In this repo, you will find samples to create your own dashboard, reports & alerts based on the Azure AD B2C logs.
-
Read about Audit Logs and Sign in Logs to gain better understanding about their usage and schema.
-
Read about Azure Monitor to understand its key features.
-
Read about Azure Active Directory reporting latencies and Log data ingestion time in Azure Monitor which covers various latencies across Azure AD B2C and Azure Monitor.
-
Read about Log Analytics Queries to understand how to create and run reports using Kusto language.
-
Read about Azure Monitor Workbooks which provides a flexible canvas for data analysis and the creation of rich visual reports.
-
Read about Azure Alerts their benefits and usage patterns.
-
You will be required to create an Azure AD B2C directory, see the guidance here.
-
To use the sample artifacts in this repo, follow the instructions described in the Monitor Azure AD B2C with Azure Monitor to setup Azure Monitor to route sign-in and auditing logs to Log Analytics workspace. After the setup is complete, it may take up to 45 minutes or so for logs to show up in Log Analytics workspace. Subsequently, Azure monitor will sync the logs within few minutes as they get generated by Azure AD B2C.
All the reports in this repo are based on Azure Monitor Workbooks which provide a flexible canvas for data analysis and the creation of rich visual reports within the Azure portal.
| Name | Deploy |
|---|---|
| Dashboard | |
| Risk Detections | |
| Conditional Access | |
| MFA | |
| Search by CorrelationId | |
| Phone Authentication Failures | |
| List of Abandon Journeys |
The Workbooks folder within this repo contains four workbooks in the standard JSON Gallery Template format. You can use the following instructions to import the JSON to create a new workbook. Please note that you need to repeat these steps for all workbooks.
- Dashboard
- MFA
- Risk Detections
- Conditional Access
- Search by CorrelationId
- List of Abandon Journeys
- Phone Authentication Failures
The Azure AD B2C Dashboard workbook provides various reports related to User Insights and Authentications for Azure AD B2C Tenant.
-
From Log Analytics workspace select Workbooks.
-
From the toolbar, select + New option to create a new workbook.
-
On the New workbook page, select the Advanced Editor using the </> option on the toolbar.
-
Select Gallery Template.
-
Replace the JSON in the Gallery Template with the content Azure AD B2C basic workbook:
-
Apply the template by using the Apply button.
-
Select Done Editing button from the toolbar to finish editing of the workbook.
-
Finally, save the workbook by using the Save button from the toolbar.
-
Provide a Title such as, Azure AD B2C Dashboard.
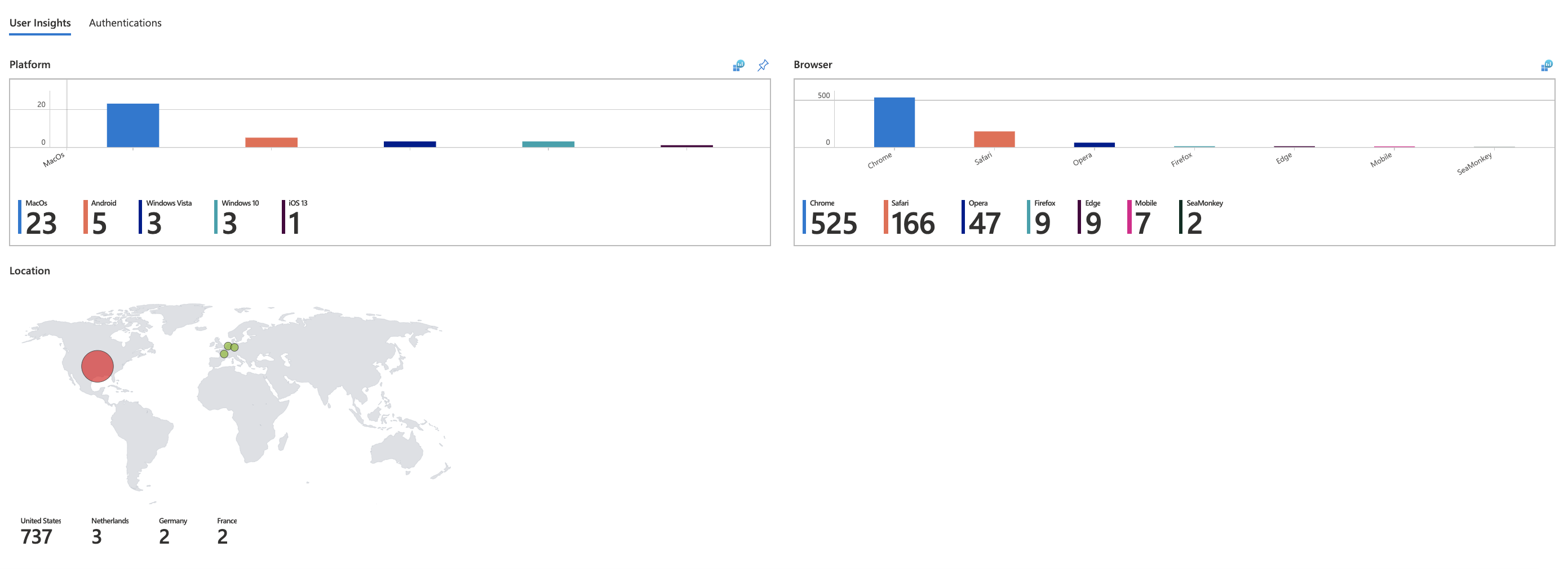
The workbook will display reports in the form of a dashboard.
