pycfais a python script to audit CloudFormation template files for security misconfigurations. It supports both JSON and YAML formats.
I was looking to something similar to Scout2 but without the hassle of spinning up the whole infrastructure. pycfais particularly useful when you have to do a security audit of a series of CloudFormation template files. I was looking for something quick and reliable. Here it is pycfa.
pycfa reads rules from a file in JSON format (by default in rules/rules.json).
It provides a colorful output to stdout (by default) or in JSON format if -j flag is provided (without colors though).
The rule file syntax is as follow:
{
"rules": [
{
"type": "<resource::type>",
"key": "<path.to.key>",
"match": "<strict | bool | regex>",
"<what-to-check>": "<value>"
}
],
"level": "<info | warning | danger>",
"description": "wut?"
}What the hell they mean? Here we go:
- type: the resource type as specified by the Type tag (optional)
- key: path to the rule's parent key, starting after the Proprieties key. e.g. if you want to check an IAM Policy Action key, then this value will be PolicyDocument.Statement
- match: the way the field rules is interpreted.strictmeans "equal",boolcheck if the what-to-check value exists, andregexpinterpreters the <value> as a regular expression.
- what-to-check: this is the leaf key you want to check. It's in the form key:value, and this is actually the core of your rule.
- level: level of risk
- description: a description of the rule
Please notethat the rules are evaluated as AND at the moment.
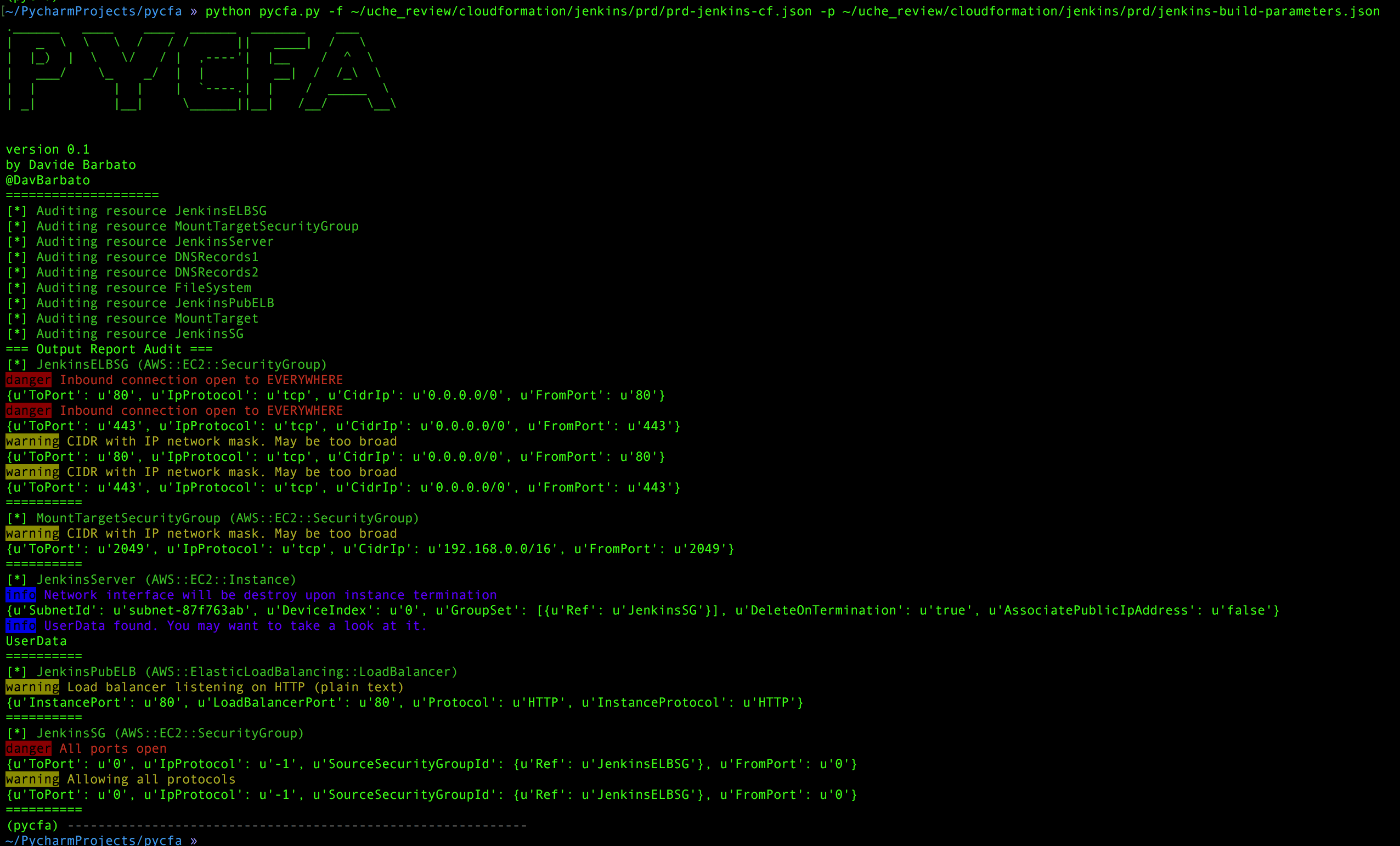
» python pycfa.py
.______ ____ ____ ______ _______ ___
| _ \ \ \ / / / || ____| / \
| |_) | \ \/ / | ,----'| |__ / ^ \
| ___/ \_ _/ | | | __| / /_\ \
| | | | | `----.| | / _____ \
| _| |__| \______||__| /__/ \__\
version 0.1
by Davide Barbato
@DavBarbato
====================
usage: pycfa.py [-h] [-d DIRPATH | -f CFTEMPLATE] [-p CFPARAMS]
[-r CUSTOM_RULE] [-j]
optional arguments:
-h, --help show this help message and exit
-d DIRPATH, --dir DIRPATH
specify a directory
-f CFTEMPLATE, --file CFTEMPLATE
a CF template file
-p CFPARAMS, --parameters CFPARAMS
parameters file for the CF template
-r CUSTOM_RULE, --rules CUSTOM_RULE
specify a custom rule file
-j, --json output in JSON format- Make it context aware to better correlate resources
- Optimize code
- Terraform support!!!! (thanks to json2hcl)
- Add more rules
- Better output (?)