Become a sponsor to BC Security
Background
We are a small group of hackers/developers/enthusiasts that maintain and develop open-source security tools, tutorials, and training.
If you use Empire, Starkiller, Invoke-PrintDemon, Invoke-ZeroLogon, or any of our other projects, a monthly contribution will mean A LOT to us. On its own, open-source development does not keep the lights on. But with your help, we can continue to develop offensive security tools.
We have been creating content in our spare time, which requires a significant amount of time and effort to continue these open-source projects. By becoming a sponsor, you would be directly funding the development of these tools and the creation of new ones.
Your money will help us contribute to the community in other ways:
Benefits
- 30 days of early access to Empire and Starkiller releases
- Access to the sponsor discord channel and role
- Swag
Bypass Repo
Access to a growing repo of bypass samples (AMSI, ETW, Script Block Logging).

Extra Starkiller features
Dashboard
Graph View
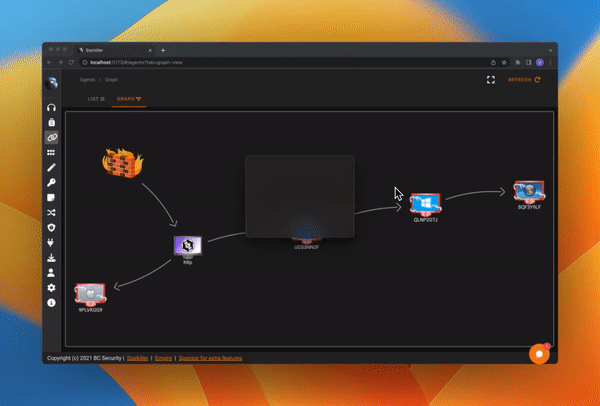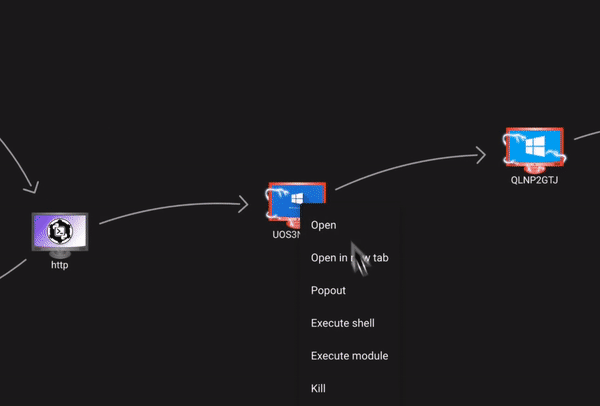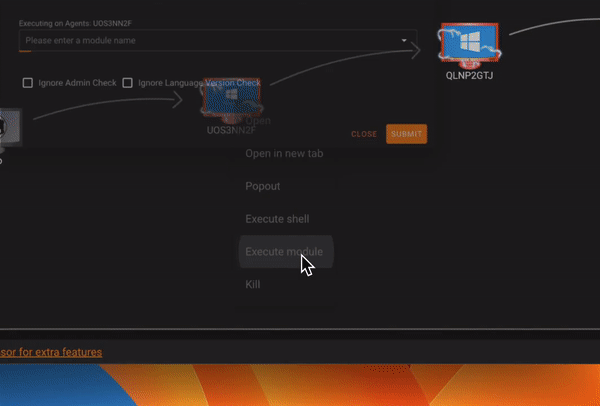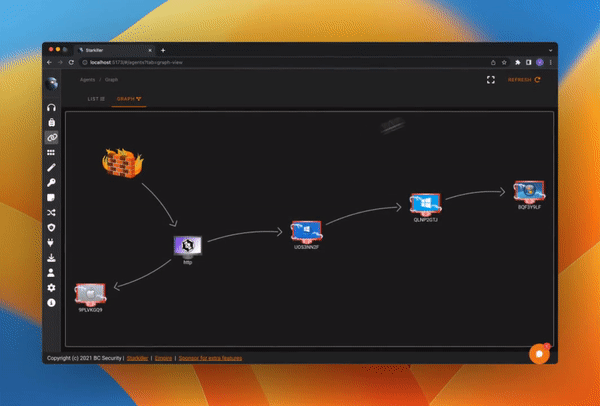
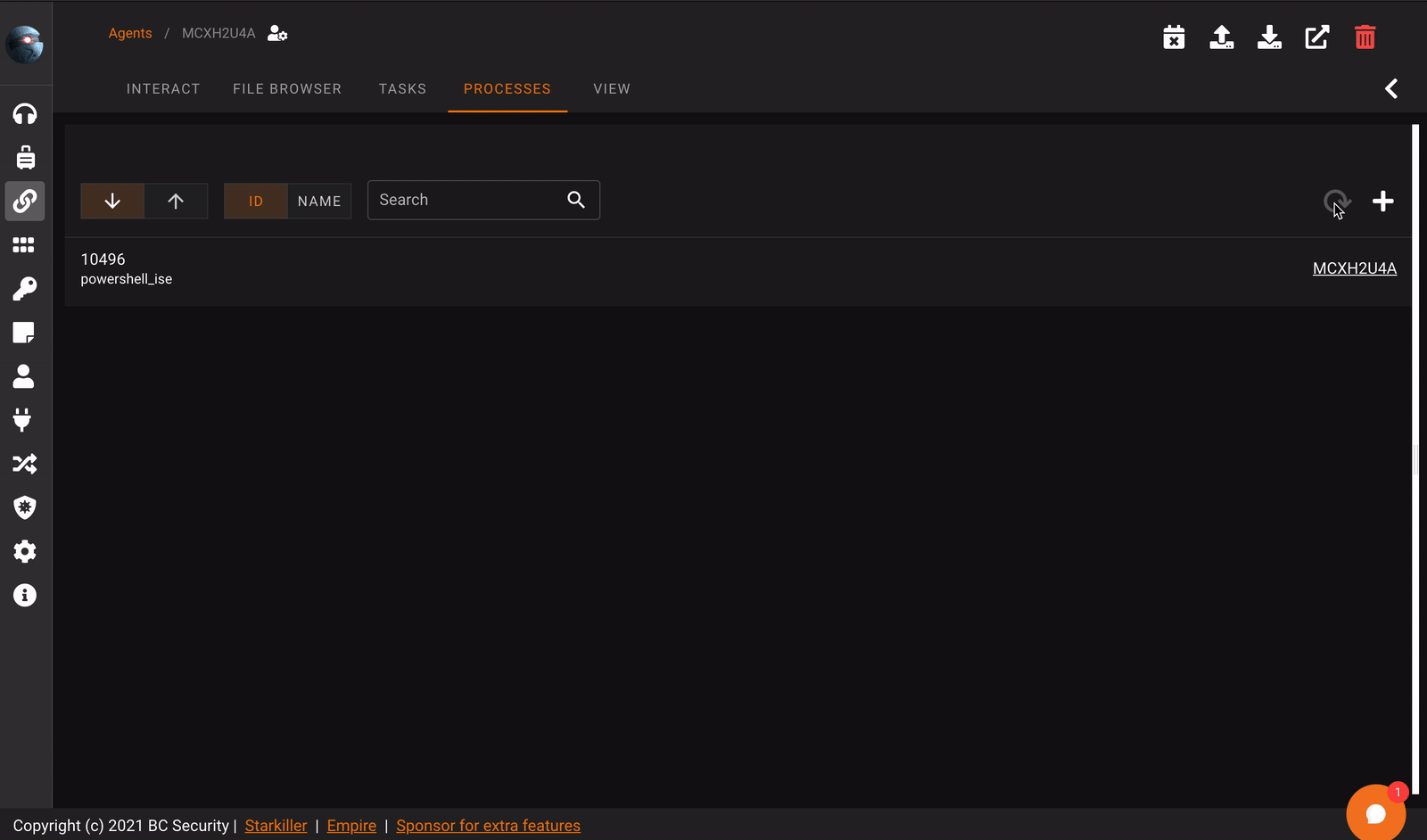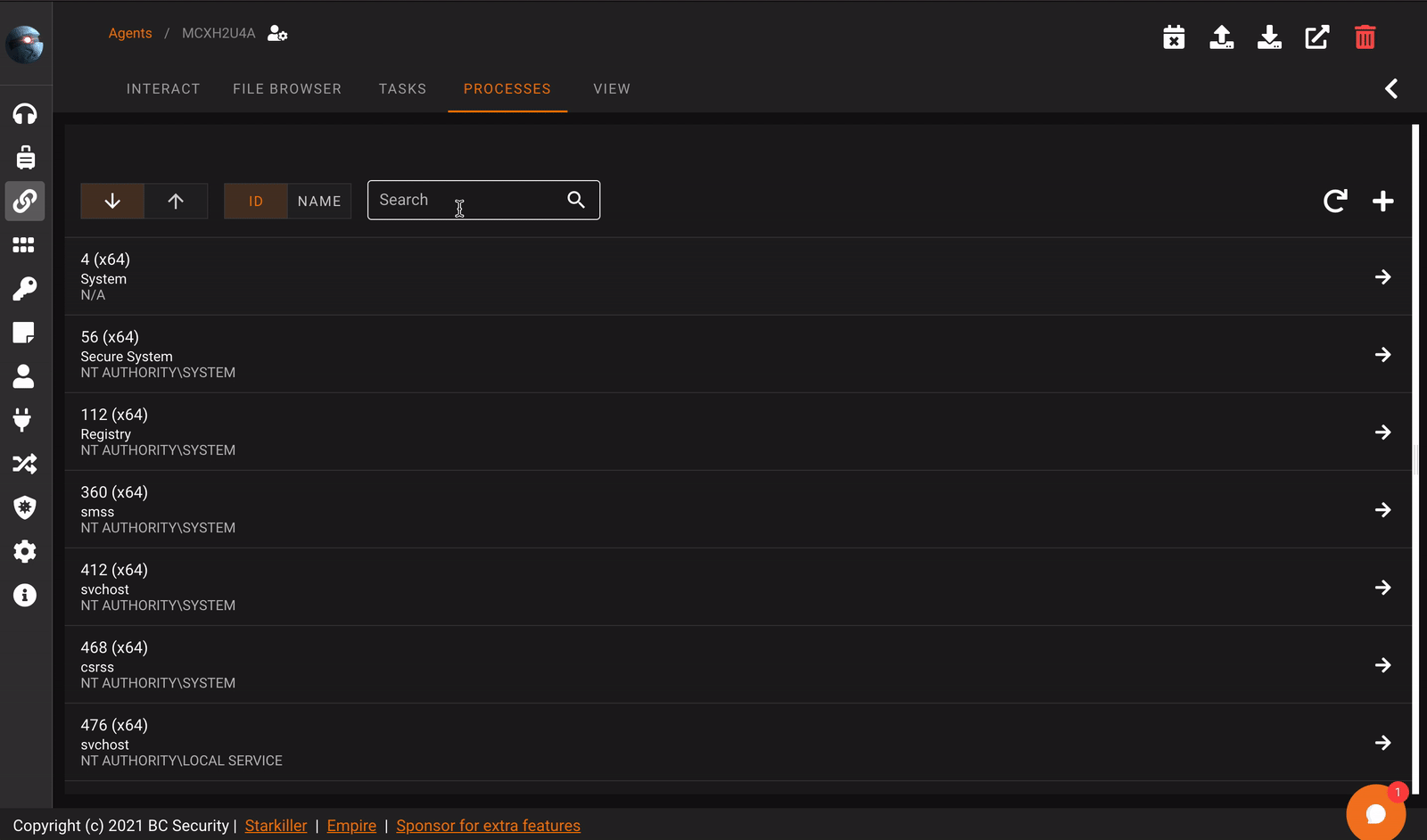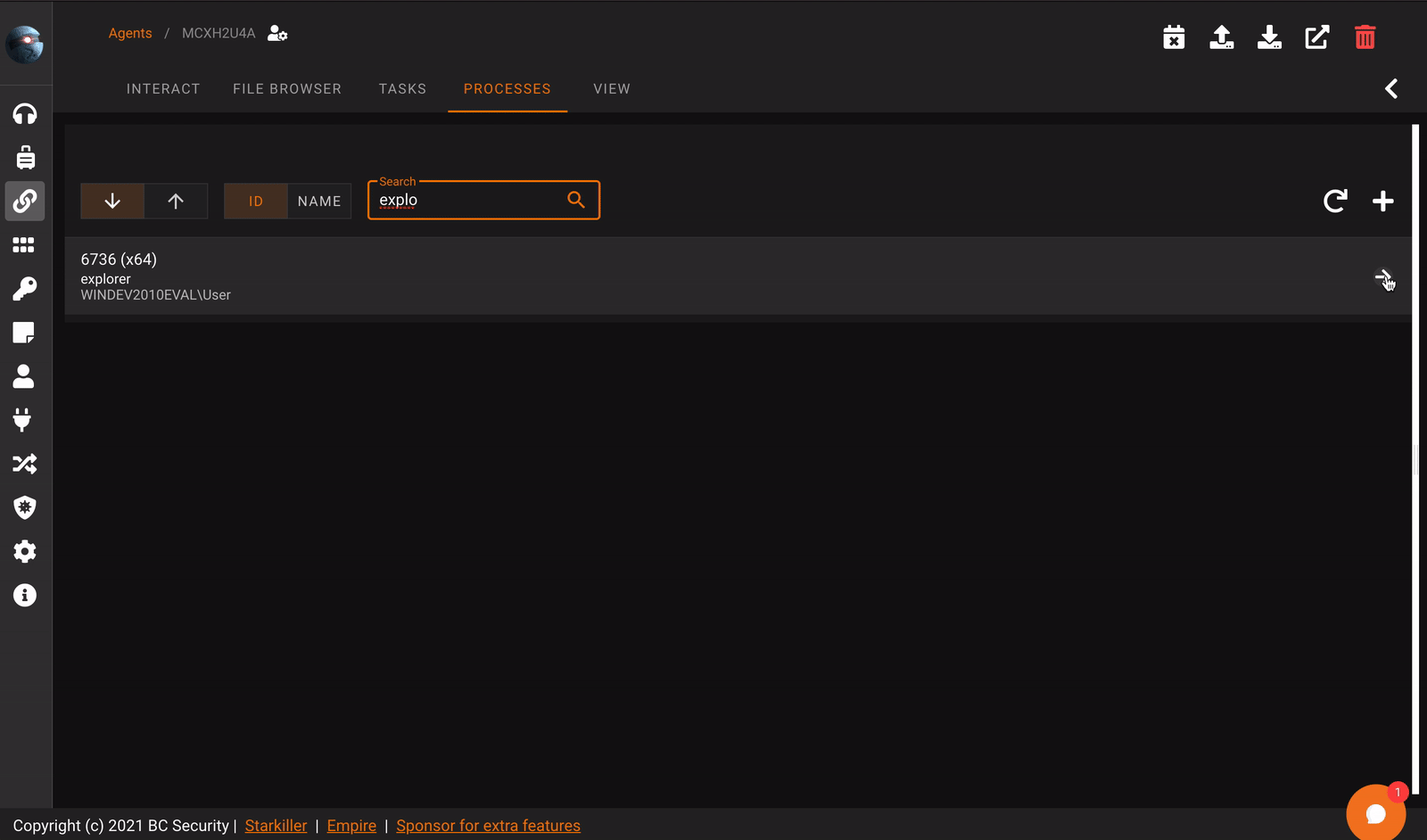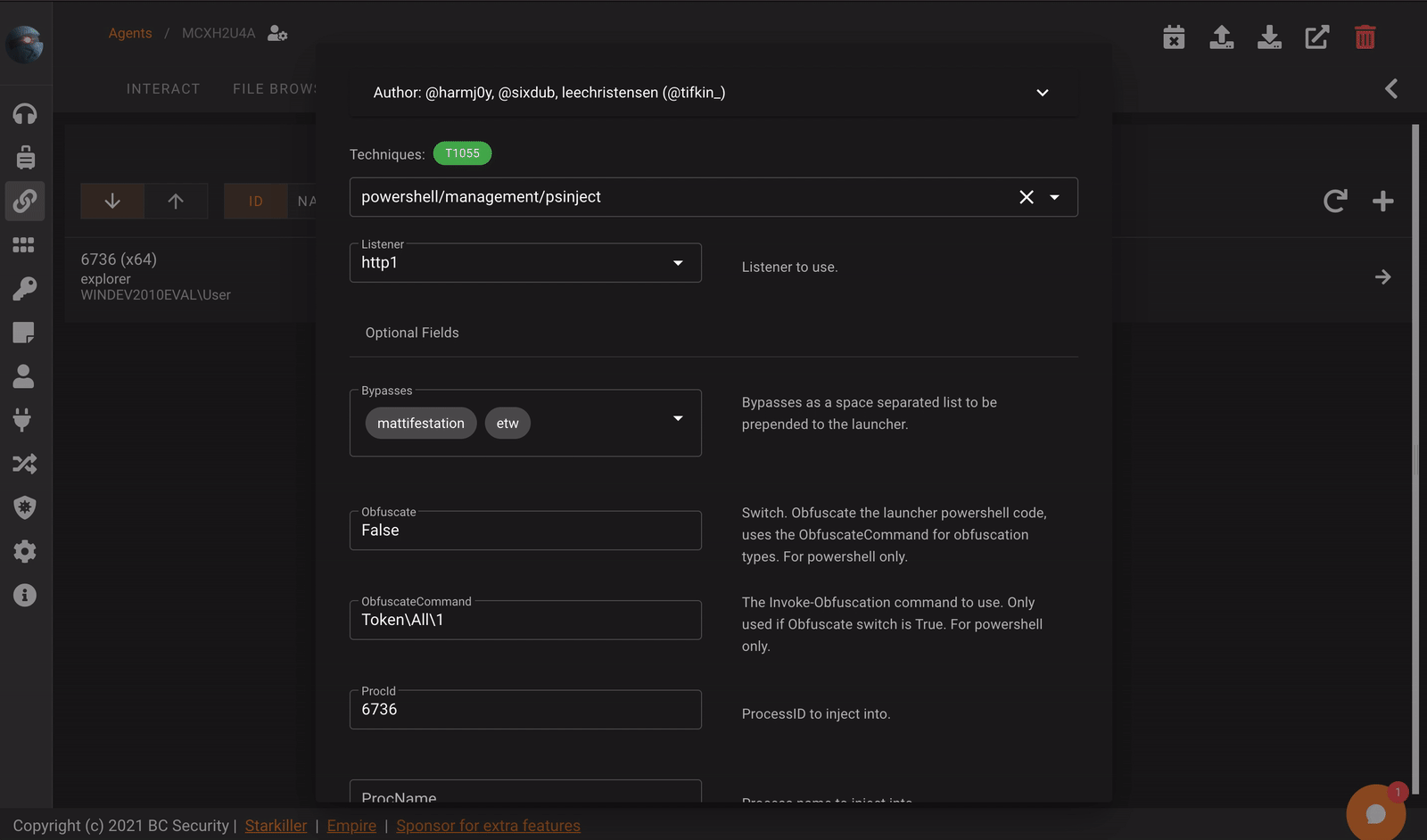