-
User Insights
- Platform
- Browser
- Location
-
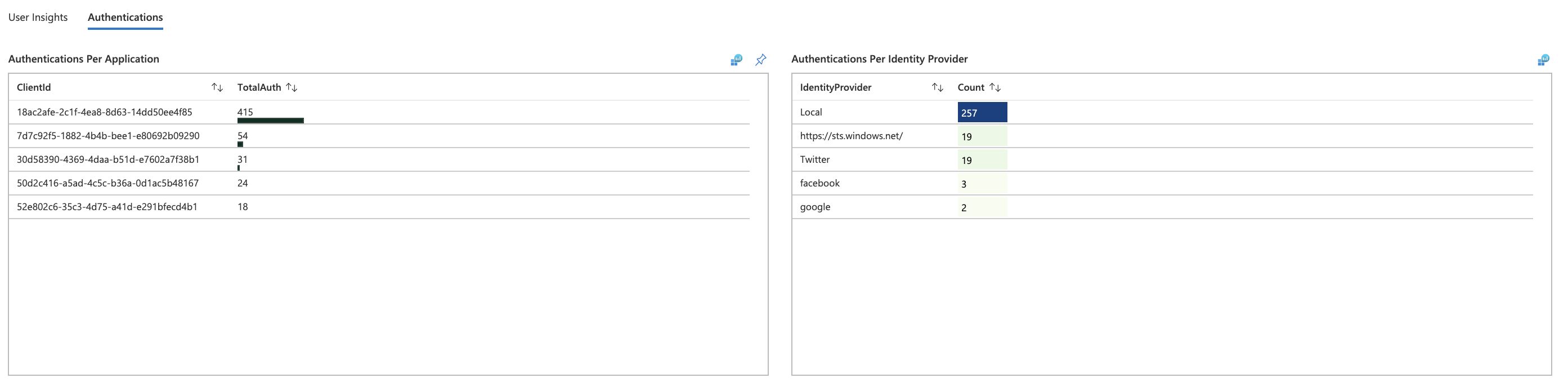
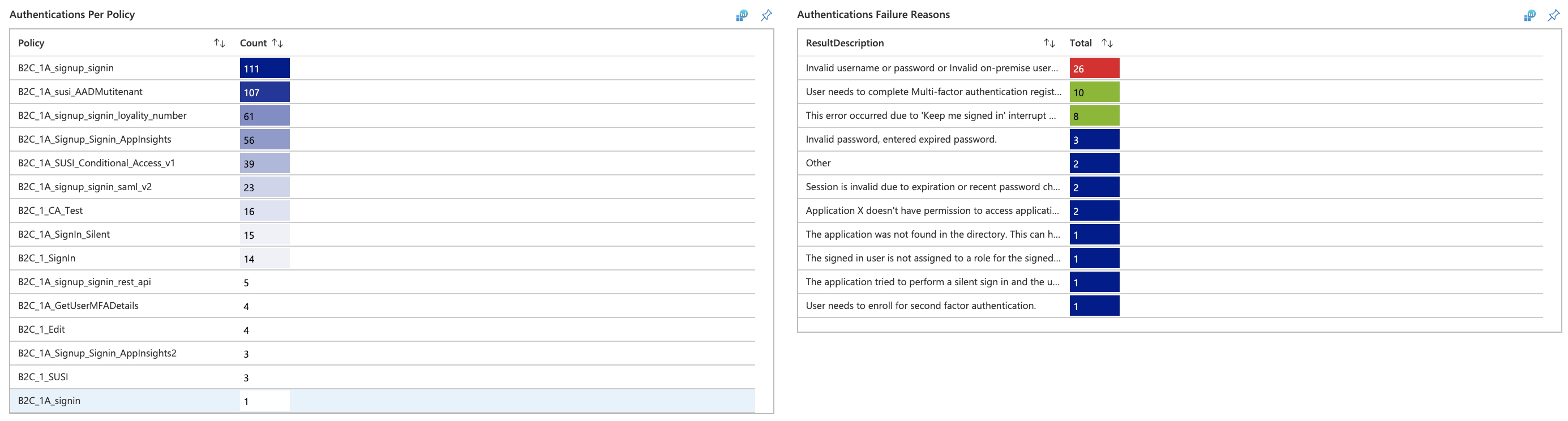
Authentications
- Authentications Per Applications
- Authentications Per Identity Provider
- Authentications Per Policy
- Authentications Failure Reasons
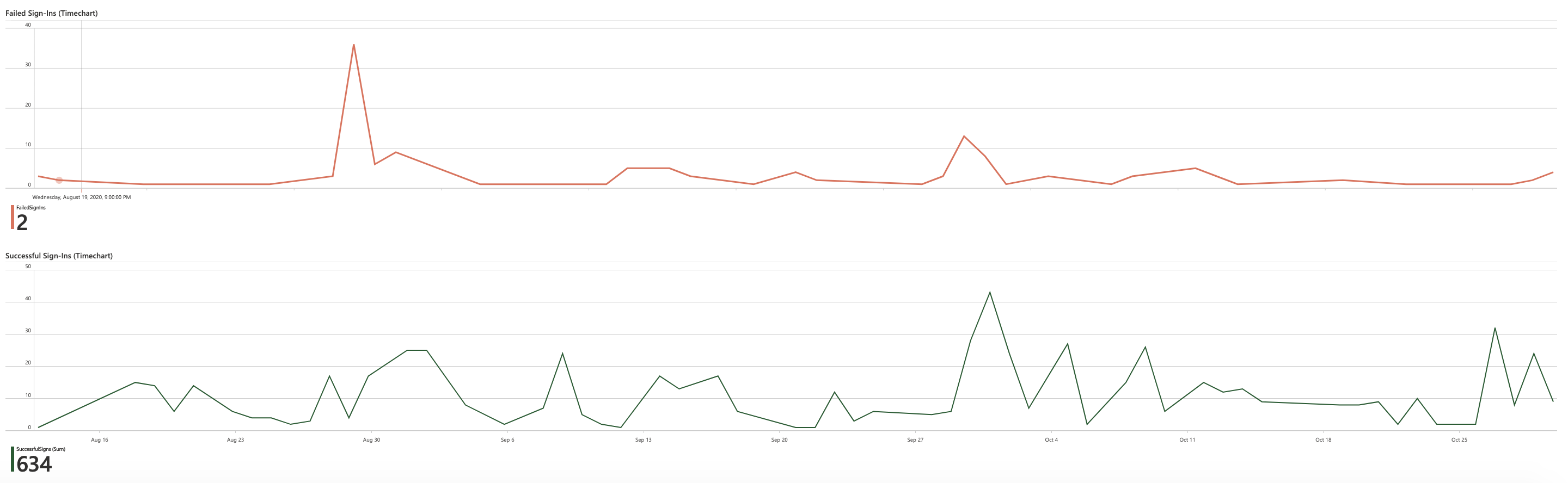
