-
Notifications
You must be signed in to change notification settings - Fork 22
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
CW017 research #21
Comments
|
👍 Thanks. Good idea keeping tracking in a separate thread (that's a pain in the ass to expand all the comments in the main) |
|
@parkerlreed yes :) similar but different hardware. The uart pads will likely be on the other side by removing the 4 silver colored screws |
|
Trying the 2.7.x files from #11 here's what I observe
2.9.x on my first try resulted in a corrupted MBR which made me think it worked but was the same result (and subsequent tries the MBR stays in tact) |
|
Serial pins should be the 4 pads on the bottom left of the picture you posted. |
|
You can use the screw hole as ground and test which is ground from the pads, then test which is 3.3v using pin 8 of the flash chip. Or you can just solder wires and swap them until you find what is rx, tx and ground (no need to connect 3.3v). Just make sure you don’t pull hard on wiring after soldering or they will come right out of the board. |
|
I tried zero'ing out beforehand and no difference. (Stayed blank instead of having any data) Does the device not care that I blew out the MBR? |
|
The MBR is sector 0 (zero) the command I gave was supposed to start zeroing from sector 1 - but I realize I forgot to pass the parameter seek=1, it should have been: dd if=/dev/zero of=/dev/mmcblkX bs=512 count=32768 seek=1 that was my bad - you would probably have to redo #11 to build a new MBR now. |
|
As for the serial, I have a couple Pi Zeros I can try and get working (They do have 3.3v UART right?) Thanks for the tips. |
|
Yeah you could wire the serial from a pi zero directly. |
|
@parkerlreed I can’t read the numbers on the chips but based on the previous version of the board the flash may actually be the one on the other side of the board instead of the one I posted above (pin 8 3.3v marked): Like I said before you don’t need to connect the 3.3v I only marked it as a way to try and determine which pads to use (so you don’t need to solder a wire to the 3.3v pad). |
|
|
Also for reference here's the listing for this camera https://www.walmart.com/ip/Merkury-Innovations-Smart-Wifi-Camera-1080p-2-Way-Communication/679786717 |
|
Send me an email and I can send you something to help out |
|
Sent. Thanks. |
|
Based on the bootargs shown the method used for Merkury 720p (my other repo) should work if you just adjust the load address (looks like 81c08000?) |
|
Thanks. Will give it a shot |
|
So do I do the port 80 enable first and then the rest? |
|
It should just need the commands in the env file (typed in thr uboot since you can), ideally we figure out the address so that hack would work on it.
If your port 80 is disabled be default you can use the ppsFactoryTool.txt to enable it but that’s not important for the hack to work.
|
|
Remove the hack= part and only do what is after the = sign .. the hack= part is to set the environment from file which is not needed in uboot. |
|
Actually nevermind that, we need to figure out where the files are loaded, can you execute printenv and post the response ? |
|
Ok so something like this? ipaddr is supposed to be it's own command or part of the first one? (There's a newline in the env so that's what's confusing me) |
|
Without being familiar with uboot it will be easier to just modify the hack for your camera — with the printenv output I can probably do it. the commands from the env file would have to be like this I think:
then another command:
It would be nice if you execute and post the output for printenv and for help so I know what is available |
|
|
After setting those two Should be good to power cycle? |
|
There’s a very good chance that if you just adjust the address in ppsMmcTool.txt and env files from the merkury 720p project to 81c08000 (instead of 81808000) you should be able to install the hack using the steps in that repo - that is what I would try first. |
|
onvif (tuyya_config.json) did reset. I forgot 8080 was the hack webserver. |
|
Ok bit the bullet and took the update. 4.0.6 Hack still works. New ppsapp |
|