Process Browser
Modify Module Scripts
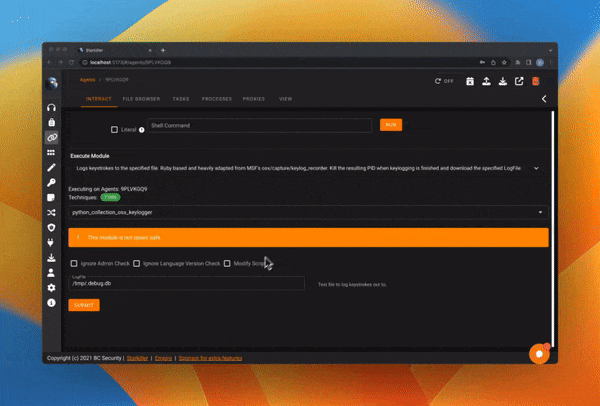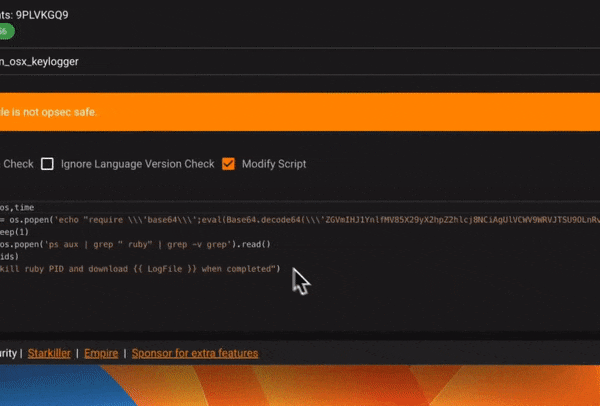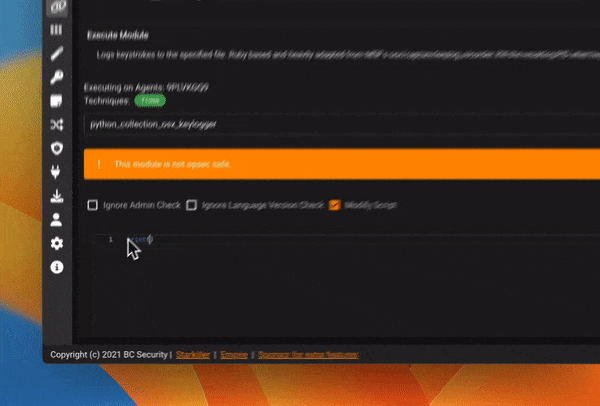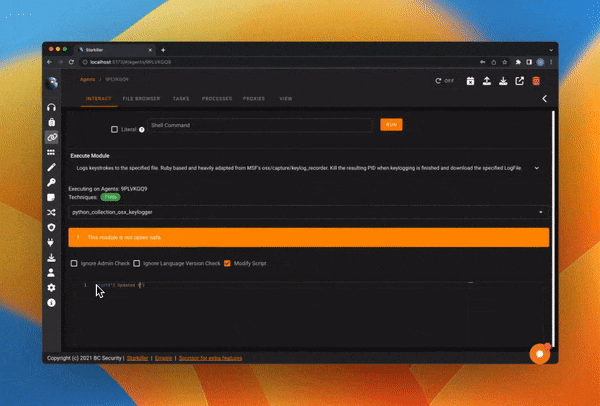
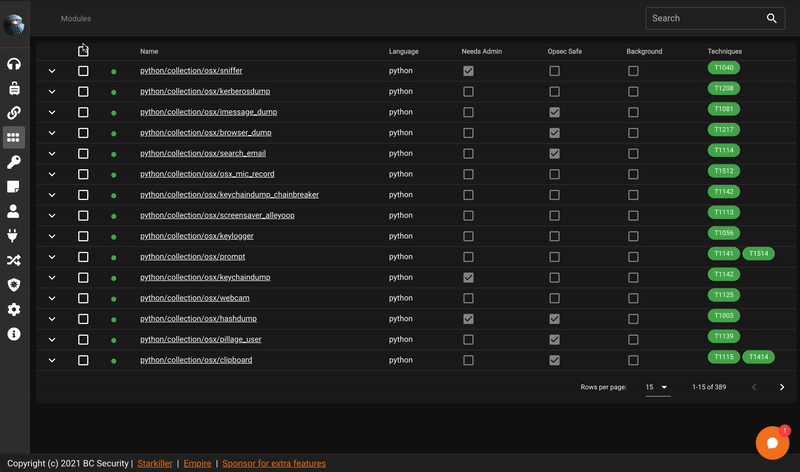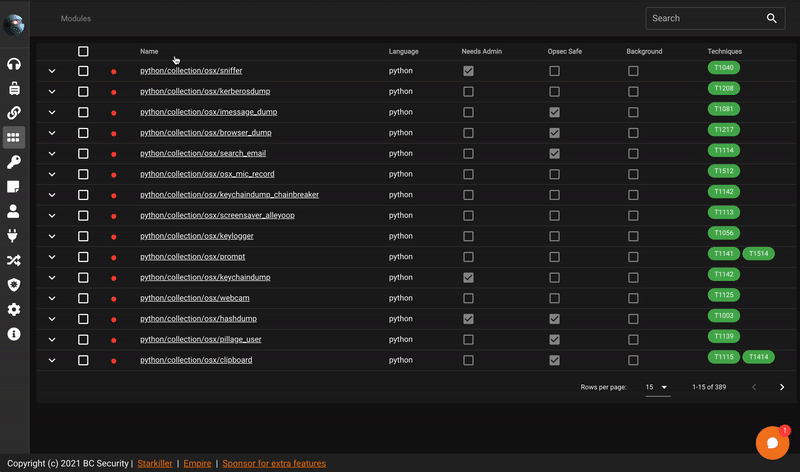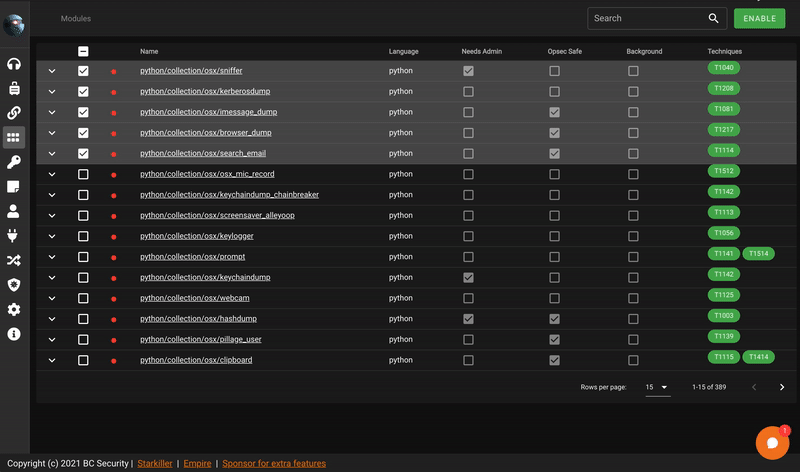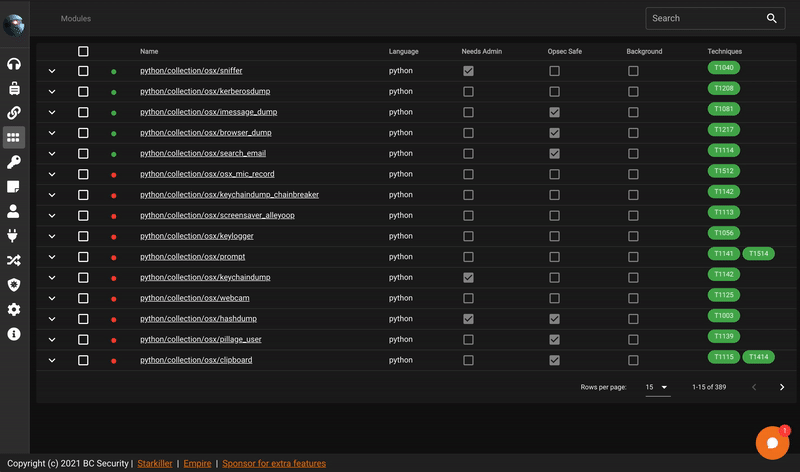
Enable/Disable modules
Proxy Management
