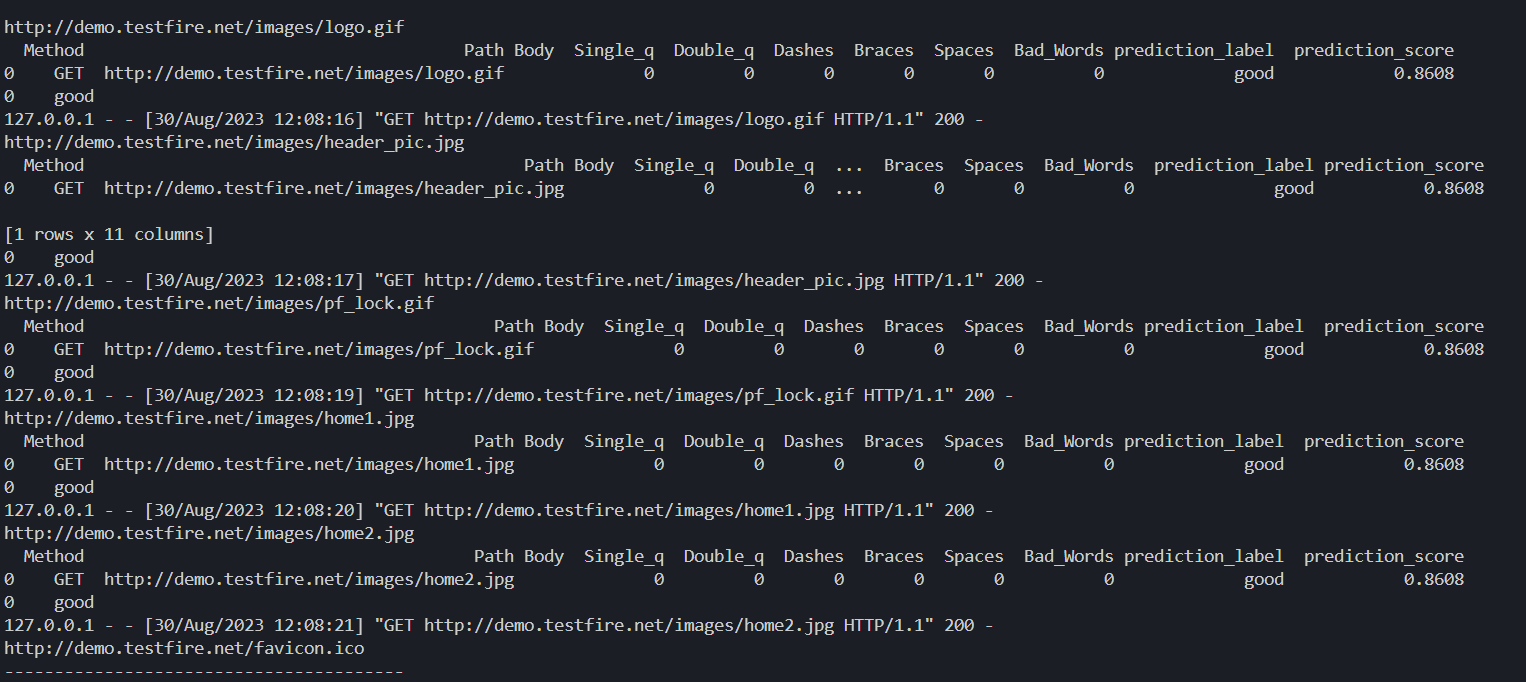
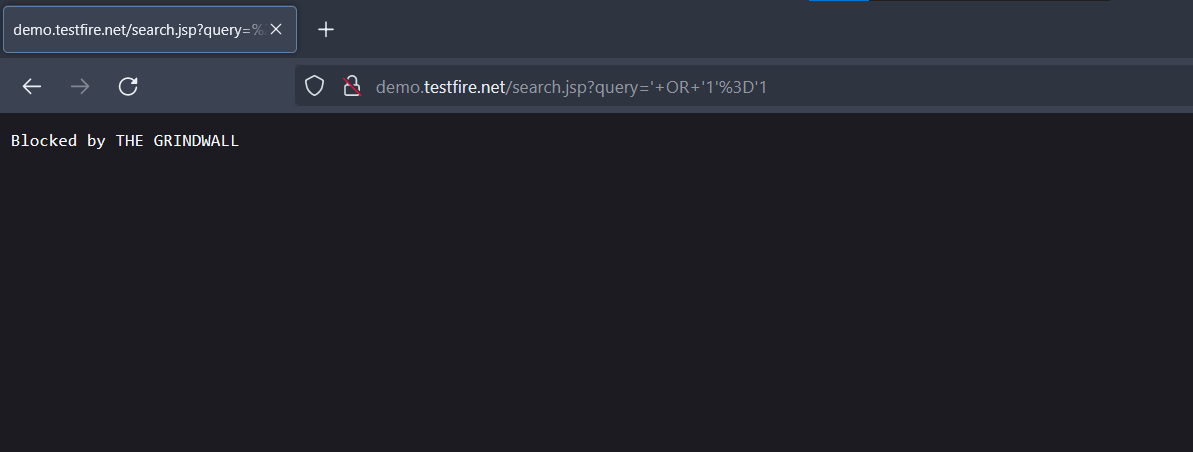
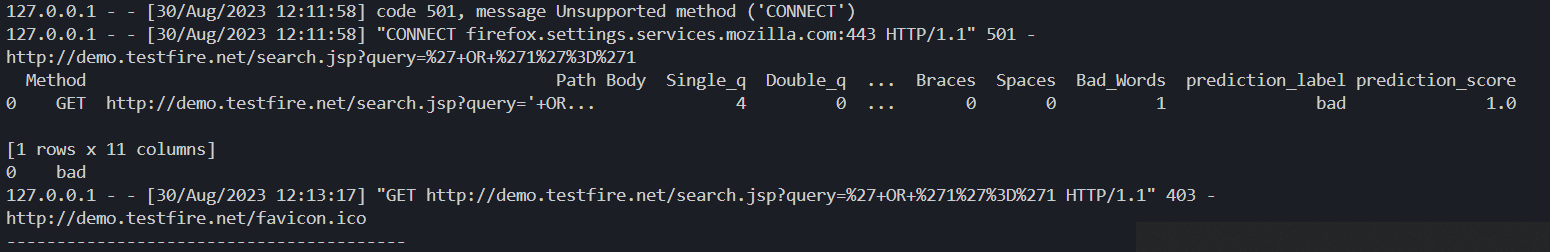
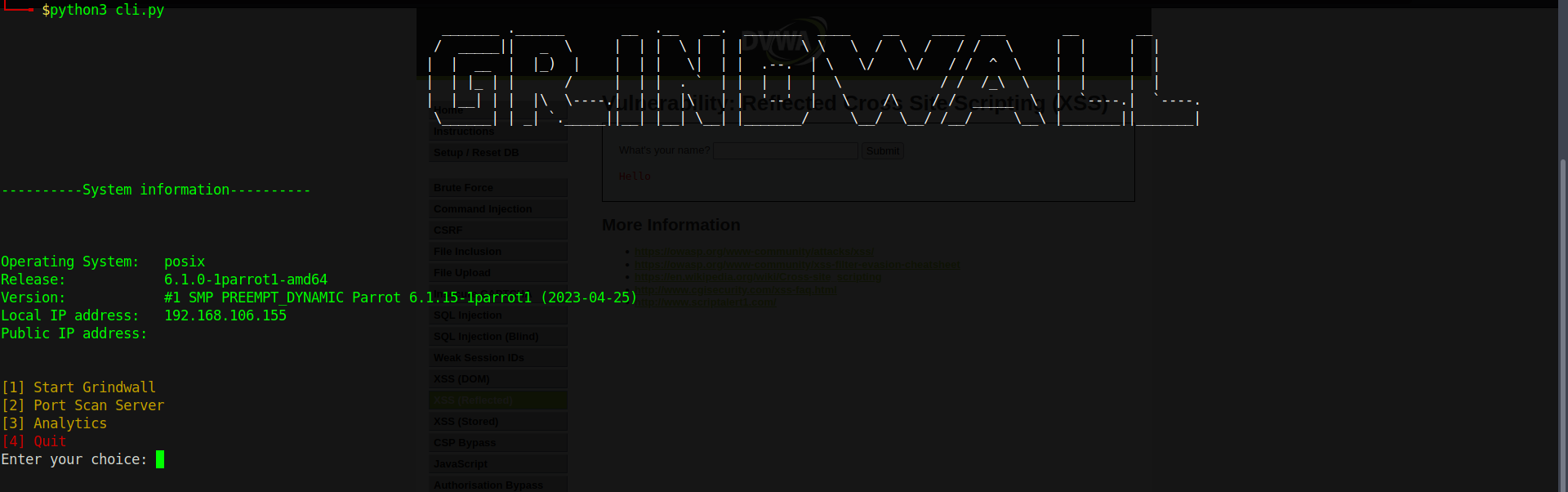
Grindwall is an ML based Firewall System that uses a machine learning model to filter out bad or malicious requests to the server.
- full_xss_sqli_dataset.csv = Dataset for training the model - Version 1
- version_4_full.csv - Full dataset for Version 4(includes cmdi)
- new_specs_dataset.csv - Dataset for classifying according to vulnerability.
- network_sec.ipynb = Notebook file used for creating the model and other operations related to ML
- grindwall.py = Main Script used to setup the firewall
- requirements.txt = Python Requirements for running the script
- test.csv = Dataset used for testing the model
- gring_gui.py = Scipt to run Grindwall as GUI
Models
- model1_grindwall.pkl = The saved model checkpoint which is loaded into the script for use in the firewall, only filters sqli - Uses Random Forest Classifier
- model2_grindwall = The saved model Checkpoint, which filters sql injections and XSS payloads - Uses Ada Boost Classifier
- model3_grindwall = Saved Model checkpoint that filters on the basis of the vulnerability that the packet tries to exploit; "sqli","xss" or "good"- Uses Random Forest Classifier
- model4_grindwall = Saved Model checkpoint that filters on the basis of the vulnerability that the packet tries to exploit; "sqli","xss","cmdi" or "good" - Uses Light Gradient Boosting Machine Classification
- sqlInjection.txt = Wordlist containing payloads for SQL injection attacks used for dataset preparation
- xss_payloads.txt = Wordlist containing XSS payloads
- cmdi_payloads.txt = Wordlist containing cmdi payloads
- Clone this Repo Install the requirements using the command
pip install -r requirements.txt - Once dependencies are installed run
python cli.pypython gring_gui.py
You can use windows proxy settings by accessing
Settings > Network And Internet > Proxy > Enable proxy with
Address - 127.0.0.1
Port - 1234
Or you can use extensions like Foxy Proxy to use a proxy server for just your browser.