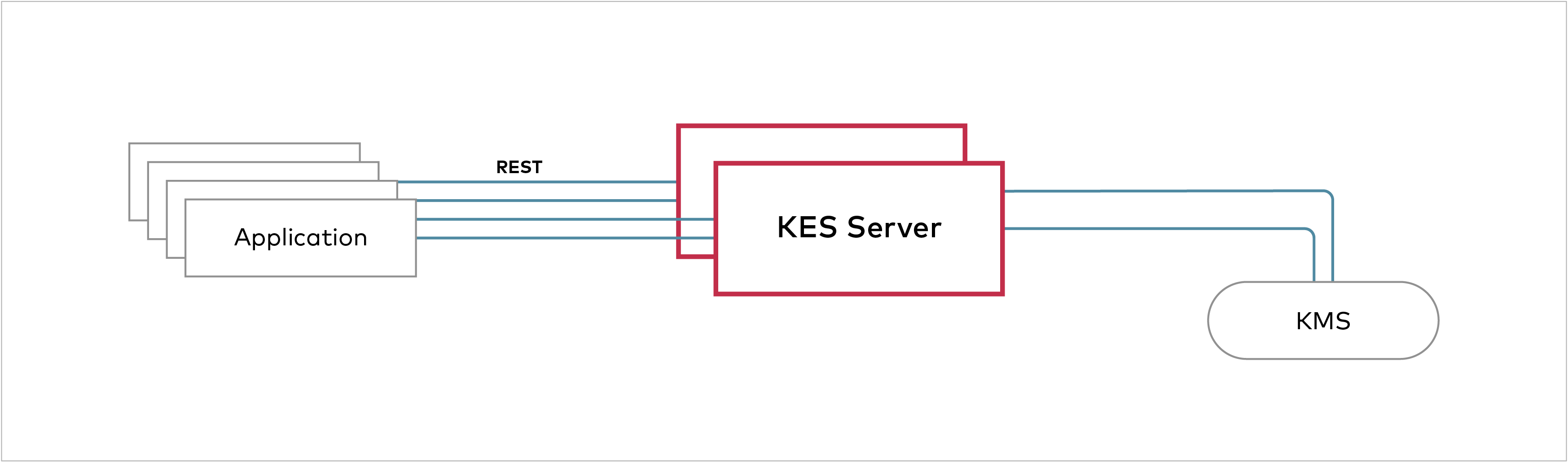
KES is a stateless and distributed key-management system for high-performance applications. We built KES as the bridge between modern applications - running as containers on Kubernetes - and centralized KMS solutions. Therefore, KES has been designed to be simple, scalable and secure by default. It has just a few knobs to tweak instead of a complex configuration and does not require a deep understanding of secure key-management or cryptography.
Binary Releases
| OS | ARCH | Binary |
|---|---|---|
| Linux | amd64 | linux-amd64 |
| Linux | arm64 | linux-arm64 |
| Linux | ppc64le | linux-ppc64le |
| Linux | s390x | linux-s390x |
| Apple M1 | arm64 | darwin-arm64 |
| Apple | amd64 | darwin-amd64 |
| Windows | amd64 | windows-amd64 |
You can also verify the binary with minisign by downloading the corresponding .minisig signature file. Then run:
minisign -Vm kes-<OS>-<ARCH> -P RWTx5Zr1tiHQLwG9keckT0c45M3AGeHD6IvimQHpyRywVWGbP1aVSGav
Build from source
GO111MODULE=on go get github.com/minio/kes/cmd/kes
You will need a working Go environment. Therefore, please follow How to install Go. Minimum version required is go1.18
We run a public KES server instance at https://play.min.io:7373 for you to experiment with.
You can interact with our play instance either via the KES CLI or cURL. Alternatively, you can
get started by setting up your own KES server in less than five minutes.
CLI
As an initial step, you will need to download the "private" key and certificate to authenticate to the KES server as the root identity.
curl -sSL --tlsv1.2 \
-O 'https://raw.githubusercontent.com/minio/kes/master/root.key' \
-O 'https://raw.githubusercontent.com/minio/kes/master/root.cert'Then we point the KES CLI to the KES server at https://play.min.io:7373 and
use the root.key and root.cert as authentication credentials.
export KES_SERVER=https://play.min.io:7373
export KES_CLIENT_KEY=root.key
export KES_CLIENT_CERT=root.certNext, we can create a new master key - e.g. my-key.
kes key create my-key
Note that creating a new key will fail with
key already existif it already exist.
Now, you can use that master key to derive a new data encryption key (DEK).
kes key dek my-keyYou will get a plaintext and a ciphertext data key. The ciphertext data key is the encrypted version of the plaintext key. Your application would use the plaintext key to e.g. encrypt some application data but only remember the ciphertext key version.
For more KES CLI commands run kes --help. For example, you can list all master
keys at the KES server:
kes key lsServer
For a quickstart setup take a look at our FS guide. For further references checkout our list of key store guides.
cURL
As an initial step, you will need to download the "private" key and certificate to authenticate to the KES server as the root identity.
curl -sSL --tlsv1.2 \
-O 'https://raw.githubusercontent.com/minio/kes/master/root.key' \
-O 'https://raw.githubusercontent.com/minio/kes/master/root.cert'Then, you can create a new master key e.g. my-key.
curl -sSL --tlsv1.3 \
--key root.key \
--cert root.cert \
-X POST 'https://play.min.io:7373/v1/key/create/my-key'Note that creating a new key will fail with
key already existif it already exist.
Now, you can use that master key to derive a new data encryption key (DEK).
curl -sSL --tlsv1.3 \
--key root.key \
--cert root.cert \
--data '{}' \
-X POST 'https://play.min.io:7373/v1/key/generate/my-key'You will get a plaintext and a ciphertext data key. The ciphertext data key is the encrypted version of the plaintext key. Your application would use the plaintext key to e.g. encrypt some application data but only remember the ciphertext key version.
For a comprehensive list of REST API endpoints refer to the KES API overview.
If you want to learn more about KES checkout our documentation.
Use of KES is governed by the AGPLv3 license that can be found in the LICENSE file.