- v1.0
An ELK Stack deployed with TLS Security for Logs
- Two docker-compose commands and you have a fully functioning ELK stack.
- Set credentials/details with
.envfile - Provides a unified platform to ingest, parse, and visualize log
- Passwords are set using the .env. Default password is "Letmein123!"
- This was built in mind for simple functionality. Not Security.
- Tested with ELK 7.11, 7.12, and 7.13.0 on Ubuntu 20.04 and Docker-Compose 3.7
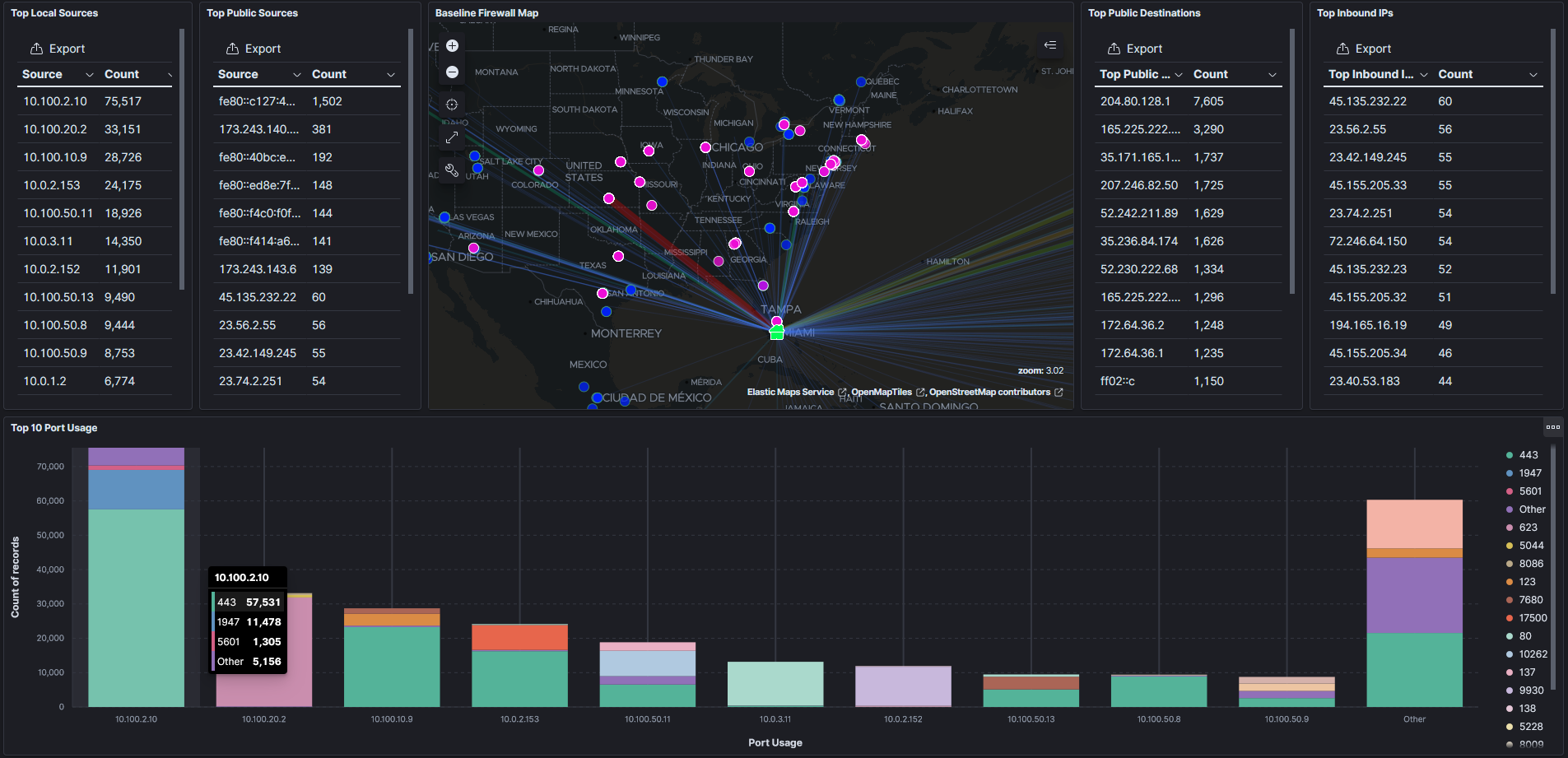
This was built with a focus on Network Security logging, analysis, and alerting, but can be used for any other log analysis. Currently, this is ships with a Logstash Pipeline for analyzing Check Point and Fortinet logs and processing them into the ECS.
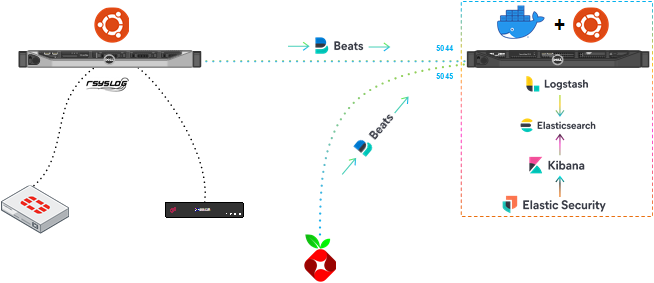
Here is the basic topology of how I use it:
- Check Point and Fortinet send syslog to a server which does some basic processing with rsyslog. Filebeat is then used to tag and ship the logs to the docker host running Logstash ( Elasticsearch, and Kibana). Filebeat logs for firewalls ingest on port 5044. Logstash converts syslog to the ECS and then Elasticsearch applies an index template. Logs can now be visualized using Kibana and SIEM operations can be performed using Elastic Security. Logstash Pipeline for firewalls can be found in the
firewallpipe.conffile. - PiHole DNS logs now have a pipeline (Added 6/2/2021). I run piHole on an Ubuntu Server for ARM Raspberry Pi and use filebeat send the logs to Logstash on port 5045. Logstash Pipeline for PiHole can be found in the
piholepipe.conffile.
This is just my setup and how I use it. This is a fully functional ELK stack right out of the box and you can simply ingest logs in one of the myriads of ways ELK provides.
- Homelabbers who want a simple functioning ELK stack
- Enterprises looking to test out the ELK stack
- Enterprises looking to not pay by the GB for fancy SIEMs (Bad idea)
- Employees who want to show upper management cool dashboards during their performance review
- Install Docker and Docker-Compose
- Clone Repo
git clone https://github.com/maxabaumgarten/FireELK.git- Create CA and Certificates
docker-compose -f create-certs.yml run --rm create_certs- Build and Start ELK
docker-compose up -d- Login to Kibana @ https://your-docker-server:5601
- User: elastic
- Password: Default: Letmein123! (Or whatever is set in
.envfile)
This will destroy all of your data.
docker-compose down -v- Check Point (Gaia Embedded) -
firewallpipe.conf - Fortinet -
firewallpipe.conf - Check Point (Gaia) - BETA -
firewallpipe.conf - PiHole -
piholepipe.conf
- NGFW Feature ECS Conversion (IPS, AV, Emulation, Filtering, DNS Security)
- Palo Alto Syslog > ECS
- Cisco Syslog > ECS
- VyOS/Ubiquiti Edgerouter Syslog > ECS