
An Exploration of a Vulnerability That Shakes the Foundation of Digital Coins .
- VIDEO: https://youtu.be/mr0r0Yoe7QU
In the dynamic world of cryptocurrencies, security is paramount. The decentralized and transparent nature of blockchain technology has revolutionized how we transact and interact digitally. However, like any technological innovation, cryptocurrencies are not immune from vulnerabilities. Among the many threats that hang over the crypto landscape, the 51% attack stands out as a particularly insidious and potentially destructive exploit. In this article, we will delve into what a 51% attack entails, its consequences, and measures to mitigate its impact.
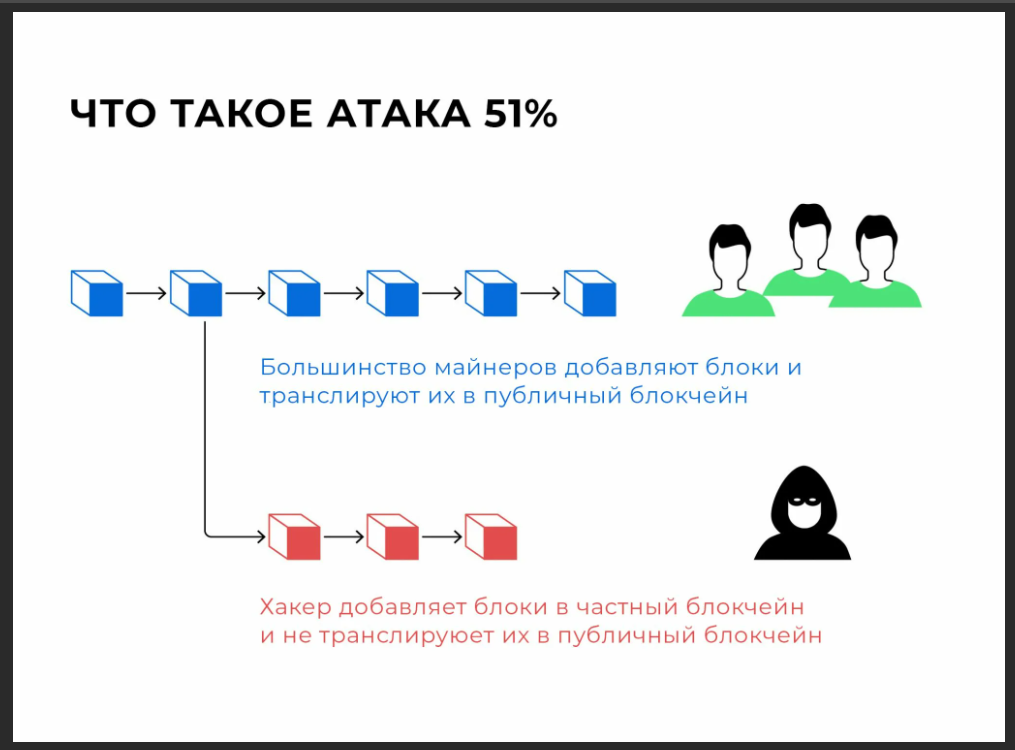
Attack Understanding 51%
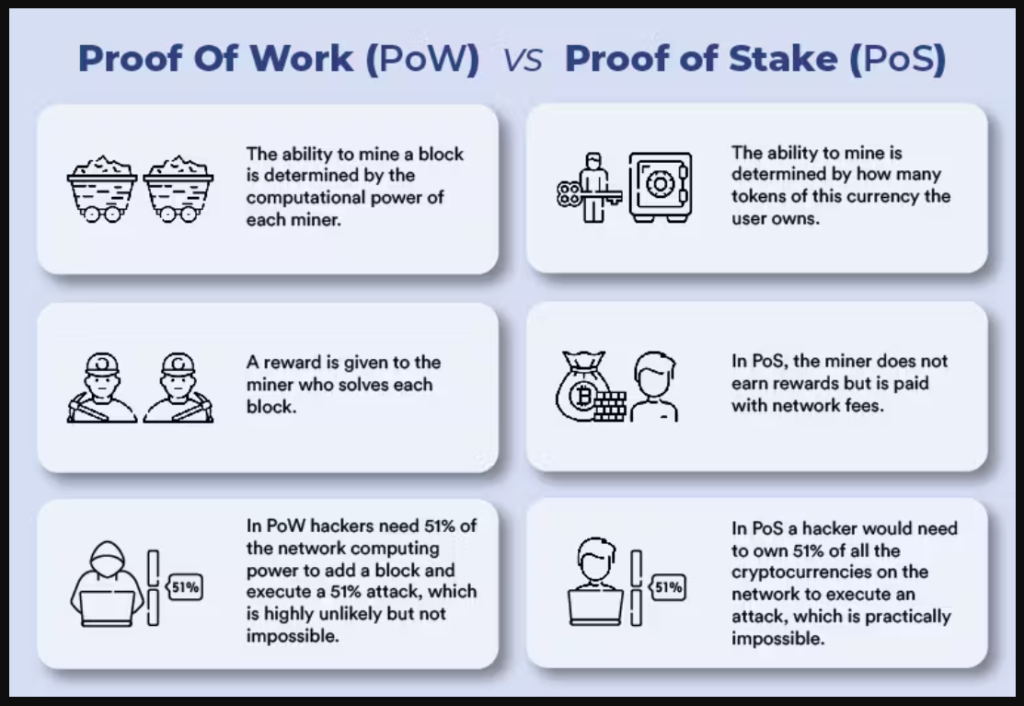
Most cryptocurrencies are based on a decentralized network of nodes that validate transactions through consensus mechanisms such as Proof of Work (PoW) or Proof of Stake (PoS). These mechanisms guarantee the legitimacy and security of transactions. A 51% attack, also known as a majority attack, occurs when an attacker or group captures more than half of the network's computing power (in the case of PoW) or staked tokens (in the case of PoS). This majority control gives them the ability to manipulate the blockchain to their advantage.
Aftermath Attacks 51%
The consequences of a successful 51% attack can be deep and far-reaching:
- Double spending. One of the most disturbing results of a 51% attack is the possibility of double spending. This means that an attacker can spend the same cryptocurrency multiple times, undermining the fundamental principle of scarcity that underlies most cryptocurrencies.
- Cancellation of transactions. Through majority control, an attacker can reverse transactions, essentially rewriting the history of the blockchain. This can lead to chaos and loss of trust in the affected cryptocurrency .
