IoT Safe Middleware implements a set of API to support interactions with GSMA IoT Safe Applet on a SIM.
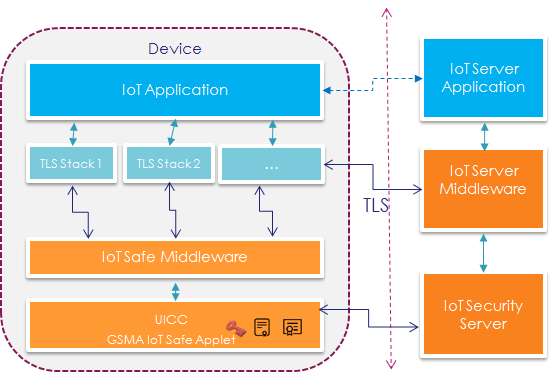 As depicted in this figure, IoT Safe Middleware is a thin layer to enable user application / other stacks to format and send APDUs to GSMA IoT Safe Applet running on a SIM card.
The IoT Safe middleware would be compiled and bundled with IoT Applications using other protocol stacks such as TLS.
The IoT Applications bundling IoT Safe Middleware would typically run on IoT Devices with cellular connectivity.
As depicted in this figure, IoT Safe Middleware is a thin layer to enable user application / other stacks to format and send APDUs to GSMA IoT Safe Applet running on a SIM card.
The IoT Safe middleware would be compiled and bundled with IoT Applications using other protocol stacks such as TLS.
The IoT Applications bundling IoT Safe Middleware would typically run on IoT Devices with cellular connectivity.
This project consists of IoT Safe Middleware library, unit tests and a sample application.
-
CMake 3.14.5 or higher
-
Build essentials C++ compiler, linker and etc.
-
sudo apt-get install libcpputest-dev
Additionally, install the CMake for Raspberry
sudo apt update
sudo apt install snapd
sudo reboot
sudo snap install --candidate cmake --classic
sudo apt-get install libssl-dev- 3G/4G/LTE Modem e.g Cinterion Connect Shield / Concept Board
- IoT Safe SIM
- Raspberry Pi
The MVP version of the applet uses the following AID:
static uint8_t AID[] = { 0xA0, 0x00, 0x00, 0x00, 0x30, 0x53, 0xF1, 0x24, 0x01, 0x77, 0x01, 0x01, 0x49, 0x53, 0x41 };
If CppUTest is already installed and in the system path, the IoT Safe library and simple demo can be built by running make from the root folder.
The make will build:
-
iotsafelib.a
-
simpledemo
-
jwtdemo
-
CppUTestIoTSafe
simpledemo or jwtdemo or CppUTestIotSafe can be run from the command line
cmake --version
Version must be above 3.14.5
Alternatively, CMake can be used to automatically pull CppUTest dependency and build the project.
mkdir build
cd build
cmake ..
make
make testAn example app to demonstrate how the IoT Safe Applet can be used to sign JWT token. This example uses ECDSA keypair on the SIM/UICC to sign JWT. IoT Safe Applet on the SIM/UICC is provisioned with key containers containing ECDSA private key (container ID = 01) and public key (Container ID = 02)
The following sample header and payload are used in this example
{"alg":"ES256","typ":"JWT"}
{"id": 42,"claimType": "claimType","claimUrl","claimUrl" }
eyJhbGciOiJFUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6IDQyLCJjbGFpbVR5cGUiOiAiY2xhaW1UeXBlIiwiY2xhaW1VcmwiOiJjbGFpbVVybCIgfQ.wMG0sp7BfdGDjvW4nJPE6swwEE0b7UvPmMWiYwa71zuAMuDpRbQasgcz3lls0V0jLh7XjmfnFPahSRs0Eh3OUQ
For easy verification of this token , the example app is also retrieving Public Key from UICC and print it in on the console
-----BEGIN PUBLIC KEY-----
MFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcDQgAElUtniK6dsGR6i/s/cAIxxISSjR7L
+lcy4O4FOlRWilW+O1R//HLobRJzzK8qEVPhp32r+GgZn8O7OgWoio4c/Q==
-----END PUBLIC KEY-----
The generated JWT can be independantly verified by tools such as online portal https://jwt.io/