Hash CrackerIntroductionA hash cracker can be considered as a sophisticated program that usually, works on an extensive database of hashes. It can guess many millions or billions of possible passwords and automatically compare the results with an entire collection of stolen hashed passwords to find matches. Hashcat is a popular and effective password recovery tool (or password cracking utility) specifically designed to break passwords or key representations. It is so effective that it can also break one of the most complex (or strong) passwords, due to which it is widely used by both criminals and penetration testers for different purposes. In short, we can say that Hashcat is one of the world's fastest CPU and GPU password recovery tools, as claimed in its documentation. Usually, password representations are specifically associated with several types of hash keys such as NTMLv2, NTMLv1, SHA, MD5, RipeMD, etc. These can be easily understood as a mathematical function that is very easy to perform, still very typical to reverse engineer. How it works?In general, hashcat converts understandable data into a garbled state that is usually a random fixed length-sized string. However, hashes do not allow users to decrypt the encrypted data with a specific key, as allowed by the standard encryption protocols. Hashcat uses pre-computed rainbow tables, dictionaries, and sometimes brute-force attacks to discover an efficient and effective way to break passwords. In order to crack a hash password, it enables the cracking of a particular encrypted key in several ways combined with versatility and speed. Nowadays, passwords are no longer stored in the form of plain text. Instead of it, they are now encrypted using the one-way function known as the hash. To break a simple password like " password1 " into a hash is not a big deal. It has the ability to crack common passwords in no time. Although, password cracking is an entirely different thing form guessing the credentials of a web login, which offers a very limited number of guesses before locking your account. Instead, one who has successfully gained access to a system with encrypted passwords (hashes) will typically try to crack those hashes or encrypted information to recover those passwords. What if all we have is a hash password? A brute-force attack may be computationally possible to reverse the hash function and recover the password, but this process can last forever (or until the user dies). However, some other efficient and effective ways are also available to reverse the hash and recover the original password. Uses of HashcatCracking passwords has many legitimate uses, besides the apparent criminal and espionage ones. A sysadmin may wish to pre-emptively check the security of user passwords. If hashcat can crack them, so can an attacker. Penetration testers on engagement will frequently find themselves cracking stolen password hashes to move laterally inside a network or escalate privileges to an admin user. How to crack hashes?The very first step to crack hashes is to try to guess the password. Each attempt is hashed and compared to the actual hashed value to see if both are the same, but this is a time-consuming process and lasts a long time. However, there are many other ways to boost this process. The dictionary, brute-force attacks, etc., are the most standard ways of predicting passwords. These methods usually use a file which contains several common passwords, words, phrases, and several other strings that can be used as viable password. 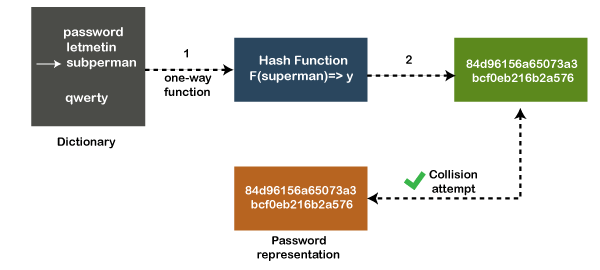 Note: One important thing to keep in mind that, at any cost, there is no guaranteed way to avoid brute force attacks and dictionary attacks.Let's see some other approaches that are used to crack the passwords
Typically, hashes are pre-computed from the dictionary, then stored in a look table structure with their respective passwords.
This type of attack allows many cyber attackers to implement a dictionary or brute-force attack on more than one hash simultaneously without requiring a pre-calculated lookup table.
Rainbow tables are a type of time-memory technique. These are similar to somewhat lookup tables, except that it sacrifices the hash cracking speed in order to create small lookup tables.
It is also a type of technique in which hashes are randomized by appending a random string, known as the "salt." It is typically applied to the passwords before the hashing. How to crack the hashes with Hashcat?Usually, Hashcat is come pre-installed on most Linux distributions and especially on Kali Linux. If it not installed on your system, you can download it form the given link: https://hashcat.net/hashcat/ Now let's see how to crack the hashes with Hashcat. To continue this demonstration we will create some hashes using the mbd5 algorithm and stored them into .txt file. Creating a dictionary with MBD5 hashesWe will create multiple hash entries containing several passwords by using the following given commands: Syntax echo -n "Password" | md5sum | tr -d' ' -f1 >> hashes.txt echo -n "HELLO" | md5sum | tr -d' ' -f1 >> hashes.txt echo -n "MYSECRET" | md5sum | tr -d' ' -f1 >> hashes.txt echo -n "Test1234" | md5sum | tr -d' ' -f1 >> hashes.txt echo -n "P455w0rd" | md5sum | tr -d' ' -f1 >> hashes.txt echo -n "welcome" | md5sum | tr -d' ' -f1 >> hashes.txt echo -n "abc1234" | md5sum | tr -d' ' -f1 >> hashes.txt They will then be stored to the specified "hashes.txt" file. Each command should be executed individually in the terminal, as shown below:  Explanation of the command: In the above command, echo is used to write or print, the -n option removes the new line added to the end of "Password." This is important as we don't want the newline characters to be hashed with our password. The part <cut -d' '-f1>removes any characters that are a space or hyphen from the output. Check password hashes Here, we will check the password hashes are successfully hashed or not. To check the password hashes, all we need to do is type the following command in the terminal. Command: cat hashes.txt Once the above-given command is executed, we may get a similar output as given below:  Explanation of the command The cat command is used to view contain of the specified file. Starting Hashcat in Kali LinuxNow, let's start the hash cat tool. To start or access the Hashcat tool, you can follow the following given instructions: 1. Open the terminal by pressing Ctrl+ Alt +T on the keyboard.  2. Once the terminal gets open, type the following command and press enter: Command hashcat -h Output  The options such as -m (or the hash type) and -a (or attack mode) are some of the most important options of hashcat. Usually, we required both of these options in almost all password cracking attempts while using the Hashcat. The hashcat has specifically designed rules to use on a wordlist file, and the character list can be customized to crack the password(s). Additionally, Hashcat provides numerous options for password hashes that can be cracked as showed in the screenshot given-below:  Specifying the world ListKali Linux comes with a vast collection of word lists that derives by default with it (or built right into it). To locate or access these word lists, you can use the following command to help you find out the all built-in word lists available in the system. Command locate wordlists Output  Note: In this demonstration, we will specifically use the "online broute" word list that we have downloaded from the "https://weakpass.com/." We can also use any of the built-in wordlists that comes pre-installed in Linux, such as the "rockyou." Now, without wasting much of your precious time, let's jump to this tutorial's next most exciting step, which is cracking the hashes: Cracking the hashesTo begin cracking the hashes, type the following given command in the terminal and press enter as shown below: Syntax $ hashcat -m 0 -a 0 -o cracked.txt hashes.txt online_broute --force --show Output 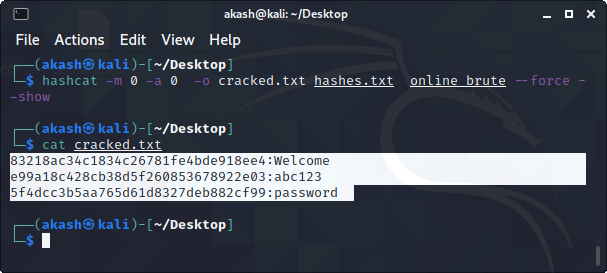 Explanation of the above command
Results Finally, we have cracked almost all of the target hashes that were initially proposed. You can view them anytime by opening the output "cracked.txt" file.  These types of passwords are easily cracked, and it does not take much effort or time to crack them, as they are weak passwords. It is important to choose a complex password because the simpler the password is, the easier it to break. Thus, make sure that you always choose a long and complex password and try to avoid using personal information. It is also important to constantly change your passwords on a small period of time and never reuse the old passwords. Additionally, there are some GUI that make hashcat easy to use. Hashview is one of the projects. Next TopicNodemon |