- Network Paralysis: An attacker with majority control can stop transactions and even prevent new ones from being added to the blockchain. This failure could have serious economic consequences and undermine investor confidence.
- Undermining security and trust. A successful 51% attack damages the perception of security and trust in cryptocurrencies. Investors and users may leave the network, leading to a significant drop in its value and prevalence.
Real Examples
Several cryptocurrencies have been the victims of 51% attacks, highlighting the severity of this threat:
- Bitcoin Gold (BTG): In May 2018, Bitcoin Gold suffered a 51% attack that resulted in the theft of millions of dollars worth of BTG. The attack demonstrated the vulnerability of small cryptocurrencies with less hashing power.
- Ethereum Classic (ETC): Notably, Ethereum Classic suffered several 51% attacks in 2020. The attackers took advantage of the network’s lower hash rate and reorganized the blockchain, resulting in the theft of significant amounts of ETC.
- Verge (XVG): Verge was the victim of a 51% attack in April 2018. Attackers took advantage of several vulnerabilities to mine large amounts of XVG and disrupt the network.
Mitigation and prevention
Although the threat of a 51% attack remains, the crypto community has taken steps to mitigate its effects:
- Increasing hashing power. Cryptocurrencies can increase their security by increasing computing power, making it prohibitively expensive for attackers to acquire a controlling interest.
- Advanced consensus mechanisms. Some emerging cryptocurrencies use innovative consensus mechanisms such as delegated proof of stake (DPoS) and proof of authority (PoA) to reduce the likelihood of 51% attacks.
- Attack monitoring. Constant monitoring of network activity can detect unusual behavior that indicates an upcoming 51% attack. This allows you to quickly respond and take preventive measures.
