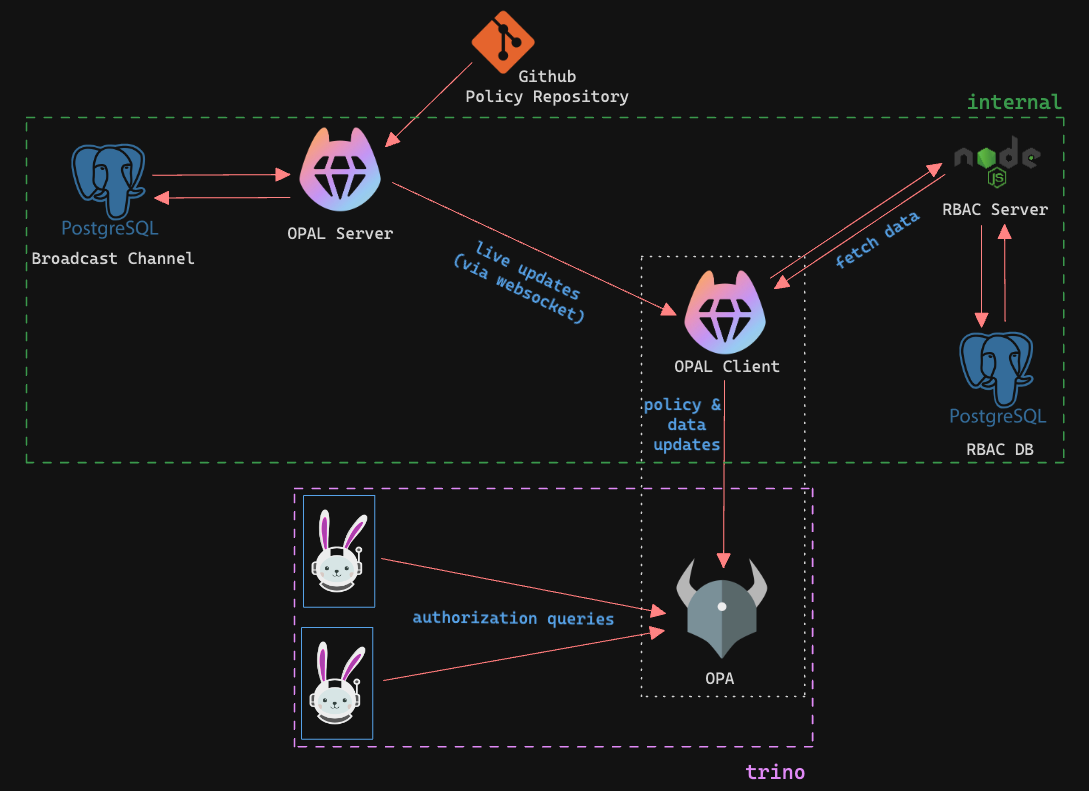
This repository guides you through the process of setting up Trino with OPA for access control.
- This guide assumes that you have a basic understanding of Trino and OPA (Open Policy Agent).
- Trino Version:
440, OPAL Version:0.7.5, Postgres Version:16
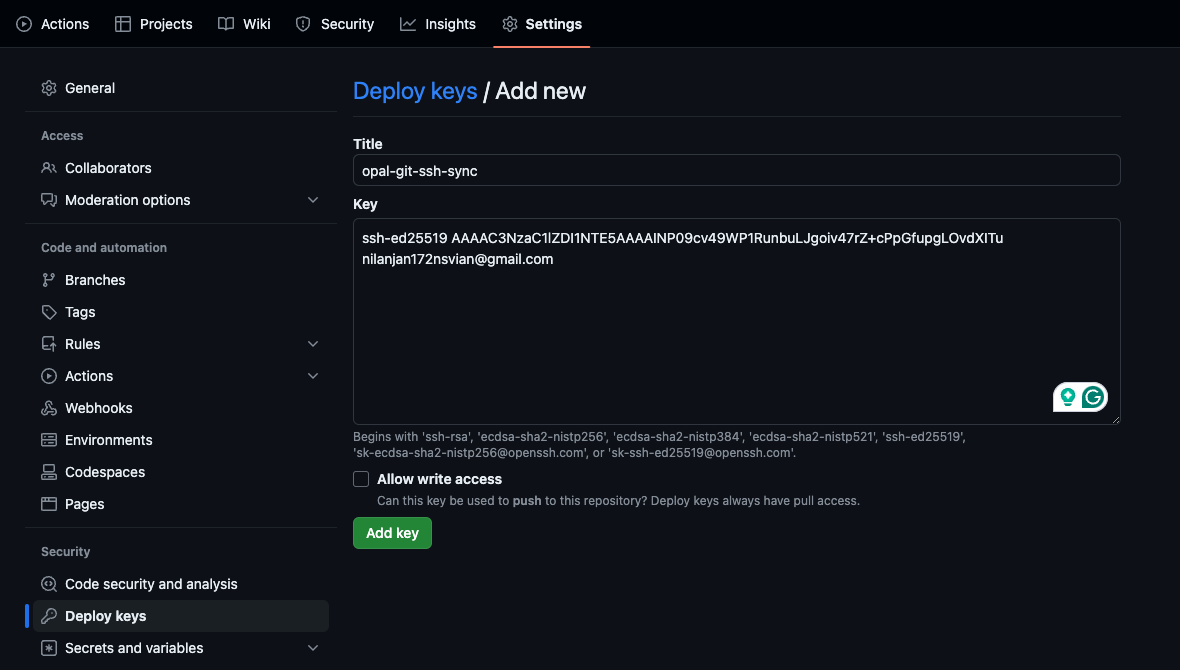
If you are using a private repository for the policy files in OPAL Server, you need to add the SSH Public key to the GitHub repository as a deploy key. Read OPAL Documentation
-
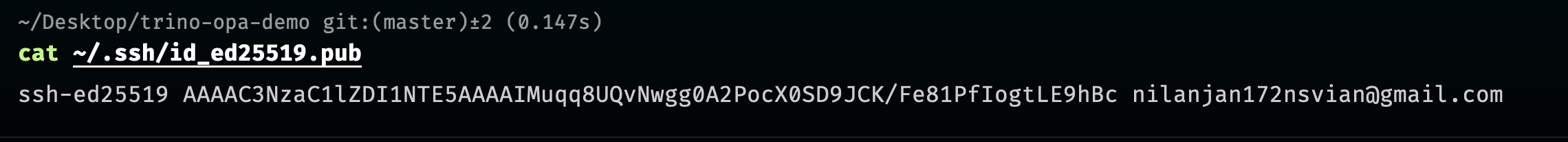
Generate a new SSH key pair using the following command:
ssh-keygen -t ed25519 -C "[email protected]" -
Add the SSH key to the GitHub Repository as a deploy key.
cat ~/.ssh/id_ed25519.pub
-
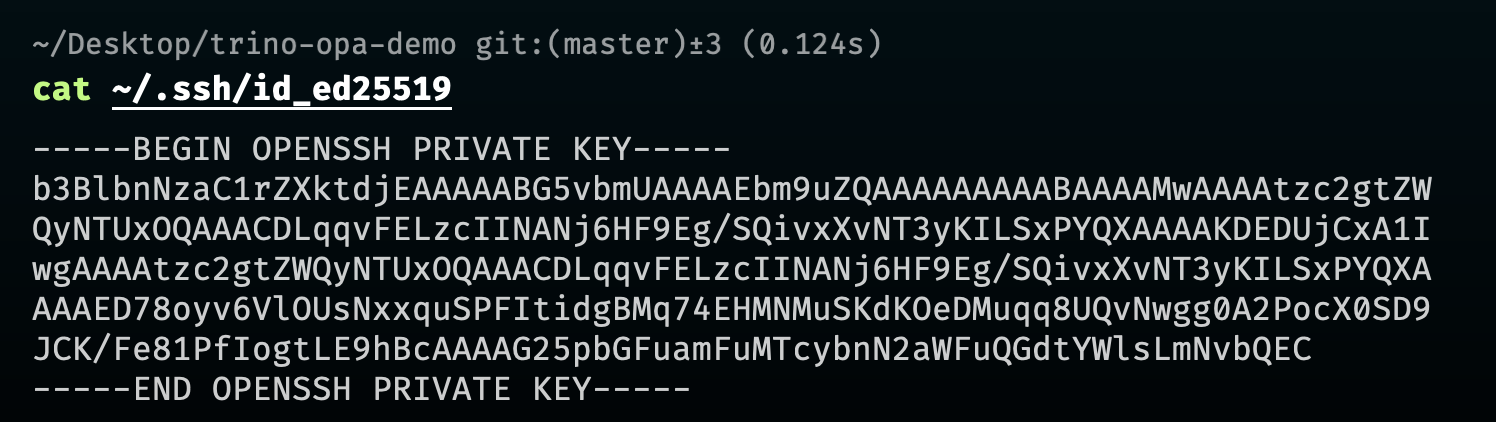
