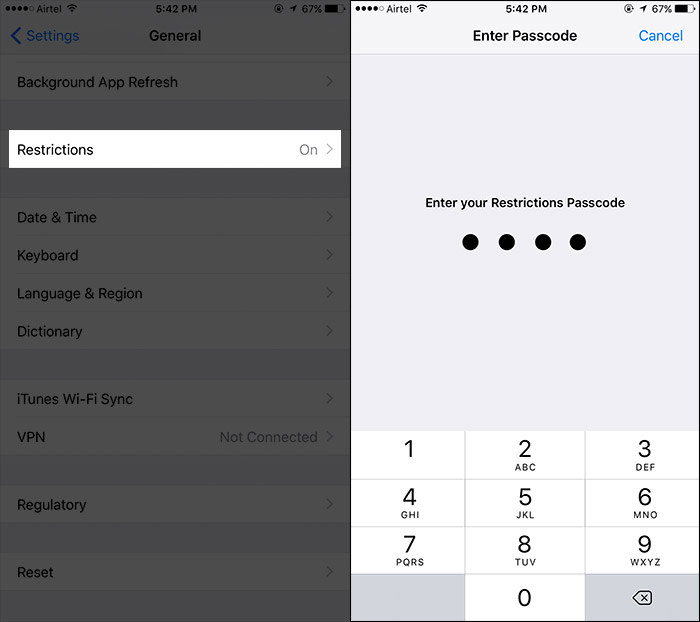
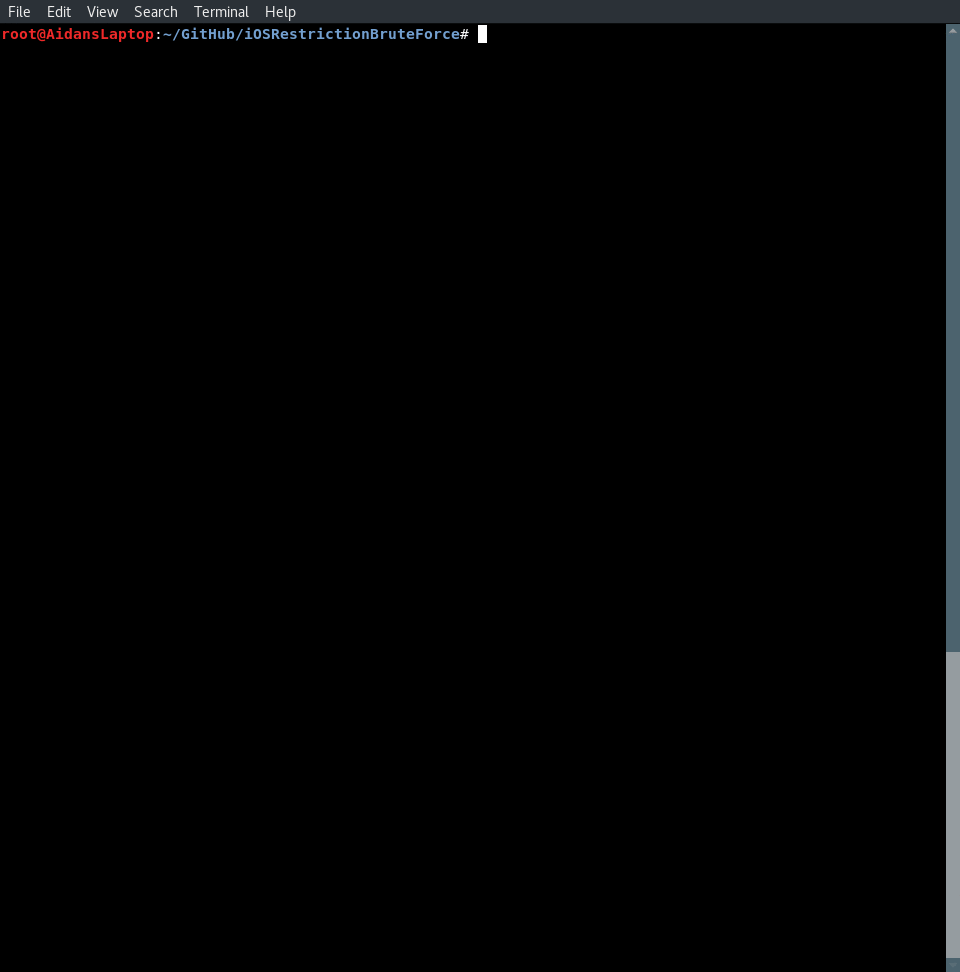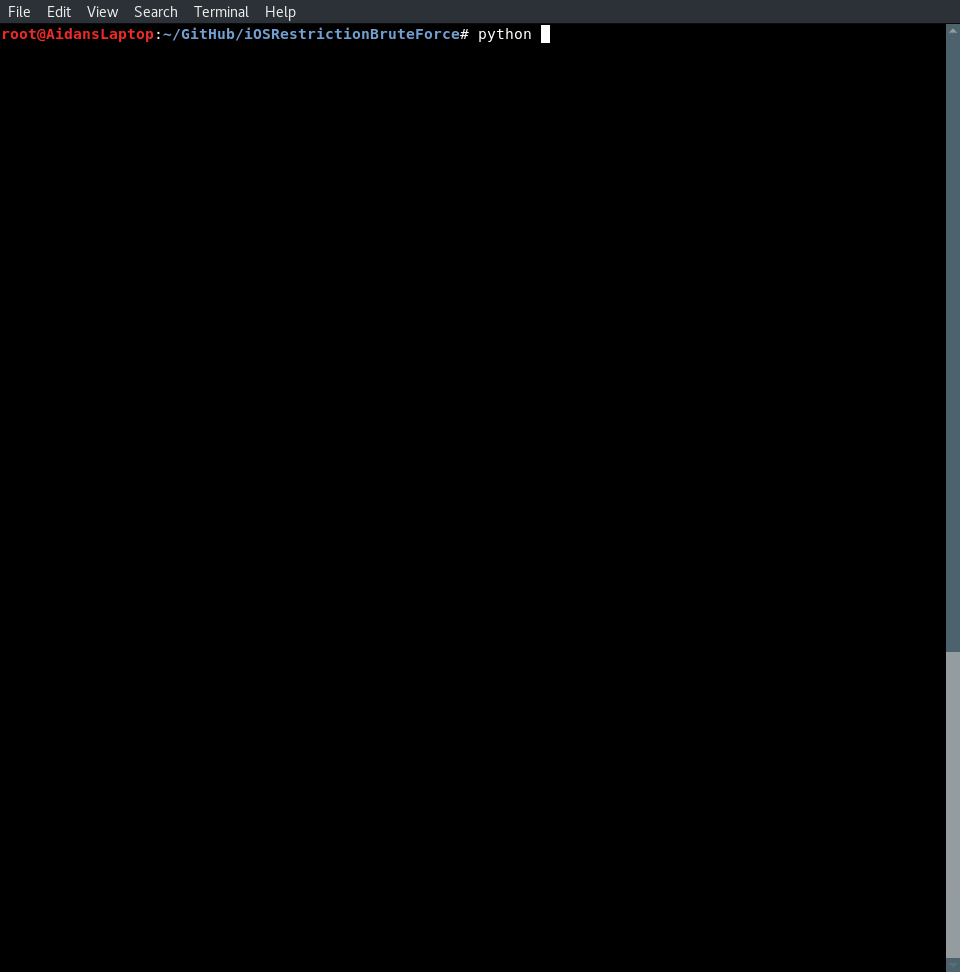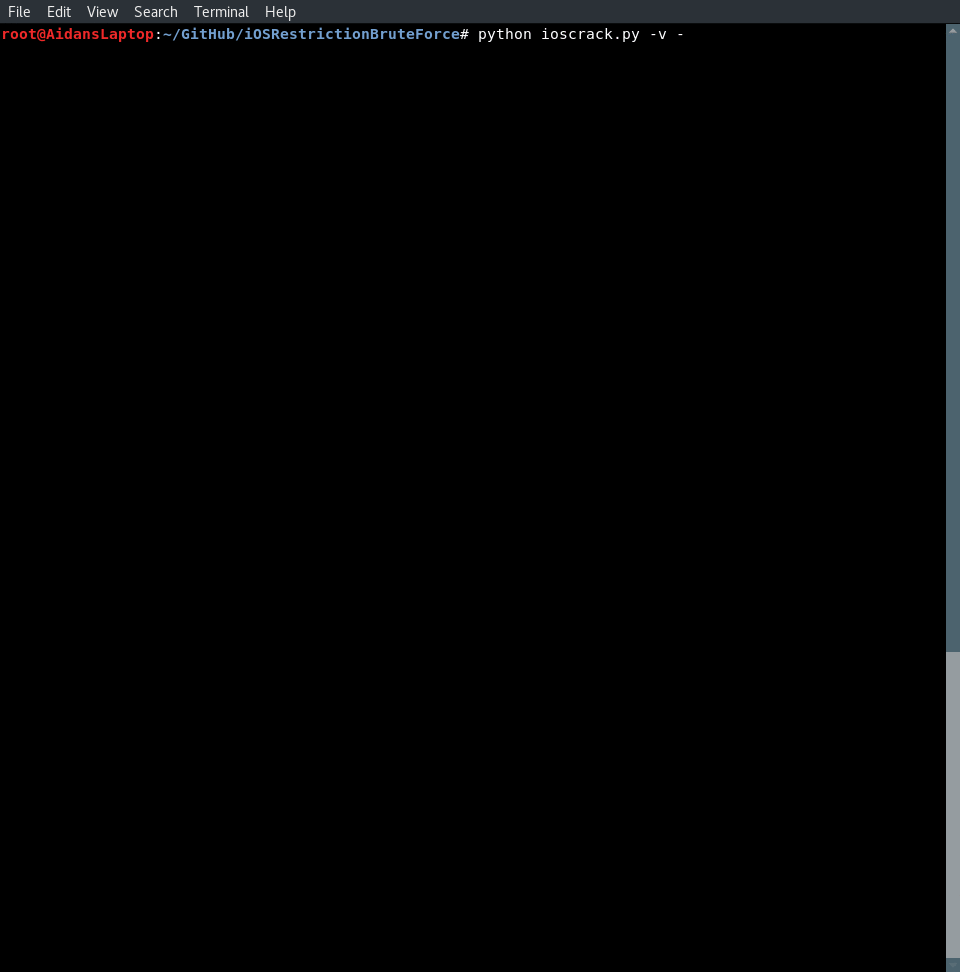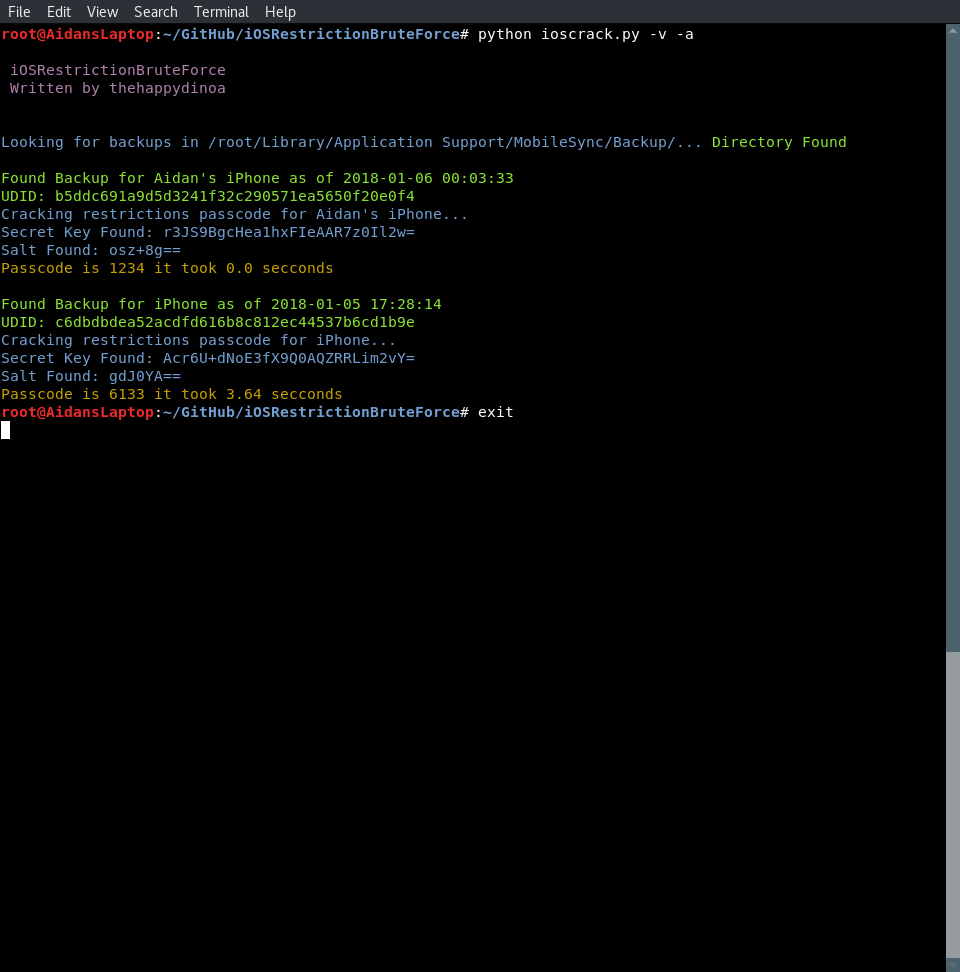
This version of the application is written in Python, which is used to crack the restriction passcode of an iPhone/iPad takes advantage of a flaw in unencrypted backups allowing the hash and salt to be discovered.
This has been tested with Python 2.7
Requires Passlib Install with pip install passlib
- Clone repository
git clone https://github.com/thehappydinoa/iOSRestrictionBruteForce && cd iOSRestrictionBruteForce-
Make sure to use iTunes or libimobiledevice to backup the iOS device to computer
-
Run
ioscrack.pywith the webserver option
python ioscrack.py -w
usage: iOSCrack.py [-h] [-v] [-a] [-c] [-w] [-b folder]
a script which is used to crack the restriction passcode of an iPhone/iPad
through a flaw in unencrypted backups allowing the hash and salt to be
discovered
optional arguments:
-h, --help show this help message and exit
-v, --verbose increase output verbosity
-a, --automatically automatically finds and cracks hashes
-c, --cli prompts user for input
-w, --webserver creates webserver running flask
-b folder, --backup folder
where backups are locatedDone by using the pbkdf2 hash with the Passlib python module
-
Trys the top 20 four-digit pins
-
Trys birthdays between 1900-2017
-
Brute force pins from 1 to 9999
-
Encrpyt backups
-
Backup only on trusted computers
Best ways to contribute
- Star it on GitHub - if you use it and like it please at least star it :)
- Promote
- Open issues
- Submit fixes and/or improvements with Pull Requests
Like the project? Please support to ensure continued development going forward: