Website • Releases • Buy license • User Guide
If you want to use a dedicated IAM user with minimal privileges please use the following policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "CloudPouchMinimalAccess",
"Effect": "Allow",
"Action": [
"application-autoscaling:DescribeScalableTargets",
"ce:GetCostAndUsage",
"cloudwatch:GetMetricStatistics",
"dynamodb:DescribeTable",
"dynamodb:ListTables",
"ec2:Describe*",
"elasticloadbalancing:DescribeLoadBalancers",
"elasticloadbalancing:DescribeTargetGroups",
"elasticloadbalancing:DescribeTargetHealth",
"logs:DescribeLogGroups",
"organizations:ListAccounts",
"rds:DescribeDBClusters",
"rds:DescribeDBInstances",
"rds:DescribeDBSnapshots"
],
"Resource": "*"
}
]
}Last change for version 1.24.0.
The CloudPouch includes an option that enables users to configure and use a certificate when connecting to the internet. This feature is particularly beneficial for users operating within corporate networks that frequently have stringent security protocols, often mandating certificate use for internet resource access.
The CloudPouch supports the use of custom and global SSL/TLS certificates in PEM format (.pem). These could be certificates issued by widely recognized CAs, or those signed by private or self-signed authorities. Please make sure to specify the correct path to your certificate when configuring your CloudPouch application.
To set up the certificate, please define the path to the certificate file in the config.json file, as shown below:
{
"certificatePath": "<Path to your .pem certificate file>"
}Here, certificatePath should contain the full path to your .pem file, including the file name. Please ensure you have the necessary read permissions to access this file.
Ensure to restart the CloudPouch application for the new certificate settings to take effect.
Should you need more detailed information about supported certificates, refer to the public documentation regarding AWS_CA_BUNDLE and NODE_EXTRA_CA_CERTS on the Internet.
The config.json file location depends on the OS you're using:
- MacOs -
/Users/<YOUR_USER_NAME>/Library/Application Support/CloudPouch/config.json - Windows -
c:\Users\<YOUR_USER_NAME>\AppData\Roaming\CloudPouch\config.json - Linux -
~/.config/CloudPouch/config.json
Certificate support was introduces in version 1.25.0.
Click this button to create CloudPouch-access-policy-stack on your AWS account with the IAM policy that you can attach to any IAM Role or IAM User.
Step-by-step guide of CloudFormation deployment
- This is the first CloudFormation service console with the template already pre-loaded. Click
Next.
- There are parameters to set. Click
Next.
- Leaver everything as is. Click
Next.

- Review and click
Next.

- CloudFormation deployment starts.

- After a moment it is finished.

- Go to IAM Policies tab and find the policy named
CloudPouch-costs-policy.
- Now you need to add this policy to an IAM User or a Role.
- After Policy is created go to the IAM Users tab, select a user and click
Add Permissionsbutton (select againAdd Permissionsfrom the dropdown list). - Select
Attach policies directlyand in the search below enter the name of the newly created IAM Policy:CloudPouch-costs-policy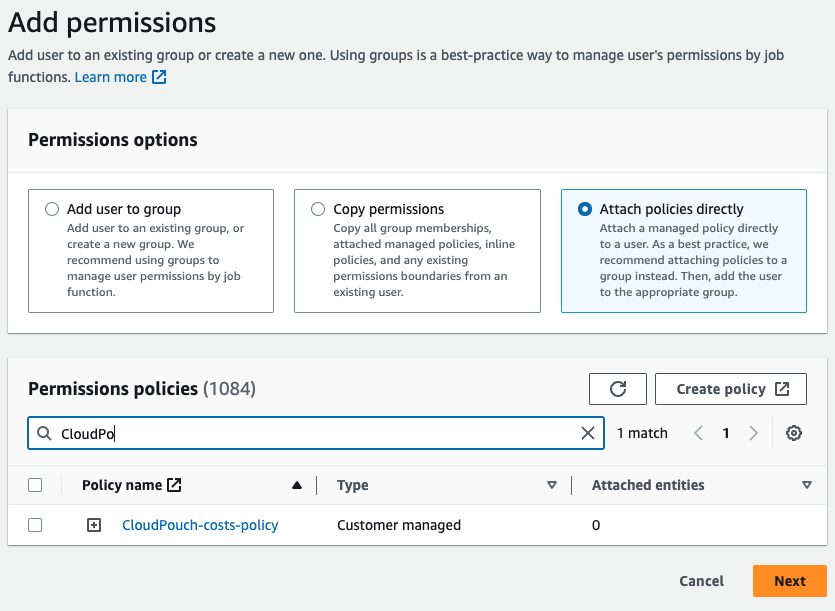
- Tick checkbox next the it and click
Next - On the next screen click
Add Permissionsbutton. - Done ✅
ce:GetCostAndUsageis crucial as allows to fetch cost data.organizations:ListAccountsused to resolve names of your accounts in the AWS Organizations. Used only when you have paying account.
Insights check your resources in the AWS cloud and provide useful information for cost optimization. They can detect waste, for example unattached EBS drives or wrongly configured resources such as over-provisioned DynamoDB tables.
- EC2 - Other insights use following privileges:
ec2:Describe*
- DynamoDB insights use:
dynamodb:DescribeTabledynamodb:ListTablescloudwatch:GetMetricStatisticsapplication-autoscaling:DescribeScalableTargets
- CloudWatch insights use:
logs:DescribeLogGroups
- RDS insights use:
rds:DescribeDBClustersrds:DescribeDBInstancesrds:DescribeDBSnapshots
<
