$$\ $$\ $$\ $$\
$$ | \__| $$ | \__| ,/| _.--''^``-...___.._.,;
$$$$$$$\ $$$$$$\ $$ | $$\ $$\ $$$$$$\ $$$$$$\ $$\ /, \'. _-' ,--,,,--'''
$$ __$$\ \____$$\ $$ | $$ |$$ |\_$$ _| \____$$\ $$ | { \ `_-'' ' /}
$$ | $$ | $$$$$$$ |$$$$$$ / $$ | $$ | $$$$$$$ |$$ | `;;' ; ; ;
$$ | $$ |$$ __$$ |$$ _$$< $$ | $$ |$$\ $$ __$$ |$$ | ._.--'' ._,,, _..' .;.'
$$ | $$ |\$$$$$$$ |$$ | \$$\ $$ | \$$$$ |\$$$$$$$ |$$ | (,_....----''' (,..--''
\__| \__| \_______|\__| \__|\__| \____/ \_______|\__|
Rust multithread ransomware that stream encrypts each file with chacha20poly1305 which, besides from stream (online) encrypting the files by chunks, it's also nonce-reuse misuse-resistant (as stated in this paper) and will verify the chunk integrity (authentication) with poly1350.
This project compiles 2 binaries:
-
ransomware: Program that will perform the encryption of the files. -
rescue: GUI Program that will decrypt all the encrypted files.
/nakitai
├── README.md
├── .editorconfig
├── Cargo.toml
├── Cargo.lock
├── ransom_message.template # Template of the message that will be left at the victim's desktop
├── ransom_message # Message that will be left at the victim's desktop
├── og_private.pem # Generated by `generate_rsa_keys.js`, will be used by `extract_decrypt_key_nky.js` internally.
├── og_public.pem # Generated by `generate_rsa_keys.js`, will be embedded into the ransomware binary.
├── /assets # Assets used in README.md
├── /scripts # Helpful scripts in js
│ ├── generate_rsa_keys.js # Generates RSA 2048 keypair: og_public.pem (this will be embedded) ad og_private.pem
│ └── extract_decrypt_key_nky.js # Decrypts the nky key and outputs the private key.
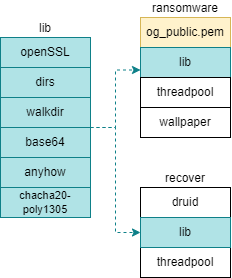
└── /src # Source code of main project
├── /assets # Assets used in the binaries (images)
├── /utils # Folder containing common funtionality
│ ├── crypto.rs # Common crypto operations such as encrypt and decrypt
│ ├── traverse.rs # Common directory and files operation, such as generating iterators to find files
│ └── mod.rs # Export functionality
├── lib.rs # Library file that will wrap up all utils functionality
└── /bin # Folder containing all binaries
├── ransomware.rs # Binary that will perform the decrypt_key.nky creation and files encryption
└── recover.rs # GUI binary that will help decrypt all the files if the correct private.pem key is provided
- RSA og keypair generated (by js script).
- Before the binaries are compiled, first
lib.rsgets compiled and included in each binary. Theog_public.pemkey will be embedded in theransomwarebin.
