We all know that Microsoft's recommended approach for analysing Azure Firewall logs is to set up a Log Analytics Workspace to collect all the data and use Kusto (KQL) queries to check the results.
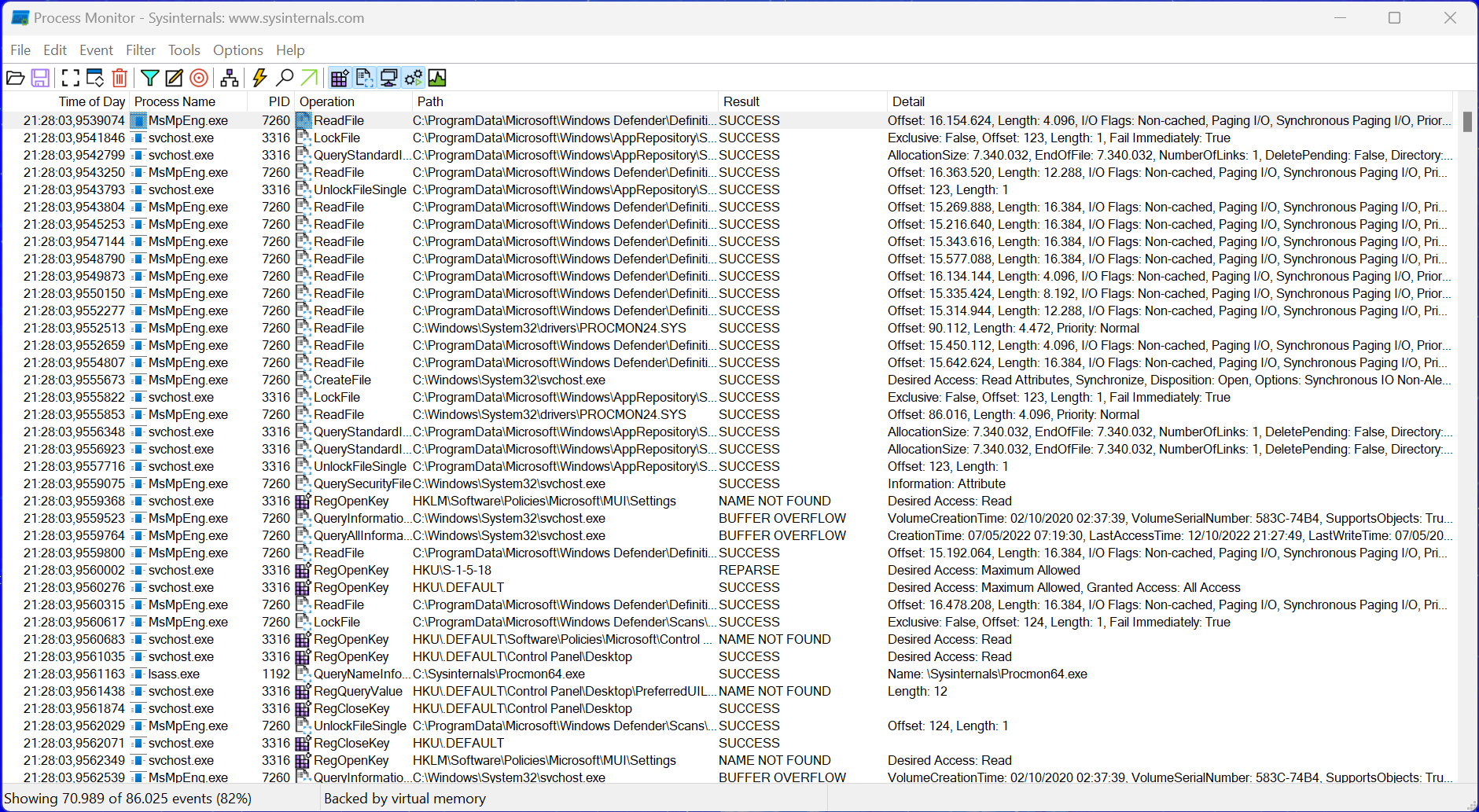
Azure-Firewall-mon focuses more on providing a tool that can answer the simple question "what is happening right now?" in an alternative and hopefully practical way: the idea is to provide an approach much more like Sysinternals Process Monitor or Check Point's SmartView/SmartLog, where there is no KUSTO queries or dashboards that you need to implement first to get working. Still, all events are available as a log-stream.
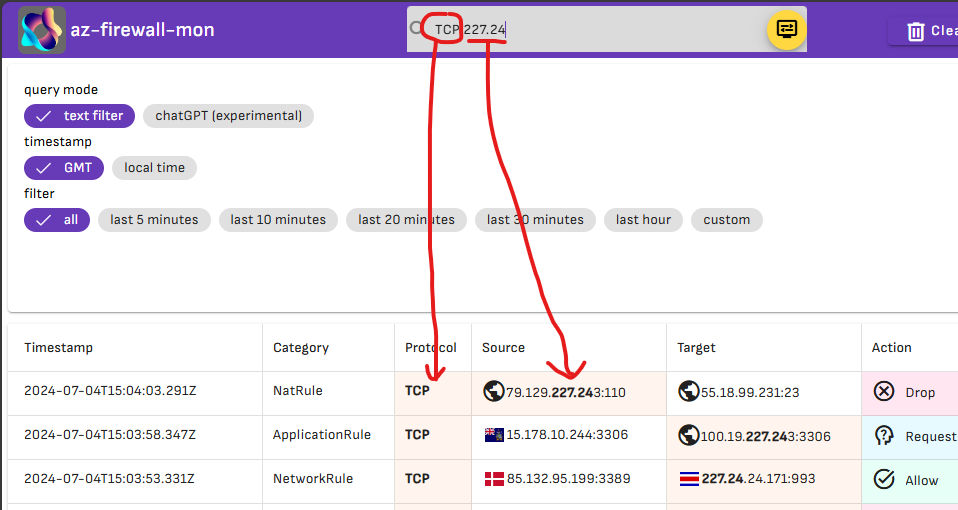
The real strength of the tool is the search field available in the top toolbar. To search for an event, simply start typing and the log flow will be automatically filtered according to those parameters.
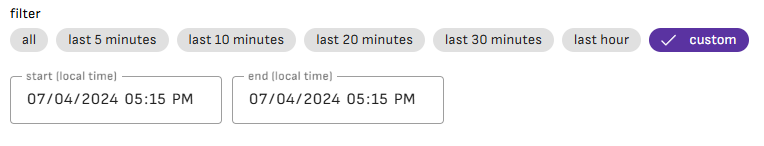
The timestamp field displays the event date in UTC or local format. You can filter the view for the last few minutes or for a specific time range.
Within this tool, only events from the last 24 hours will appear because this is the duration set on the Event Hub Namespace. A longer duration would slow down the tool and not help answer the question "what is happening right now" that az-firewall-mon aims to address.
As an alternative to full-text search, you can use the chatGPT mode: in the top search field, you can enter a request in natural language, and the system will filter the content accordingly.
Some examples of queries are as follows:
- "Show me events from the last 15 minutes"
- "Search project alpha"
- "Filter rows with category containing "NetworkRule""
- "Filter events between 12:00 and 13:00"
- "Filter for target containing 192.168.1.1"
- "Include only logs with protocol TCP"
- "Show me only the deny actions"
- "More information on source 192.168.1.1"
Azure-Firewall-mon is an open source, Single Page Application, written in Angular.
To use this app with YOUR data, you must perform the following steps on your Azure Subscription:
-
Create an Azure Event Hub Namespace
-
Create an Azure Event Hub inside the namespace, with a
1-day retentionand1 partition -
Create a Shared Access Policy, with Listen claim
-
Create an Azure Map Account
-
Create an Azure OpenAI Service
-
Go to OpenAI Studio > Deployments > Create a new deployment using as model
gpt-4-32k v0613 -
Open the Azure Firewall instance you want to monitor, go to Monitoring > Diagnostic Settings > Add Diagnostic Settings:
- Select all logs and "Stream to Event Hub"
- Select the Event Hub Namespace and Hub created above
- click
SAVE
Lazy engineers can performs steps from 1 to 6 by clicking the following button :-)
Now, open https://az-firewall-mon.duckiesfarm.com/ and do the following:
- copy in the
Event Hub Connection Stringfield the connection string of the Shared Access Policy created above - copy the corresponding
Event Hub Consumer GroupName - copy in the
Azure Map Account Shared Keyfield the primary or secondary Shared Key of the Azure Map Account created above - copy in the
Azure OpenAi Endpointfield the enpoint URI for the OpenAI resouce created above - copy in the
Azure OpenAI deploymentfield tne name of the deployment created above - copy in the
Azure OpenAI access keyfield the primary or secondary Shared Key of the Azure OpenAI account created above - click on
Let's begin.
@lukemurraynz has written a very detailed blog post on how deploy Azure-Firewall-mon in an Azure Static Web App. If you prefer this approach, have a look at his blog post https://luke.geek.nz/azure/deploy-azure-firewall-mon-to-a-static-web-app/
NOTE:
environment.prod.tsmust be updated with your environment information. az-firewall-mon requires an Application Insights instance to work properly.
Azure Firewall (AF) is a cloud-native and intelligent network firewall security service that provides the best of breed threat protection for your cloud workloads running in Azure. It's a fully stateful, firewall as a service with built-in high availability and unrestricted cloud scalability. It provides both east-west and north-south traffic inspection.
Azure Monitor helps you maximize the availability and performance of your applications and services. It delivers a comprehensive solution for collecting, analyzing, and acting on telemetry from your cloud and on-premises environments.
AF (Azure-Firewall-Mon) is integrated with Azure Monitor. This means you can forward AF metrics and logs to:
- Log Analytics Workspace
- Azure Storage
- Event hub
A Log Analytics workspace is a unique environment for log data from Azure Monitor and other Azure services. Each workspace has its own data repository and configuration but might combine data from multiple services.
Be mindful, that the ingest of logs into a Log Analytics workspace has some Latency, so you may see a delay with the logs displaying.
Latency refers to the time that data is created on the monitored system and the time that it comes available for analysis in Azure Monitor.
The Kusto Query Language is a tool to explore your data in a Log Analytics Workspace. The query uses schema entities that are organized in a hierarchy similar to SQL's: databases, tables, and columns.
Check Point's SmartView web log access
SysInternals process monitor
- 90342-security.json lottie animation by Kawsar Mahmud
- lf20_giodppcr.json lottie animation by hdev coder
- rubik.json lottie animation by Ision Industries
- Logo built with the new Bing