Ingress Nginx + Cloudflare: The Bouncer Your Kubernetes Needs"
Alright, folks. If you're here, it's probably because you're tired of random strangers pinging your Kubernetes cluster like it's an open bar. Today, we're going to lock that sucker down using Ingress Nginx with Cloudflare's Origin SSL/TLS. Think of it like hiring a bouncer for your app—no entry unless you're on the guest list. And the only VIP here? Cloudflare.
So, grab your coffee (or Red Bull), put on your debugging hat, and let's get secure.
What's the Game Plan?
Picture this: your users send a request, it hits Cloudflare, which then forwards it to your Kubernetes cluster. But how do you know Cloudflare's being honest? What if it's really some sketchy bot in a trench coat? That's where Cloudflare Origin SSL/TLS comes in. This setup ensures only traffic coming from legit Cloudflare servers reaches your cluster.
Here's the traffic flow:
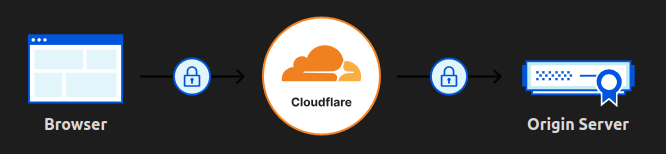
Browser <-> Cloudflare <-> Your Kubernetes Cluster (Ingress Nginx)
In a nutshell: The browser connects to Cloudflare, Cloudflare connects to your origin server (the Ingress controller), and everything is wrapped up in a warm, cozy layer of encryption.
Prerequisites
Before you start, make sure you have the following:
- A Kubernetes cluster running somewhere in the cloud (or your basement, we don't judge).
- Helm installed on your system.
- Ingress-Nginx running on your cluster
- A domain managed by Cloudflare.
- Some patience, because Kubernetes loves to test your resilience.
Step 1: Getting Cloudflare to Play Nice
First, we need to set up Cloudflare so it will only allow traffic to and from your Kubernetes cluster. Think of it like handing out exclusive invites to your secret club.
Creating an Origin SSL Certificate
- Log in to your Cloudflare account (if you forgot your password, good luck).
- Go to SSL/TLS -> Origin Server.
- Enable Authenticated Origin Pulls. This ensures only Cloudflare's servers can reach your origin.
- Click Create Certificate.
- Select Generate private key and CSR with Cloudflare.
- Choose RSA (2048) because, well, it's the Toyota Camry of encryption: solid and dependable.
- Enter your domain (
myapp.example.com). - Set the validity period to something ridiculous like 15 years (if your app is still running by then, congrats).
- You'll see two text boxes:
- Origin Certificate -> Save this to a file called
cf.crt. - Private Key -> Save this to a file called
cf.key.
- Origin Certificate -> Save this to a file called
Pro Tip: Treat these files like your Netflix password. Don't share them, don't commit them to GitHub, and don't forget where you saved them.
Enable Full (Strict) SSL Mode
- Head over to SSL/TLS -> Overview.
- Set your SSL mode to Full (strict).
This ensures Cloudflare only talks to your server if it has a valid certificate. No posers allowed.
Step 2: Download the Cloudflare Origin CA Certificate
We need to grab Cloudflare's root certificate to validate incoming traffic. Think of it like checking ID at the door.
wget https://developers.cloudflare.com/ssl/static/authenticated_origin_pull_ca.pemThis certificate will help Ingress Nginx verify that requests are really coming from Cloudflare and not some random bot trying to crash your party.

iykyk.
Step 3: Store Certificates as Kubernetes Secrets
Now, it's time to securely stash those certificates in Kubernetes. Because leaving them lying around on your disk is like leaving your car unlocked in a sketchy neighborhood.
Create a Secret for Cloudflare CA
this should create the secret in default namespace, allowing reusability of the secret into different namespaces
kubectl create secret generic cloudflare-tls-secret \
--from-file=./authenticated_origin_pull_ca.pemCreate a Secret for Your Origin SSL Certificate
namespace needs to reflect where your host is cruising
kubectl create secret tls cloudflare-origin-server \
-n <namespace> \
--key cf.key --cert cf.crtNote: If Kubernetes throws a tantrum here, double-check those file paths. And maybe give your cluster a pep talk.
Step 4: Configure Ingress Nginx to Play by the Rules
Now comes the part where we tell your hosts' Ingress Nginx to only trust traffic coming from Cloudflare. It's like a velvet rope at a club—no entry without the right credentials. Assuming the file is called ingress.yml:
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: my-app-ingress
namespace: <namespace>
annotations:
# Annotations that do the magic
nginx.ingress.kubernetes.io/auth-tls-pass-certificate-to-upstream: 'true'
nginx.ingress.kubernetes.io/auth-tls-secret: default/cloudflare-tls-secret
nginx.ingress.kubernetes.io/auth-tls-verify-client: 'on'
nginx.ingress.kubernetes.io/auth-tls-verify-depth: '1'
nginx.ingress.kubernetes.io/ssl-redirect: 'true'
nginx.ingress.kubernetes.io/force-ssl-redirect: 'true'
spec:
ingressClassName: nginx
rules:
- host: myapp.example.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: my-service
port:
number: 80
tls:
- hosts:
- myapp.example.com
secretName: cloudflare-origin-server- Apply the Configuration
kubectl apply -f ingress.yaml -n <namespace>If everything works, Kubernetes will do its magic. If not, time to check logs and whisper sweet nothings to your cluster.
Step 5: Update Your Cloudflare DNS
Almost there, folks. We just need to point Cloudflare to the right place.
- Go to DNS in your Cloudflare dashboard.
- Create an A record:
Type: AName: myapp.example.comContent: The external IP of your Ingress Nginx LoadBalancer. You can find it with:
shkubectl get svc -n ingress-nginx - Proxy status: Keep it Proxied (orange cloud). This ensures all traffic is routed through Cloudflare.
Step 6: Test Your Setup
Moment of truth. Let's see if your configuration actually works:
curl -v https://myapp.example.comIf everything went well, you should see a successful SSL handshake and the response from your app. If not, Kubernetes has once again decided to test your sanity.
Common Issues & Fixes
- SSL Handshake Failures: Check if your Cloudflare SSL mode is set to Full (strict).
- 404 Errors: Make sure the Ingress host matches your Cloudflare DNS entry exactly. No typos allowed.
- Infinite Redirects: Verify
nginx.ingress.kubernetes.io/force-ssl-redirectis set correctly.
Wrapping Up

And there you have it. You've successfully set up Ingress Nginx with Cloudflare Origin SSL/TLS. Your Kubernetes cluster is now guarded like Fort Knox. So, go ahead and kick back with a cold beverage—you've earned it. 🍺
But remember: Kubernetes is like a cat—it might act nice today, but it's always plotting something. Cheers! 🎉