-
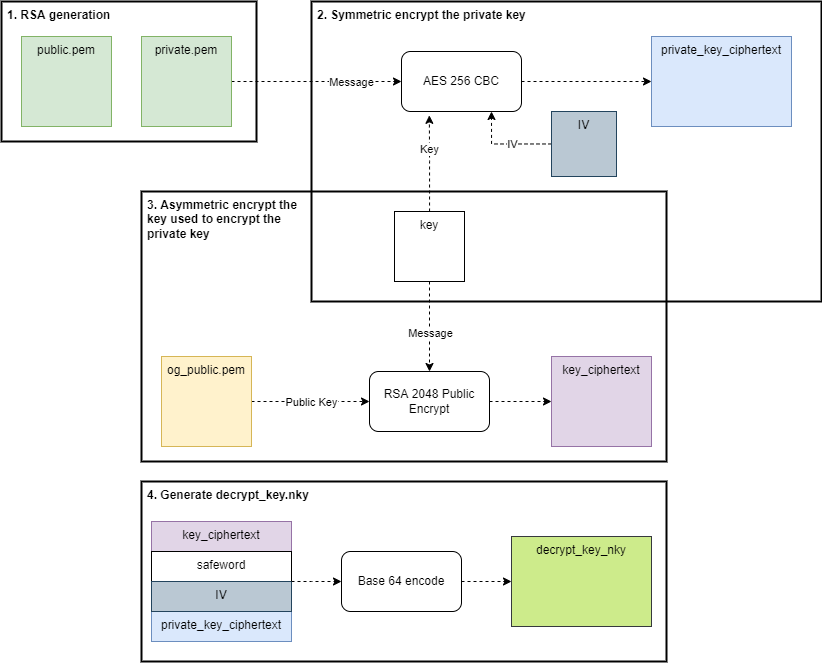
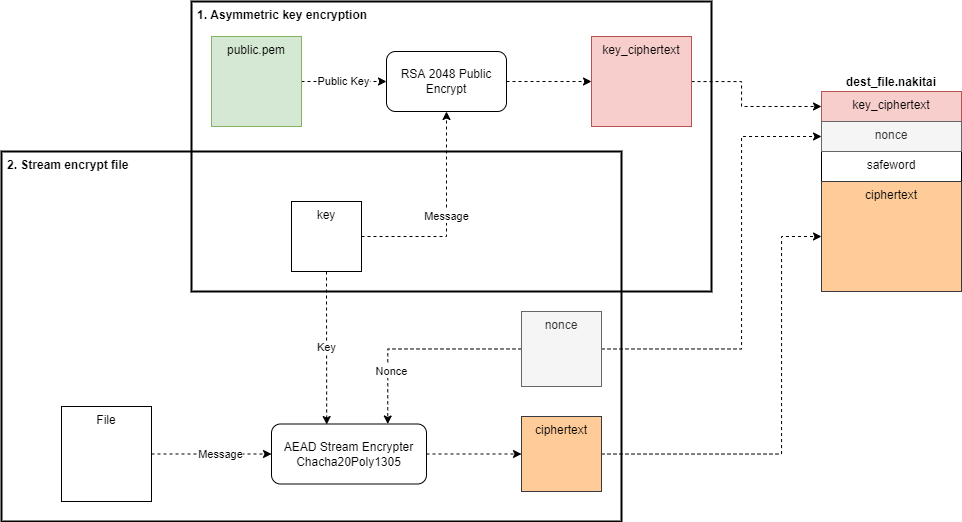
Once the ransomware gets executed, it will create the
decrypt_key.nkyin 4 steps:- Generate another RSA 2048 keypair:
private.pemandpublic.pem. - Symmetric encrypt the
private.pem. For that akeyand aivwill be generated securely using a PRNG function. Then it will take thekey,ivand themessage, apply an AES-256-CBC block cipher encryption and will product theprivate_key_ciphertext. - Asymmetric encrypt the previously created
key. Using the embeddedog_public.pemwill RSA encrypt thekeyand produce thekey_ciphertext. - Finally, we join all the encrypted parts with a fixed (hardcoded) safeword ("H4k" <=>
[0x48, 0x34, 0x6B]) and will encode all these bytes using base64 algorithm and generate thedecrypt_key.nky.
- Generate another RSA 2048 keypair:
-
After that, the ransomware will traverse all "interesting" files and will encrypt them in 2 steps:
- First it wil generate a file encryption
keyand anonceusing a PRNG function and then asymmetric encrypt thekeywith thepublic.pemgenerated previously. This will produce akey_ciphertext(this key ciphertext is from the key generated to encrypt a single file). Once thekey_ciphertextis generated, then it will be written in the destination file (dest_file.nakitai) along thenonceand the fixed safeword ("H4k"). - Finally, the "interesting" file will be opened and encrypted using the
keyandnoncegenerated previously. This will produce aciphertextin a stream way, that means that every chunk encrypted (that will have the same size as plaintext + some bytes for integrity check) will be appended to thedest_file.nakitai. Doing it this way (by chunks) won't load all the file in RAM at once, this is particular helpful when we have really large files and limited RAM.