- Failed Sign-Ins (Timechart)
- Successful Sign-Ins (Timechart)
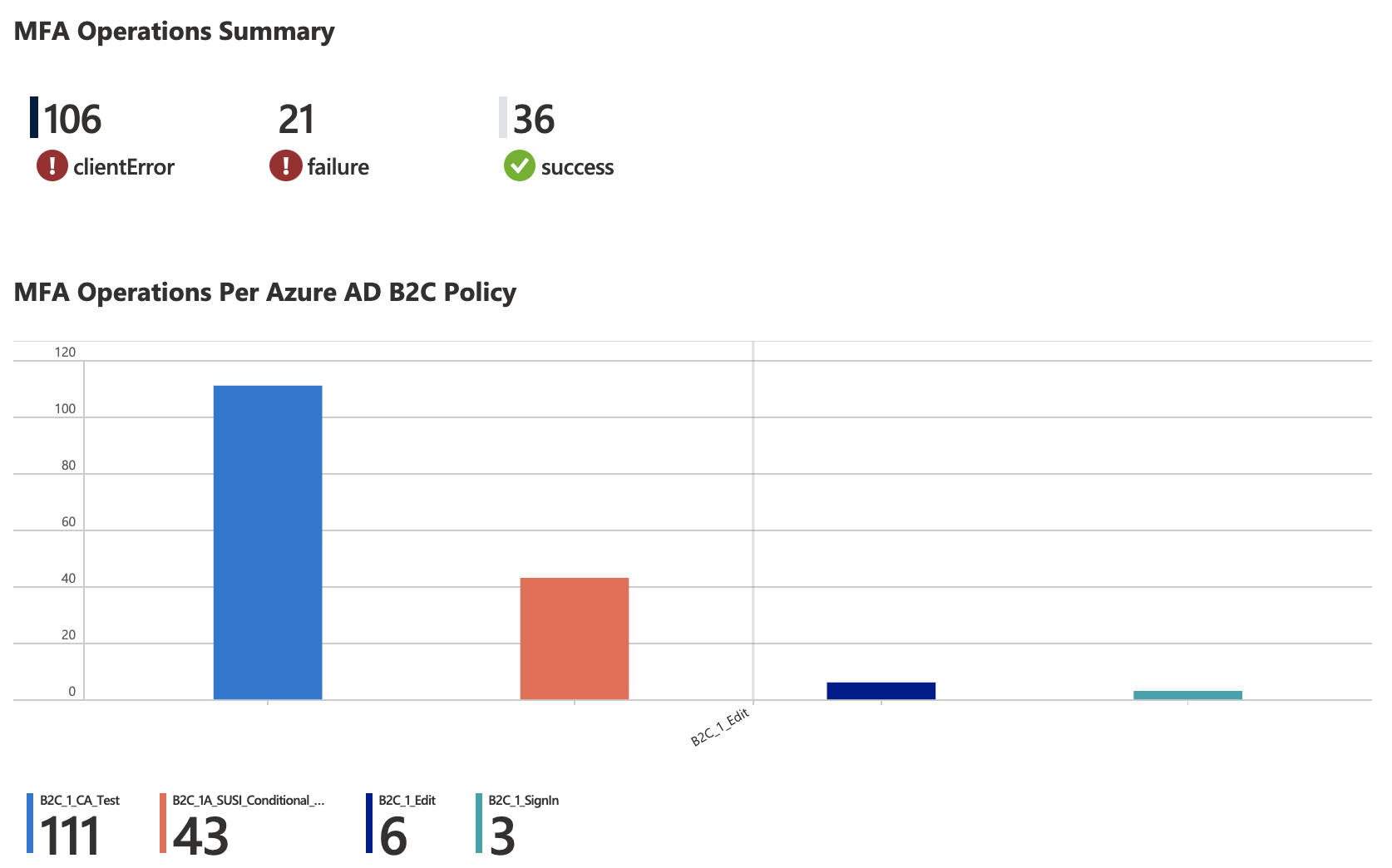
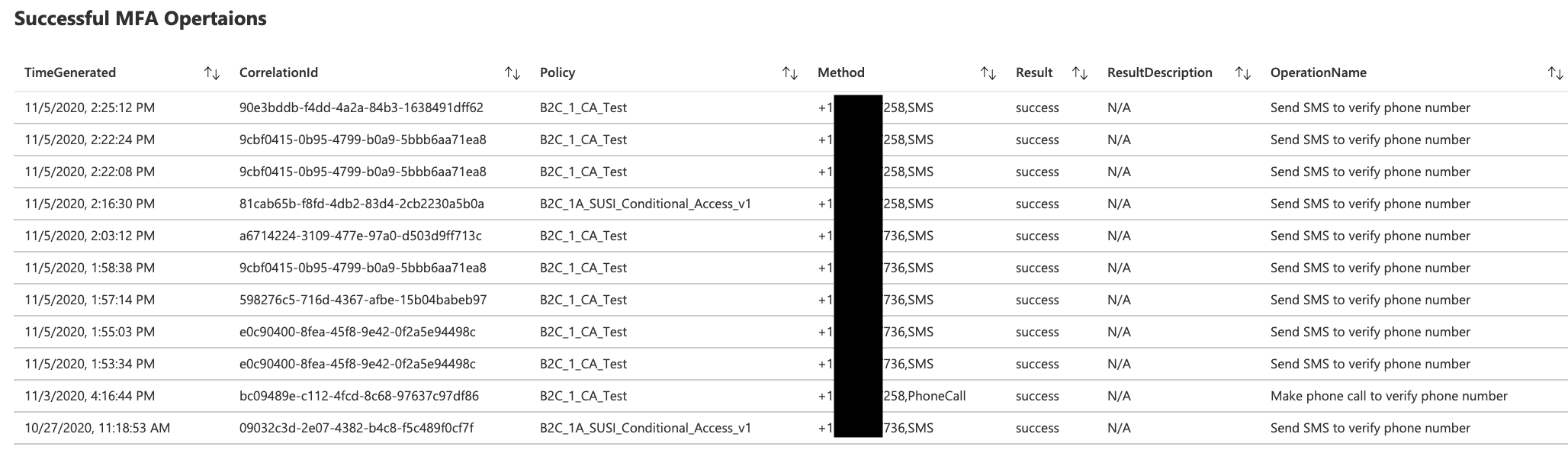
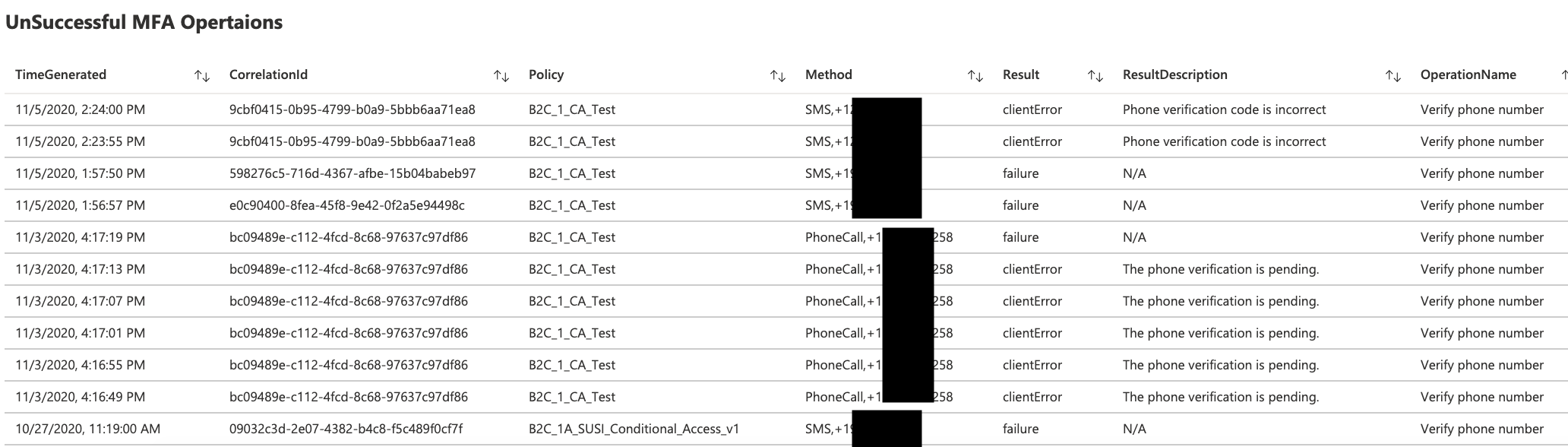
MFA workbook provides summary of successful and failed MFA operations throughout Azure AD B2C Tenant.
-
MFA Operations
- Summary of MFA operations (success, failed, client error)
- MFA operations per Azure AD B2C Policy
- Details of Successful MFA Operations
- Details of Unsuccessful MFA Operations
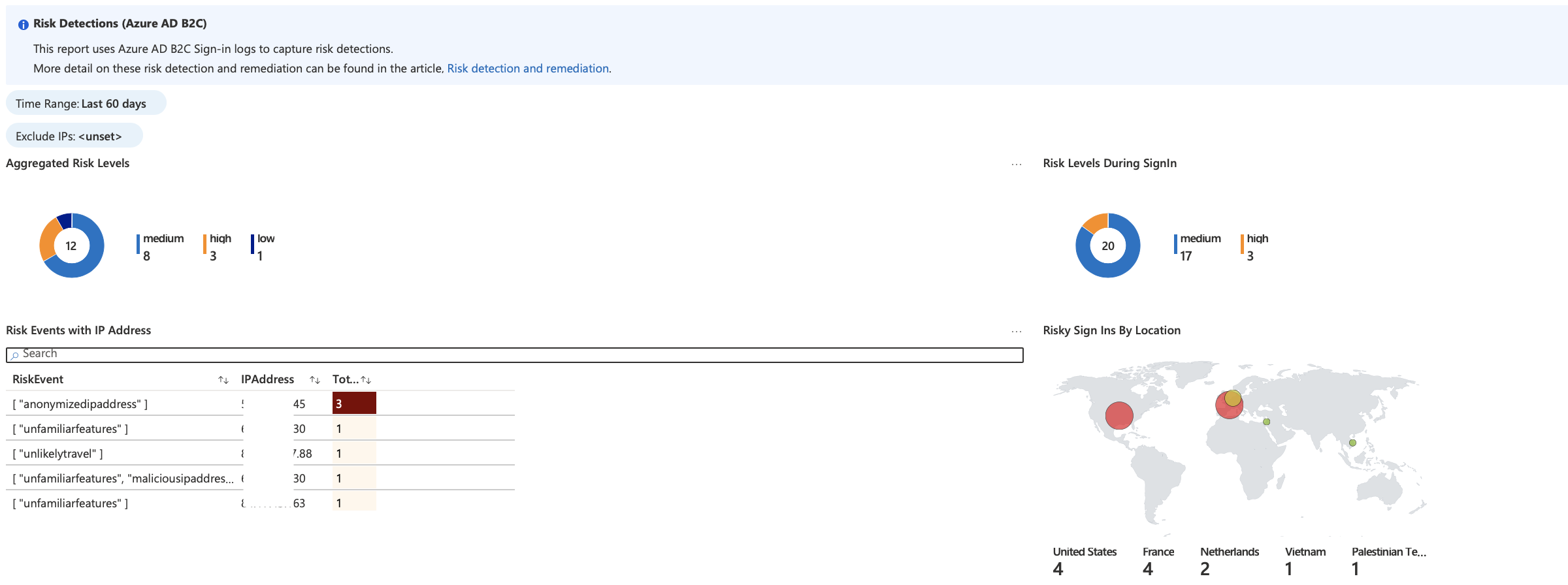
This report uses Azure AD B2C Sign-in logs to capture risk detections. More detail on these risk detections and remediation can be found in the article, Risk detection and remediation.
NOTE: Please note that Azure AD B2C Premium P2 is required for some Identity Protection features and hence the risk detections. Please read about Pricing tier and its influence on risk detections.
-
Aggregated Risk Levels
-
Risks Levels during SignIn
-
Risk Levels by Region
-
Risk Events by IP Address (Filterable)
-
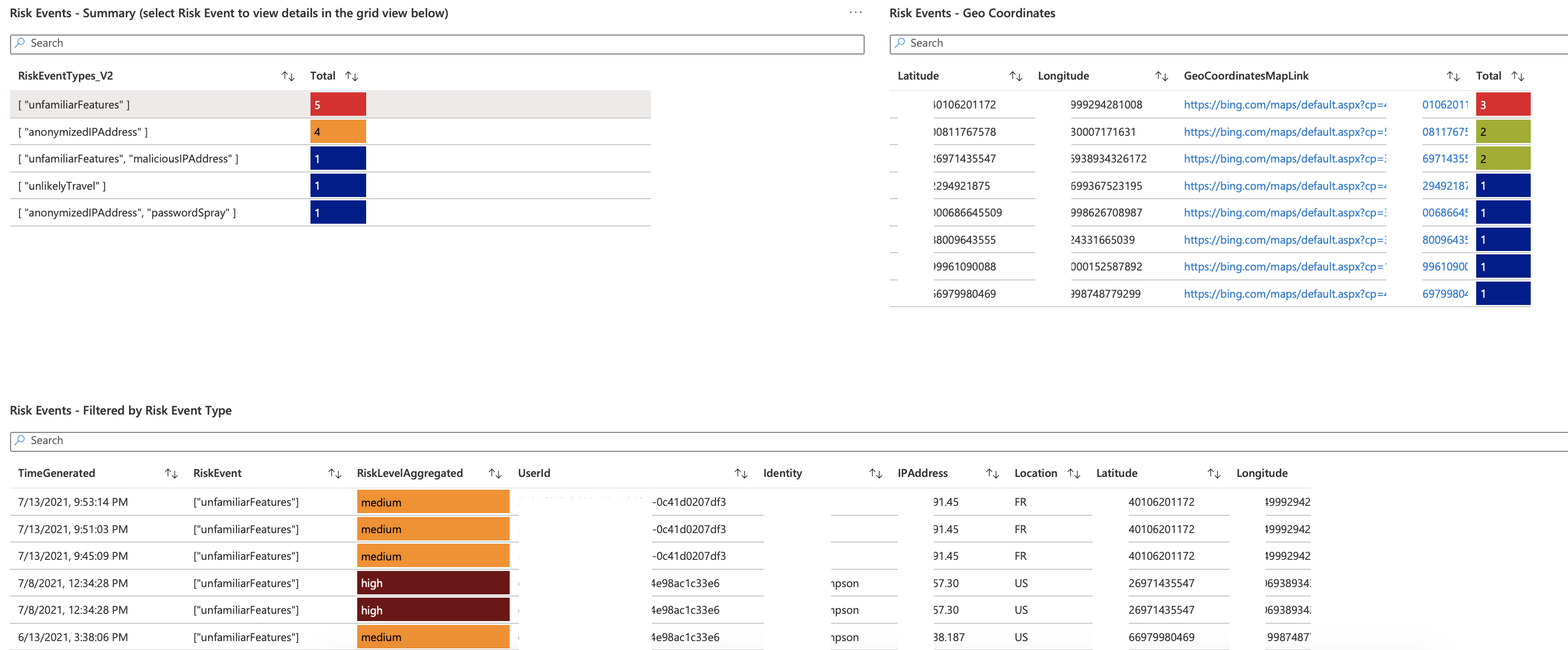
Risk Events by Type (Filterable)
- Risk Events Details (based on selected Risk Type)
-
Risk Events by Geo Coordinates (Filterable)
-
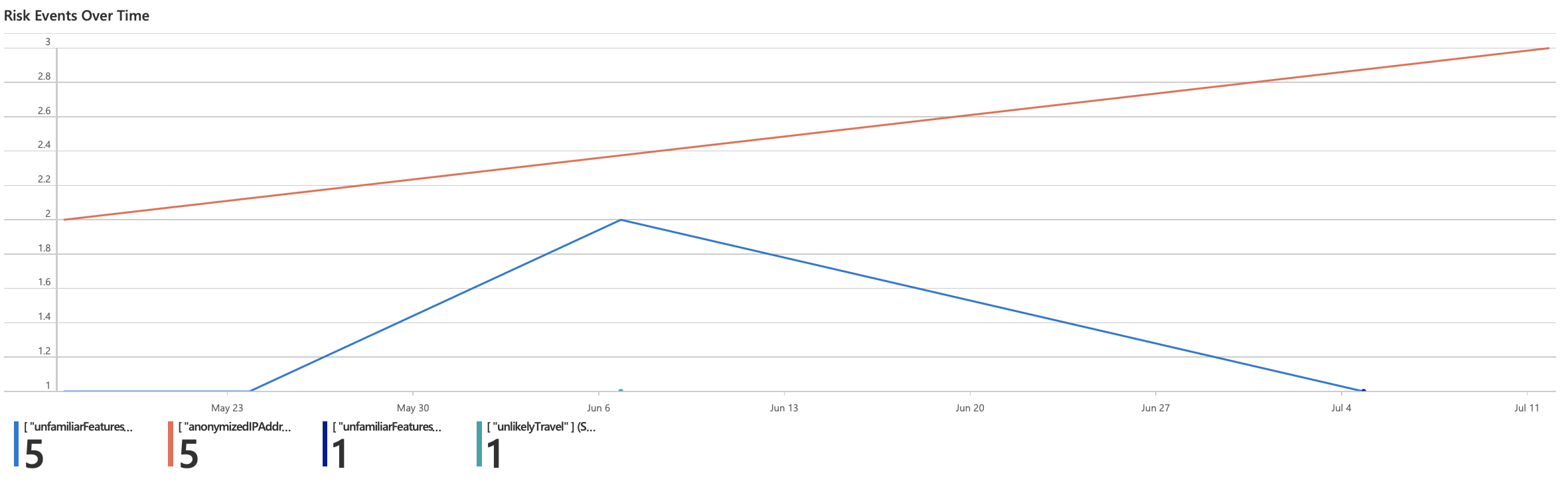
Risks Events Over Time
MFA workbook provides details related to Conditional Access within Azure AD B2C tenant.
