Vault 1.1.0 introduced OIDC Redirect Flow Support, allowing authentication using browser. In this repository we describe the steps to integrate this feature to authenticate with Vault using a Gmail address.
- Vault server with a "demo" ACL policy
- A domain name for Vault
- Google account
You can use any registrar, no specific requirements. If you decide to use AWS Route53:
- Log in to AWS, go to Route53
- Create a Hosted Zone if none exist
- Click on existing Hosted Zone
- Click Create Record Set
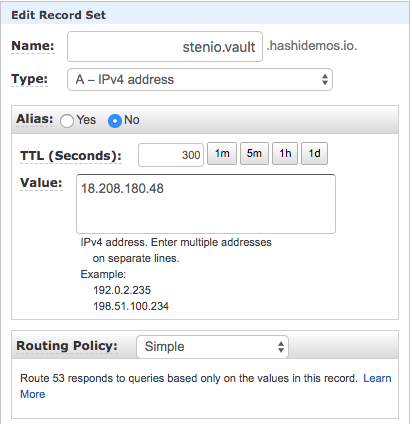
- Enter a name and update the IP value, as shown here:
- Throughout this repo, assume that "YOUR_VAULT_ADDR" is this address, example:
YOUR_VAULT_ADDR=http:https://stenio.vault.hashidemos.io:8200
Go to https://console.developers.google.com/apis/credentials/, log in if needed
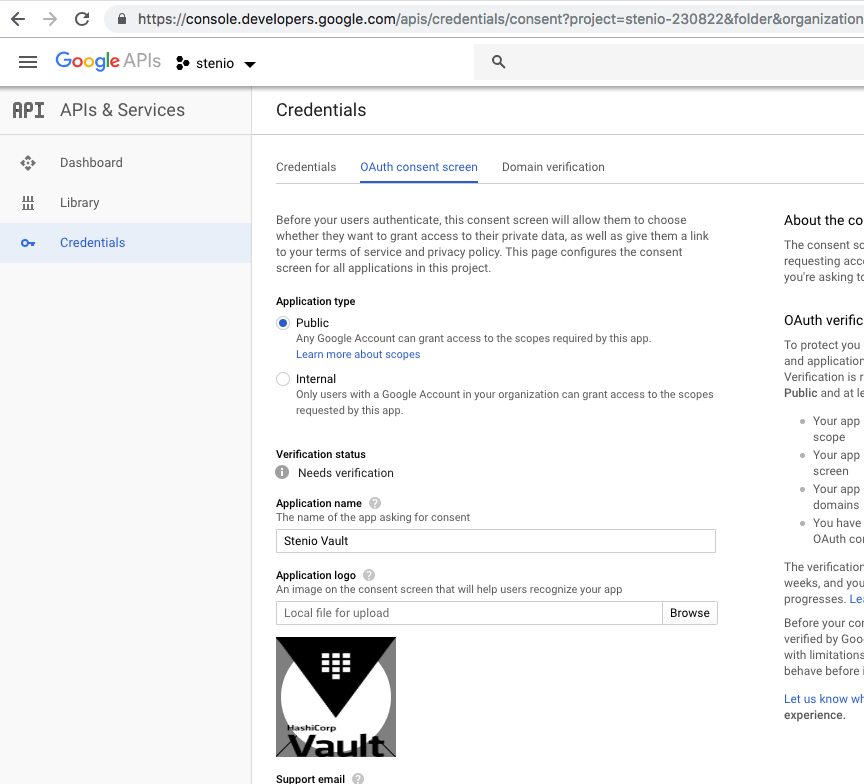
- Click on "Oauth Consent Screen tab":
- Enter Name, upload picture to show on consent screen (optional)
- Scopes - email, profile, openid
- On "authorized domains", enter the domain of your vault server. Example myvault.com
- Enter Application homepage and privacy link (optional)
- Press "Save"
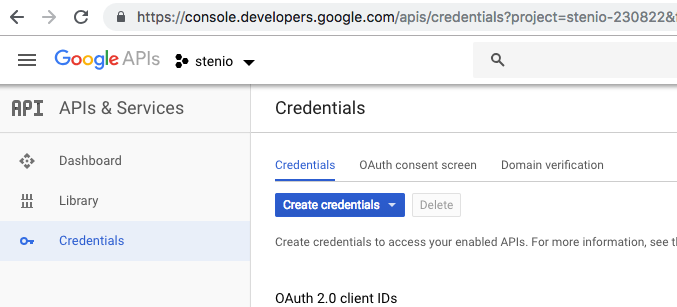
- Now click on the "Credentials" tab:
- Click "Create credentials > OAuth ClientID"
- Select "Web application", give it a name
