API hooking in Windows, calls to these APIs are intercepted, allowing them to be monitored, modified or redirected. This is done by inserting intermediate code (the "hook") between the function call and its actual execution. When an application calls an API function, the hook is triggered first, allowing the operation to be manipulated.
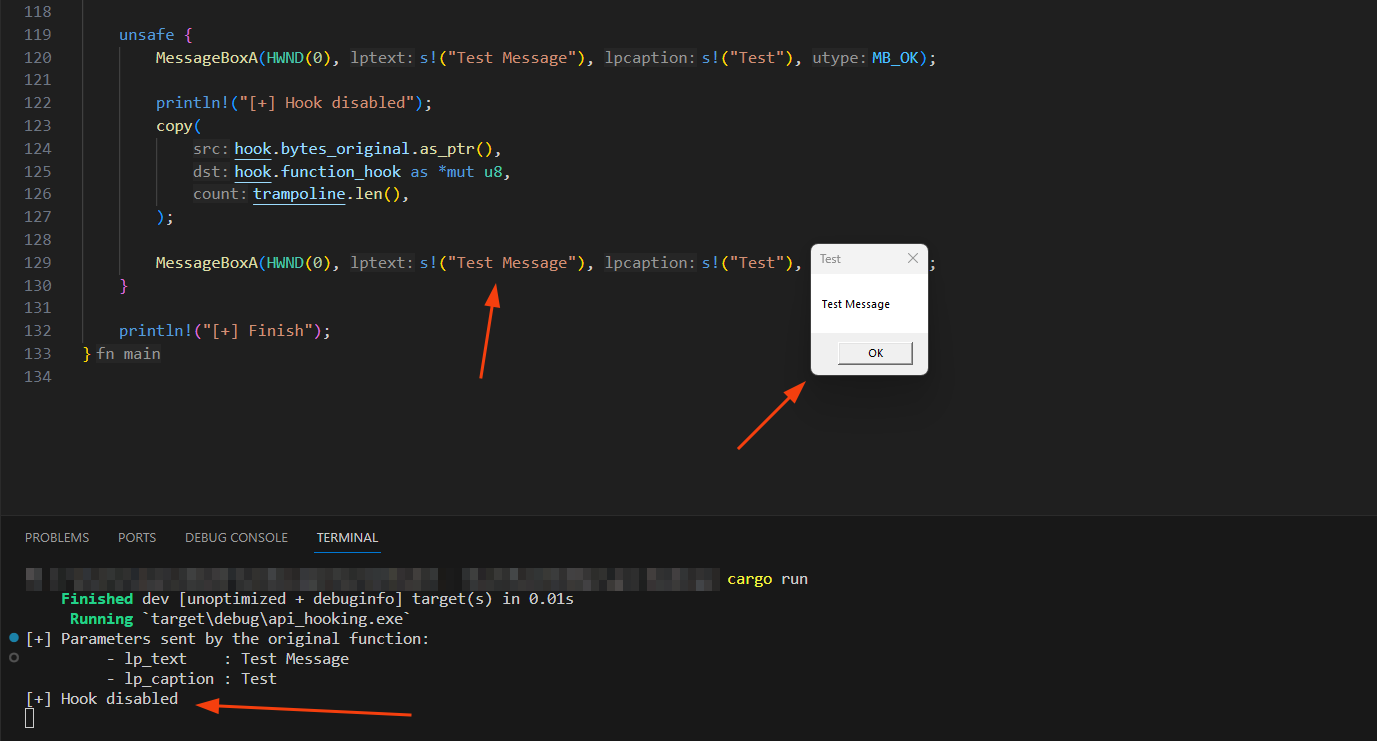
Performing the API Hooking technique in MessageBoxA:

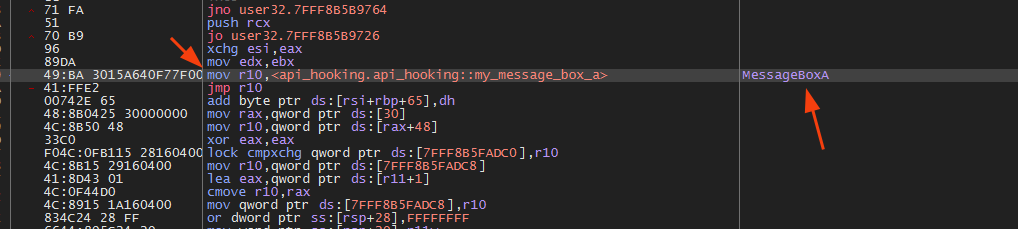
Checking the debugger for the change:
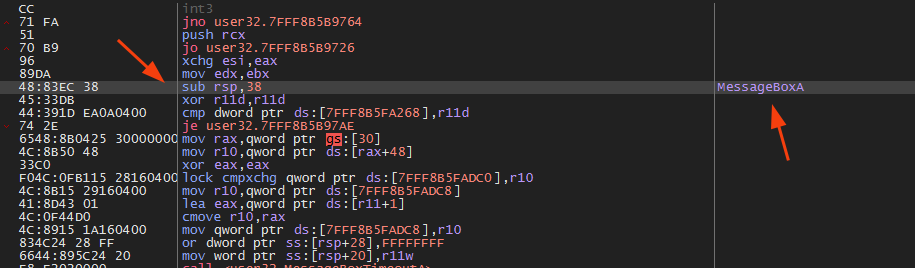
Checking the debugger when disabling the hook:
You can run with cargo run or the compiled binary directly:
cargo runtarget/release/api_hooking.exe