Jannos-443
- Monitor automatic Windows Services
- Added Ability to use HTTP Push to avoid local Permission on critical Remote Servers (Backup etc.)
- Added Ability to define Critical Services that have to be present
- Added ChannelPerService and HideAutomaticNotRunning parameter
Option 1: Execute on Remote Server without PRTG needing local permissions on the Remote Server (HTTP Push Advanced)
- Place the lookup file
prtg.winservices.state.ovlon the PRTG probe(s) underC:\Program Files (x86)\PRTG Network Monitor\lookups\custom - Place Script on Remote Server (C:\PRTG\PRTG-WinServices.ps1)
- Create PRTG "HTTP Push Advanced Sensor" and copy the Token (Token is available in the Sensor Settings after creating the Sensor)
- you should set "no incoming data" to "switch to down status after x minutes"
- Create Schueduled Task
Example:
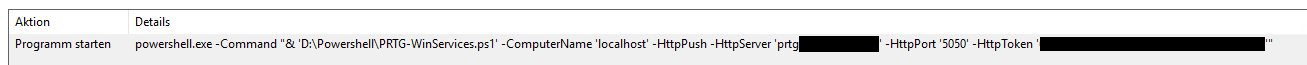
powershell.exe -Command "& 'C:\PRTG\PRTG-WinServices.ps1' -ComputerName 'localhost' -HttpPush -HttpServer 'YourPRTGServer' -HttpPort '5050' -HttpToken 'YourHTTPPushToken'"
-
Place
PRTG-WinService.ps1underC:\Program Files (x86)\PRTG Network Monitor\Custom Sensors\EXEXML -
Place the lookup file
prtg.winservices.state.ovlon the PRTG probe(s) underC:\Program Files (x86)\PRTG Network Monitor\lookups\custom -
Create new Sensor
Settings Value EXE/Script Advanced PRTG-WinService.ps1 -ComputerName "%host" Scanning Interval 10 min
If you connect to Computers by IP or to not Domain Clients please read Microsoft Docs
you maybe have to add the target to the TrustedHosts on the PRTG Probe and use explicit credentials.
example (replace all currenty entries):
Set-Item -Path WSMan:\localhost\Client\TrustedHosts -Value "ServerIP1,ServerIP2,ServerHostname1"
example want to and and not replace the list:
$curValue = (Get-Item wsman:\localhost\Client\TrustedHosts).value
Set-Item WSMan:\localhost\Client\TrustedHosts -Value "$curValue,NewServer3.test.com"
exmaple PRTG parameter with explicit credentials:
-ComputerName "%host" -Username "%windowsuser" -Password "%windowspassword"
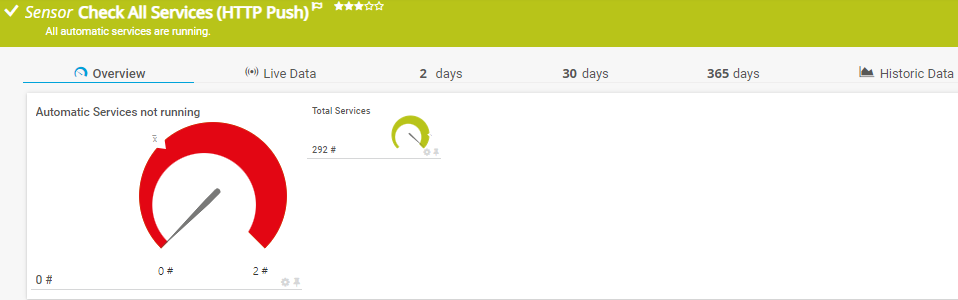
simple check automatic Services of Remote Computer
-ComputerName "%host"exclude every service starting with "Intel"
-ComputerName "%host" -ExcludePattern '^(Intel.*)$'exclude "Test123" and every service starting with "Intel"
-ComputerName "%host" -ExcludePattern '^(Intel.*|Test123)$'only check services starting with "Intel"
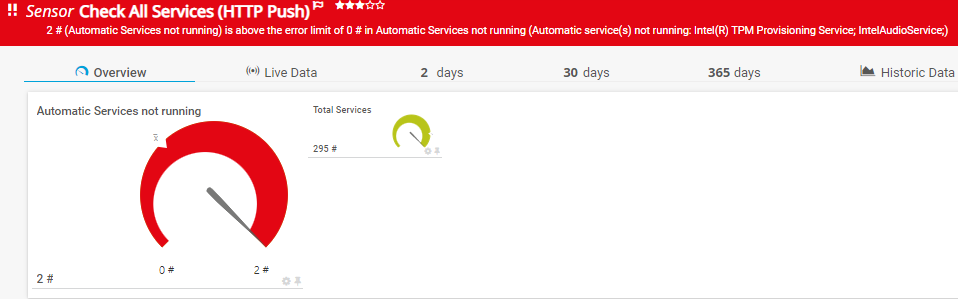
-ComputerName "%host" -IncludePattern '^(Intel.*)$'filters for "Bitdefender" Services that are preset. CriticalService will be the number of matching services
-ComputerName "%host" -CriticalServicePattern '^(Bitdefender)$'filters for "Bitdefender" Services that are preset and running. CriticalService will be the number of matching services
-ComputerName "%host" -CriticalServicePattern '^(Bitdefender)$' -CriticalServiceMustRuncheck automatic Services and require the client to have two matching CriticalServices present and running. Does only work for channel creation.
-ComputerName "%host" -CriticalServicePattern '^(Bitdefender|WinDefend)$' -CriticalServiceMustRun -CriticalServiceLimit 2Use explicit credentials ("Windows credentials of parent device" is the better way)
-ComputerName "%host" -UserName "YourRemoteComputerUser" -Password "YourRemoteComputerPassword"HTTP Push from Remote Server
powershell.exe -Command "& 'C:\PRTG\PRTG-WinServices.ps1' -ComputerName 'localhost' -HttpPush -HttpServer 'YourPRTGServer' -HttpPort '5050' -HttpToken 'YourHTTPPushToken'"HTTP Push from Remote Server and exclude every service starting with "Intel"
powershell.exe -Command "& 'C:\PRTG\PRTG-WinServices.ps1' -ComputerName 'localhost' -HttpPush -HttpServer 'YourPRTGServer' -HttpPort '5050' -HttpToken 'YourHTTPPushToken' -ExcludePattern '^(Intel.*)$'"Show channel for each service, use with "IncludePattern"
-ComputerName "%host" -IncludePattern '^(prtg.*)$' -HideTotalServiceCount -HideAutomaticNotRunning -ChannelPerServiceYou can use the variables to exclude/include Services The variables take a regular expression as input to provide maximum flexibility.
For more information about regular expressions in PowerShell, visit Microsoft Docs.
".+" is one or more charakters ".*" is zero or more charakters
look into the following links:
- User has to be in the following groups: Performance Monitor Users and Distributed COM Users
- Windows Firewall WMI/WinRM
- Set WMI Permission
- https://github.com/grbray/PowerShell/blob/main/Windows/Set-WMINameSpaceSecurity.ps1
- https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClcsCAC