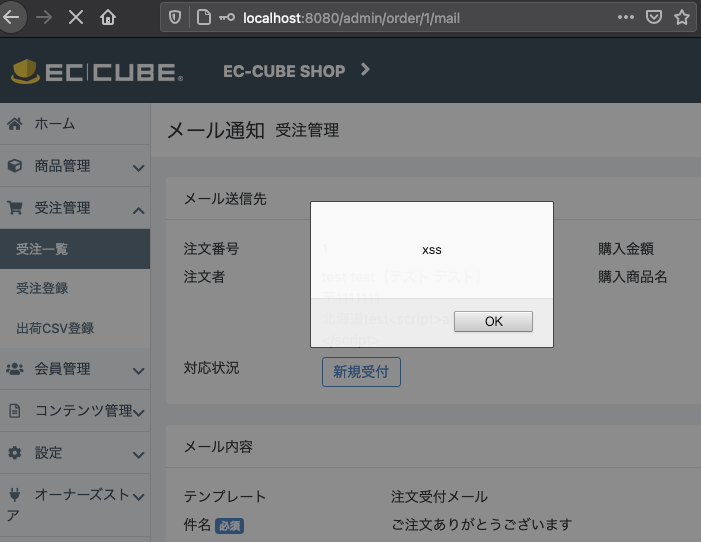
Cross-site scripting vulnerability in EC-CUBE 4.0.0 to 4.0.5 allows a remote attacker to inject a specially crafted script in the specific input field of the EC web site which is created using EC-CUBE. As a result, it may lead to an arbitrary script execution on the administrator's web browser.
- Clone EC Cube
git clone https://github.com/EC-CUBE/ec-cube.git -b 4.0.5
- Docker Build
docker build -t eccube4-php-apache .
- Docker Run
docker run --name ec-cube -p "8080:80" -p "4430:443" eccube4-php-apache
-
Add to Cart & Proceed to Checkout
-
Inject Script to Inquiry Form
- Complete Purchase
https://localhost:8080/admin/login
-
Login admin:password
-
Open Order List Page
-
Click (Malicious) Order
-
Click Create Mail Button
-
Select Template
-
Click Confirm Mail Button
https://github.com/EC-CUBE/ec-cube/commit/9bae20f070acfe0b84451bc1e082c699ac197faf