NOTE: This report requires Azure AD B2C Conditional Access to be enabled on Azure AD B2C. For more information, please read Add Conditional Access to user flows in Azure Active Directory B2C and Define a Conditional Access technical profile in an Azure Active Directory B2C custom policy
-
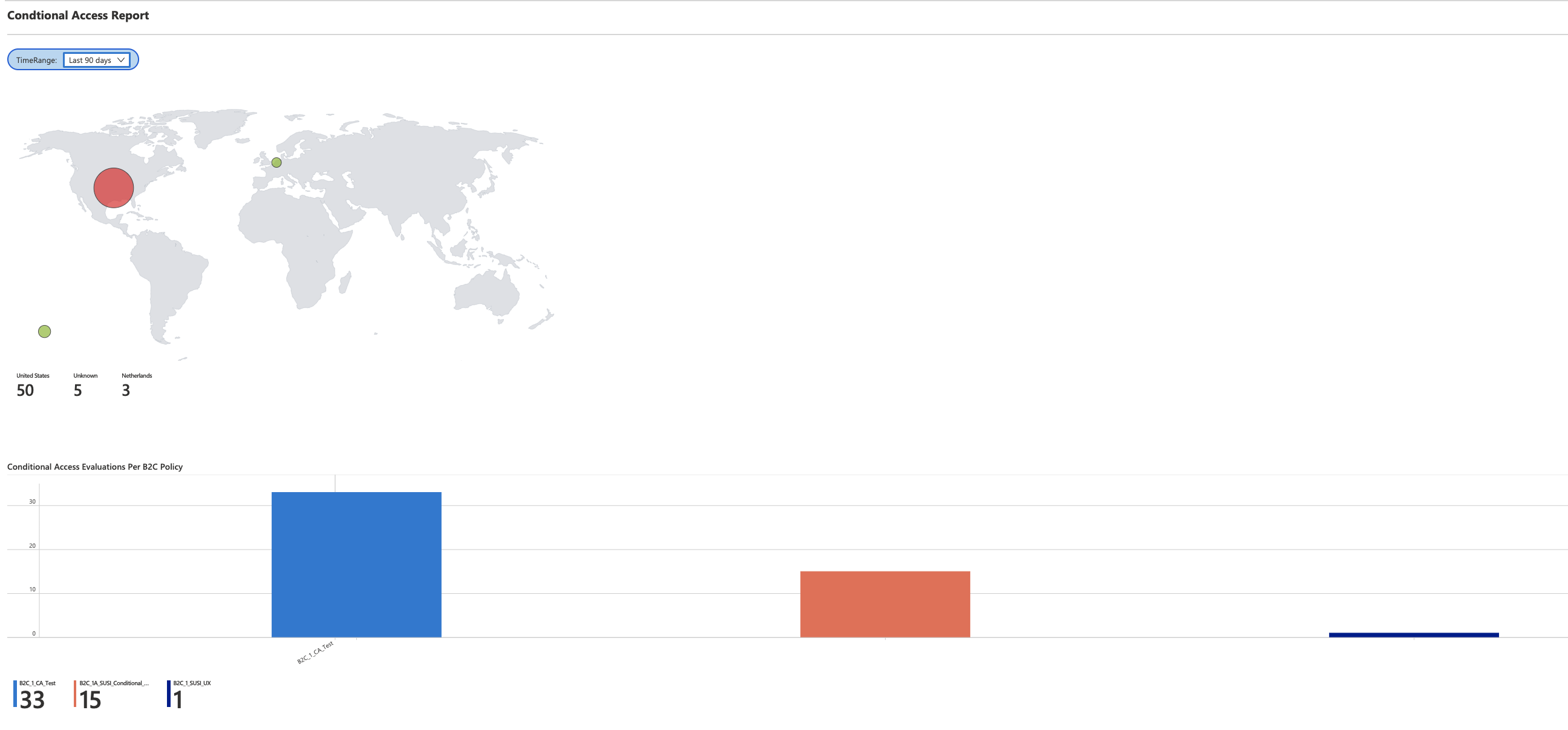
Conditional Access Report
- Location (Based on user request to B2C policy/user flow which results in Conditional Access evaluation)
- Conditional Access Evaluations Per B2C Policy
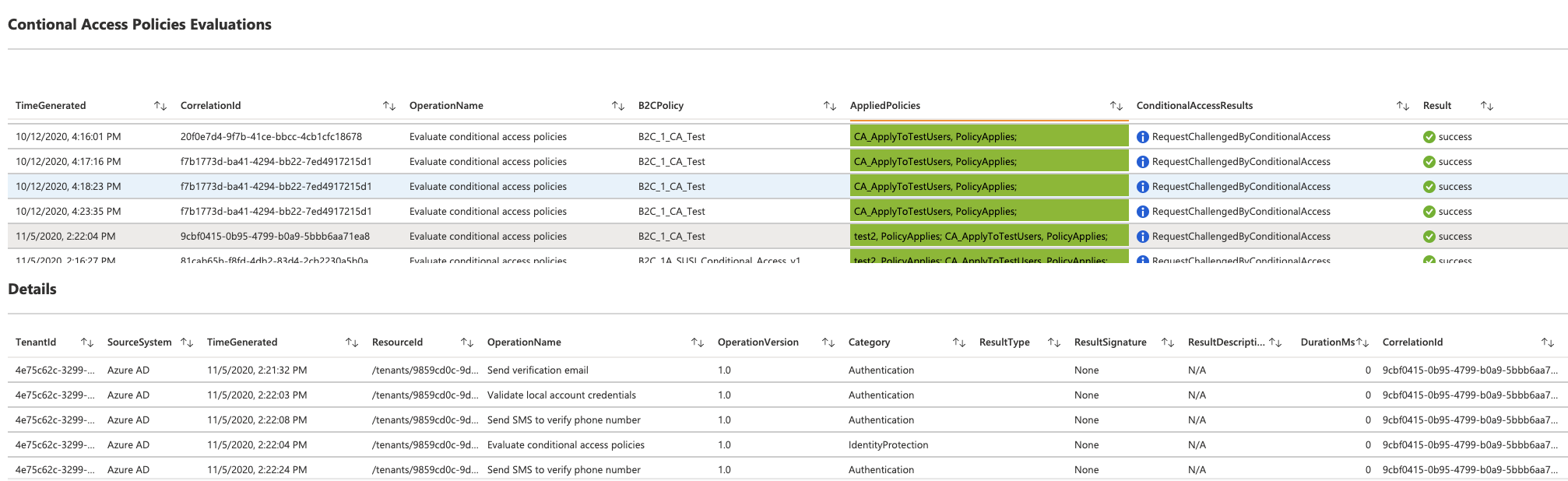
- Conditional Access Evaluations (all relevant operations)
- Details (of a particular Conditional Access Evaluation. Click on a row item within the Conditional Access Evaluation to view an operation details)
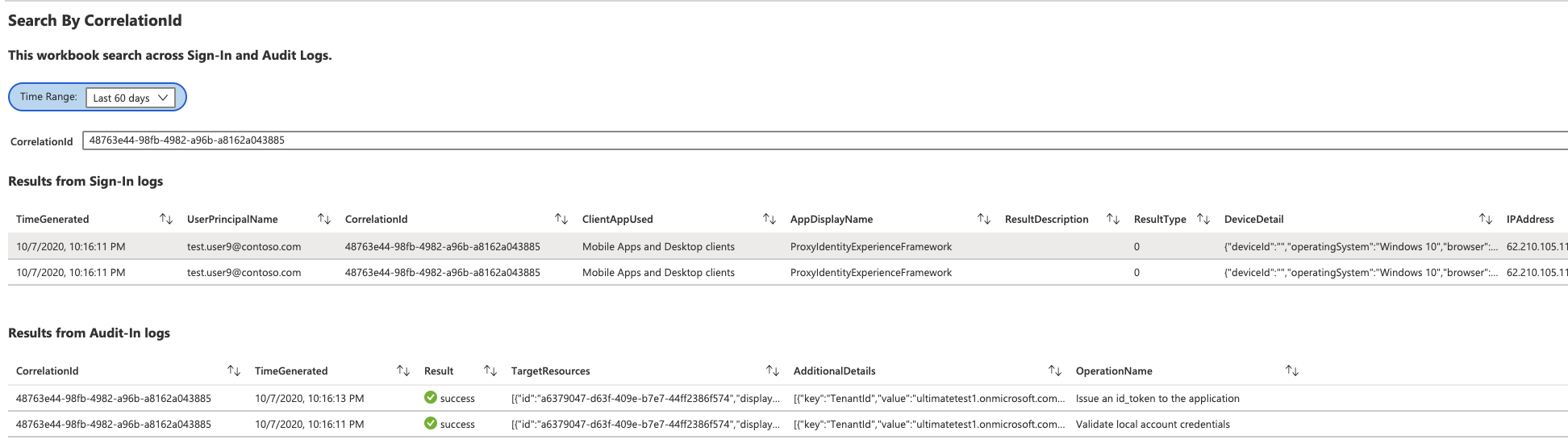
