| Branch | Status |
|---|---|
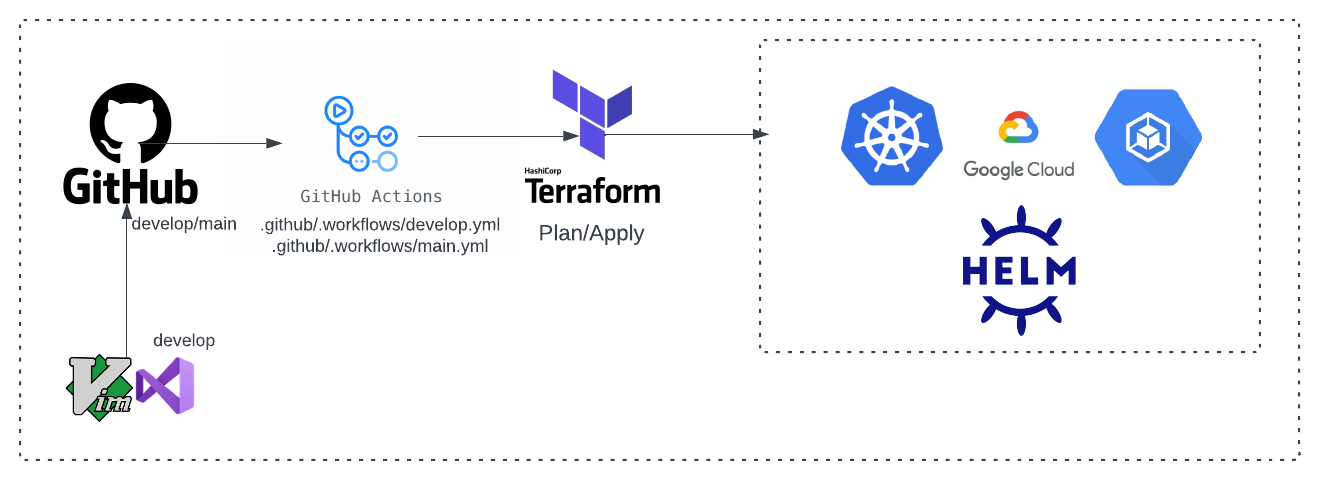
main |
|
develop |
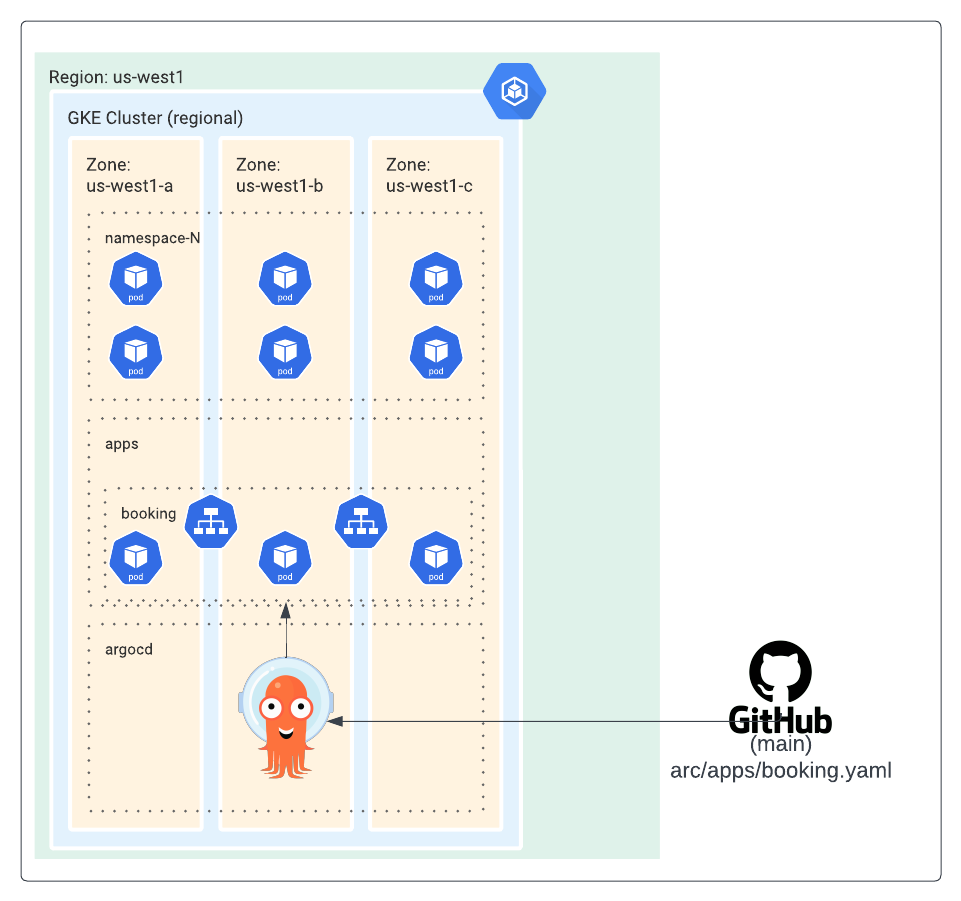
Regional cluster
- Control and Data plane High Availability
- Resilence from zone failure
- Continuous control plane upgrades
- Reduced downtime from control plane failures
Argocd is used for applications deployments to the GKE cluster. For this demo, we are using the raw kubernetes manifest files, but Argocd also supports other methods such as helm.