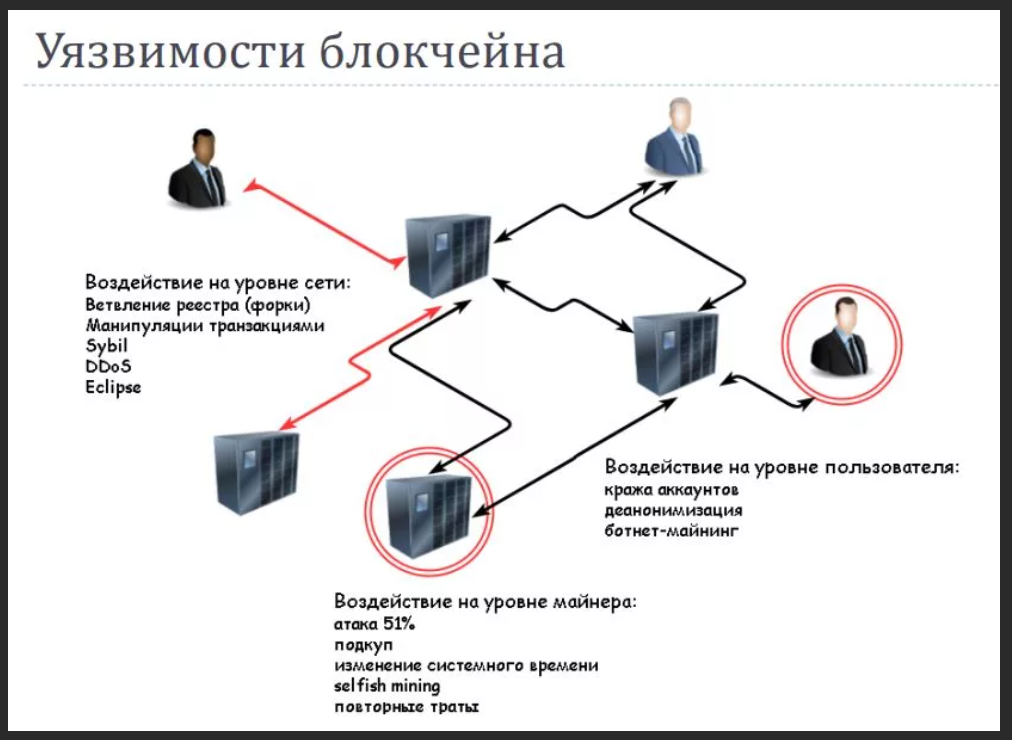
A blockchain vulnerability refers to anything that can be exploited by a hacker to exploit the protocol.
One of the most common is the risk of centralization. Centralization often creates a single point of failure that hackers can use to gain access to the entire network.
Logic problem vulnerabilities require code restructuring and may be related to bugs. Reentry attacks are hacks that exploit logic problems. An attacker can trick a smart contract into sending funds that have already been sent.
Gas optimization is important as projects grow. The gas required to validate transactions can increase so much that new blocks can no longer be verified.
The gas optimization result of a CertiK security audit identifies areas where the amount of gas can be reduced without affecting code operation.
Vulnerabilities arise at the external endpoints of blockchain intersections, known as oracles. Information transmitted by oracles and their smart contracts can be used by hackers.
Cross-chain bridges have emerged as a vital infrastructure that allows users to move between blockchains. Vulnerabilities can arise due to differences in rules and organizations between chains.
Conclusion
The 51% attack remains a major problem in the crypto space, highlighting the need for strong security measures and constant vigilance. The decentralized nature of blockchain technology has brought enormous benefits, but it also requires constant adaptation to emerging threats. As the crypto community continues to innovate and collaborate, the goal is to secure networks from potential attackers, ensuring the continued growth and adoption of cryptocurrencies on a global scale.
Telegram: https://t.me/cryptodeeptech
Video: https://www.youtube.com/@cryptodeeptech
Source: https://cryptodeep.ru/blockchain-attack-vectors
 Change51% Attack: Cryptocurrency Vulnerability Revealed
Change51% Attack: Cryptocurrency Vulnerability Revealed
.png)