OPAL_POLICY_REPO_SSH_KEY:cat ~/.ssh/id_ed25519OPAL_POLICY_REPO_SSH_KEY="-----BEGIN OPENSSH PRIVATE KEY-----_XX_YY_-----END OPENSSH PRIVATE KEY-----"Replace newline characters (
\n) with underscore (_). -
OPAL_AUTH_PRIVATE_KEYandOPAL_AUTH_PUBLIC_KEY:Please follow the instructions from the OPAL Documentation to generate the RSA keys.
-
OPAL_AUTH_MASTER_TOKEN:python3 -m venv .venv
source .venv/bin/activatepip install opal-server
opal-server generate-secret
Create a .env file with the variables from .env.sample and run the following command:
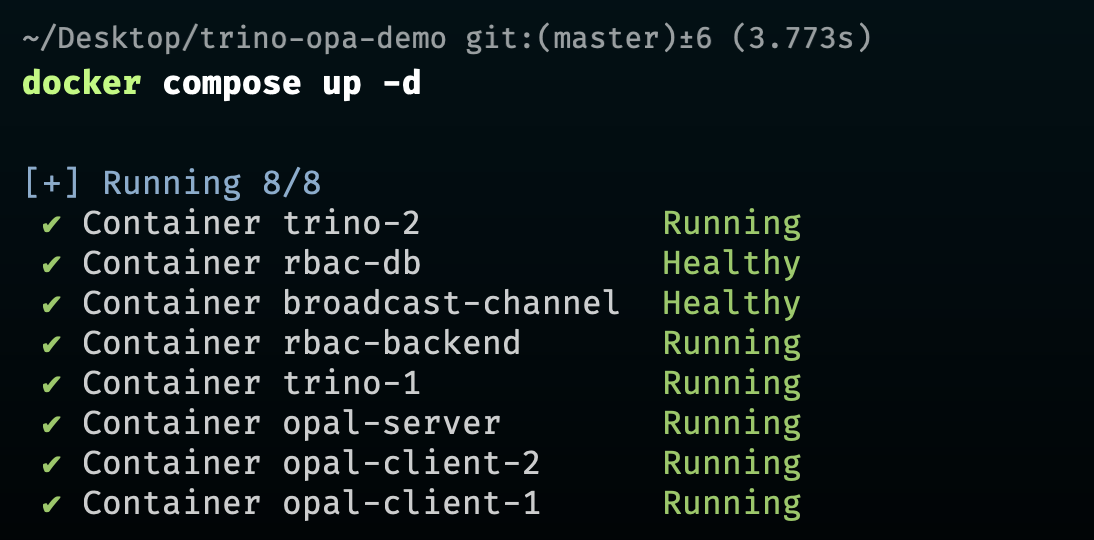
docker compose up -dPlease use this Postman Collection to create users, groups, and policies.
