A Windows DLL which hooks low-level Winsock 2 APIs to redirect sockets to a SOCKS5 proxy server.
Over time less and less modern network-enabled applications offer the user with the ability to specify an HTTP or SOCKS proxy server. For this specific need, so called "proxification" applications exist, which are unfortunately scarce and closed-source. This fork is an attempt to provide a modern, working and open solution for this very specific case.
Socksifier is a self-contained DLL with no external dependencies (except the APIs shipped with Windows) that is meant to get loaded into the process who's connections should get "proxified" and achieves this by API-hooking the low-level connect, bind, WSASendTo, WSARecvFrom and closesocket functions. API-hooking is performed upon library load using the well-known and battle-tested Microsoft Detours library.
After the hook is established, the process's existing connection handles get enumerated and terminated, forcing the network layer of the application to re-establish them, but now calling the hooked API-variant instead.
The detoured functions contain the logic necessary to re-route the to-be-established socket connection to a SOCKS5 proxy by performing the necessary protocol-specific handshake and upon success simply returns the socket back to the callee, which is now transparently talking to the proxy instead of the origin destination (e.g. HTTP(S) or WebSocket connection).
This project has been designed for and tested with Electron-based applications and Shadowsocks as SOCKS5 proxy only. Rudimentary UDP tunneling support for WebRTC sessions is implemented, but should be considered experimental.
Other use-cases might work but are left to the reader to discover by experimentation.
Currently only IPv4 support is implemented.
This project makes heavy use of code and mechanisms unfortunately widely (ab)used by malware (loading foreign code into processes, manipulating handles and network traffic flow), therefore might trigger anti-virus/anti-cheat solutions. Make sure to add an exclusion to your AV in case this becomes and issue and refrain from injecting into anti-cheat protected games as this might pose the risk of a false-positive ban. You have been warned ❤️
The reader is highly encouraged to study the code and build the project by themselves instead of trusting the provided binaries.
You can build individual projects of the solution within Visual Studio 2022 (any edition is fine).
You can get pre-built binaries (x86, x64) at the release page.
To enable the redirection you just have to inject the DLL into your target process. Either use a DLL injector tool or make injection persistent across application launches with additional help from LoadDLLViaAppInit or similar tools (IAT patching and alike).
Optionally set up the following environment variables to configure the DLL. Default values are used if omitted.
SOCKSIFIER_ADDRESS- IP address of the SOCKS5 proxy to connect to (defaults to127.0.0.1)SOCKSIFIER_PORT- Port of the SOCKS5 proxy to connect to (defaults to1080)
The default values assume that a Shadowsocks client is running and listening on localhost.
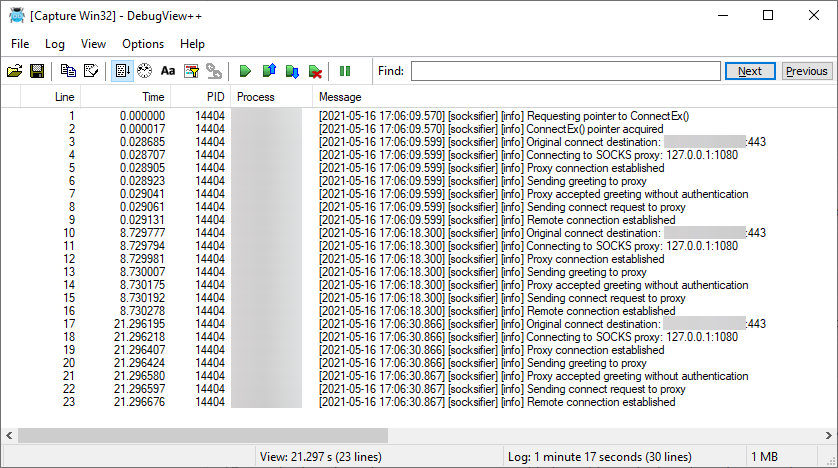
The library logs to the Windows Debugger Backend and can be observed with DebugView++ or similar.
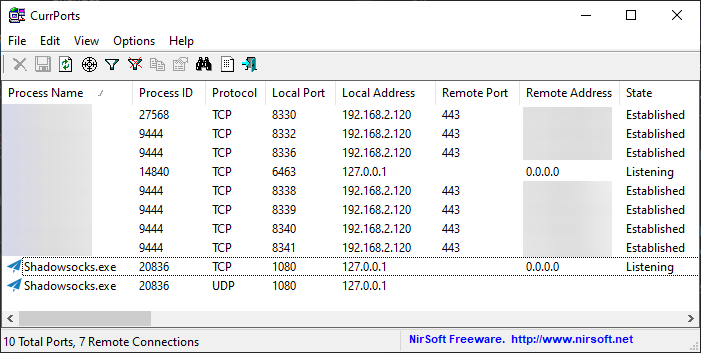
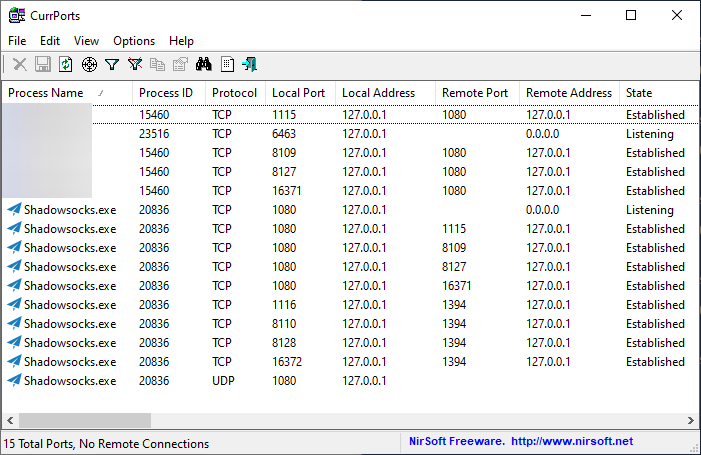
Observe the change in network connections with e.g. NirSoft CurrPorts.
This project benefits from these awesome projects and articles ❤ (appearance in no special order):
- Windows Sockets Error Codes
- WSAEWOULDBLOCK error on non-blocking Connect()
- ConnectEx function
- connect function
- WSAGetOverlappedResult function
- Working ConnectEx example
- Simple SOCKS5 client written in C++
- WSock Socks5 proxy forwarding POC
- SOCKS Protocol Version 5
- shadowsocks-windows
- Sysinternals - Enumerate socket handles
- Get name of all handles in current process
- Get a list of Handles of a process
- Hijacking connections without injections: a ShadowMoving approach to the art of pivoting
- Lateral Movement by Duplicating Existing Sockets
- SYSTEM_HANDLE_TABLE_ENTRY_INFO
- Get Handle of Open Sockets of a Program
- Why does SOCKS5 require to relay UDP over UDP?
- shadowsocks-rust