-
-
Notifications
You must be signed in to change notification settings - Fork 5.3k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Add require signed commit for protected branch #9708
Add require signed commit for protected branch #9708
Conversation
|
It's annoying but you can't just use gogitRepository to get these as it appears that the quarantine incoming checks don't work correctly. |
|
also close #8584 |
Codecov Report
@@ Coverage Diff @@
## master #9708 +/- ##
==========================================
- Coverage 42.21% 42.21% -0.01%
==========================================
Files 602 602
Lines 78669 78669
==========================================
- Hits 33213 33209 -4
- Misses 41392 41395 +3
- Partials 4064 4065 +1
Continue to review full report at Codecov.
|
…ath/gitea into protect-branch-signed-commits-only
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Only a concern about very large commits. In a future PR we should make it so the signature is checked as the payload is being loaded (and discarded) in order to require less memory.
This comment has been minimized.
This comment has been minimized.
|
Nope it's that I failed to get the payload regeneration correct in the last few changes. |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
not working
EDIT: looks like 7a04a47 break something (worked before - with this commit it dont)
|
@zeripath remember to claim the bounty. |
| <i class="icon lock green"></i> | ||
| {{$.i18n.Tr "repo.signing.will_sign" .SigningKey}} | ||
| </div> | ||
| {{else}} |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I don't think this else case should be here. It should only be shown if RequireSigned and is already handled above.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Users should know if the commit will be signed or not.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Yes but the green text + icon if it will be signed would be enough? Many teams/companies don't use signing at all, so if you don't require signed commits it would be a bit annoying to have a yellow text "Commits are never signed" which many users will not even know what it means.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
GitHub allow admin to override also signing. If signed commits are not required, GitHub doesn't show anything about signing.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
So on the editor screen I was able to add a simple unlock icon to precede the Create Commit which could be mouseovered but there's not really a place on the merge screen to do that hence I felt that just adding it as another status box on merge is reasonable.
You need to know if your commits are going to be signed and why - on GH it's impossible to know why and if a commit is going to be signed.
In reality it's a status box that is only visible if you can merge.
| {{$notAllOk := or .IsBlockedByApprovals .IsBlockedByRejection (and .RequireSigned (not .WillSign)) (and .EnableStatusCheck (not .IsRequiredStatusCheckSuccess))}} | ||
| {{if and (or $.IsRepoAdmin (not $notAllOk)) (or (not .RequireSigned) .WillSign)}} |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Shall repo admin be able to bypass "require signed" or not? Currently the term in $notAllOk has no effect.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
It's a question I put on the original issue. I would guess we need an additional suboption to allow the repo admin to bypass this. The trouble is signing is different from pr approval or whitelisting.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
If you really want every commit to be signed I think it doesn't make sense for admin to override it?
So the condition to $notAllOk are more there for future, in case we allow admin to merge?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I haven't changed $notAllOK - those are the other checks that were there previously. As I've written it RequireSign overrides all other checks as it's not overridable.
Perhaps I should have changed the name of notAllOK to notAllOverridableStatusChecksOK but it felt a little over the top.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
But you have added (and .RequireSigned (not .WillSign)), is that not intentional?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
yeah that was future proofing.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
It also meant that the UI would keep sane.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
yeah exactly.
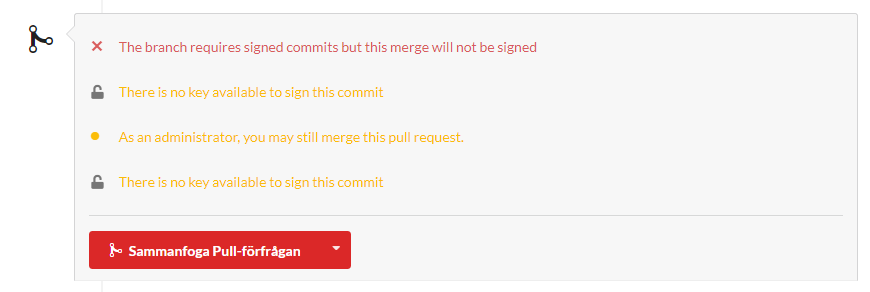
Fix #4249
Screenshots
New setting on protected branch
Merge Signed
Prevent Merge Unsigned
CRUD signed
Prevent CRUD unsigned