The Search by CorrelationId workbook allows you to search Sign-In and Audit Logs against a particular correlation id. This is helpful when you are trying to troubleshoot a particular issue and want to filter based on a correlation id across both logs.
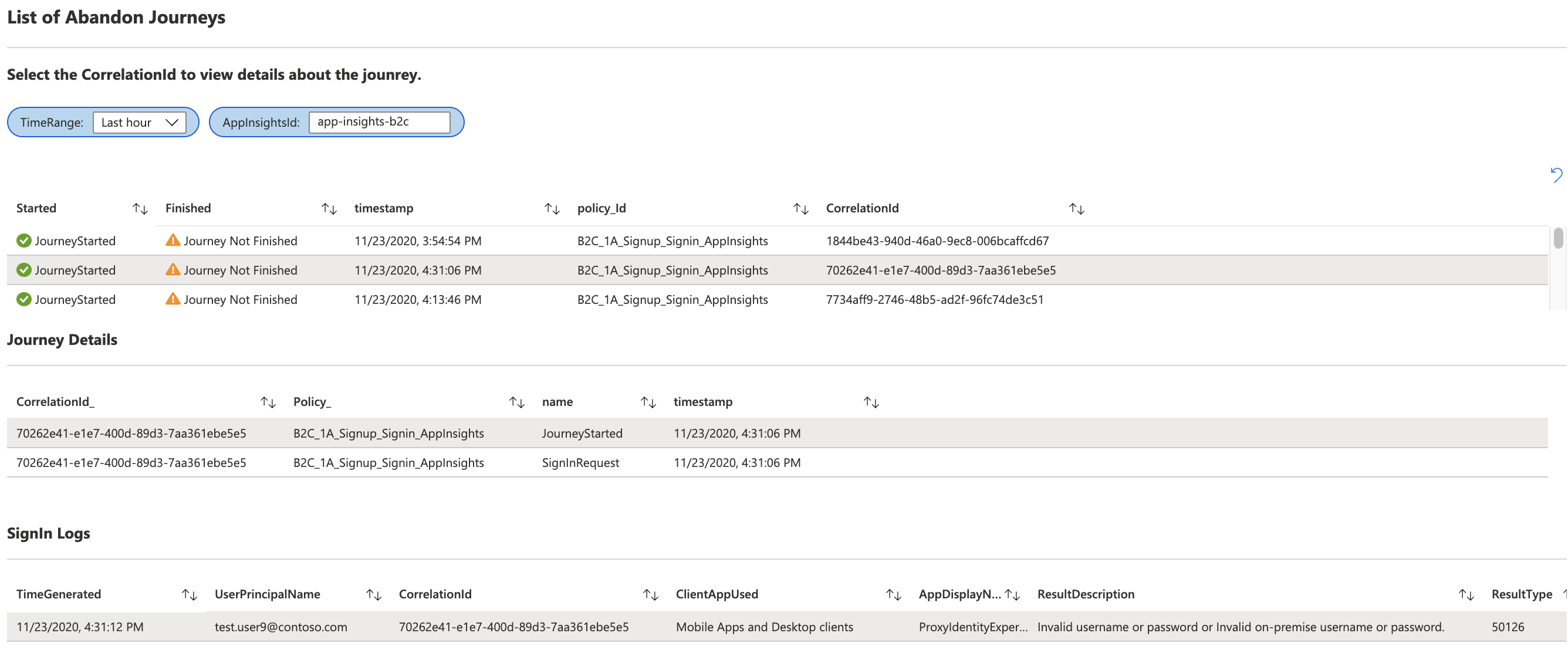
The List of Abandon Journeys workbook allows you to gain insights about user journeys that are started by the user but are not completed. It also allows you to select a particular journey and gather more information from Sign-In and Audit Logs based on the correlationId. The sample Azure AD B2C is available here
Please note that this workbook requires Application Insights to be configured for the Azure AD B2C policy. For more information about configuring Application Insights please read the document Track user behavior in Azure Active Directory B2C using Application Insights.
Please note that AppInsightsId is the name of the Application Insights instance which you have configured within Azure AD B2C policy.
