Automated malware collection and classification with signature based scan.
Main script is Allonsy.py, it collects the malwares from specified sources below and scans them with the existing rules, checks ssdeep values with the existing malwares in the database, when 90% or upper match is found, it is written to database.
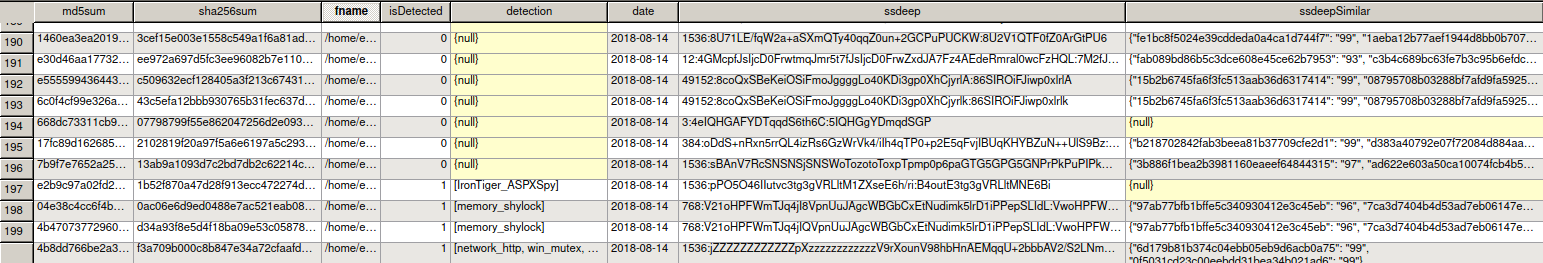
It saves the collected malwares under $PWD\Malwares path and creates Sqlite3 database for the malwares as in the image below.
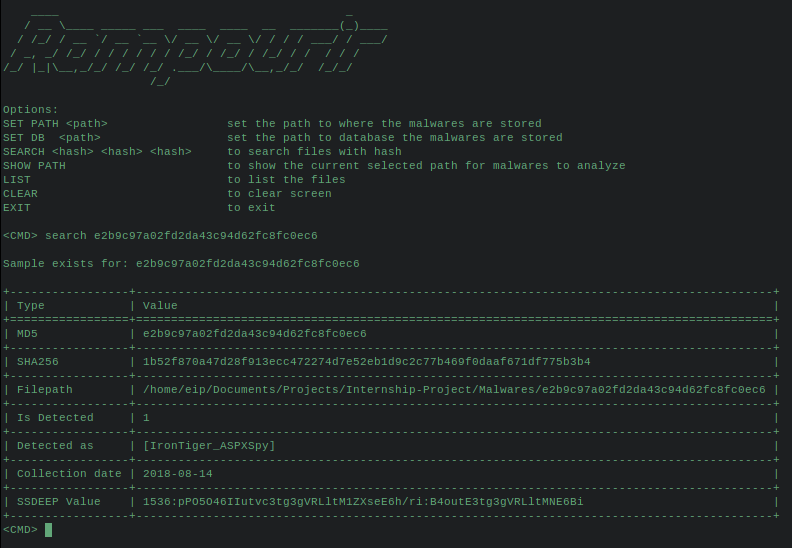
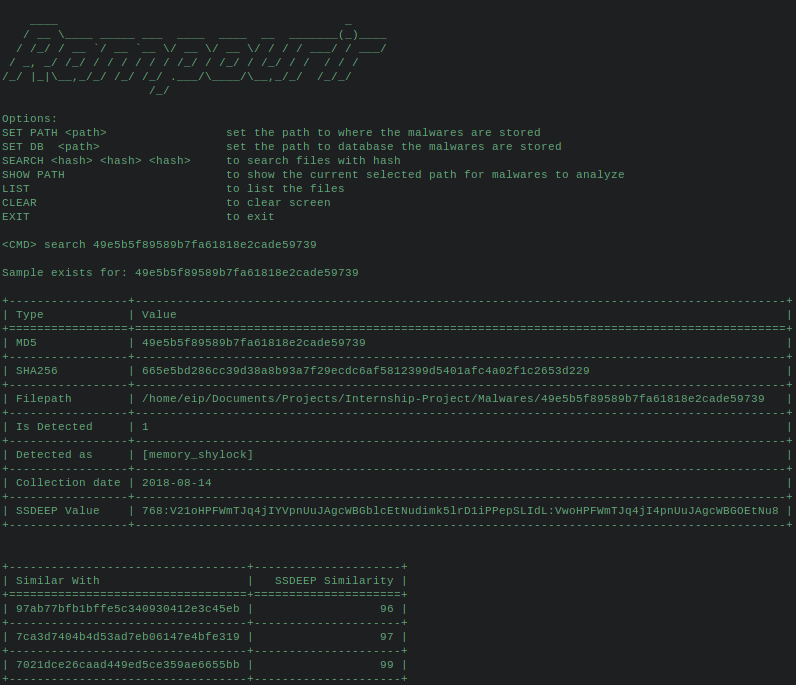
You can list samples collected. You can search for a sample, with md5 or sha256.
It also shows the similar samples if there is any.
- Malshare => Added
- Malc0de => Added
- VX-Vault => Added
- Tracker-h3x => Added
- Malakel => It is not being updated (Cumulative downloader will be written for contribution to database) => Added
- Cybercrime-Tracker => canceled, not up to date
- Yara-Rules => Added
- Yara rules will be collected from source or added manually based on personal analysis of samples.
- When a new rule is gathered, old undetected samples will be checked again with new rules.
- New malwares will be checked and hashes will be written to database at certain frequency(probably daily)
- If sample doesn't exist in database it will be pulled.
- Pulled samples will be scanned with yara rules and detections will be saved database.