Trivy (tri pronounced like trigger, vy pronounced like envy) is a comprehensive security scanner. It is reliable, fast, extremely easy to use, and it works wherever you need it.
Trivy has different scanners that look for different security issues, and different targets where it can find those issues.
Targets:
- Container Image
- Filesystem
- Git repository (remote)
- Kubernetes cluster or resource
Scanners:
- OS packages and software dependencies in use (SBOM)
- Known vulnerabilities (CVEs)
- IaC misconfigurations
- Sensitive information and secrets
Much more scanners and targets are coming up. Missing something? Let us know!
Read more in the Trivy Documentation
Get Trivy by your favorite installation method. See installation section in the documentation for details. For example:
apt-get install trivyyum install trivypacman -S trivybrew install aquasecurity/trivy/trivysudo port install trivydocker run aquasec/trivy- Download binary from https://github.com/aquasecurity/trivy/releases/latest/
trivy <target> [--security-checks <scanner1,scanner2>] TARGET_NAMEExamples:
$ trivy image python:3.4-alpineResult
trivy-image.mov
$ trivy fs --security-checks vuln,secret,config myproject/Result
trivy-fs.mov
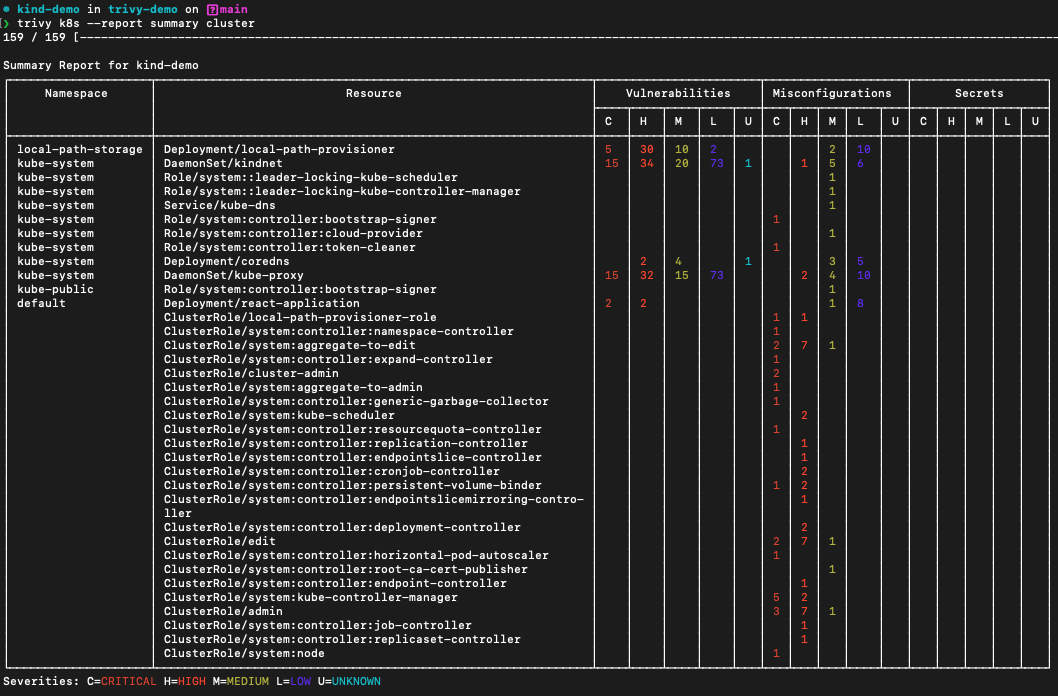
$ trivy k8s --report summary clusterNote that you can also receive a detailed scan, scan only a specific namespace, resource and more.
Find out more in the Trivy Documentation - Getting Started
- Comprehensive vulnerability detection
- OS packages (Alpine Linux, Red Hat Universal Base Image, Red Hat Enterprise Linux, CentOS, AlmaLinux, Rocky Linux, CBL-Mariner, Oracle Linux, Debian, Ubuntu, Amazon Linux, openSUSE Leap, SUSE Enterprise Linux, Photon OS and Distroless)
- Language-specific packages (Bundler, Composer, Pipenv, Poetry, npm, yarn, Cargo, NuGet, Maven, and Go)
- High accuracy, especially Alpine Linux and RHEL/CentOS
- Supply chain security (SBOM support)
- Support CycloneDX
- Support SPDX
- Misconfiguration detection (IaC scanning)
- Wide variety of security checks are provided out of the box
- Kubernetes, Docker, Terraform, and more
- User-defined policies using OPA Rego
- Secret detection
- A wide variety of built-in rules are provided out of the box
- User-defined patterns
- Efficient scanning of container images
- Simple
- Available in apt, yum, brew, dockerhub
- No pre-requisites such as a database, system libraries, or eny environmental requirements. The binary runs anywhere.
- The first scan will finish within 10 seconds (depending on your network). Consequent scans will finish instantaneously.
- Fits your workflow
- Great for CI such as GitHub Actions, Jenkins, GitLab CI, etc.
- Available as extension for IDEs such as vscode, jetbrains, vim
- Available as extension for Docker Desktop, Rancher Desktop
- See integrations section in the documentation.
Trivy is an Aqua Security open source project.
Learn about our open source work and portfolio here.
Contact us about any matter by opening a GitHub Discussion here