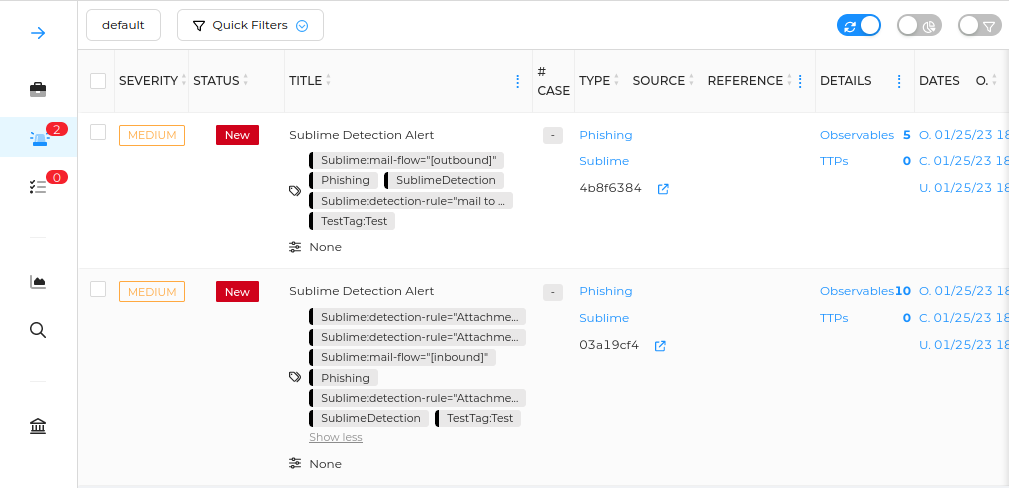
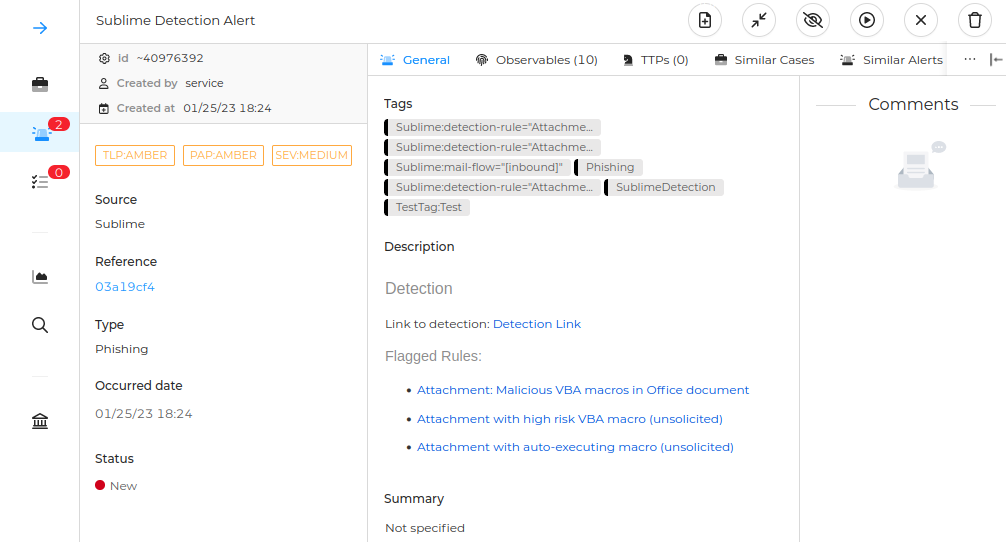
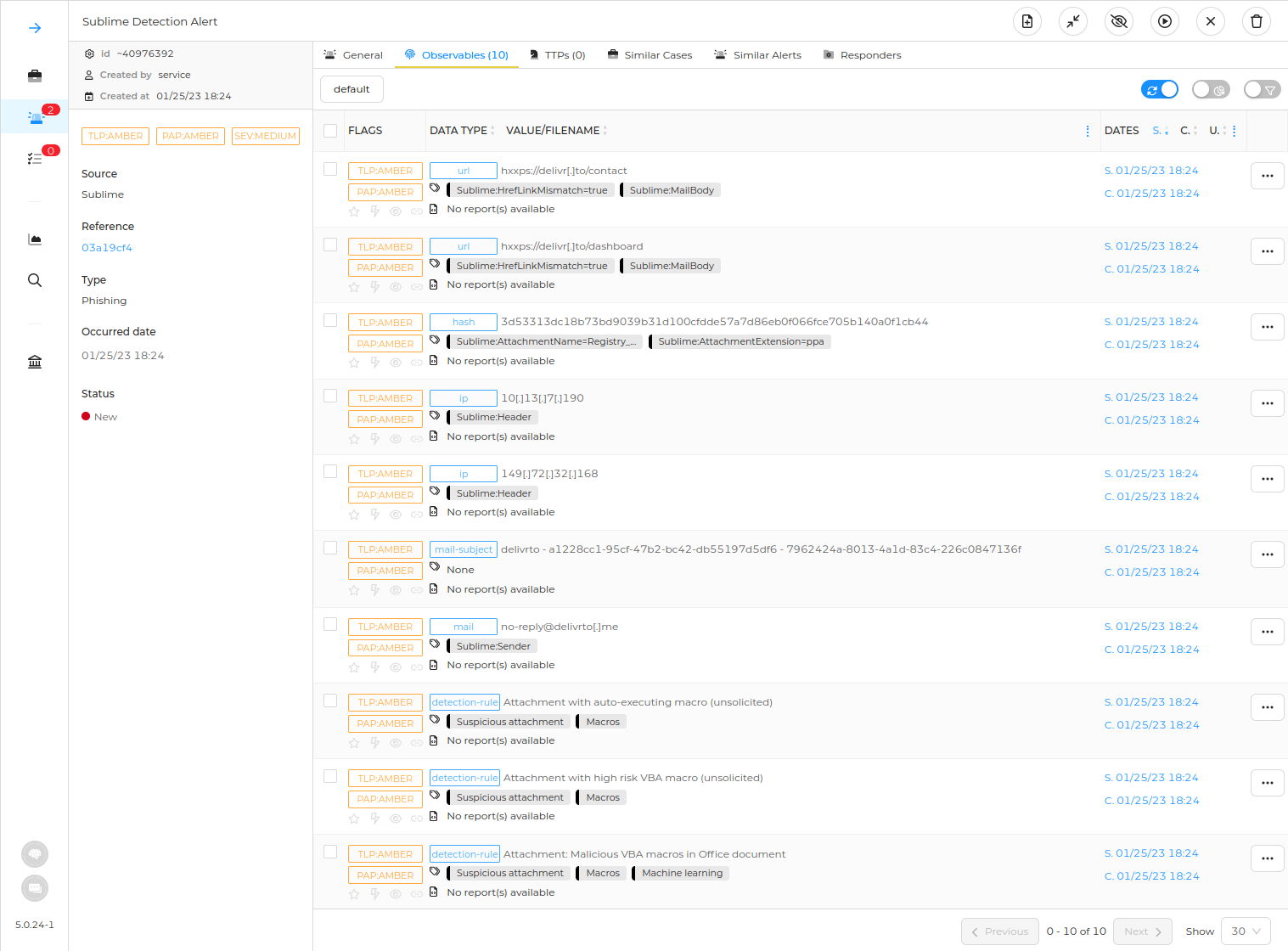
Hivelime is a comprehensive integration between TheHive and Sublime. Utilizing Sublime webhooks, Hivelime can be effortlessly configured to create alerts on TheHive!
- Triggered event (malicious email detection) is parsed and converted into an actionable TheHive alert with tags, observables;
- Request signing can be used if
SUBLIME_SIGNING_KEYvariable is provided; - Observables have detailed tags to further analyze, filter or use in remediation step;
- Built with both Security and OPS in mind. HiveLime has small footprint, great performance on various workloads and easily deployable with minimal configuration;
- Tags can be provided in configuration to be appended to alerts created by HiveLime;
- Alert has a brief summary description with links to detection, flagged rules and important information.
- Parameters should be provided via environment variables. Please see docker-compose file.
- Run the app via docker or via simply
./hivelime - HiveLime will listen
https://SERVER_ADDRESS/sublime/event. Make sure to provide/sublime/eventurl resource to Sublime Webhook action configuration.
- Alert reference is first 8 chars of detection CanonicalID;
- Check Releases section.
- Make sure that you have a working Golang workspace.
go build .go build -ldflags="-s -w" .could be used to customize compilation and produce smaller binary.
docker pull ghcr.io/kaansk/hivelime
Using Dockerfile
- Edit config file or provide environment variables to commands bellow
docker build -t hivelime .docker run -it hivelime
Using docker-compose file
- Edit environment variables and configurations in docker-compose file
docker-compose run -d
- Sublime Security
- Dockerfile Reference
- Release management with GoReleaser
- Delivr.to