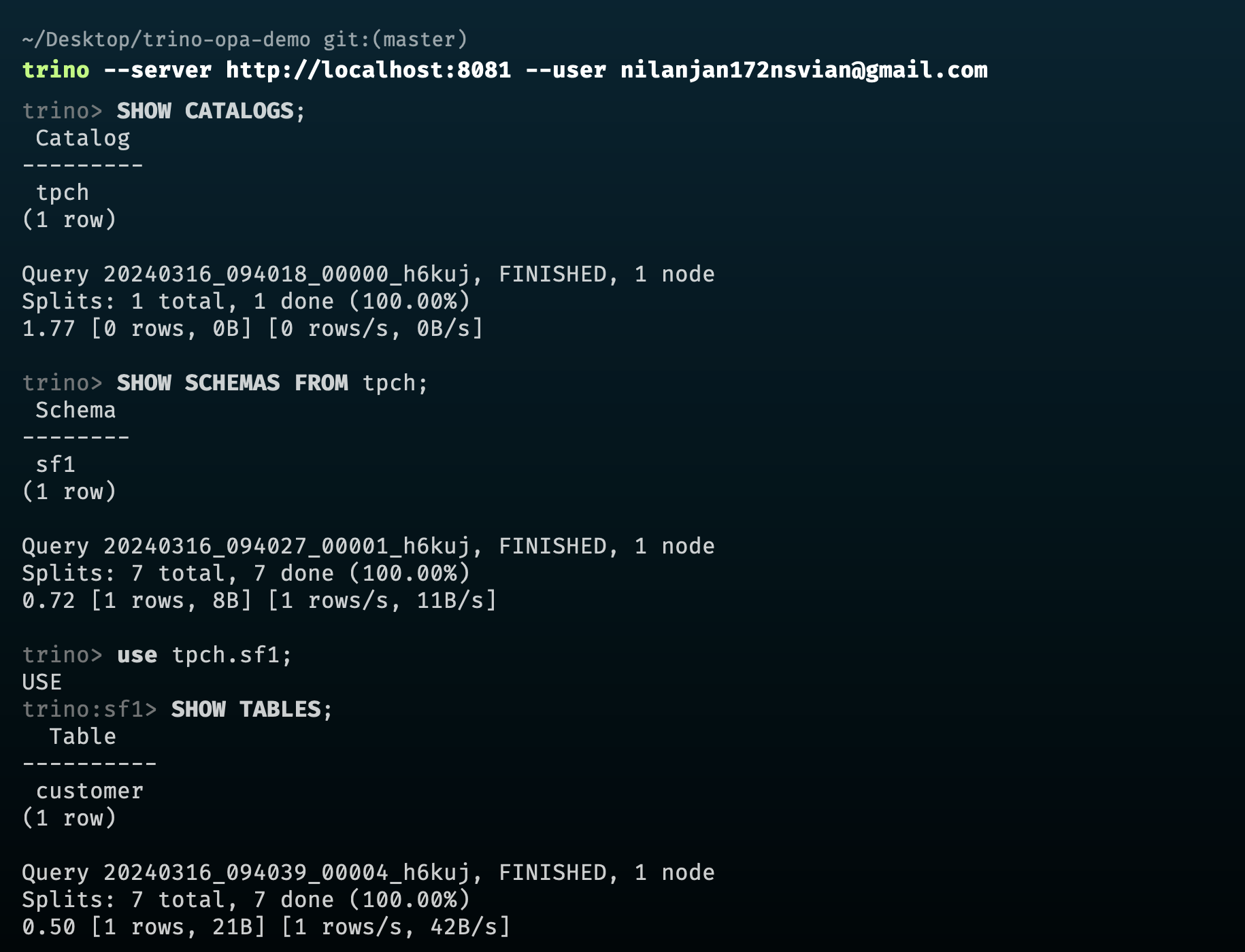
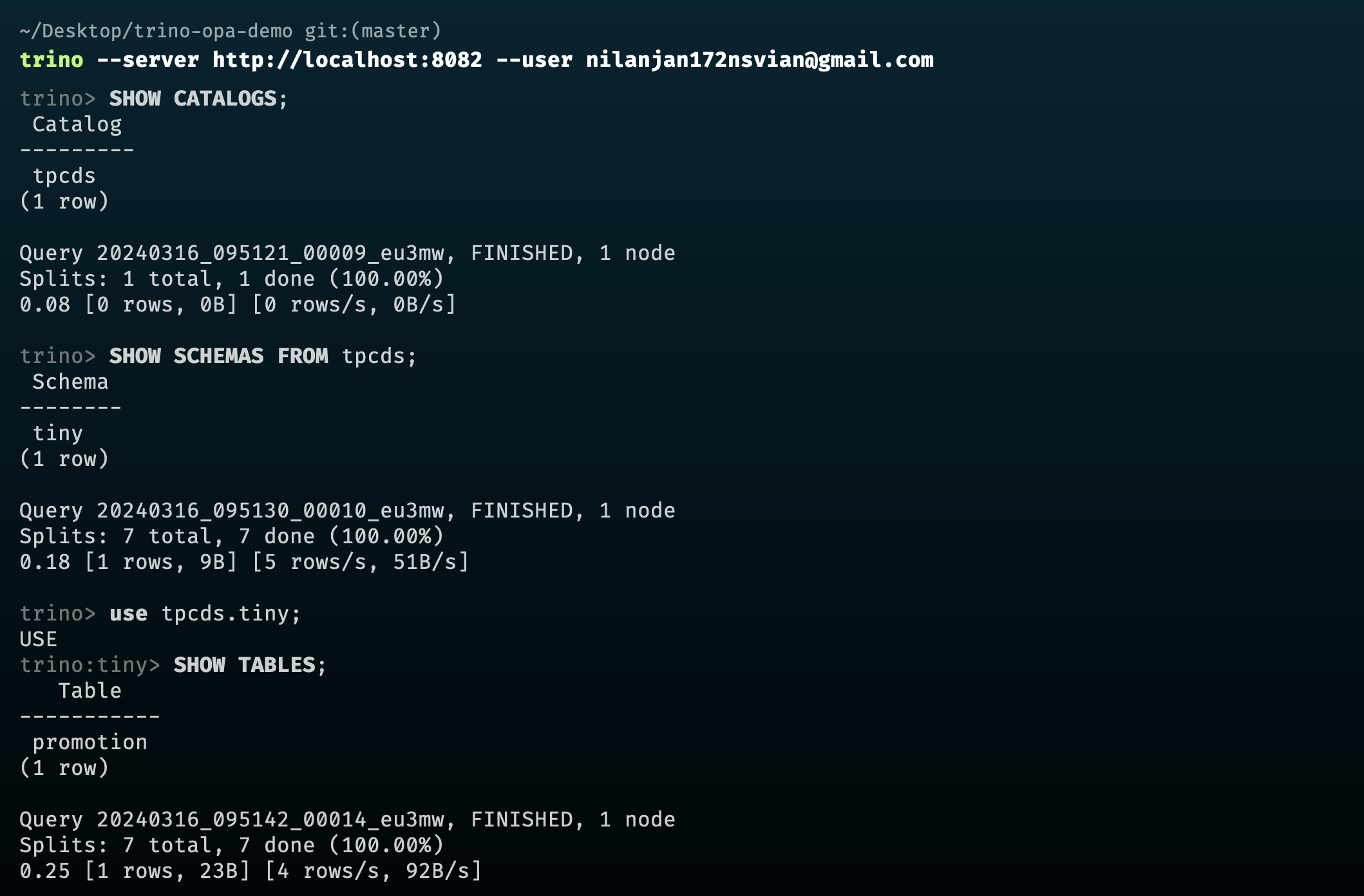
For this demo, I have created a user [email protected] and associated it with the group sales and with the following access policy:
- Policy 1:
- Catalog:
tpch - Schema:
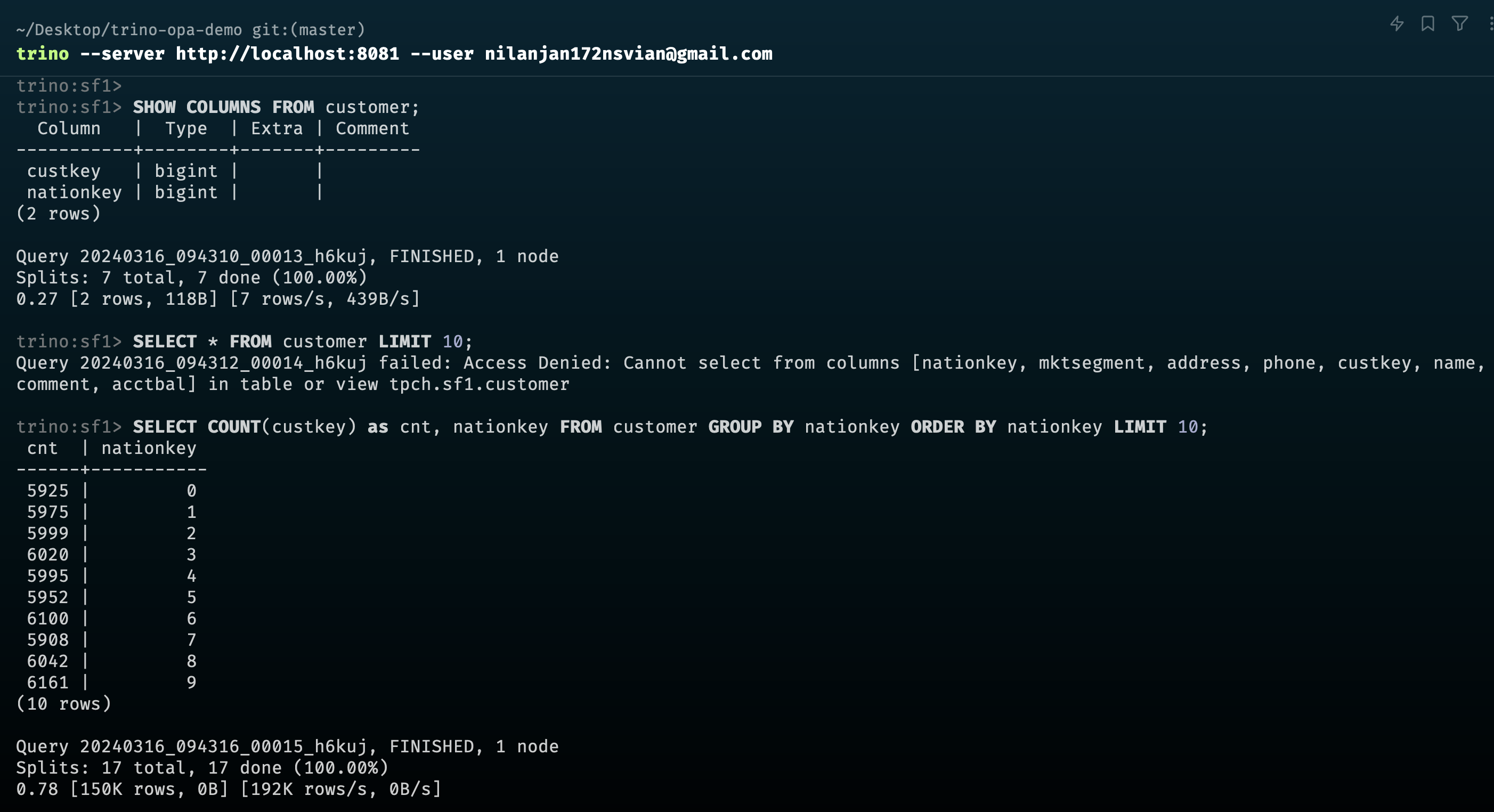
sf1 - Table:
customer - columns:
custkey,nationkey - cluster:
trino-1
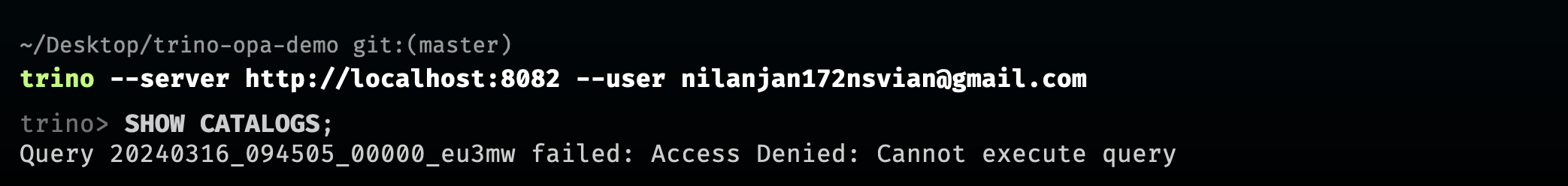
- Catalog:
trino --server localhost:8081 --user [email protected]trino --server localhost:8082 --user [email