Job controller to launch kubernetes jobs based on git event
make
-
Download helm chart releases from releases pages
-
Install the helm chart.
kubectl create namespace gitjob
helm install gitjob --namespace gitjob ./path/to/your/helm/tarballgitjob allows you to launch kubernetes jobs based on git event. By default it uses polling to receive git event, but also can be configured to use webhook.
To run kubectl apply on a github repo:
- First, create a serviceAccount and rbac roles so that you have sufficient privileges to create resources.
apiVersion: v1
kind: ServiceAccount
metadata:
name: kubectl-apply
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: kubectl-apply
rules:
- apiGroups:
- "apps"
resources:
- 'deployments'
verbs:
- '*'
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: kubectl-apply
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: kubectl-apply
subjects:
- kind: ServiceAccount
name: kubectl-apply- Create a gitjob CRD that apply manifest when git repo changes.(Using polling)
apiVersion: gitjob.cattle.io/v1
kind: GitJob
metadata:
name: example
namespace: default
spec:
syncInterval: 15 // in seconds, default to 15
git:
branch: master
repo: https://github.com/StrongMonkey/gitjob-example
provider: polling
jobSpec:
template:
spec:
serviceAccountName: kubectl-apply
restartPolicy: "Never"
containers:
- image: "bitnami/kubectl:latest"
name: kubectl-apply
command:
- kubectl
args:
- apply
- -f
- deployment.yaml
workingDir: /workspace/sourceNote: Git repository will be cloned under /workspace/source by default.
Two environmental variables: COMMIT, EVENT_TYPE will be added into your job spec.
- A kubernetes job will be created with specified job template.
NAME COMPLETIONS DURATION AGE
example-3af7c 1/1 5s 24hFor private repo that needs credential:
- Create a kubernetes secret that contains ssh-private-key.
kubectl create secret generic ssh-key-secret --from-file=ssh-privatekey=/path/to/private-key- Apply a gitjob CRD with secret specified.
apiVersion: gitjob.cattle.io/v1
kind: GitJob
metadata:
name: example-private
spec:
git:
branch: master
repo: [email protected]:StrongMonkey/priv-repo.git
provider: polling
gitSecretName: ssh-key-secret
gitHostName: github.com
jobSpec:
template:
spec:
serviceAccountName: kubectl-apply
restartPolicy: "Never"
containers:
- image: "bitnami/kubectl:latest"
name: kubectl-apply
command:
- kubectl
args:
- apply
- -f
- deployment.yaml
workingDir: /workspace/sourcegitjob can be configured to use webhook to receive git event. This currently supports Github. More providers will be added later.
- Create a gitjob that is configured with webhook.
apiVersion: gitjob.cattle.io/v1
kind: GitJob
metadata:
name: example-webhook
namespace: default
spec:
git:
branch: master
repo: https://github.com/StrongMonkey/gitjob-example
provider: github
github:
token: randomtoken
jobSpec:
template:
spec:
serviceAccountName: kubectl-apply
restartPolicy: "Never"
containers:
- image: "bitnami/kubectl:latest"
name: kubectl-apply
command:
- kubectl
args:
- apply
- -f
- deployment.yaml
workingDir: /workspace/sourceNote: you can configure a secret token so that webhook server will validate the request and filter requests that are only coming from Github.
- Create an ingress that allows traffic.