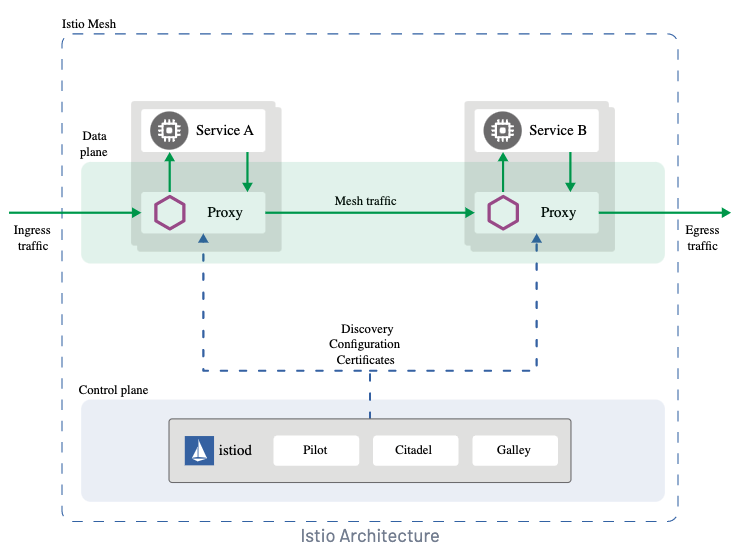
This project uses the istio default monitoring tools:
-
Prometheus, the open source monitoring system and time series database. You can use Prometheus with Istio to record metrics that track the health of Istio and of applications within the service mesh.
-
Grafana, the open source monitoring solution that can be used to configure dashboards for Istio. You can use Grafana to monitor the health of Istio and of applications within the service mesh.
-
Kiali, visualize different aspects of your Istio mesh, such as application wizards, detail views, health, istio configurations, multi-cluster deployments, etc.
- Secure cloud-native apps
- Manage traffic effectively
- Monitor service mesh
- Facilitates multiple deployment strategies
- Simplify load balancing with advanced features
- Enforce security
- End to end encryption with mTLS
For this demo, Booking, the istio example, is used:

- A GCP Service Account file that will be used as a GitHub Actions secret named
GKE_SA, please follow these guide - The GCP
project idyou will deploy to. Currently, the project has this value hardcoded at locals.tf. If you desire to have mo flexibility, you can create adatasourceor use other method to provide the value such as aTF_VAR
kubectl port-forward svc/kiali -n istio-system 5000:20001
kubectl port-forward svc/grafana -n istio-system 5001:3000
Get token:
kubectl get secret -n istio-system $(kubectl get sa kiali-service-account -n istio-system -o "jsonpath={.secrets[0].name}") -o jsonpath={.data.token} | base64 -d
kubectl port-forward svc/argocd-server -n argocd 5002:443
Get password:
kubectl -n argocd get secret argocd-initial-admin-secret -o jsonpath="{.data.password}" | base64 -d
TODO some day