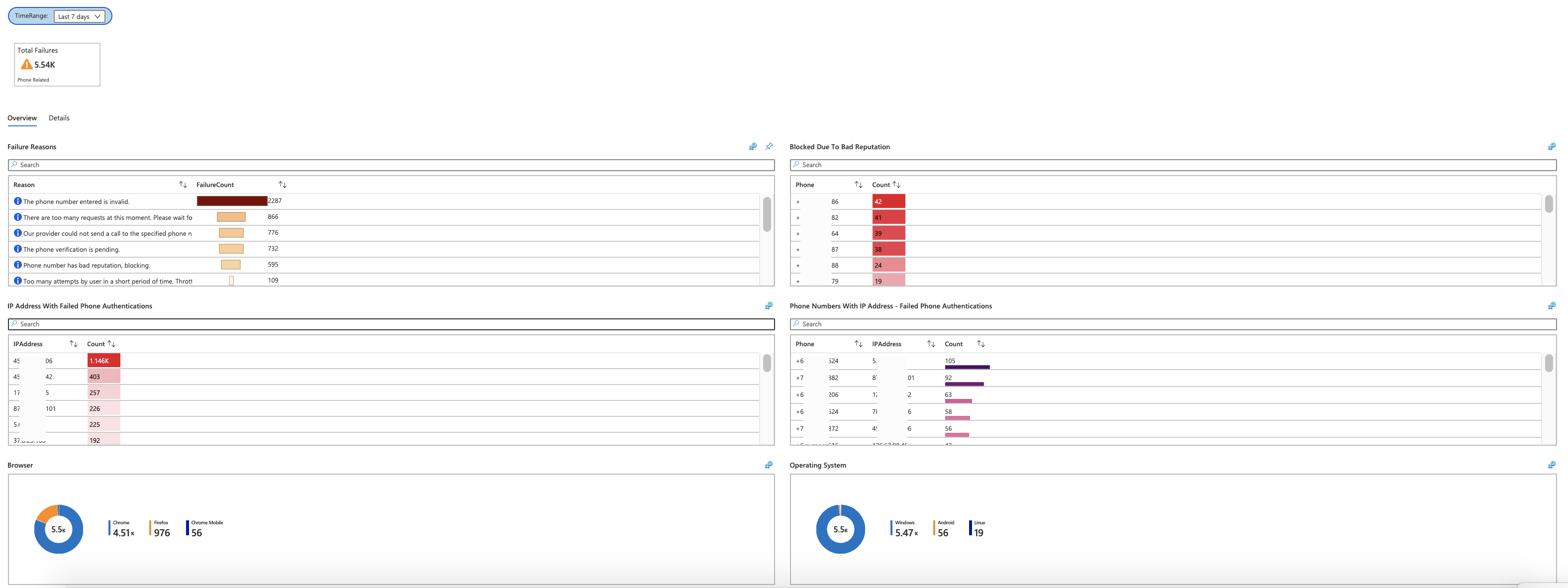
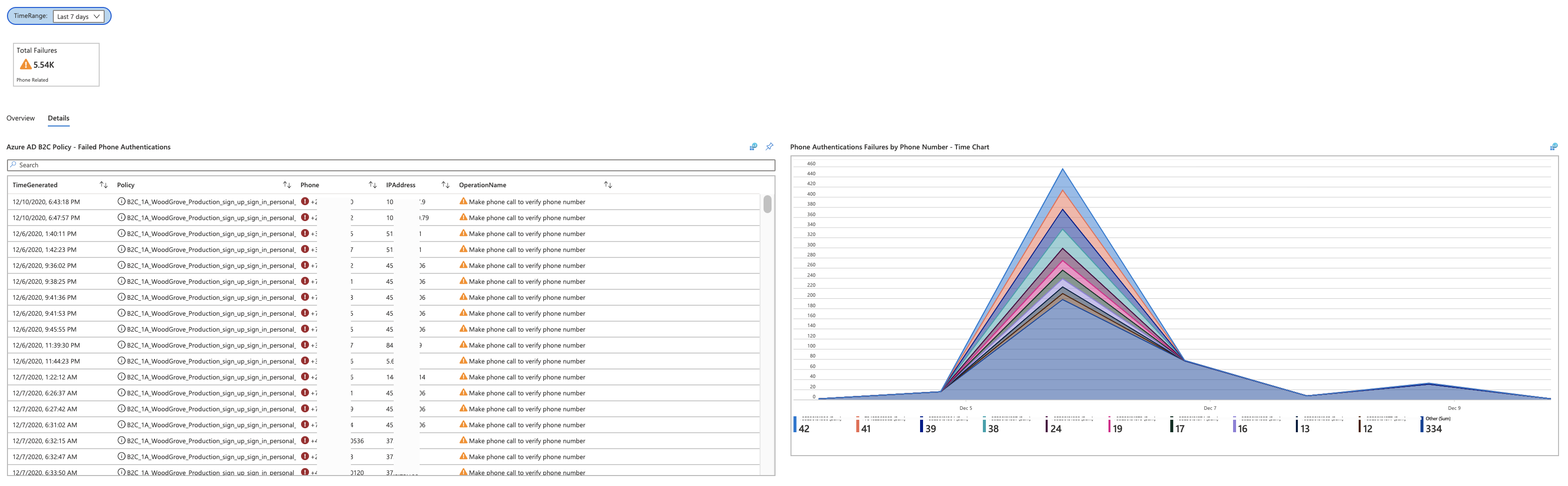
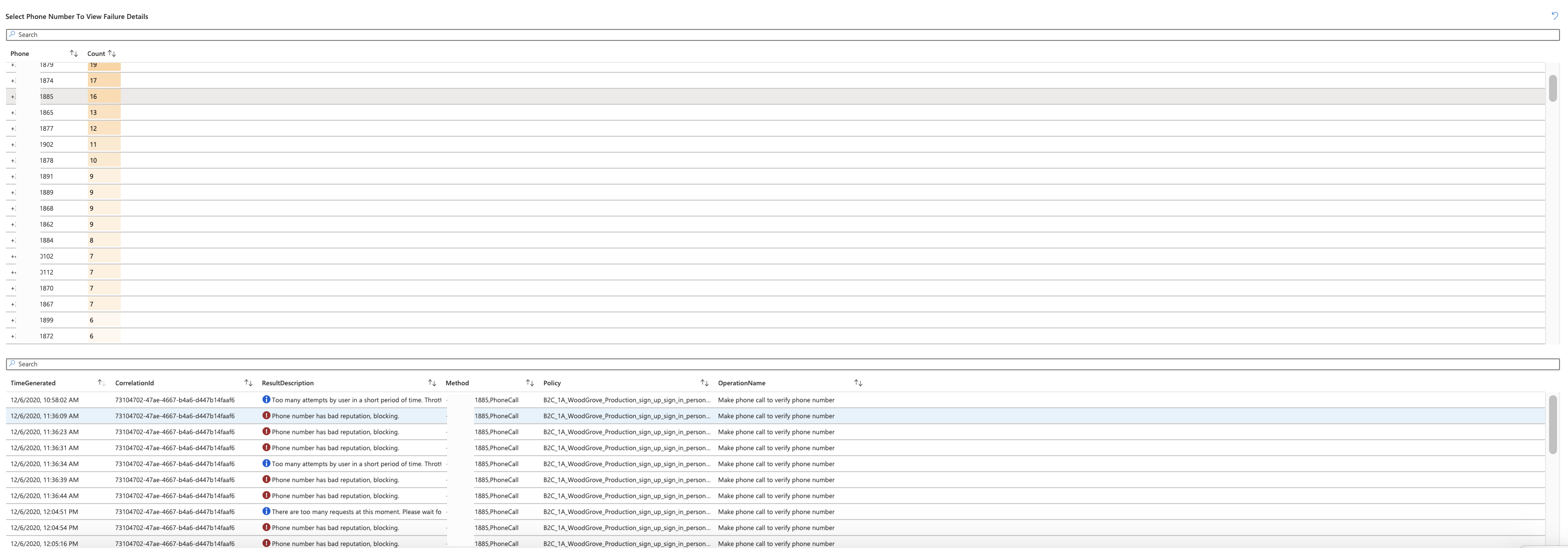
The Phone Authentication Failures workbook allows you to gain insights about phone authentication related failures.
