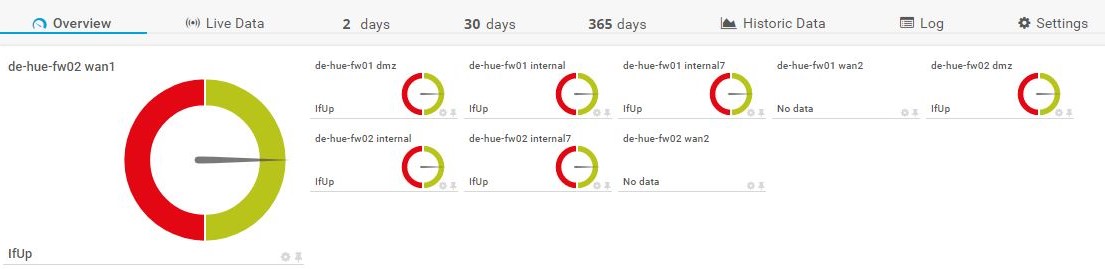
PRTG custom sensor to query nodes behind the virtual management IP
Slave Fortigate Cluster nodes send their management traffic through the primary unit if no separate management IP is defined. This makes queries for interfaces with normal SNMP queries impossible, as an OID query to an interface of the subordinate unit returns #N SNMP_EXCEPTION_NOSUCHINSTANCE.
Slave nodes can be queried by appending the serial number to the SNMP community and querying the cluster IP. See Fortinet Link for Monitoring HA Clusters
Sample Data Structure (Python Dictionaries):
{'unit1': {'clIndex': '1',
'hostname': 'de-xxx-fw02',
'int': {'dmz': {'ifIndex': '3', 'ifstatus': '1'},
'internal': {'ifIndex': '101', 'ifstatus': '1'},
'internal7': {'ifIndex': '110', 'ifstatus': '1'},
'modem': {'ifIndex': '6', 'ifstatus': '2'},
'npu0_vlink0': {'ifIndex': '4', 'ifstatus': '2'},
'npu0_vlink1': {'ifIndex': '5', 'ifstatus': '2'},
'ssl.root': {'ifIndex': '7', 'ifstatus': '1'},
'wan1': {'ifIndex': '1', 'ifstatus': '1'},
'wan2': {'ifIndex': '2', 'ifstatus': '2'}},
'serial': 'FGT60E4Q855555455',
'snmpc': 'public-FGT60E4Q855555455'},
'unit2': {'clIndex': '2',
'hostname': 'de-xxx-fw01',
'int': {'dmz': {'ifIndex': '3', 'ifstatus': '1'},
'internal': {'ifIndex': '101', 'ifstatus': '1'},
'internal7': {'ifIndex': '110', 'ifstatus': '1'},
'modem': {'ifIndex': '6', 'ifstatus': '2'},
'npu0_vlink0': {'ifIndex': '4', 'ifstatus': '2'},
'npu0_vlink1': {'ifIndex': '5', 'ifstatus': '2'},
'ssl.root': {'ifIndex': '7', 'ifstatus': '1'},
'wan1': {'ifIndex': '1', 'ifstatus': '1'},
'wan2': {'ifIndex': '2', 'ifstatus': '2'}},
'serial': 'FGT60E4Q56565656565',
'snmpc': 'public-FGT60E4Q56565656565'}}Sample Sensor Output:
6/26/2018 9:15:13 AM Exit Code: 0
6/26/2018 9:15:13 AM RawStream Size: 880
6/26/2018 9:15:13 AM OutputStream Size: 880
6/26/2018 9:15:13 AM Script Output (UTF8 Encoding): {"prtg": {"result": [{"ValueLookup": "custom.lookup.forti.interfaces",
"Value": 1, "Channel": "de-xxx-fw02 wan1", "Unit": "Custom"}, {"ValueLookup": "custom.lookup.forti.interfaces",
"Value": 1, "Channel": "de-xxx-fw02 internal", "Unit": "Custom"}, {"ValueLookup": "custom.lookup.forti.interfaces",
"Value": 1, "Channel": "de-xxx-fw02 dmz", "Unit": "Custom"}, {"ValueLookup": "custom.lookup.forti.interfaces",
"Value": 1, "Channel": "de-xxx-fw02 internal7", "Unit": "Custom"}, {"ValueLookup": "custom.lookup.forti.interfaces",
"Value": 1, "Channel": "de-xxx-fw01 internal", "Unit": "Custom"}, {"ValueLookup": "custom.lookup.forti.interfaces",
"Value": 1, "Channel": "de-xxx-fw01 dmz", "Unit": "Custom"}, {"ValueLookup": "custom.lookup.forti.interfaces",
"Value": 1, "Channel": "de-xxx-fw01 internal7", "Unit": "Custom"}], "text": "OK"}}[CR][LF]PySNMP class from here
The Python version installed with PRTG doesn't include pip or easy_install, so modules have to be manually installed including all dependencies
- Download pysnmp for the PRTG Python version (e.g. Python 3.4 for PRTG 18.4.46.1754) on pypi.org
- Extract
pysnmp-4.4.9-py3.4.eggusing 7-Zip or whatever works - Do the same for pysnmp dependencies (PyASN1, PySMI, pysnmpcrypto)
- Copy the module directories to the PRTG server:
<PRTG Install Directory>\Python34\Lib\site-packages\
- Copy
prtg-custom-forti-cl.pyto:C:\Program Files (x86)\PRTG Network Monitor\Custom Sensors\python\ - Copy lookup file to:
C:\Program Files (x86)\PRTG Network Monitor\lookups\custom\ - Load custom lookup file: Setup - System Administration - Administrative Tools, 'Load Lookups and File Lists' -> Go
- Add new
Python Script AdvancedSensor - Select script in dropdown menu and create sensor
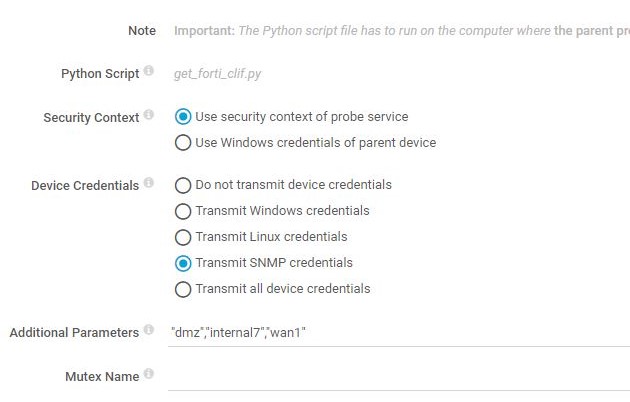
- Sensor settings
- Select 'Transmit SNMP credentials'
- Additional Parameters: Add interfaces to be monitored, e.g.:
"wan1","dmz","lan1"