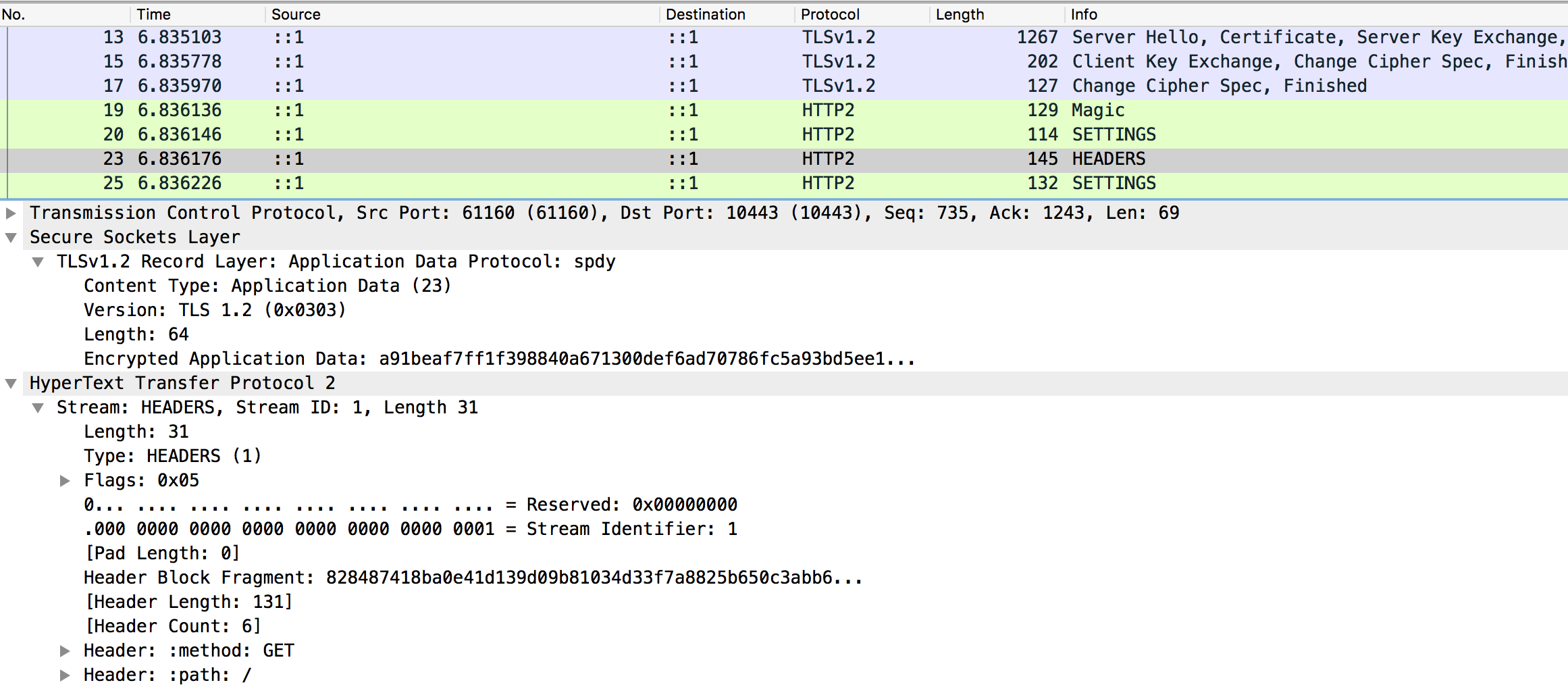
With the crypto/tls KeyLogWriter we can dump TLS secrets in a format Wireshark can read to decrypt TLS sessions. This allows debugging on-the-wire data in applications, including perfect forward secrecy and without access to server private key.
The key log must be enabled in application being debugged, normally requiring a change in the source code. Both client and server can be modified to log the secrets.
The required tls.Config#KeyLogWriter feature will be in Go 1.8 release (expected to be released around January 31st, 2017). Until then, installing the development version ("go tip") is required.
Requirements: Go 1.8 or development version ("tip").
$ go get -u github.com/joneskoo/http2-keylog/h2keylog-server
$ go get -u github.com/joneskoo/http2-keylog/h2keylog-client
See h2keylog-client source code.
$ h2keylog-client https://http2.golang.org
Leaking TLS keys to ssl-keylog.txt
----------------------
HTTP/2.0 200 OK
Content-Length: 1593
Content-Type: text/html; charset=utf-8
Date: Wed, 16 Nov 2016 23:05:06 GMT
[body not shown]You need to start a packet capture, e.g. with Wireshark, before you run h2keylog-client. h2keylog-client will write a text file that Wireshark can use to decrypt TLS traffic from the client.
ssl-keylog.txt:
# SSL/TLS secrets log file, generated by go
CLIENT_RANDOM b45c940d802822fd04c85a38b03b7227168457fbadb8be57a0f9cd05c4a0d2d3 6cbdd6f6bcdc5c3d7df7f0074b481eec649002ec64e2cfd91255e346aab617e72a1da2668176216e1d03f70505a335ebYou can now use the file as (Pre)-Master-Secret in SSL preferences in Wireshark to decode the traffic.
See h2keylog-server source code.
$ h2keylog-server
Listening at https://:10443/
Leaking TLS keys to ssl-keylog.txtMeanwhile in another terminal, and while Wireshark capture is active:
$ curl -k --http2 -6 'https://localhost:10443/'
This is an example server.
You can now use the file as (Pre)-Master-Secret in SSL preferences in Wireshark to decode the traffic.