Alerts are created by alert rules in Azure Monitor and can automatically run saved queries or custom log searches at regular intervals. You can create alerts based on specific performance metrics or when certain events are created, absence of an event, or a number of events are created within a particular time window. For example, alerts can be used to notify you when average number of sign-in exceeds a certain threshold. For more information, see Create alerts.
| Name | Deploy |
|---|---|
| User account is sending excessive amount of risky sign-in requests |
Use the following instructions to create a new Azure Alert which will send an email notification whenever there is a 25% drop in the Total Requests compare to previous period. Alert will run every 5 minutes and look for the drop within last 24 hours windows. The alerts are created using Kusto query language.
-
From Log Analytics workspace, select Logs.
-
Create a new Kusto query by using the query below.
let start = ago(24h); let end = now(); let threshold = -25; //25% decrease in total requests. AuditLogs | serialize TimeGenerated, CorrelationId, Result | make-series TotalRequests=dcount(CorrelationId) on TimeGenerated in range(start, end, 1h) | mvexpand TimeGenerated, TotalRequests | serialize TotalRequests, TimeGenerated, TimeGeneratedFormatted=format_datetime(todatetime(TimeGenerated), 'yyyy-M-dd [hh:mm:ss tt]') | project TimeGeneratedFormatted, TotalRequests, PercentageChange= ((toreal(TotalRequests) - toreal(prev(TotalRequests,1)))/toreal(prev(TotalRequests,1)))*100 | order by TimeGeneratedFormatted | where PercentageChange <= threshold
-
Select Run, to test the query. You should see the results if there is a drop of 25% or more in the total requests within the past 24 hours.
-
To create an alert rule based on the query above, use the + New alert rule option available in the toolbar.
-
On the Create a alert rule page, select Condition name
-
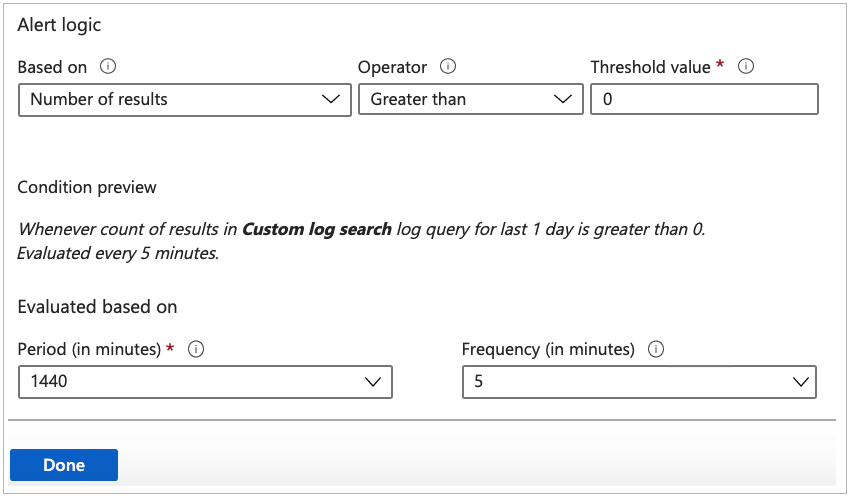
On the Configure signal logic page, set following values and then use Done button to save the changes.
- Alert logic: Set Number of results Greater than 0 .
- Evaluation based on: Select 1440 for Period (in minutes) and 5 for Frequency (in minutes)
After the alert is created, go to Log Analytics workspace and select Alerts. This page displays all the alerts that have been triggered in the duration set by Time range option.
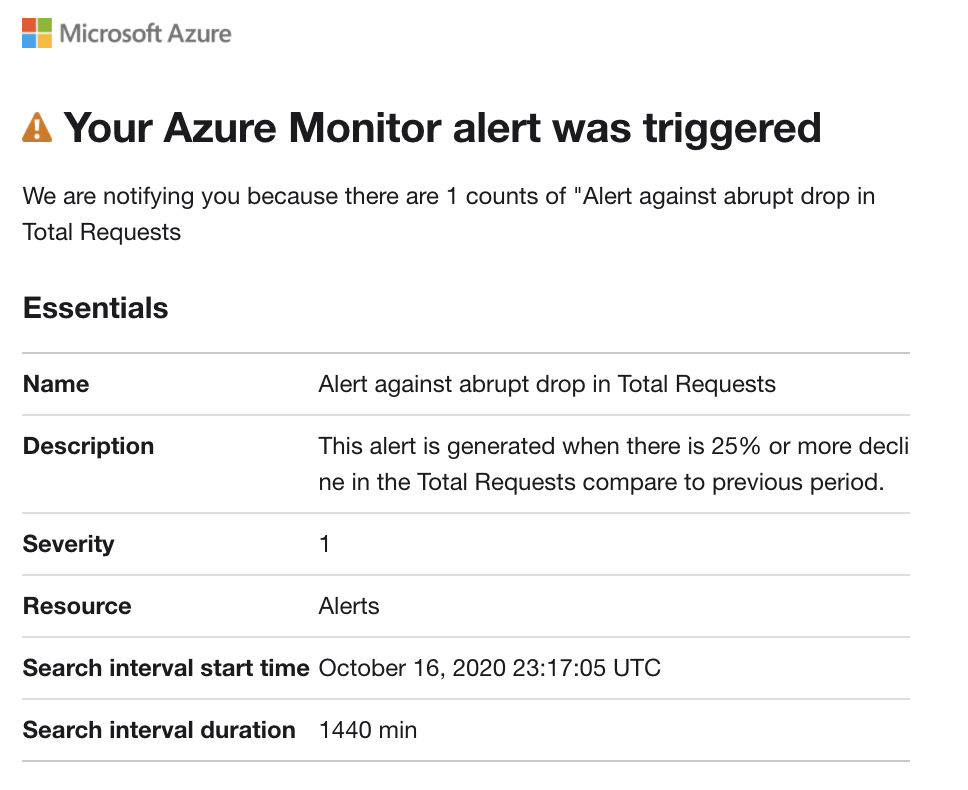
Azure Monitor and Service Health alerts use action groups to notify users that an alert has been triggered. You can include sending a voice call, SMS, email; or triggering various types of automated actions. Follow the guidance Create and manage action groups in the Azure portal
Here is an example of an alert notification email.
-
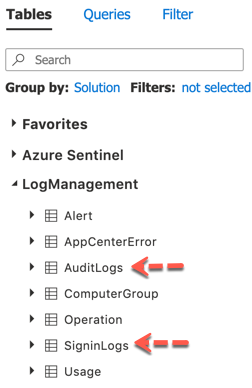
How do I know Azure AD B2C logs are available in Logs Analytics workspace?
Azure AD B2C Audit and Sign-In Logs shows up in the LogManagement console as shown below.
-
Why my reports are not able to show data beyond past 30 days?
By default Logs Analytics workspace only retain data for 30 days. You can change the retention period by using the instructions provided here
-
Can I display application name instead of application object id in the reports?
Currently, application object id is the only value that is available within the Azure AD B2C logs.