- First it wil generate a file encryption
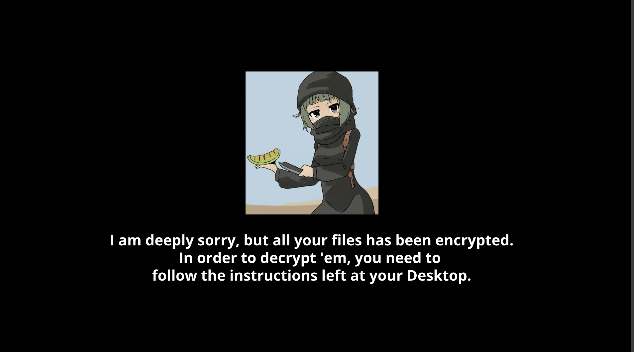
- At this point all the important files must be encrypted and the ransomware will create an
INSTRUCTIONS.txtfile in the victim's desktop with the message provided in theransom_messagefile. It will also change your background image to this one:
-
The BTC transaction verification is outside the scope of this project, but, you could develop a bot that checks for any payment made to your BTC wallet. Then extract the transaction's description and separate the victim's email from the encrypted nky key. The description format should look like this:
<[email protected]>fCny/pMgNAO7GxU8JYcardP/3PQoVSzZ0zPbDAxbevt....You optionally can use the
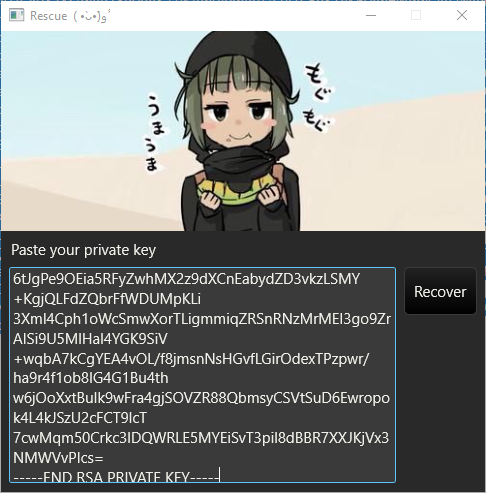
extract_decrypt_key_nky.jsfile to decrypt the nky key using theog_private.pempreviously generated. This process will generate theprivate.pem. -
Finally, the files' decryption will be performed when the
private.pemis provided.
- Before all, you will need to have OpenSSL installed.
In the case of Windows I suggest using the one provided by Shining Light Productions: https://slproweb.com/products/Win32OpenSSL.html
Make sure you download the Win32 OpenSSL v3.0.3 version (not the light), and
don't forget to add the folder C:\Program Files (x86)\OpenSSL-Win32\bin to the
PATH env variable and set OPENSSL_CONF variable to C:\Program Files (x86)\OpenSSL-Win32\bin\openssl.cfg.
-
After that, you will need to provide a
ransom_messagethat will be left at the victim's desktop. You can clone the one calledransom_message.templatebut do not forget to change the bitcoin wallet info ;) -
Then, you need to generate the
og_private.pemandog_public.pem, for that you will need to execute the generation script on the root project:
$ ./script/generate_rsa_keys.jsor
$ node script/generate_rsa_keys.js- In order to compile the code for development purposes just execute:
$ cargo buildThe above will generate the ransomware binary, but it won't be harmful since it won't delete the
files after encrypted and will stdout all the process.
If you want to build for "production" then execute:
$ cargo build --release --features harmful-
Which AES block cipher mode should I use ?
There are many of them: ECB, CBC, OFB, CFB, CTR, XTS. Since we are going to encrypt more than one block ECB is off the table. CBC, OFB and CFB are quite similar, they use the output of each block to feed the key of the next block (in ECB blocks are independent), so it can be any of this 3. Maybe we can consider CTR, since it's benefit is with parallelism and encryption is cpu intensive. (Source Stackoverflow)
-
How should I generate random bytes (for iv, nonce or key) ?
We need to guarantee the randomness of the generation of bytes, so using a weak seed such as the system clock (which is used by default) can be very predictable. That's why we need PRNG (Pseudo Random Number Generation).
The author does not hold any responsibility for the bad use of this tool,
remember that attacking targets without prior consent is illegal and punished by law.