- On "Authorized redirect URLs", enter "http:https://YOUR_VAULT_ADDR/ui/vault/auth/oidc/oidc/callback"
- Press Save
- In the next step you will use the Client ID and the Client Secret when configuring Vault
- Enable oidc auth and configure it with the Google client information:
vault auth enable oidc
vault write auth/oidc/config \
oidc_discovery_url="https://accounts.google.com" \
oidc_client_id="YOUR_GOOGLE_API_CLIENT_ID", \
oidc_client_secret="YOUR_GOOGLE_API_CLIENT_SECRET", \
default_role="gmail"
- Create a role to use for authentication. You can be as restrictive as desired by using the different "bound" fields. These allow you to specify values that need to be present from Google in order to allow authentication. Here documentation on claims and values sent by Google, here information on the bound fields.
vault write auth/oidc/role/gmail \
user_claim="sub" \
bound_audiences=[YOUR_GOOGLE_API_CLIENT_ID] \
allowed_redirect_uris=[http:https://YOUR_VAULT_ADDR/ui/vault/auth/oidc/oidc/callback] \
policies=demo \
ttl=1h
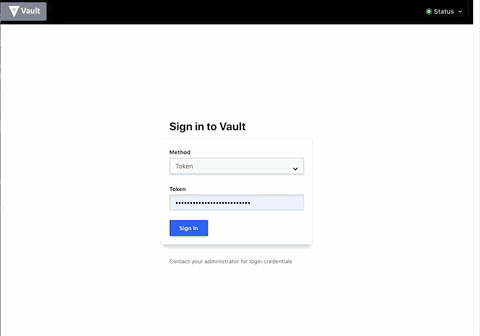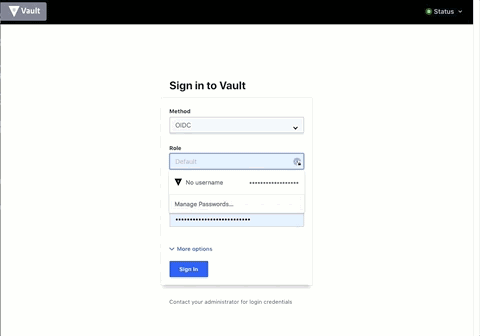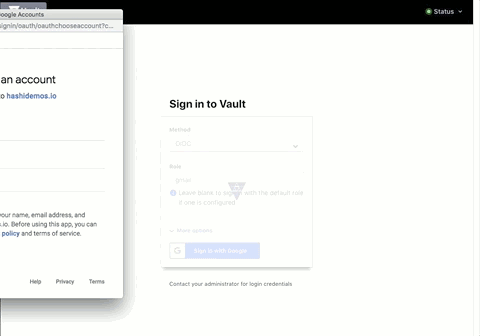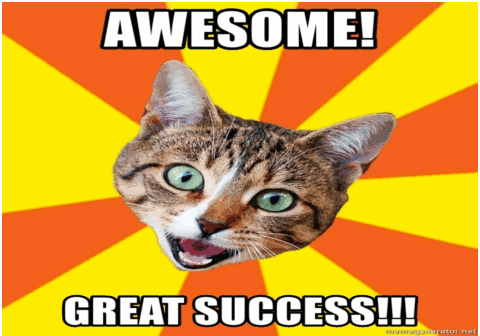
- Go to Vault UI
- Select "OIDC auth"
- Enter the role you want to log in to Vault with. In this example we only have one role, but multiple can be created and associated with different claims and bounds as needed.
- Log in!