protected]Now, I have created another group marketing and associated it with the following access policy:
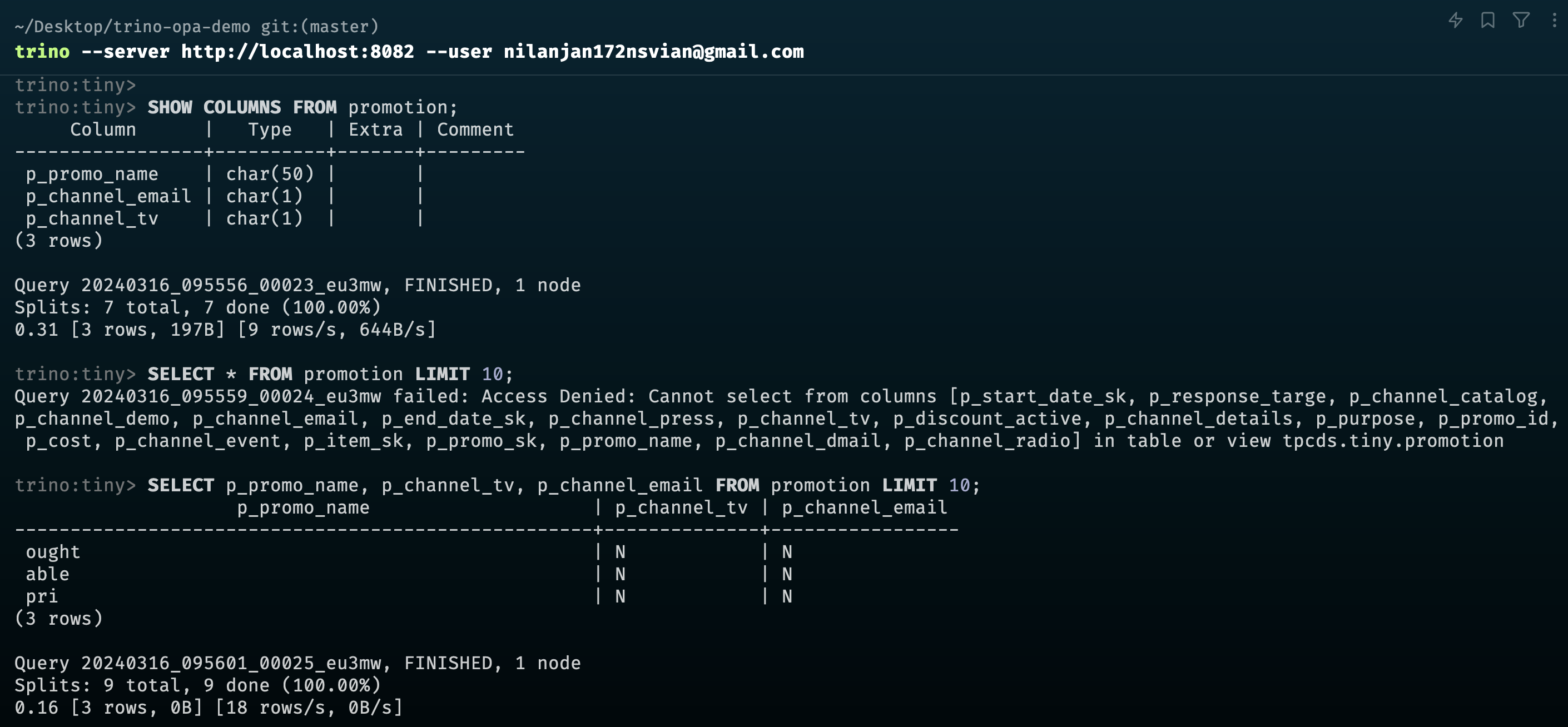
- Policy 2:
- Catalog:
tpcds - Schema:
tiny - Table:
promotion - columns:
p_promo_name,p_channel_tv,p_channel_email - cluster:
trino-2
- Catalog:
trino --server localhost:8082 --user [email protected]- Trino OPA Docs
- Open Policy Agent
- OPAL Server Configuration
- OPAL Client Configuration
- Trino OPA Example by Dragon Pomelo
- Sequelize Node.js ORM
Made with ❤️ by nil1729