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: webhook-ingress
namespace: gitjob
spec:
rules:
- host: your.domain.com
http:
paths:
- path: /hooks
pathType: Prefix
backend:
serviceName: gitjob
servicePort: 80Note: To configure a HTTPS receiver, make sure you have proper TLS configuration on your ingress
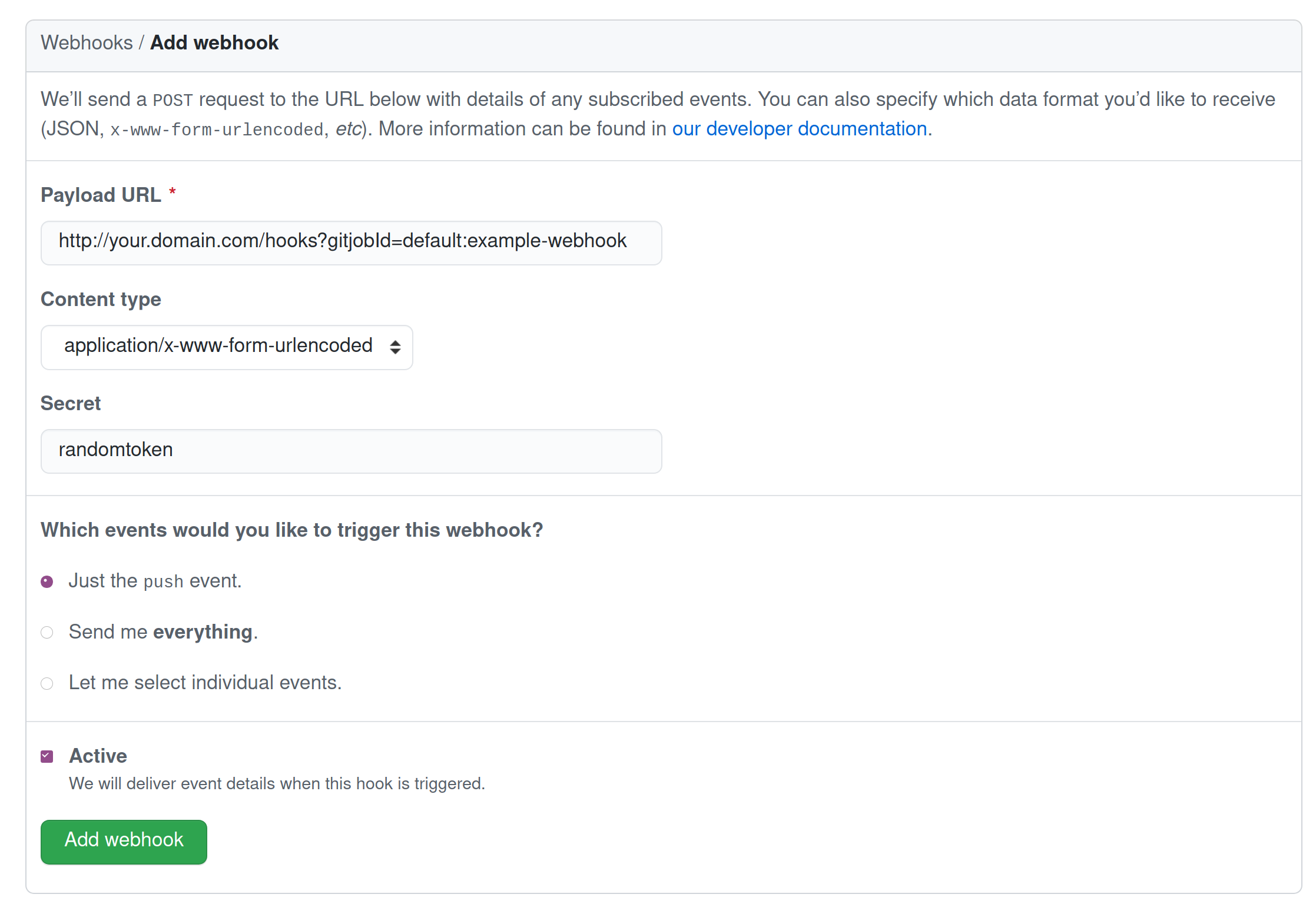
- Create a Github webhook that sends payload to
https://your.domain.com/hooks?gitjobId=default:example-webhook.
You can choose which event to send when creating the webhook. Gitjob currently supports push and pull-request event.
GitJob will create webhook for you if you have proper setting created
- Create a configmap in kube-system namespace
apiVersion: v1
kind: ConfigMap
metadata:
name: github-setting
namespace: kube-system
data:
WebhookURL: https://webhook.example.com #This will be your webhook callback URL
SecretName: githubtoken- Create a secret that contains your github access token
kubectl create secret generic -n kube-system githubtoken --from-literal=token=$ACCESS_TOKEN- Create a gitjob CR and set provider to github
apiVersion: gitjob.cattle.io/v1
kind: GitJob
metadata:
name: example-webhook
namespace: default
spec:
git:
branch: master
repo: https://github.com/StrongMonkey/gitjob-example
provider: github
jobSpec:
...GitJob controller will automatically create webhook with callback URL https://webhook.example.com?gitjobId=default:example-webhook based on the global setting. At this time it doesn't delete webhook if CR is deleted from cluster, so make sure to clean up webhook if not used.
- Setup ingress and TLS to allow traffic to go into GitJob controller so that it can start receiving events.
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: webhook-ingress
namespace: gitjob
spec:
rules:
- host: webhook.example.com
http:
paths:
- pathType: Prefix
backend:
serviceName: gitjob
servicePort: 80
tls:
- hosts:
- webhook.example.com
secretName: testsecret-tlsAPI types are defined in here
Part of this project is built upon Tekton.
Copyright (c) 2020 Rancher Labs, Inc.
Licensed under the Apache License, Version 2.0 (the "License"); you may not use this file except in compliance with the License. You may obtain a copy of the License at
https://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License.