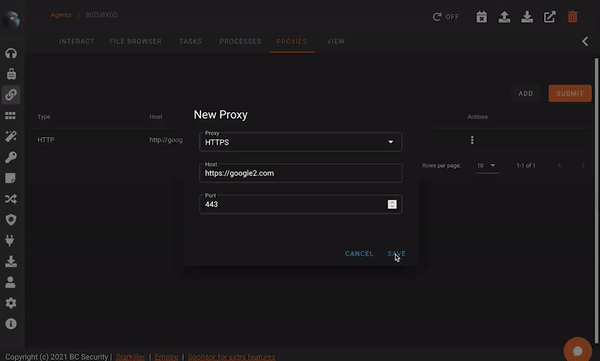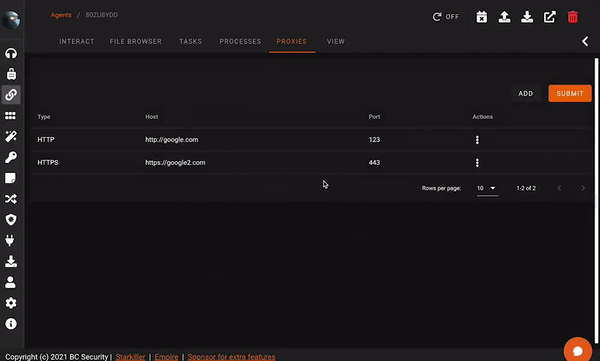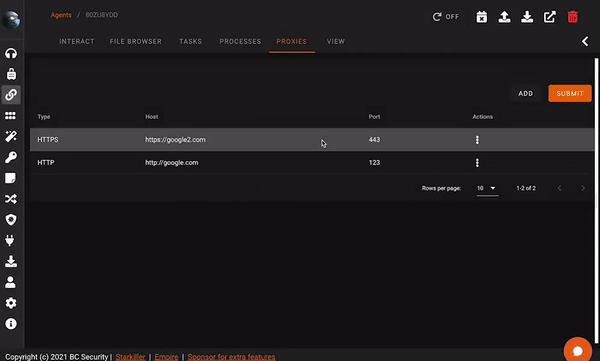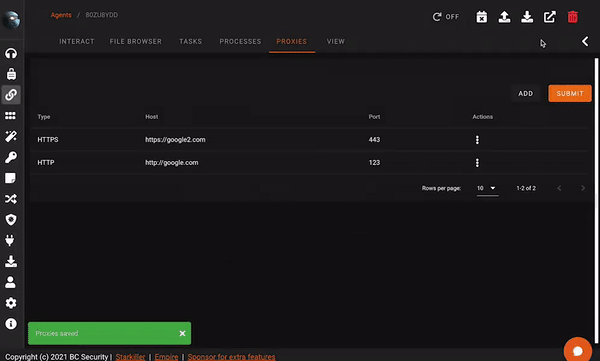
Empire Sponsor Plugins
| Plugin Name | Description |
|---|---|
| AMSI Fail | The AMSI Fail Plugin calls the AMSI.fail API to generate and add a fresh AMSI Bypass to the Empire database. |
| MITRE ATT&CK | The ATT&CK plugin assists in better threat emulation in Empire by leveraging the MITRE ATT&CK Framework for report generation and module management. |
