🔗 | Lab Description
🔗 | Lab Report
.
├── docs
│ ├── LaTeX
│ │ ├── assets
│ │ │ ├── d_diagram.png
│ │ │ ├── task1.png
│ │ │ ├── task2.png
│ │ │ ├── task3.1.png
│ │ │ ├── task3.2.png
│ │ │ └── task3.3.png
│ │ ├── cite.bib
│ │ ├── ieee.cls
│ │ ├── lix.sty
│ │ └── main.tex
│ ├── LAB.pdf
│ ├── Padding_Oracle_Attack.pdf
│ └── tty.gif
├── docker-compose.yml
├── Makefile
├── main.py
└── README.mdclone the project using the following command:
git clone https://github.com/mabushelbaia/Padding-Oracle-Attack.git
cd Padding-Oracle-Attackmake: default run with 5, 10, 16 bytes.
make bytes n=i: where i is the number of bytes.Skip this part its useless
build and run the docker container make sure you have docker-compose installed sudo apt install docker-compose
docker-compose build
docker-compise up -d #d for detchedThen you can run the script to decrypt the secret message.
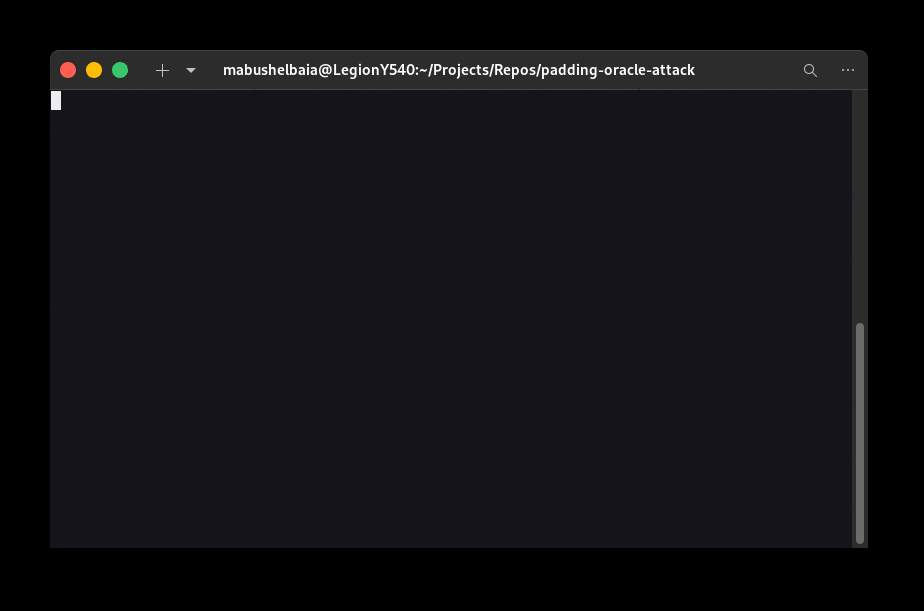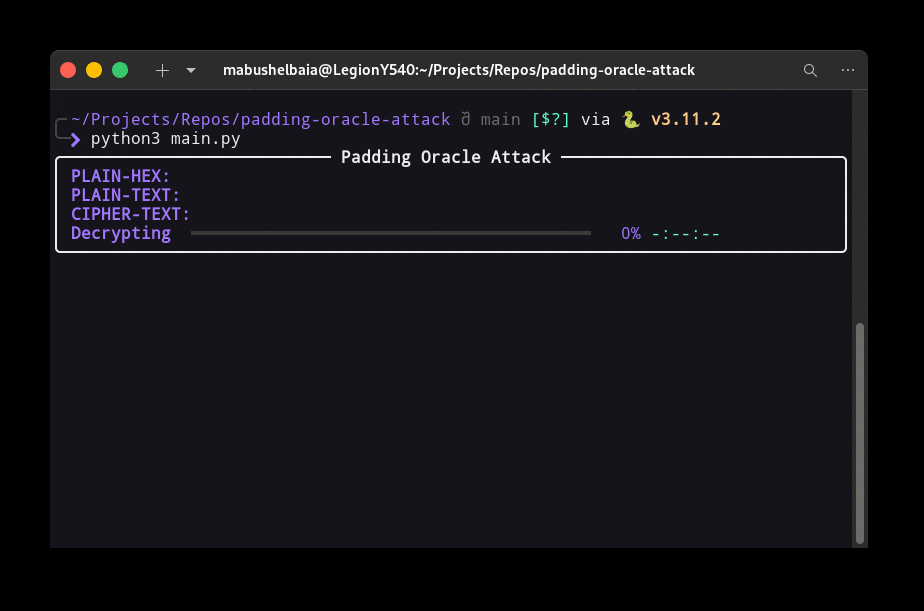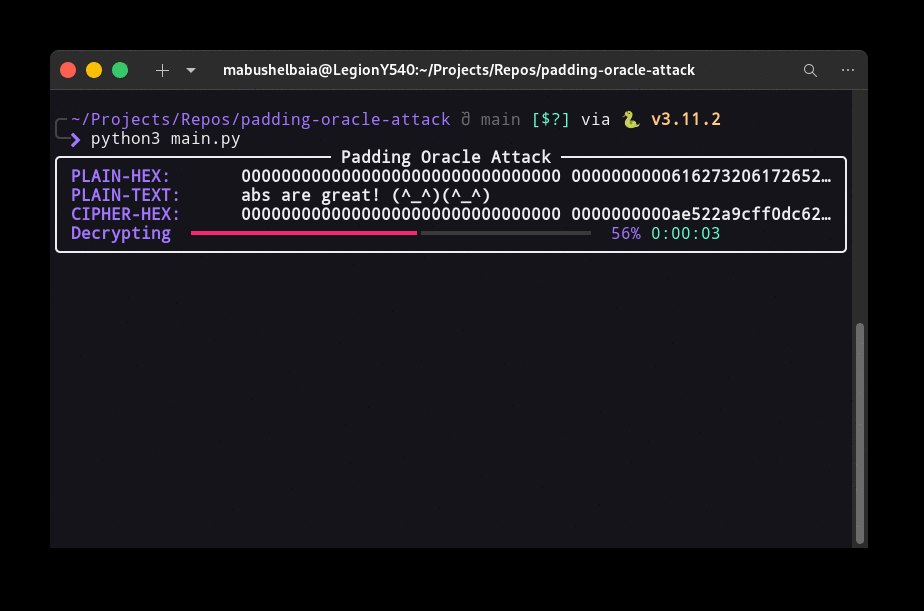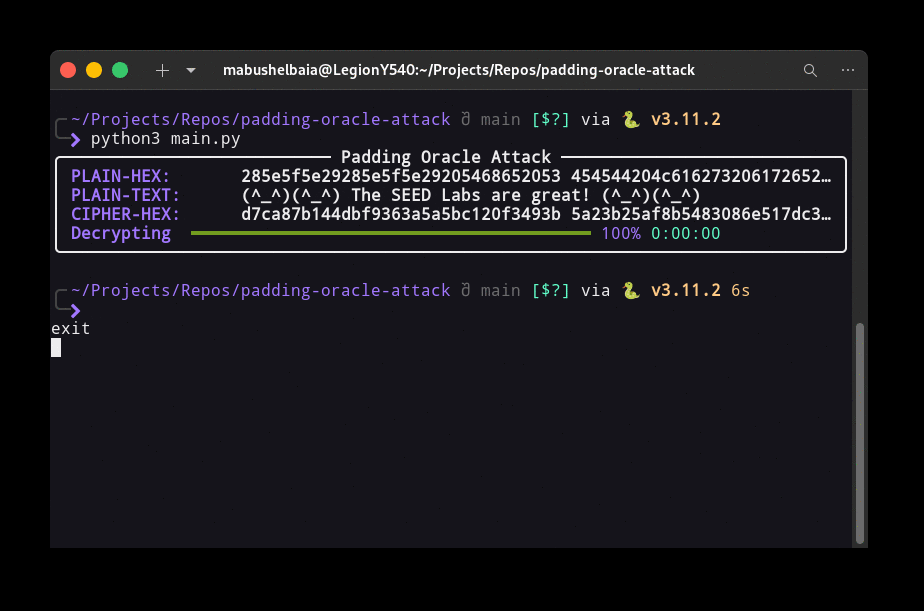
python3 main.py