Adhrit is an open source Android APK reversing and analysis suite. The tool is an effort to find an efficient solution to all the needs of mobile security testing and automation. Adhrit has been built with a focus on flexibility and mudularization. Adhrit currently uses the Ghera benchmarks to identify vulnerability patterns in Android applications. The project is subject to continuous updations and will incorporate the latest available methodologies and tools. Adhrit has been presented at conferences like OWASP Seasides, ThreatCon and Cysinfo. Feature requests and bug reports are always welcome!
-
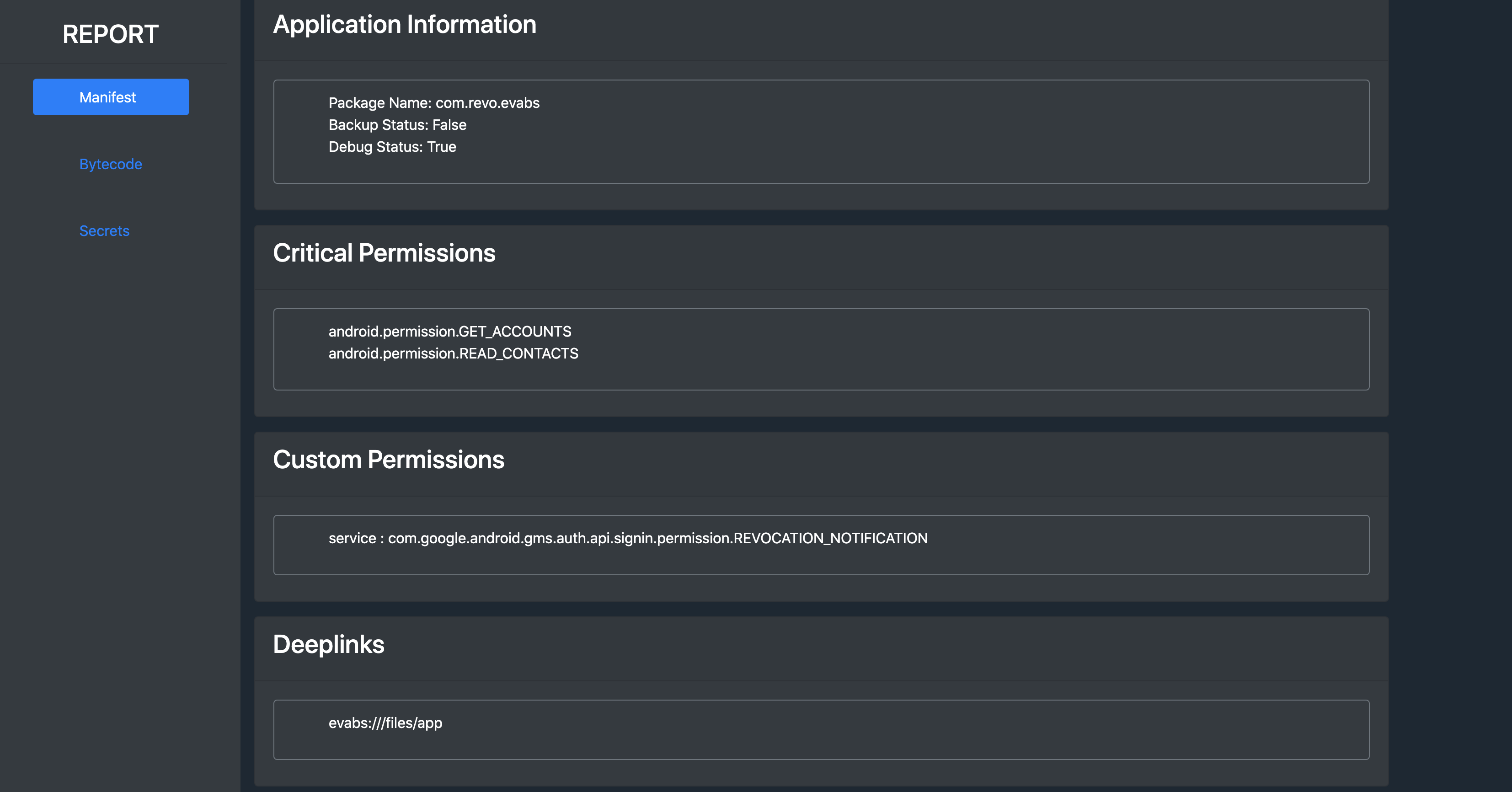
- Package name, debug and backup status
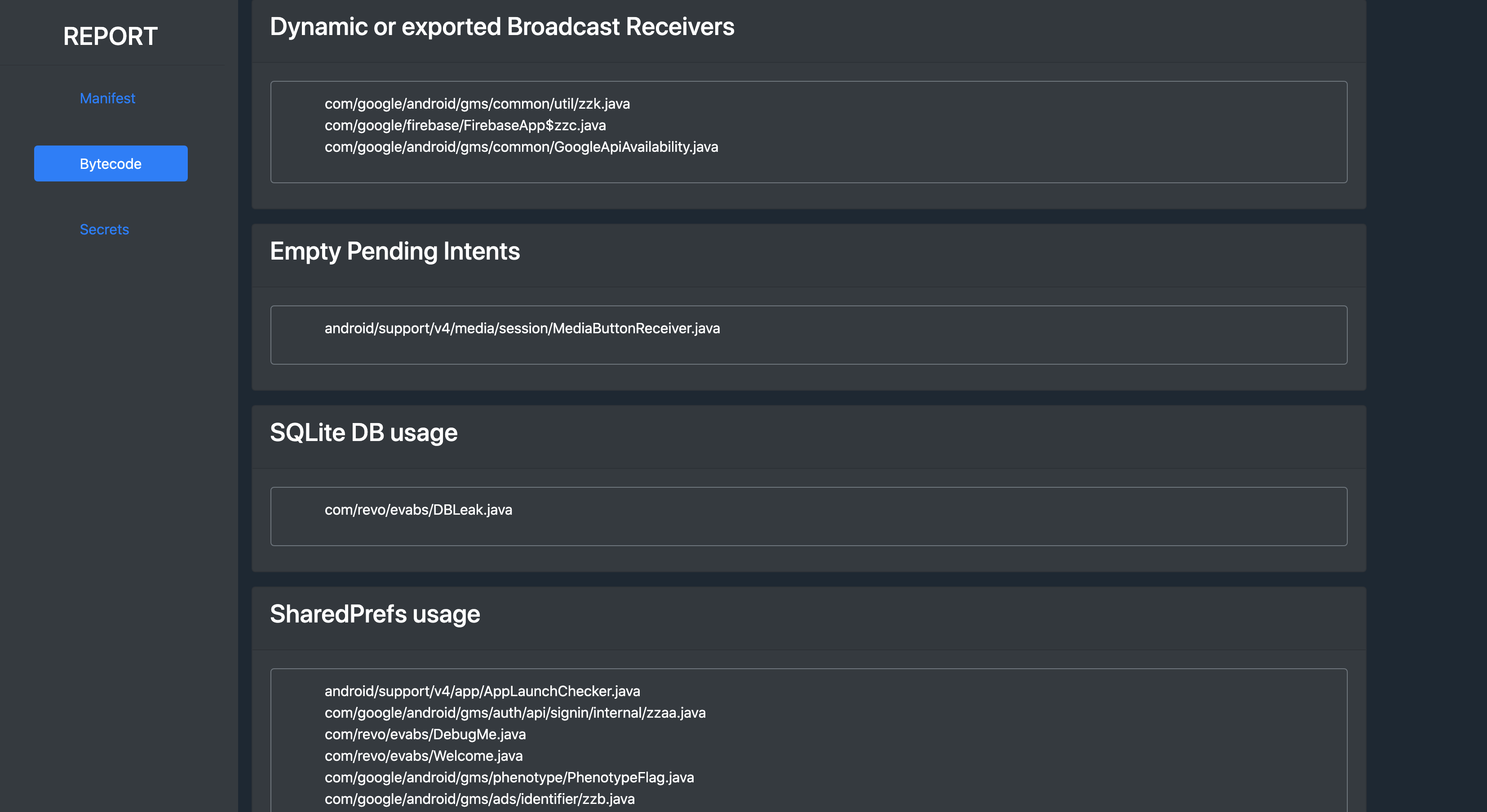
- Exported components (activities, services, providers and receivers)
- Deeplinks
- Implicit intent filters
- Critical permissions
-
-
Usage Analysis
- SQLite DBs
- SharedPreferences
-
Vulnerability Analysis
- ICC
- Web Issues
- Storage Issues
- Networking
- Crypto Issues
-
-
- URLs
- API tokens
- Strings from native libraries
- Linux or MAC
- Python3
- Java JDK
- Dowload the zip or clone the package and extract the tool (
git clone https://github.com/abhi-r3v0/Adhrit.git). - Run
python3 run.py
The script automatically identifies if you're running Adhrit for the first time and will install all the dependencies & libraries required by the tool.
docker-compose up
Then visit https://127.0.0.1:4200
python3 run.py
This will automatically launch the Web interface where the APK can be uploaded and the report will be generated.
If the UI didn't launch by itself, navigate to https://localhost:4200/
- Abhishek J M ([email protected], @HawkSpawn)
- Rahul Sani ([email protected], @rahulsani99)
- P S Narayanan ([email protected], @0xP5N_)
- Akhil Mahendra ([email protected], @Akhil_Mahendra)
- Sooraj Soman ([email protected] Sooraj)
- Heeraj Nair ([email protected], @heerajnair)
- Vaisakh ([email protected], @vaisakhjnr) (new)
- Loyd Jayme ([email protected], @loydjayme25)