| Advanced Reports | Creates customizable PDF reports (Empire Report, Module Report, Master Log, Sessions, Credentials) |
| EternalBlue | EternalBlue-Plugin uses the EternalBlue exploit (CVE-17-010) to perform remote code execution on SMB. |
| Nmap | Nmap-Plugin gives a way to interface directly from Empire to Nmap and send commands through Python3-Nmap. |
| SMBGhost | SMBGhost-Plugin is a python implemenation of SMBGhost/CoronaBlue (CVE-2020-0796) that uses a remote code execution vulnerability to exploit Microsoft Server Message Block 3.1.1 (SMBv3) protocol. |
Thank you for your support!
Current sponsors 34
Meet the team
Featured work
-
BC-SECURITY/Empire
Empire is a post-exploitation and adversary emulation framework that is used to aid Red Teams and Penetration Testers.
PowerShell 4,129 -
BC-SECURITY/Starkiller
Starkiller is a Frontend for PowerShell Empire.
Vue 1,324 -
BC-SECURITY/Invoke-PrintDemon
This is a PowerShell Empire launcher PoC using PrintDemon and Faxhell.
PowerShell 196 -
BC-SECURITY/Invoke-ZeroLogon
Invoke-ZeroLogon allows attackers to impersonate any computer, including the domain controller itself, and execute remote procedure calls on their behalf.
PowerShell 213 -
BC-SECURITY/Malleable-C2-Profiles
Malleable C2 Profiles. A collection of profiles used in different projects using Cobalt Strike & Empire.