The new one looks like the old one too (not in the same format as 2.7.x and 2.9.x) -- the mjpeg/snap address should be: 00375b1c if you want to try play.cgi the address should be: 00376328 I still need more time to look at enabling RTSP/ONVIF (whatever is possible) |
|
--deleted-- EDIT: Looking a little more in the code the change has good potential to enable onvif, the question is if the onvif implementation works (or if at least RTSP works) |
|
Will check it out and report back. I brought the camera to work but forgot the SD card. Doh. |
|
Do I still need to enable onvif in tuya_config or should that have forced it? Without touching the cfg, it doesn't appear to be open. |
|
You should not need to modify the json file but did you try onvif device manager or something similar anyway? The onvif/rtsp may be udp only and not show up on nmap - I will take a look at the log to see if I can find anything. |
|
Nevermind.. from the log it looks like the onvif function did not open as I hoped - either the change I made did not work OR the patched file did not run — since you got a log file I am certain that you placed the file in the right place and rebooted the device so unless it was the wrong file (unlikely) I assume change I made was not enough. I will review and give you something else to try. |
|
--deleted-- Can you try this one and make me another log ? I made 3 changes to ensure the onvif setting would be enable in all places that were setting it. |
|
@parkerlreed I assume you had no chance to try the new changes yet ? |
|
Have not. Sorry. Been tied up with work. I can test it tonight. |
|
8000 is open this time What's the onvif username/password? I haven't been able to connect with any combo yet. |
|
Log |
|
Should be admin/admin - you may want to check onvif device manager (Windows) or some onvif app. You may want to try rtsp:https://IP:8554/Streaming/Channels/101 (may need user passowrd admin:admin) and probably only will work on udp since tcp is not open |
|
That worked! UDP 8554 and admin:admin Since that worked is there any way to kill the connection to the tuya servers... |
|
Awesome! Offline requires more changes and this being a totally different code it would require more research into it. I wonder also if there’s a time limit in using rtsp (udp) and wonder if tcp may also work (just not detected by nmap). I can take a quick look but no promises on the offline thing. |
|
By the way the same url /102 should be low resolution stream. |
|
Ahh yes TCP worked as well |
|
102 is indeed 640x480 |
|
Cool! I will create/post a patch and probably make another repo with details of this camera just for future reference. If I find something regarding the offline mode I will let you know so you can test it. |
|
Trying with an ONVIF viewer on the computer and the device doesn't seem to be in spec for full operation. Two tools have failed to probe the full info/connect to the camera fully. Manual RTSP viewing is fine. |
|
@parkerlreed New repo is up with details from here and from ghidra work: https://github.com/guino/Merkury1080P |
|
@parkerlreed if you'd like to try the device off-cloud you can use this patch: Please note that you'll need to block off the tuya servers on your router AND add a call to ntpd like this: #4 (comment) in order to set the time on the device (or it will display incorrect time). Since this is a wifi device it's obvious it has to connect to some network in order to be used but this patch should allow it to start up without waiting 'forever' to connect to the tuya servers so you could use it in an isolated network with access to a local ntp server (or you could just use some other script/way to set the time in it when it boots up). There may be other information on #4 that could be relevant so it may be worth glancing over. If you do find the time to test it let me know how that goes. |
|
how to interrupt U-boot at |
|
@mariarti send me an email (it is on my github profile) and I can help you out. |



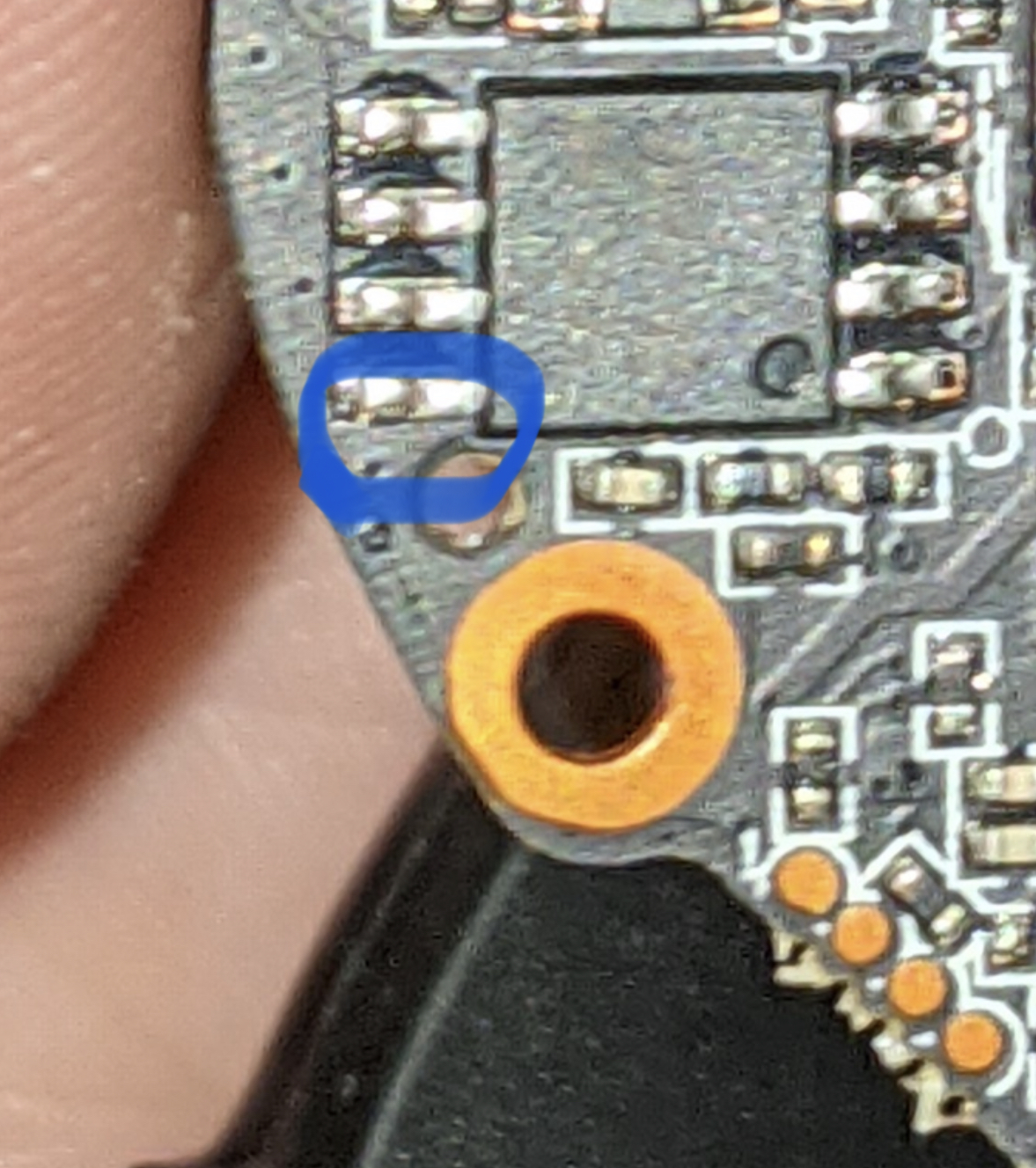





Here's a couple of images. Looks similar to the board in #11 from @swisslegacy
Originally posted by @parkerlreed in #2 (comment)
The text was updated successfully, but these errors were encountered: